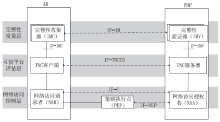
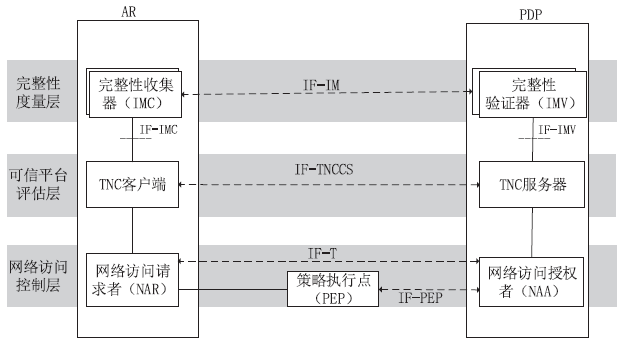
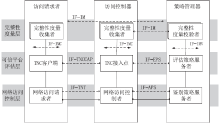
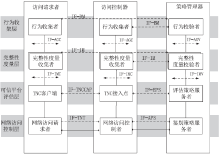
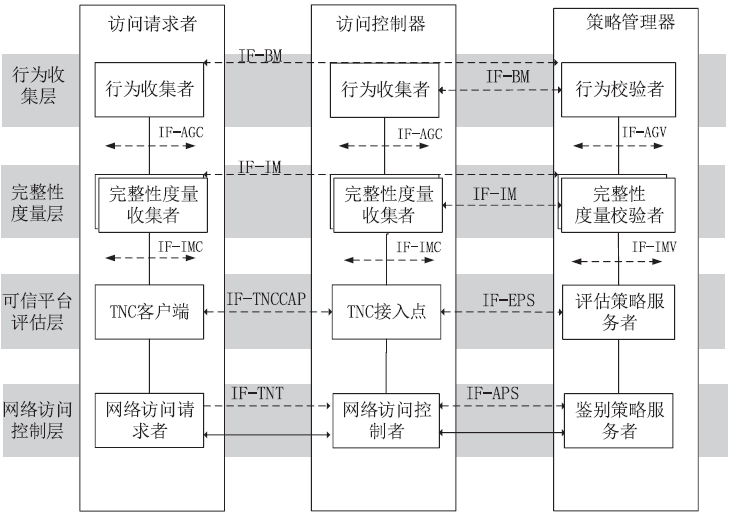
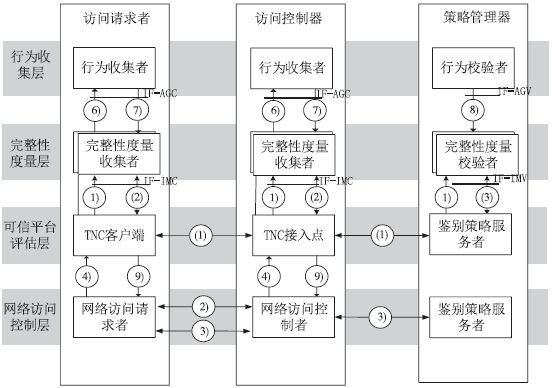
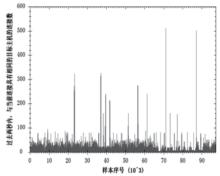
| [1] |
FAN Y.Research on the Security Problem in Windows7 Operating System[C]//MTMA. EighthInternational Conference on Measuring Techn-ology and Mechatronics Automation,March 11-12,2016,Machu,China.New York:IEEE,2016:568-571.
|
| [2] |
CORREGEDOR M, SOLMS S V.Windows 8 32 bit-Improved Security?[C]//IEEE. AFRICON 2013, September 9-12, 2013, Pointe-Aux-Piments, Mauritius. New York:IEEE, 2013:1-5.
|
| [3] |
SINGH B.Network Security and Management[C]// ICCIC.IEEE International Conference on Computational Intelligence and Computing Research,December 28-29,2010, Coimbatore, India. New York:IEEE, 2010:1-6.
|
| [4] |
房梁,殷丽华,郭云川,等. 基于属性的访问控制关键技术研究综述[J]. 计算机学报,2017,40(7):1680-1698.
|
| [5] |
李振汕. 指纹识别技术在身份认证中的应用与研究[J]. 信息网络安全,2011(3):12-14.
|
| [6] |
HU L, MAYO J, WALLACE C.An Empirical Study of Three Access Control Systems[C]// IET.International Conference on Security of Information and Networks, November 26-28,2013, Aksaray,Turkey.New York:ACM,2013:287-291.
|
| [7] |
Trusted Computing Group. TCG Specification Architecture Overview[EB/OL]. , 2017-10-1.
|
| [8] |
周婕. 可信网络连接架构及关键技术研究[J]. 计算机与数字工程,2016(9):1774-1779.
|
| [9] |
张焕国,陈璐,张立强. 可信网络连接研究[J]. 计算机学报,2010,33(4):706-717.
|
| [10] |
XIAO J, LI T, HU A.Design of Upper Layer Authentication Protocol Supporting Trusted Network Connect[C]// ICICEE.International Conference on Industrial Control and Electronics Engineering,August 23-25,2012,Xi'an,China.New York:IEEE,2012:1953-1956.
|
| [11] |
黄强,王高剑,米文智,等. 集中统一的可信计算平台管理模型研究及其应用[J]. 信息网络安全,2017(4):9-14.
|
| [12] |
GENZEL C H, SETHMANN R.Custom TransportInterface for the Integration of Trusted Network Connect in German Smart Metering Systems[C]// IEEE.Intelligence and Security Informatics Conference,May 27-29,2015,Baltimore,MD,USA. New York: IEEE, 2015:45-52.
|
| [13] |
张建标,赵子枭,胡俊,等. 云环境下可重构虚拟可信根的设计框架[J]. 信息网络安全,2018(1):1-8.
|
| [14] |
罗亚丽,周安民,吴少华,等. 一种基于行为分析的程序异常检测方法[J]. 计算机应用,2008,28(10):2492-2494.
|
| [15] |
GONG B, ZHANG J B, SHEN C X, et al.Behavior Measurement Model Based on Prediction and Control of Trusted Network[J]. China communications, 2012, 9(5):117-128.
|
| [16] |
PARVEEN H, PANDEY S.Sentiment Analysis on Twitter Dataset Using Naive Bayes Algorithm[C]//IEEE.International Conference on Applied and Theoretical Computing and Communication Technology,November 9-11,2017,Karnataka,India.New York:IEEE,2017:416-419
|
 ), Guojie LIU, Fan YANG
), Guojie LIU, Fan YANG