Netinfo Security ›› 2022, Vol. 22 ›› Issue (7): 37-45.doi: 10.3969/j.issn.1671-1122.2022.07.005
Previous Articles Next Articles
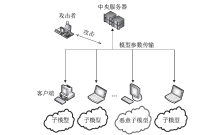
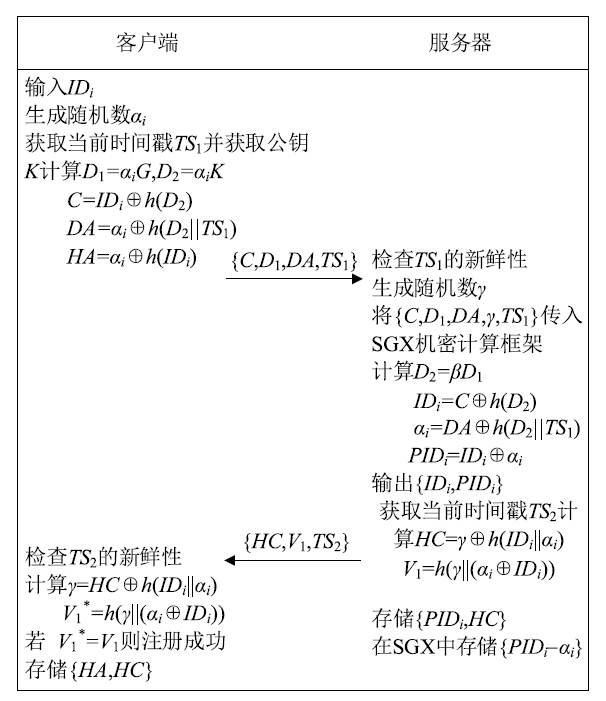
A Lightweight Authentication Protocol Based on Confidential Computing for Federated Learning Nodes
LIU Xin( ), LI Yunyi, WANG Miao
), LI Yunyi, WANG Miao
- School of Information Science & Engineering, Lanzhou University, Lanzhou 730000, China
-
Received:2022-04-10Online:2022-07-10Published:2022-08-17 -
Contact:LIU Xin E-mail:xinl@lzu.edu.cn
CLC Number:
Cite this article
LIU Xin, LI Yunyi, WANG Miao. A Lightweight Authentication Protocol Based on Confidential Computing for Federated Learning Nodes[J]. Netinfo Security, 2022, 22(7): 37-45.
share this article
| [1] | HE Wei. Overview of China’s Digital Economy Development[J]. Information and Communications Technology and Policy, 2021(2): 1-7. |
| 何伟. 我国数字经济发展综述[J]. 信息通信技术与政策, 2021(2):1-7. | |
| [2] | LI Li, FAN Yuxi, TSE M, et al. A Review of Applications in Federated Learning[EB/OL]. (2020-12-07)[2022-03-04]. http://dx.doi.org/10.1016/j.cie.2020.106854. |
| [3] | LI Tian, SAHU A K, TALWALKAR A, et al. Federated Learning: Challenges, Methods, and Future Directions[J]. IEEE Signal Processing Magazine, 2020, 37(3): 50-60. |
| [4] | ZHU Jianming, ZHANG Qinnan, GAO Sheng, et al. Privacy Preserving and Trustworthy Federated Learning Model Based on Blockchain[J]. Chinese Journal of Computers, 2021, 44(12): 2464-2484. |
| 朱建明, 张沁楠, 高胜, 等. 基于区块链的隐私保护可信联邦学习模型[J]. 计算机学报, 2021, 44(12):2464-2484. | |
| [5] | WANG Kunqing, LIU Jing, LI Chen, et al. A Survey on Threats to Federated Learning[J]. Journal of Information Security Research, 2022, 8(3): 223-234. |
| [6] | WU Jianhan, SI Shijing, WANG Jianzong, et al. Threats and Defenses of Federated Learning: A Survey[EB/OL]. (2022-02-17)[2022-03-04]. http://kns.cnki.net/kcms/detail/10.1321.G2.20220216.1702.010.html. |
| 吴建汉, 司世景, 王健宗, 等. 联邦学习攻击与防御综述[EB/OL]. (2022-02-17)[2022-03-04]. http://kns.cnki.net/kcms/detail/10.1321.G2.20220216.1702.010.html. | |
| [7] | SYVERSON P, CERVESATO I. The Logic of Authentication Protocols[C]// Springer. International School on Foundations of Security Analysis and Design. Heidelberg: Springer, 2000: 63-137. |
| [8] | LARA E, AGUILAR L, SANCHEZ M A, et al. Lightweight Authentication Protocol for M2M Communications of Resource-Constrained Devices in Industrial Internet of Things[EB/OL]. (2020-03-27)[2022-03-04]. https://doi.org/10.3390/s20020501. |
| [9] |
YU S, LEE J, PARK K, et al. IoV-SMAP: Secure and Efficient Message Authentication Protocol for IoV in Smart City Environment[J]. IEEE Access, 2020, 8: 167875-167886.
