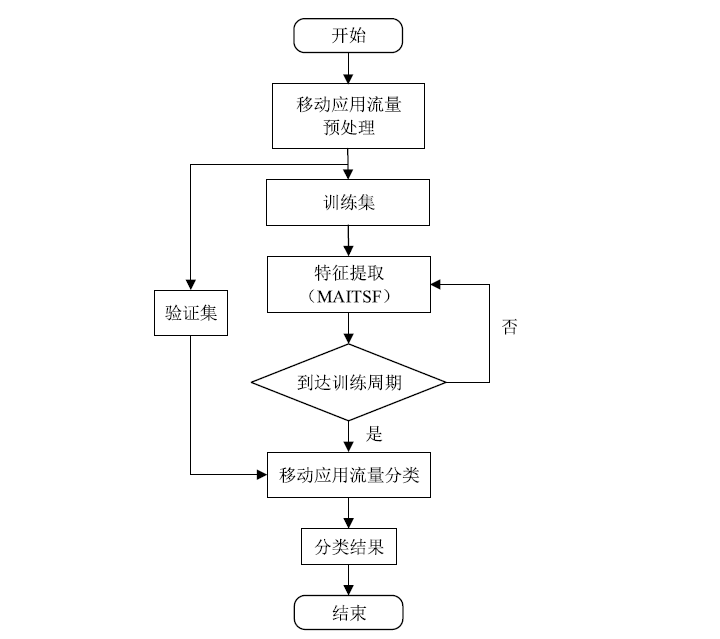
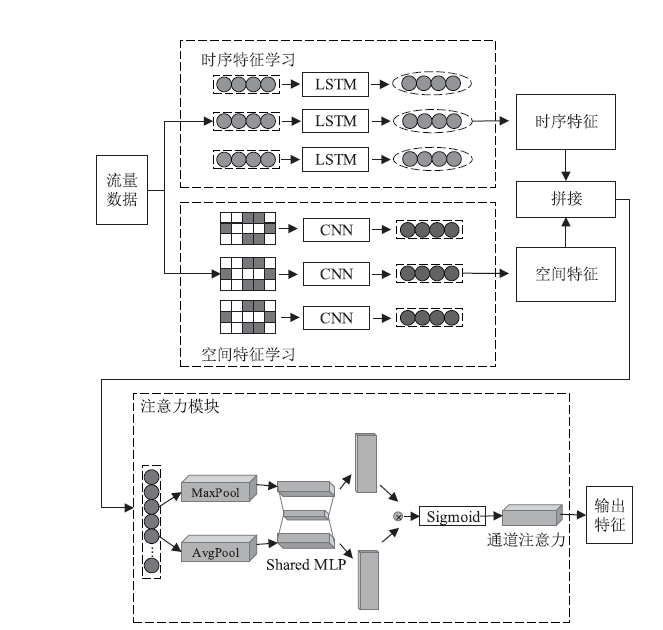
Netinfo Security ›› 2022, Vol. 22 ›› Issue (7): 18-26.doi: 10.3969/j.issn.1671-1122.2022.07.003
Previous Articles Next Articles
Mobile Traffic Application Recognition Based on Multi-Feature Fusion
LIU Guangjie, DUAN Kun( ), ZHAI Jiangtao, QIN Jiayu
), ZHAI Jiangtao, QIN Jiayu
- School of Electronic & Information Engineering, Nanjing University of Information Science & Technology, Nanjing 210044, China
-
Received:2022-03-12Online:2022-07-10Published:2022-08-17 -
Contact:DUAN Kun E-mail:duankun0608@163.com
CLC Number:
Cite this article
LIU Guangjie, DUAN Kun, ZHAI Jiangtao, QIN Jiayu. Mobile Traffic Application Recognition Based on Multi-Feature Fusion[J]. Netinfo Security, 2022, 22(7): 18-26.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.07.003
| 公开数据集 | 数据量/条 | 比例 | 实际数据集 | 数据量/条 | 比例 |
|---|---|---|---|---|---|
