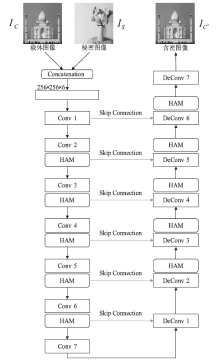
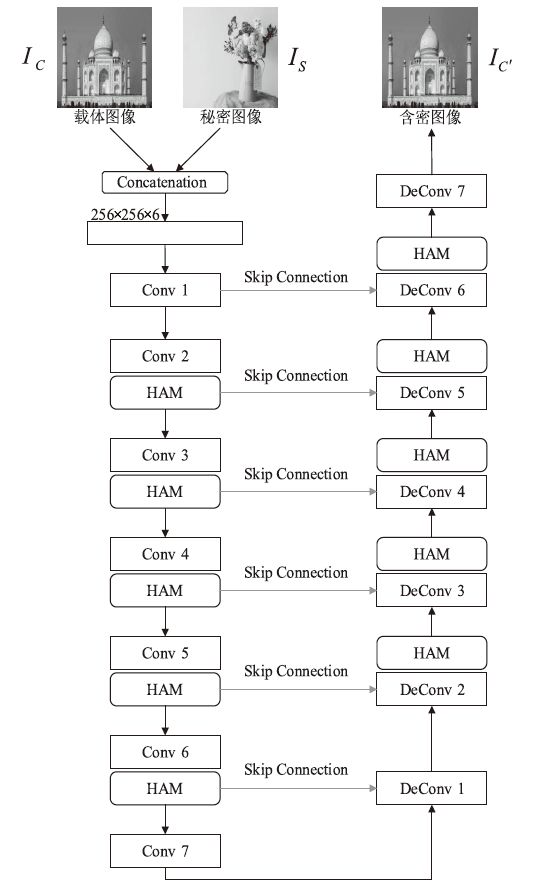
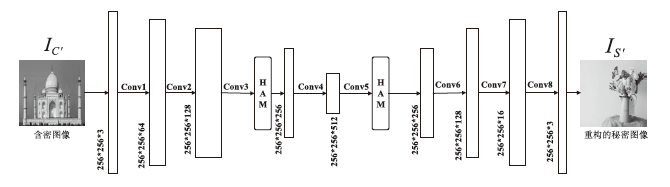
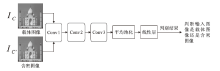
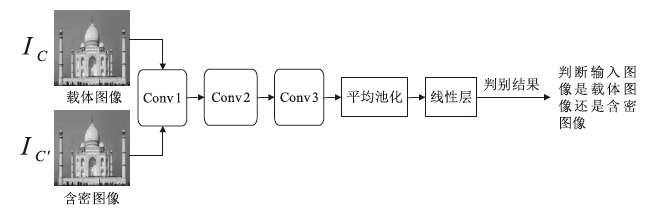
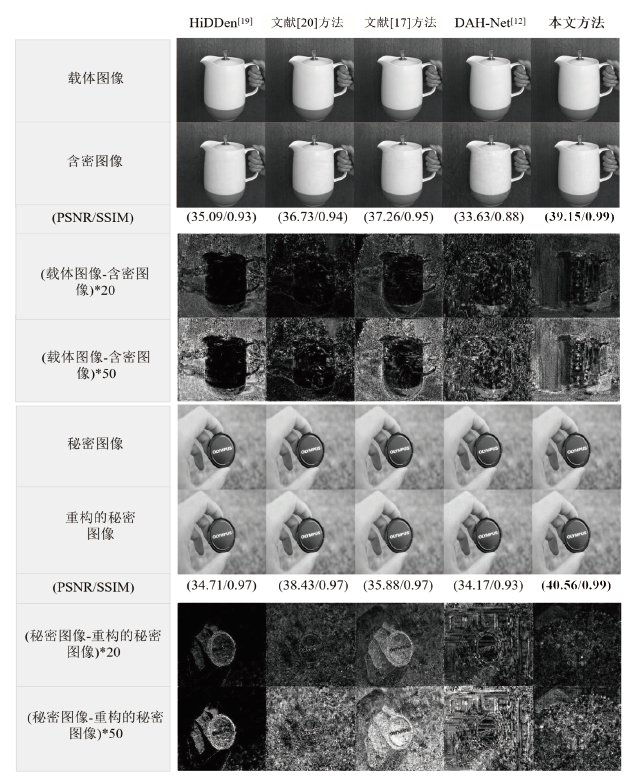
| [1] |
MANDAL P C, MUKHERJEE I, PAUL G, et al. Digital Image Steganography: A Literature Survey[J]. Information Sciences, 2022, 609: 1451-1488.
|
| [2] |
XIA Qiang, HE Peisong, LUO Jie, et al. An Efficient Enhancement Algorithm of Cover Image Based on Universal Adversarial Noise[J]. Netinfo Security, 2022, 22(2): 64-75.
|
|
夏强, 何沛松, 罗杰, 等. 基于普遍对抗噪声的高效载体图像增强算法[J]. 信息网络安全, 2022, 22(2): 64-75.
|
| [3] |
ZHANG Hongjuan, ZHU Chenming. Novel LSB Steganography Algorithm of Against Statistical Analysis[J]. Computer Engineering, 2008, 34(23): 144-146.
doi: 10.3969/j.issn.1000-3428.2008.23.052
|
| [4] |
LI Xiaolong, YANG Bin, CHENG Daofang, et al. A Generalization of LSB Matching[J]. IEEE Signal Processing Letters, 2009, 16(2): 69-72.
