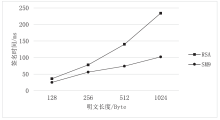
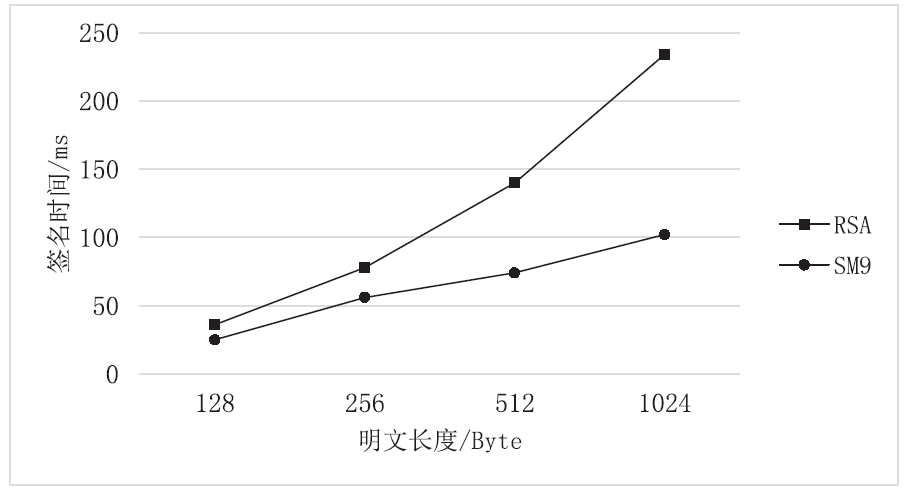
| [1] |
CHEN Mingqi, HONG Xuehai, WANG Wei, et al.The Development Trends of the Network Security and Information Technology[J]. Netinfo Security, 2015(4): 1-4.
|
|
陈明奇,洪学海,王伟,等.关于网络安全和信息技术发展态势的思考[J].信息网络安全,2015(4):1-4.
|
| [2] |
DIFFIE W, HELLMAN M.New Directions in Cryptography[J]. IEEE Transactions on Information Theory, 1976, 22(6): 644-654.
|
| [3] |
RIVEST R, SHAMIR A, ADLEMAN L M.A Method for Obtaining Digital Signatures and Public-key Cryptosystems[J]. Communications of the Acm, 1978, 21(2): 120-126.
|
| [4] |
ELGAMAL T.A Public Key Cryptosystem and a Signature Scheme Based on Discretelogarithms[J]. IEEE Transactions on Information Theory, 1985, 31(4): 469-472.
|
| [5] |
SCHNORR C P.Efficient Identification and Signatures for Smart Cards[C]// BRASSARD G. Advances in Cryptology - CRYPTO’ 89 Proceedings, August 20-24, 1989, Santa Barbara, CA, USA. New York: Springer, 1989: 239-252.
|
| [6] |
NYBERG K, RUEPPEL R A.A New Signature Scheme based on the DSA Giving Message Recovery[C]// ACM. Proceedings of the 1st ACM Conference on Computer and Communications Security, November 3-5, 1993, Fairfax, VA, USA. New York: ACM, 1993: 58-61.
|
| [7] |
OKAMOTO T.Provably Secure and Practical Identification Schemes and Corresponding Signature Schemes[C]//Springer. Advances in Cryptology - CRYPTO’ 92, August 16-20, 1992, Santa Barbara, CA, USA. Berlin: Springer, 1992: 31-53.
|
| [8] |
CHAUM D.Blind Signature System[C]//Springer. Advances in Cryptology: Proceedings of Crypto 83, August 21-24, 1983, Santa Barbara, CA, USA. Berlin: Springer, 1984: 153.
|
| [9] |
POINTCHEVAL D, STERN J.Security Arguments for Digital Signatures and Blind Signatures[J]. Journal of Cryptology, 2000, 13(3): 361-396.
|
| [10] |
ABE M, FUJISAKI E.How to Date Blind Signatures[C]//Springer. Advances in Cryptology - ASIACRYPT’96, November 3-7, 1996, Kyongju, Korea. Berlin: Springer, 1996: 244-251.
|
| [11] |
POINTCHEVAL D, STERN J.Security Arguments for Digital Signatures and Blind Signatures[J]. Journal of Cryptology, 2000, 13(3): 361-396.
