Netinfo Security ›› 2018, Vol. 18 ›› Issue (5): 32-40.doi: 10.3969/j.issn.1671-1122.2018.05.004
• Orginal Article • Previous Articles Next Articles
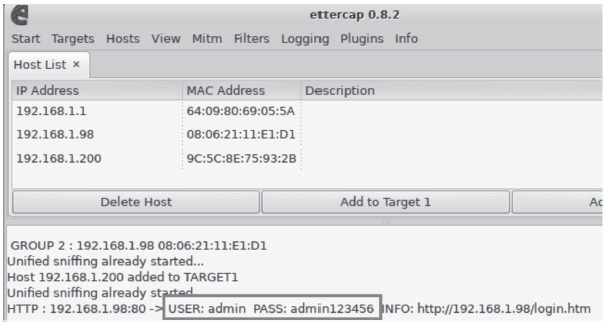
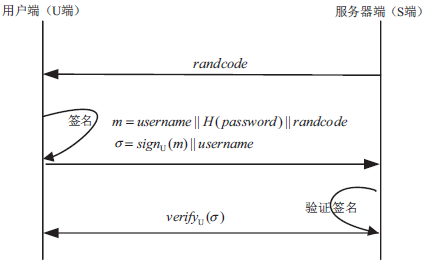
Protection Technology of Network Camera Based on SM2 Digital Signature
Liming ZUO1,2( ), Pingping XIA1,2, Zuosong CHEN1,2
), Pingping XIA1,2, Zuosong CHEN1,2
- 1. School of Science, East China Jiaotong University, Nanchang Jiangxi 330013, China
2. Institute of Systems Engineering and Cryptograph, East China Jiaotong University, Nanchang Jiangxi 330013, China
-
Received:2018-02-26Online:2018-05-15Published:2020-05-11
CLC Number:
Cite this article
Liming ZUO, Pingping XIA, Zuosong CHEN. Protection Technology of Network Camera Based on SM2 Digital Signature[J]. Netinfo Security, 2018, 18(5): 32-40.
share this article
| [1] | ZHANG Yuting, YAN Chenghua, WEI Yuren.Research on Security of IoT Perception Layer Based on Node Authentication[J]. Netinfo Security, 2015(11): 27-32. |
| 张玉婷,严承华,魏玉人. 基于节点认证的物联网感知层安全性问题研究[J]. 信息网络安全,2015(11):27-32. | |
| [2] | CSDN. Google’s Bugs: Let You Control the Camera of the World through the Network[EB/OL]. ,2018-1-21. |
| CSDN. Google的漏洞——让你通过网络控制全世界的摄像头[EB/OL]. ,2018-1-21. | |
| [3] | Sina. Network Cameras are Now Vulnerableto Hackers can Easily Capture the Content of the Shooting[EB/OL]. ,2018-1-21. |
| 新浪科技. 传网络摄像机现漏洞黑客可轻易获取拍摄内容[EB/OL]. ,2018-1-21. | |
| [4] | General Administration of Quality Supervision, Inspection and Quarantine of People’s Republic of China. AQSIQ Releases Smart Camera Quality Safety Risk Warning[EB/OL]. ,2018-1-21. |
| 国家质量监督检验检疫总局. 质检总局发布智能摄像头质量安全风险警示[EB/OL]. ,2018-1-21. | |
| [5] | HackerNews. Nearly 2/3 Surveillance Camera Network in Washington, DC has been Hijacked by Romanian Hackers[EB/OL]. ,2018-1-21. |
| HackerNews. 美国华盛顿近2/3监控摄像机网络曾遭罗马尼亚黑客劫持[EB/OL]. ,2018-1-21. | |
| [6] | PIERRE KIM. IT Security Research by Pierre[EB/OL]. ,2018-1-29. |
| [7] | CHEN Bing, ZOU Xiang, SHEN Hanhui, et al.Design and Implementation of Video Security Access System[J]. Netinfo Security, 2010(8): 74-75. |
| 陈兵,邹翔,沈寒辉,等. 视频安全接入系统设计与实现[J]. 信息网络安全,2010(8):74-75. | |
| [8] | YOKOTE T, FUJII Y, MARU K, et al.Introduction of Security Camera System with Privacy Protection into a Residential Area[J]. Social and Behavioral Sciences, 2010, 2(1): 105-110. |
| [9] | WANG Malong, HU Xiaoqin, WANG Lin, et al.Research and Implementation of Anti-leakage System for Android Smartphone User Scenario Information[J]. Netinfo Security, 2013(2): 35-37. |
| 王马龙,胡晓勤,王琳,等. Android智能手机用户场景信息防泄漏系统的研究与实现[J]. 信息网络安全,2013(2):35-37. | |
| [10] | MAREK G, PETER Š. Design the Robot as Security System in the Home[EB/OL]. , 2018-1-21. |
| [11] | PARK J, OH S H, LEE Y S.Network Security Camera System and Its Application for Consumer Electronics in Ubiquitous Environment[J]. Multimedia Tools & Applications, 2015, 74(5): 1577-1591. |
| [12] | WANG Jingzhong, WANG Jingfeng, WANG Baocheng, et al.A Security Research on Smart Phone Access Control System Based on QR Code Hybrid Encryption Technology[J]. Netinfo Security, 2015(12): 8-13. |
| 王景中,王精丰,王宝成,等. 基于二维码混合型加密技术的智能手机门禁系统安全性研究[J]. 信息网络安全,2015(12):8-13. | |
| [13] | WU Zhenyu, CHIANG D L, LIN T C, et al.A Reliable Dynamic User-remote Password Authentication Scheme over Insecure Network[C]//IEEE. 26th International Conference on Advanced Information Networking and Applications Workshops, March 26-29, 2012, Fukuoka, Japan. New Jersey: IEEE, 2012: 25-28. |
| [14] | SHUANG Shi.Top Ten Reasons for Hacking Web Attacks and Ten Ways to Resist[J]. Network & Information, 2008, 22(11): 58-59. |