doi: 10.1109/ACCESS.2020.3022778 URL |
| [10] |
AGHILI S F, MALA H, KALIYAR P, et al. SecLAP: Secure and Lightweight RFID Authentication Protocol for Medical IoT[J]. Future Generation Computer Systems, 2019, 101: 621-634.
doi: 10.1016/j.future.2019.07.004 URL |
| [11] | DEEP G, MOHANA R, NAYYAR A, et al. Authentication Protocol for Cloud Databases Using Blockchain Mechanism[EB/OL]. (2019-12-06)[2022-03-04]. https://doi.org/10.3390/s19204444. |
| [12] | REN Jie, LI Meihong, DU Ye, et al. Lightweight Identity-Based Authentication Key Agreement Protocol for Horizontal Federated Learning Environment[EB/OL]. (2021-07-30)[2022-03-04]. https://kns.cnki.net/kcms/detail/detail.aspx?FileName=BJHK20210729006&DbName=CAPJ2021. |
| 任杰, 黎妹红, 杜晔, 等. 横向联邦学习环境基于身份轻量级认证密钥协商协议[EB/OL]. (2021-07-30)[2022-03-04]. https://kns.cnki.net/kcms/detail/detail.aspx?FileName=BJHK20210729006&DbName=CAPJ2021. | |
| [13] |
ZHAO Pengcheng, HUANG Yuanhao, GAO Jianping, et al. Federated Learning-Based Collaborative Authentication Protocol for Shared Data in Social IoV[J]. IEEE Sensors Journal, 2022, 22(7): 7385-7398.
doi: 10.1109/JSEN.2022.3153338 URL |
| [14] | DRUCKER N, GUERON S. Combining Homomorphic Encryption with Trusted Execution Environment: A Demonstration with Paillier Encryption and SGX[C]// ACM. 9th ACM CCS International Workshop on Managing Insider Security Threats(MIST). New York:ACM, 2017: 85-88. |
| [15] | SUN Haiyou, XIAO Sheng. DNA-X: Dynamic Network Authentication Using SGX[C]// ACM. 2nd International Conference on Cryptography, Security and Privacy(ICCSP). New York:ACM, 2018: 110-115. |
| [16] | YANG Qiang, LIU Yang, CHEN Tianjian, et al. Federated Machine Learning: Concept and Applications[J]. ACM Transactions on Intelligent Systems and Technology(TIST), 2019, 10(2): 1-19. |
| [17] | COSTAN V, DEVADAS S. Intel SGX Explained[EB/OL]. (2017-02-21)[2022-03-04]. https://eprint.iacr.org/2016/086. |
| [18] |
VIGANO L. Automated Security Protocol Analysis with the AVISPA Tool[J]. Electronic Notes in Theoretical Computer Science, 2006, 155: 61-86.
doi: 10.1016/j.entcs.2005.11.052 URL |
| [19] | KAUR K, GARG S, KADDOUM G, et al. A Lightweight and Privacy-Preserving Authentication Protocol for Mobile Edge Computing[C]// IEEE. 2019 IEEE Global Communications Conference(GLOBECOM). New York: IEEE, 2019: 1-6. |
| [20] |
SOWJANYA K, DASGUPTA M, RAY S. An Elliptic Curve Cryptography Based Enhanced Anonymous Authentication Protocol for Wearable Health Monitoring Systems[J]. International Journal of Information Security, 2020, 19(1): 129-146.