| ILoveHue | 43473 | 11.59% | 12306 | 34192 | 7.46% |
| Video call | 46866 | 12.51% | 百度地图 | 50990 | 11.12% |
| Bookmate | 37539 | 10.02% | 大麦网 | 57933 | 12.53% |
| Medicalid Free | 30285 | 8.08% | 大众点评 | 53352 | 11.52% |
| Lifehack Cheatsheet:A lifehacker app | 55612 | 14.83% | 饿了么 | 51455 | 11.22% |
| Instant Gaming | 28017 | 7.48% | 返利网 | 42568 | 9.28% |
| Knight Dark Gothic Wallpaper | 35540 | 9.48% | 马蜂窝 | 36259 | 7.91% |
| Apex Launcher | 34448 | 9.19% | 美团外卖 | 38438 | 8.61% |
| Access Phone | 28145 | 7.51% | 亚马逊 | 45622 | 9.94% |
| Freedom Mobile My Count | 34861 | 9.31% | 前程无忧 | 47720 | 10.41% |
| 总计 | 374786 | 100% | — | 458529 | 100% |
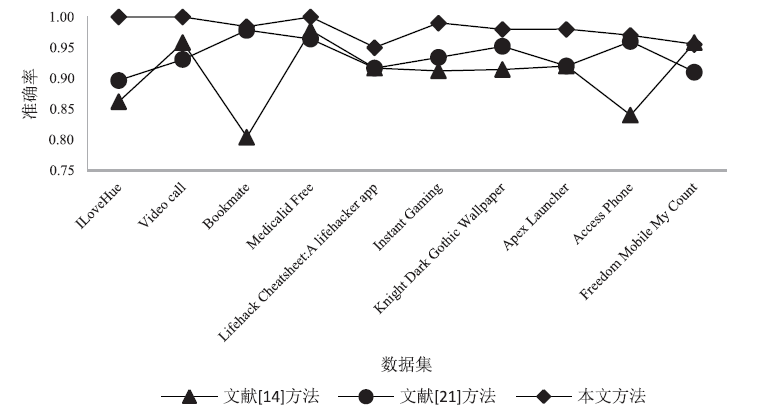
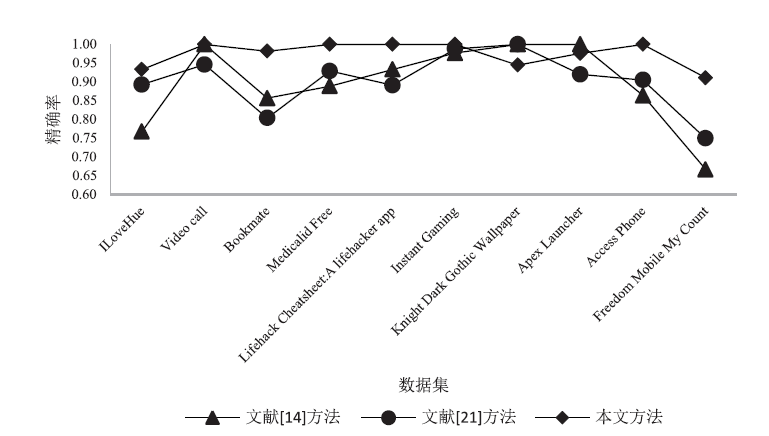
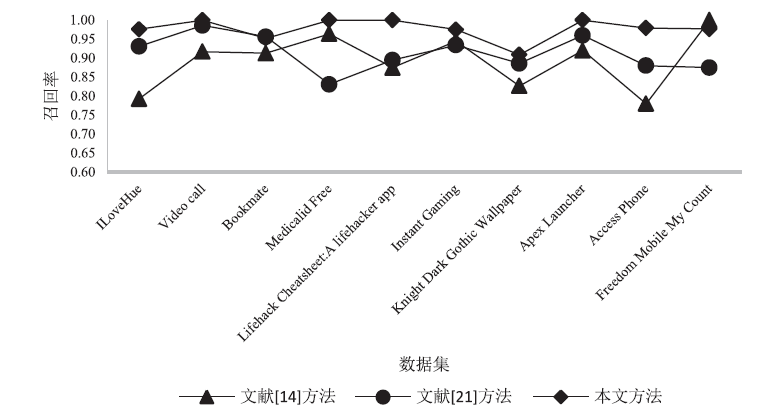
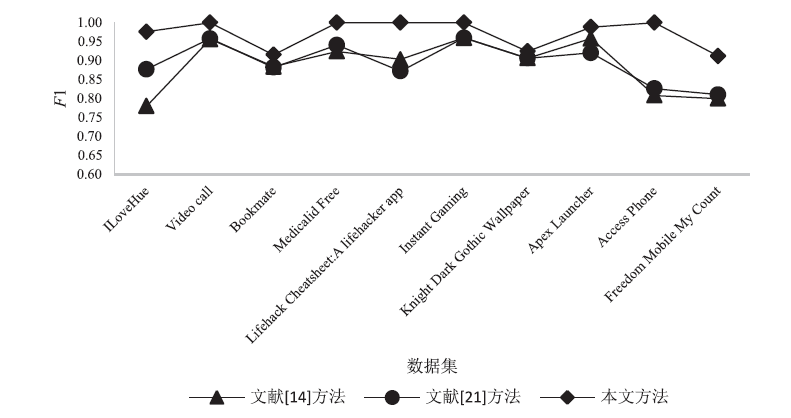
| 公开数据集 | 精确率 | 召回率 | F1 |
|---|---|---|---|
| ILoveHue | 0.93 | 0.98 | 0.97 |
| Video call | 1.00 | 1.00 | 1.00 |
| Bookmate | 0.98 | 0.95 | 0.95 |