| 双十. 黑客Web攻击的十大原因及十大抵御方法[J]. 网络与信息,2008,22(11):58-59. | |
| [15] | LI Yonghai.Applications of SM2 Algorithm in the Security Ward Information System of Central Bank[J]. Financial Technology Time, 2017(12): 39-41. |
| 李永海. SM2算法在央行发行库安全守卫信息系统中的应用[J]. 金融科技时代,2017(12):39-41. | |
| [16] | LUO Zhao, XIE Jihua, GU Wei, et al.Development of Power Grid Information Security Support Platform Based on SM2 Cipher System[J]. Automation of Electric Power Systems, 2014, 38(6): 68-74. |
| 骆钊,谢吉华,顾伟,等. 基于SM2密码体系的电网信息安全支撑平台开发[J]. 电力系统自动化,2014,38(6):68-74. | |
| [17] | LUO Zhao, YAN Tong, XIE Jihua, et al.Application of SM2 Encryption System in Telecontrol Communication of Smart Substations[J]. Automation of Electric Power Systems, 2016, 40(19): 127-133. |
| 骆钊,严童,谢吉华,等. SM2加密体系在智能变电站远动通信中的应用[J]. 电力系统自动化,2016,40(19):127-133. | |
| [18] | WU Chengwei, XIONG Yanling, WU Jing, et al.Design of WeChat Platform for Traceability System of Agricultural Products Based on Trade Secret QR Code[J]. Modern Agricultural Science and Technology, 2017(17): 287-289. |
| 吴成伟,熊燕玲,吴静,等. 基于商密二维码的农产品溯源系统微信平台设计[J]. 现代农业科技,2017(17):287-289. | |
| [19] | Penetration Testing and Security Service. How Tos Pwning CCTV Cameras[EB/OL]. , 2018-1-21. |
| [20] | LI Juan, YU Zhongchen, HAN Wenying.The Security Risk Analysis of IoT Camera in Smart City[J]. Information Security and Communications Privacy, 2017(12): 40-48. |
| 李娟,于忠臣,韩文英. 智慧城市中物联网摄像头安全风险分析[J]. 信息安全与通信保密,2017(12):40-48. | |
| [21] | OSCCA. Public Key Cryptography Algorithm SM2 Based on Elliptic Curves[EB/OL]. ,2018-1-21. |
| 国家密码管理局. SM2椭圆曲线公钥密码算法[EB/OL]. ,2018-1-21. | |
| [22] | WANG Yong, CEN Rongwei, GUO Hong, et al.The Research of SM2 Cryptographic Algorithm Update over CEGN Network Electronic Certification System[J]. Netinfo Security, 2012(10): 83-85. |
| 王勇,岑荣伟,郭红,等. 国家电子政务外网电子认证系统SM2国密算法升级改造方案研究[J]. 信息网络安全,2012(10):83-85. | |
| [23] | ZHANG Fangguo, CHEN Xiaofeng, WANG Yumin.The Status of Attack on the Discrete Logarithm of Elliptic Curves[J]. Journal of Xidian University, 2002, 29(3): 398-403. |
| 张方国,陈晓峰,王育民. 椭圆曲线离散对数的攻击现状[J]. 西安电子科技大学学报,2002,29(3):398-403. | |
| [24] | LI Junfang, CUI Jianshuang.A Method to Generate Elliptic Curves[J]. Computer Engineering and Applications, 2004, 40(36): 67-68. |
| 李俊芳,崔建双. 抗MOV规约法攻击的一类安全椭圆曲线[J]. 计算机工程与应用,2004,40(36):67-68. | |
| [25] | SHAO Fei, MENG Bo.A Non-interactive Deniable Authentication Protocol Based on Elliptic Curve Discrete Logarithm Problem[J]. Journal of Chinese Computer Systems, 2014, 35(1): 89-92. |
| 邵飞,孟博. 一种基于椭圆曲线离散对数问题的非交互式可否认认证协议[J]. 小型微型计算机系统,2014,35(1):89-92. | |
| [26] | ZHOU Keyuan.Digital Signature Scheme Based on Elliptic Curve and Factoring[J]. Computer Science, 2014, 41(S1): 366-368. |
| 周克元. 基于椭圆曲线和因子分解双难题的数字签名方案[J]. 计算机科学,2014,41(S1):366-368. | |
| [27] | LAUTER K.The Advantages of Elliptic Curve Cryptography for Wireless Security[J]. IEEE Wireless Communications, 2004, 11(1): 62-67. |
| [28] | ZHANG Yongjian.Research of RSA Algorithm and SM2 Algorithm[D]. Ganzhou: Jiangxi University of Science and Technology, 2015. |
| 张永建. RSA算法和SM2算法的研究[D]. 赣州:江西理工大学,2015. | |
| [29] | WANG Quan, YANG Lin, LIU Wei, et al.Research on Access Control Methods Based on USBKEY[J]. Computer Engineering and Design, 2008, 29(11): 2727-2729. |
| 王权,杨林,刘伟,等. 基于USBKEY的访问控制方法研究[J]. 计算机工程与设计,2008,29(11):2727-2729. | |
| [30] | SOLINAS J A.Efficient Arithmetic on Koblitz Curves[J]. Designs, Codes and Cryptography, 2000, 19(2-3): 195-249. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||