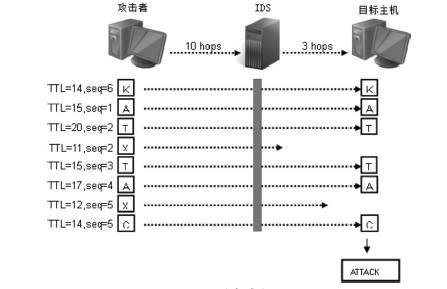
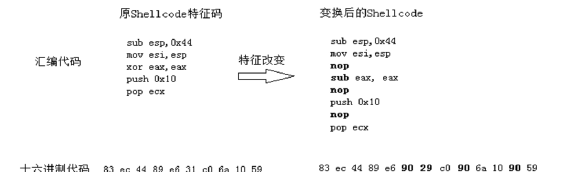
| [1] |
王磊,双锴. 入侵逃逸技术综述[EB/OL]..
|
| [2] |
王竹晓,夏宏,石瑾,等. 高级逃逸技术综述: SCADA系统Cyber安全的挑战[EB/OL]..
|
| [3] |
POSTEL J.Rfc 791: Internet Protocol[J]. Status Internet Standard Internet Engineering Task Force, 1981, 28(2-3):235-239.
|
| [4] |
BOLTZ M, JALAVA M, WALSH J.New Methods and Combinatorics for Bypassing Intrusion Prevention Technologies[R]. Stonesoft, Tech. Rep, 2010.
|
| [5] |
Ptacek T H, Newsham T N. Insertion, Evasion,Denial of Service: Eluding Network Intrusion Detection [R].Calgary Alberta,Secure Networks INC, 1998.
|
| [6] |
王蛟,杨波. 高级逃逸技术分析[J]. 中国电业(技术版),2012(11):74-77.
|
| [7] |
DYRMOSE M, VANDENBRINK R.Beating the IPS[R]. Tech. rep., SANS Institute, 2013.
|
| [8] |
CHENG T H, LIN Y D, LAI Y C, et al.Evasion Techniques: Sneaking through Your Intrusion Detection/prevention Systems[J]. Communications Surveys & Tutorials, IEEE, 2012, 14(4): 1011-1020.
|
| [9] |
XYNOS K, SUTHERLAND I, BLYTH A.Effectiveness of Blocking Evasions in Intrusion Prevention System[J]. University of South Wales, 2013: 1-6.
|
| [10] |
WATSON D, SMART M, MALAN G R, et al.Protocol Scrubbing: Network Security through Transparent Flow Modification[J]. IEEE/ACM Transactions on Networking (TON), 2004, 12(2): 261-273.
|
| [11] |
VUTUKURU M, BALAKRISHNAN H, PAXSON V.Efficient and Robust TCP Stream Normalization[C]//IEEE. Symposium on Security and Privacy, 2008, Oakland, CA. NewYork: IEEE, 2008: 96-110.
|
| [12] |
HANDLEY M, PAXSON V, KREIBICH C.Network Intrusion Detection: Evasion, Traffic Normalization, and End-to-End Protocol Semantics[C]//USENIX. 10th USENIX Security Symposium, 2001, Washington DC. New York: USENIX, 2001: 115-131.
|
| [13] |
SHANKAR U, PAXSON V.Active Mapping: Resisting NIDS Evasion without Altering Traffic[C]//IEEE. Symposium on Security and Privacy, 2003, Berkeley, CA New York:IEEE, 2003: 44-61.
|
| [14] |
TALECK G.Ambiguity Resolution via Passive OS Fingerprinting[C]//Springer. Recent Advances in Intrusion Detection,2003, Pittsburgh, PA.Heidelber:Springer g, 2003: 192-206.
|
| [15] |
VARGHESE G, FINGERHUT J A, BONOMI F.Detecting Evasion Attacks at High Speeds without Reassembly[J]. ACM SIGCOMM Computer Communication Review, 2006, 36(4): 327-338.
|
| [16] |
ANTICHI G, FICARA D, GIORDANO S, et al.Counting Bloom Filters for Pattern Matching and Anti-evasion at the Wire Speed[J]. Network, IEEE, 2009, 23(1): 30-35.
|