|
| [12] |
LYSYANSKAYA A, RAMZAN Z.Group Blind Digital Signatures: A Scalable Solution to Electronic Cash[C]//Springer. FC 1998: Financial Cryptography, February 23-25, 1998, Anguilla, British West Indies. Berlin: Springer, 1998: 184-197.
|
| [13] |
OKAMOTO T.An Efficient Divisible Electronic Cash Scheme[C]// Springer. CRYPTO 1995: Advances in Cryptology - CRYPT0’ 95. August 27-31, 1995, Santa Barbara, CA, USA. Berlin: Springer, 1995: 438-451.
|
| [14] |
ZHANG Jianzhong, WANG Jie, LIU Qinxi.New Proxy Blind Signature Scheme and Its Application in Electronic Cash[J]. Application Research of Computers, 2009, 26(1): 347-349.
|
|
张建中,王洁,刘勤喜.新的代理盲签名方案及其在电子现金中的应用[J].计算机应用研究,2009,26(1):347-349.
|
| [15] |
WANG Changji, PEI Dingyi, JIANG Wenbao.An Improved e-Cash System Based on Restrictive Blind Signature[J]. Acta Electronica Sinica, 2002, 30(7): 1083-1085.
|
|
王常吉,裴定一,蒋文保.一个改进的基于限制性盲签名的电子现金系统[J].电子学报,2002,30(7):1083-1085.
|
| [16] |
FAN C I, LEI C L.Efficient Blind Signature Scheme Based on Quadratic Residues[J]. Electronics Letters, 1996, 32(9): 811-813.
|
| [17] |
HARN L, XU Y.Design of generalised ElGamal Type Digital Signature Schemes Based on Discrete Logarithm[J]. Electronics Letters, 1994, 30(24): 2025-2026.
|
| [18] |
GARG S, RAO V, SAHAI A, et al.Round OPTIMAL BLIND SIGNATures[C]//ROGAWAY P. CRYPTO 2011: Advances in Cryptology, August 14-18, 2011, Santa Barbara, CA, USA. Berlin: Springer, 2011: 630-648.
|
| [19] |
SHAMIR A.Identity-Based Cryptosystems and Signature Schemes[C]//BLAKLEY G R, CHAUM D. CRYPTO 1984: Advances in Cryptology, August 19-22, 1984, Santa Barbara, CA, USA. Berlin: Springer, 1984: 47-53.
|
| [20] |
JOYE M, NEVEN G.Identity-based Cryptography[M]// Information and Communication Technology. Springer International Publishing, 2008.
|
| [21] |
CAMENISCH J, KOHLWEISS M, RIAL A, et al.Blind and Anonymous Identity-Based Encryption and Authorised Private Searches on Public Key Encrypted Data[C]//JARECKI S, TSUDIK G. PKC 2009: Public Key Cryptography - PKC 2009, March 18-20, 2009, Irvine, CA, USA. Berlin: Springer, 2009: 196-214.
|
| [22] |
DING X, TSUDIK G.Simple Identity-Based Cryptography with Mediated RSA[C]//JOYE M. CT-RSA 2003: Topics in Cryptology, April 13-17, 2003, San Francisco, CA, USA. Berlin: Springer, 2003: 193-210.
|
| [23] |
YUAN Feng, CHENG Zhaohui.Overview on SM9 Identity-Based Cryptographic Algorithm[J]. Journal of Information Security Research, 2016, 2(11): 1008-1027.
|
|
袁峰,程朝辉. SM9标识密码算法综述[J].信息安全研究,2016,2(11):1008-1027.
|
| [24] |
SHI Youhui, LI Weisheng.A Survey of Blind Signature Studies[J]. Computer Engineering & Science, 2005, 27(7): 83-85.
|
|
史有辉,李伟生.盲签名研究综述[J].计算机工程与科学,2005,27(7):83-85.
|
| [25] |
WANG Xiaoyun, YU Hongbo.SM3 Cryptographic Hash Algorithm[J]. Journal of Information Security Research, 2016, 2(11): 983-994.
|
|
王小云,于红波. SM3密码杂凑算法[J].信息安全研究,2016,2(11):983-994.
|