|
| [5] |
HOLUB V, FRIDRICH J. Designing Steganographic Distortion Using Directional Filters[C]// IEEE. 2012 IEEE International Workshop on Information Forensics and Security (WIFS). New York: IEEE, 2012: 234-239.
|
| [6] |
PEVNY T, FILLER T, BAS P. Using High-Dimensional Image Models to Perform Highly Undetectable Steganography[C]// Springer. 12th Information Hiding Conference. Heidelberg: Springer, 2010: 161-177.
|
| [7] |
LI Bin, WANG Ming, HUANG Jiwu, et al. A New Cost Function for Spatial Image Steganography[C]// IEEE. 2014 IEEE International Conference on Image Processing (ICIP). New York: IEEE, 2014: 4206-4210.
|
| [8] |
HOLUB V, FRIDRIVH J, DENEMARK T. Universal Distortion Function for Steganography in an Arbitrary Domain[J]. EURASIP Journal on Information Security, 2014, 2014: 1-13.
|
| [9] |
CHAUMONT M. Deep Learning in Steganography and Steganalysis[M]. New York: Academic Press, 2020.
|
| [10] |
YU Chong. Attention Based Data Hiding with Generative Adversarial Networks[C]// AAAI. 34th AAAI Conference on Artificial Intelligence. Menlo Park: AAAI, 2020: 1120-1128.
|
| [11] |
TAN Jingxuan, LIAO Xin, LIU Jiate, et al. Channel Attention Image Steganography with Generative Adversarial Networks[J]. IEEE Transactions on Network Science and Engineering, 2021, 9(2): 888-903.
|
| [12] |
ZHANG Le, LU Yao, LI Jinxing, et al. Deep Adaptive Hiding Network for Image Hiding Using Attentive Frequency Extraction and Gradual Depth Extraction[J]. Neural Computing and Applications, 2023, 35(15):10909-10927.
|
| [13] |
GOODFELLOW I, POUGET-ABADIE J, MIRZA M, et al. Generative Adversarial Networks[J]. Communications of the ACM, 2020, 63(11): 139-144.
|
| [14] |
VOLKHONSKIY D, NAZAROV I, BURNAEV E. Steganographic Generative Adversarial Networks[C]// ICMV. Twelfth International Conference on Machine Vision (ICMV 2019). Bellingham: SPIE, 2020: 991-1005.
|
| [15] |
WANG Yaojie, NIU Ke, YANG Xiaoyuan. Image Steganography Scheme Based on GANs[J]. Netinfo Security, 2019, 19(5): 54-60.
|
|
王耀杰, 钮可, 杨晓元. 基于生成对抗网络的信息隐藏方案[J]. 信息网络安全, 2019, 19(5): 54-60.
|
| [16] |
LEI Yu, LIU Jia, LI Jun, et al. Research and Implementation of a Image Steganography Method Based on Conditional Generative Adversarial Networks[J]. Netinfo Security, 2021, 21(11): 48-57.
|
|
雷雨, 刘佳, 李军, 等. 一种基于条件生成对抗网络的图像隐写方法研究与实现[J]. 信息网络安全, 2021, 21(11): 48-57.
|
| [17] |
BALUJA S. Hiding Images within Images[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2019, 42(7): 1685-1697.
|
| [18] |
XIONG Jinbo, MA Rong, ZHANG Yuanyuan, et al. Image Information Hiding Method and Implementation for Social Network[J]. Netinfo Security, 2017, 17(3): 6-8.
|
|
熊金波, 马蓉, 张媛媛, 等. 面向社交网络的图片信息隐藏方法与实现[J]. 信息网络安全, 2017, 17(3): 6-8.
|
| [19] |
ZHU Jiren, KAPLAN R, JOHNSON J, et al. Hidden: Hiding Data with Deep Networks[C]// ECCV. 15th European Conference on Computer Vision. Heidelberg: Springer, 2018: 657-672.
|
| [20] |
WENG Xinyu, LI Yongzhi, CHI Lu, et al. High-Capacity Convolutional Video Steganography with Temporal Residual Modeling[C]// ACM. Proceedings of the 2019 on International Conference on Multimedia Retrieval. New York: ACM, 2019: 87-95.
|
| [21] |
RUSSAKOVSKY O, DENG Jia, SU Hao, et al. Imagenet Large Scale Visual Recognition Challenge[J]. International Journal of Computer Vision, 2015, 115: 211-252.
|
| [22] |
LIN T Y, MAIRE M, BELONGIE S, et al. Microsoft COCO: Common Objects in Context[C]// ECCV. 13th European Conference on Computer Vision. Heidelberg: Springer, 2014: 740-755.
|
| [23] |
AGUSTSSON E, TIMOFTE R. Ntire 2017 Challenge on Single Image Super-Resolution: Dataset and Study[C]// IEEE. 30th IEEE/CVF Conference on Computer Vision and Pattern Recognition Workshops (CVPRW). New York: IEEE, 2017: 126-135.
|
| [24] |
RUSTAD S, ANDONO P N, SHIDIK G F. Digital Image Steganography Survey and Investigation (Goal, Assessment, Method, Development, and Dataset)[J]. Signal Processing, 2023, 27(5): 985-1024.
|
| [25] |
AGRAWAL R, AHUJA K. CSIS: Compressed Sensing-Based Enhanced-Embedding Capacity Image Steganography Scheme[J]. IET Image Processing, 2021, 15(9): 1909-1925.
|
 )
)