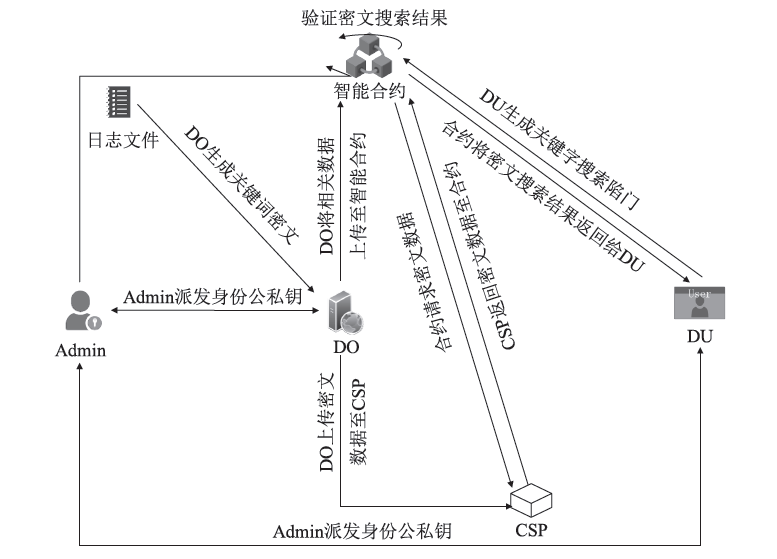
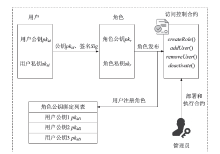
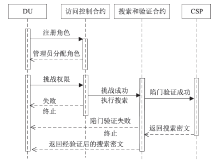
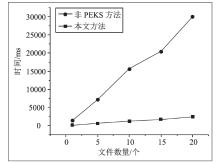
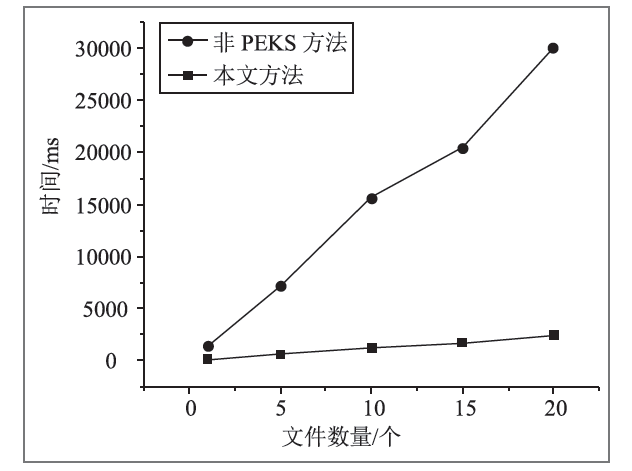
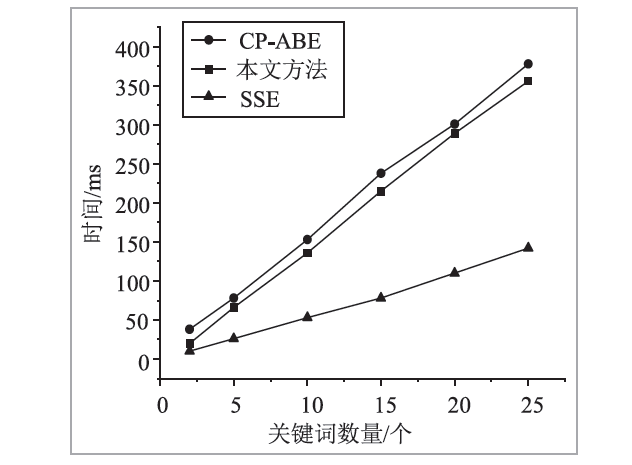
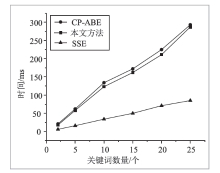
| [1] |
LIAO Xiangke, LI Shanshan, DONG Wei, et al. Survey on Log Research of Large Scale Software System[J]. Journal of Software, 2016, 27(8): 1934-1947.