| Medicalid Free | 1.00 | 1.00 | 1.00 |
| Lifehack Cheatsheet:A lifehacker app | 1.00 | 1.00 | 1.00 |
| Instant Gaming | 1.00 | 0.98 | 1.00 |
| Knight Dark Gothic Wallpaper | 0.95 | 0.92 | 0.93 |
| Apex Launcher | 0.98 | 1.00 | 0.99 |
| Access Phone | 1.00 | 0.97 | 1.00 |
| Freedom Mobile My Count | 0.92 | 0.98 | 0.93 |
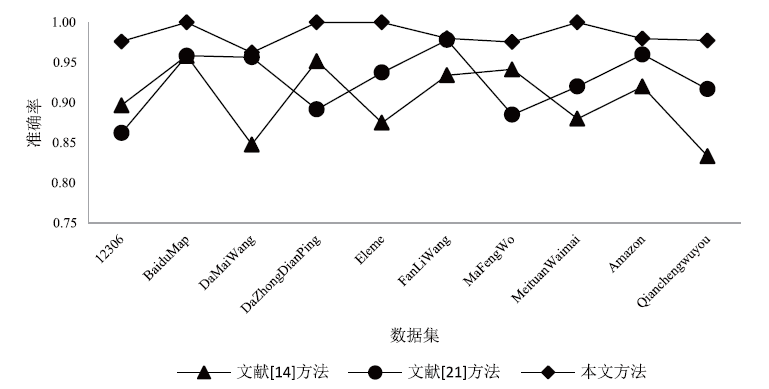
| 实际数据集 | 精确率 | 召回率 | F1 |
| 12306 | 0.98 | 1.00 | 0.99 |
| 百度地图 | 0.99 | 0.99 | 1.00 |
| 大麦网 | 1.00 | 0.98 | 0.99 |
| 大众点评 | 0.98 | 1.00 | 0.99 |
| 饿了么 | 1.00 | 1.00 | 1.00 |
| 返利网 | 1.00 | 0.99 | 1.00 |
| 马蜂窝 | 0.95 | 0.96 | 0.95 |
| 美团外卖 | 1.00 | 1.00 | 1.00 |
| 亚马逊 | 0.99 | 0.99 | 0.99 |
| 前程无忧 | 0.95 | 0.94 | 0.95 |
| [1] |
GREIS J, YUSHCHENKO A, VOGEL D, et al. Automated Identification of Vulnerable Devices in Networks Using Traffic Data and Deep Learning[J]. International Journal of Information Privacy, Security and Integrity, 2021, 5(1): 1-17.