doi: 10.1007/s10207-019-00464-9 URL |
| [21] |
TSOBDJOU L D, PIERRE S, QUINTERO A. A New Mutual Authentication and Key Agreement Protocol for Mobile Client-Server Environment[J]. IEEE Transactions on Network and Service Management, 2021, 18(2): 1275-1286.
doi: 10.1109/TNSM.2021.3071087 URL |
| [22] | LIU Xin, YANG Haorui, GUO Zhenbin, et al. An Authentication Protocol Achieving Online Registration and Privilege Separation for Industrial Internet of Things[J]. Netinfo Security, 2021, 21(7): 1-9. |
| 刘忻, 杨浩睿, 郭振斌, 等. 一种实现在线注册与权限分离的工业物联网身份认证协议[J]. 信息网络安全, 2021, 21(7):1-9. |
| [1] | LYU Guohua, HU Xuexian, YANG Ming, XU Min. Ship AIS Trajectory Classification Algorithm Based on Federated Random Forest [J]. Netinfo Security, 2022, 22(4): 67-76. |
| [2] | LIU Xin, WANG Jiayin, YANG Haorui, ZHANG Ruisheng. An Internet of Vehicles Authentication Protocol Based on Blockchain and secGear Framework [J]. Netinfo Security, 2022, 22(1): 27-36. |
| [3] | BAI Hongpeng, DENG Dongxu, XU Guangquan, ZHOU Dexiang. Research on Intrusion Detection Mechanism Based on Federated Learning [J]. Netinfo Security, 2022, 22(1): 46-54. |
| [4] | XU Shuo, ZHANG Rui, XIA Hui. Privacy-preserving Strategies for Federated Learning Based on Data Attribute Modification [J]. Netinfo Security, 2022, 22(1): 55-63. |
| [5] | WANG Yuedong, XIONG Yan, HUANG Wenchao, WU Jianshuang. A Formal Analysis Scheme for 5G Private Network Authentication Protocol [J]. Netinfo Security, 2021, 21(9): 1-7. |
| [6] | LU Honglin, WANG Liming, YANG Jing. A New Parameter Masking Federated Learning Privacy Preserving Scheme [J]. Netinfo Security, 2021, 21(8): 26-34. |
| [7] | LIU Xin, YANG Haorui, GUO Zhenbin, WANG Jiayin. An Authentication Protocol Achieving Online Registration and Privilege Separation for Industrial Internet of Things [J]. Netinfo Security, 2021, 21(7): 1-9. |
| [8] | REN Tao, JIN Ruochen, LUO Yongmei. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning [J]. Netinfo Security, 2021, 21(7): 27-34. |
| [9] | LIU Xin, GUO Zhenbin, SONG Yuchen. An Authentication Scheme Based on SGX for Industrial Internet of Things [J]. Netinfo Security, 2021, 21(6): 1-10. |
| [10] | LU Honglin, WANG Liming. User-oriented Data Privacy Preserving Method for Federated Learning that Supports User Disconnection [J]. Netinfo Security, 2021, 21(3): 64-71. |
| [11] | WANG Li, LI Erxia, JI Yuchen, LI Xiaoyong. PUF-based Anti-physical Cloning RFID Security Authentication Protocol [J]. Netinfo Security, 2020, 20(8): 89-97. |
| [12] | SUN Ziwen, ZHANG Xiangyang. Large-scale Mobile RFID System Shamir’s Key Sharing PUF Security Authentication Protocol [J]. Netinfo Security, 2020, 20(6): 26-35. |
| [13] | WANG Rong, MA Chunguang, WU Peng. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [14] | Yongshuang WEI, Jianhua CHEN, Yongmei WEI. Security Authentication Protocol for RFID/NFC Based on Elliptic Curve Cryptography [J]. Netinfo Security, 2019, 19(12): 64-71. |
| [15] | Wenjiang HAO, Fei SONG, Yueliang WAN. Research on Security Authentication Protocol for Wearable Police Devices [J]. Netinfo Security, 2018, 18(9): 25-29. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||