|
|
廖湘科, 李姗姗, 董威, 等. 大规模软件系统日志研究综述[J]. 软件学报, 2016, 27(8):1934-1947.
|
| [2] |
WANG Cong, REN Kui, LOU Wenjing, et al. Toward Publicly Auditable Secure Cloud Data Storage Services[J]. IEEE Network, 2010, 24(4): 19-24.
doi: 10.1109/MNET.2010.5510914
URL
|
| [3] |
DO H G, NG W K. Blockchain-Based System for Secure Data Storage with Private Keyword Search[C]// IEEE. 2017 IEEE World Congress on Services(SERVICES). New York: IEEE, 2017: 90-93.
|
| [4] |
POURMAJIDI W, MIRANSKYY A. Logchain: Blockchain-Assisted Log Storage[C]// IEEE. IEEE 11th International Conference on Cloud Computing(CLOUD). New York: IEEE, 2018: 978-982.
|
| [5] |
LV Jianfu, LAI Yingxu, LIU Jing. Log Security Storage and Retrieval Based on Combination of on-Chain and off-Chain[J]. Computer Science, 2020, 47(3): 298-303.
|
|
吕建富, 赖英旭, 刘静. 基于链上链下相结合的日志安全存储与检索[J]. 计算机科学, 2020, 47(3):298-303.
|
| [6] |
BONEH D, CRESCENZO G D, OSTROVSKY R, et al. Public Key Encryption with Keyword Search[C]// Springer. International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2004: 506-522.
|
| [7] |
LI Huige, TIAN Haibo, ZHANG Fangguo, et al. Blockchain-Based Searchable Symmetric Encryption Scheme[J]. Computers & Electrical Engineering, 2019, 73: 32-45.
|
| [8] |
DU Ruizhong, TAN Ailun, TIAN Junfeng. Public Key Searchable Encryption Scheme Based on Blockchain[J]. Journal on Communications, 2020, 41(4): 114-122.
|
|
杜瑞忠, 谭艾伦, 田俊峰. 基于区块链的公钥可搜索加密方案[J]. 通信学报, 2020, 41(4): 114-122.
|
| [9] |
CHEN Lanxiang, LEE W K, CHANG C C, et al. Blockchain Based Searchable Encryption for Electronic Health Record Sharing[J]. Future Generation Computer Systems, 2019, 95: 420-429.
doi: 10.1016/j.future.2019.01.018
URL
|
| [10] |
AZARIA A, EKBLAW A, VIEIRA T, et al. Medrec: Using Blockchain for Medical Data Access and Permission Management[C]// IEEE. 2nd International Conference on Open and Big Data(OBD). New York:IEEE, 2016: 25-30.
|
| [11] |
FERRAIOLO D, CUGINI J, KUHN D R. Role-Based Access Control(RBAC): Features and Motivations[EB/OL]. [2021-12-11]. https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=916537.
|
| [12] |
DING Yi, JIN Jun, ZHANG Jinglun, et al. SC-RBAC: A Smart Contract Based RBAC Model for DApps[C]// Springer. International Conference on Human Centered Computing. Heidelberg: Springer, 2019: 75-85.
|
| [13] |
ZHANG Liang, ZHANG Hanlin, YU Jia, et al. Blockchain-Based Two-Party Fair Contract Signing Scheme[J]. Information Sciences, 2020, 535(11): 142-155.
doi: 10.1016/j.ins.2020.05.054
URL
|
| [14] |
YANG Yang, LIN Hongrui, LIU Ximeng, et al. Blockchain-Based Verifiable Multi-Keyword Ranked Search on Encrypted Cloud with Fair Payment[J]. IEEE Access, 2019, 7: 140818-140832.
doi: 10.1109/ACCESS.2019.2943356
|
| [15] |
YAN Xixi, YUAN Xiaohan, TANG Yongli, et al. Verifiable Attribute-Based Searchable Encryption Scheme Based on Blockchain[J]. Journal on Communications, 2020, 41(2): 187-198.
|
|
闫玺玺, 原笑含, 汤永利, 等. 基于区块链且支持验证的属性基搜索加密方案[J]. 通信学报, 2020, 41(2):187-198.
|