doi: 10.1504/IJIPSI.2021.119166 URL |
| [2] | XUE Wenlong, YU Jiong, GUO Zhiqi, et al. End-to-End Encrypted Traffic Classification Based on Feature Fusion Convolutional Neural Network[J]. Computer Engineering and Applications, 2021, 57(18): 114-121. |
| 薛文龙, 于炯, 郭志琦, 等. 基于特征融合卷积神经网络的端到端加密流量分类[J]. 计算机工程与应用, 2021, 57(18): 114-121. | |
| [3] | YAN Haonan, LI Hui, XIAO Mingchi, et al. PGSM-DPI: Precisely Guided Signature Matching of Deep Packet Inspection for Traffic Analysis[C]// IEEE. 2019 IEEE Global Communications Conference (GLOBECOM). New York: IEEE, 2019: 1-6. |
| [4] | LIU Chang, CAO Zigang, XIONG Gang, et al. MaMPF: Encrypted Traffic Classification Based on Multi-Attribute Markov Probability Fingerprints[C]// IEEE. 2018 IEEE/ACM 26th International Symposium on Quality of Service (IWQoS). New York: IEEE, 2018: 1-10. |
| [5] | REZAEI S, LIU Xin. Deep Learning for Encrypted Traffic Classification: An Overview[J]. IEEE Communications Magazine, 2019, 57(5): 76-81. |
| [6] | WANG Pan, CHEN Xuejiao, YE Feng, et al. A Survey of Techniques for Mobile Service Encrypted Traffic Classification Using Deep Learning[J]. IEEE Access, 2019(7): 54024-54033. |
| [7] | TONGAONKAR A, DAI Shuaifu, NUCCI A, et al. Understanding Mobile App Usage Patterns Using in-App Advertisements[C]// Springer. International Conference on Passive and Active Network Measurement. Heidelberg: Springer, 2013: 63-72. |
| [8] | TREVISAN M, DRAGO I, MELLIA M, et al. Towards Web Service Classification Using Addresses and DNS[C]// IEEE. 2016 International Wireless Communications and Mobile Computing Conference (IWCMC). New York: IEEE, 2016: 38-43. |
| [9] | ALAN H F, KAUR J. Can Android Applications be Identified Using only TCP/IP Headers of Their Launch Time Traffic?[C]// ACM. 9th ACM Conference on Security & Privacy in Wireless and Mobile Networks. New York: ACM, 2016: 61-66. |
| [10] | WANG Wei, SHENG Yiqiang, WANG Jinlin, et al. HAST-IDS: Learning Hierarchical Spatial-Temporal Features Using Deep Neural Networks to Improve Intrusion Detection[J]. IEEE Access, 2017(6): 1792-1806. |
| [11] | WANG Yong, ZHOU Huiyi, FENG Hao, et al. Network Traffic Classification Method Basing on CNN[J]. Journal on Communications, 2018, 39(1): 14-23. |
| 王勇, 周慧怡, 俸皓, 等. 基于深度卷积神经网络的网络流量分类方法[J]. 通信学报, 2018, 39(1): 14-23. | |
| [12] | CHEN Zhengyang, YU Bowen, ZHANG Yu, et al. Automatic Mobile Application Traffic Identification by Convolutional Neural Networks[C]// IEEE. 2016 IEEE Trustcom/BigDataSE/ISPA. New York: IEEE, 2016: 301-307. |
| [13] | WANG Wei, ZHU Ming, ZENG Xuewen, et al. Malware Traffic Classification Using Convolutional Neural Network for Representation Learning[C]// IEEE. 2017 International Conference on Information Networking (ICOIN). New York: IEEE, 2017: 712-717. |
| [14] | WANG Wei, ZHU Ming, WANG Jinlin, et al. End-to-End Encrypted Traffic Classification with One-Dimensional Convolution Neural Networks[C]// IEEE. 2017 IEEE International Conference on Intelligence and Security Informatics (ISI). New York: IEEE, 2017: 43-48. |
| [15] | LASHKARI A H, KADIR A F A, GONZALEZ H, et al. Towards a Network-Based Framework for Android Malware Detection and Characterization[C]// IEEE. 2017 15th Annual Conference on Privacy, Security and Trust (PST). New York: IEEE, 2017: 233-249. |
| [16] | XU Hongping, MA Zewen, YI Hang, et al. Network Traffic Anomaly Detection Technology Based on Convolutional Recurrent Neural Network[J]. Netinfo Security, 2021, 21(7): 54-62. |
| 徐洪平, 马泽文, 易航, 等. 基于卷积循环神经网络的网络流量异常检测技术[J]. 信息网络安全, 2021, 21(7): 54-62. | |
| [17] |
LOTFOLLAHI M, ZADE R S H, SIAVOSHANI M J, et al. Deep Packet: A Novel Approach for Encrypted Traffic Classification Using Deep Learning[J]. Soft Computing, 2020, 24(3): 1999-2012.
doi: 10.1007/s00500-019-04030-2 URL |
| [18] | GUO Yanhua, SUN Lei, ZHANG Zhihong, et al. Algorithm Research on Improving Activation Function of Convolutional Neural Networks[C]// IEEE. 2019 Chinese Control and Decision Conference (CCDC). New York: IEEE, 2019: 3582-3586. |
| [19] | ZHANG Guanghua, YAN Fengru, ZHANG Dongwen, et al. Insider Threat Detection Model Based on LSTM-Attention[J]. Netinfo Security, 2022, 22(2): 1-10. |
| 张光华, 闫风如, 张冬雯, 等. 基于LSTM-Attention的内部威胁检测模型[J]. 信息网络安全, 2022, 22(2): 1-10. | |
| [20] |
SHAPIRA T, SHAVITT Y. FlowPic: A Generic Representation for Encrypted Traffic Classification and Applications Identification[J]. IEEE Transactions on Network and Service Management, 2021, 18(2): 1218-1232.
doi: 10.1109/TNSM.2021.3071441 URL |
| [21] | ZOU Zhuang, GE Jingguo, ZHENG Hongbo, et al. Encrypted Traffic Classification with a Convolutional Long Short-Term Memory Neural Network[C]// IEEE. 2018 IEEE 20th International Conference on High Performance Computing and Communications. New York: IEEE, 2018: 329-334. |
| [1] | WANG Haoyang, LI Wei, PENG Siwei, QIN Yuanqing. An Intrusion Detection Method of Train Control System Based on Ensemble Learning [J]. Netinfo Security, 2022, 22(5): 46-53. |
| [2] | LIU Feng, YANG Chengyi, YU Xincheng, QI Jiayin. Spectral Graph Convolutional Neural Network for Decentralized Dual Differential Privacy [J]. Netinfo Security, 2022, 22(2): 39-46. |
| [3] | LI Yanlin, CAI Manchun, LU Tianliang, XI Rongkang. A Website Fingerprinting Attack Method via Convolutional Neural Network Optimized by Genetic Algorithm [J]. Netinfo Security, 2021, 21(9): 59-66. |
| [4] | PAN Xiaoqin, DU Yanhui. Forged Voice Identification Method Based on Feature Fusion and Multi-channel GRU [J]. Netinfo Security, 2021, 21(10): 1-7. |
| [5] | XU Guotian, SHENG Zhenwei. DGA Malicious Domain Name Detection Method Based on Fusion of CNN and LSTM [J]. Netinfo Security, 2021, 21(10): 41-47. |
| [6] | MA Xiao, CAI Manchun, LU Tianliang. Malicious Domain Name Training Data Generation Technology Based on Improved CNN Model [J]. Netinfo Security, 2021, 21(10): 69-75. |
| [7] | TAN Ruhan, ZUO Liming, LIU Ergen, GUO Li. Malicious Code Detection Based on Image Feature Fusion [J]. Netinfo Security, 2021, 21(10): 90-95. |
| [8] | WANG Xiangyi, ZHANG Jian. Abnormal Behavior Detection of Virtualization Platform Based on Image and Machine Learning [J]. Netinfo Security, 2020, 20(9): 92-96. |
| [9] | LIU Jing, ZHANG Xueqian, LIU Quanming. Research on Captcha Recognition of Lightweight Convolutional Neural Network with Gabor [J]. Netinfo Security, 2020, 20(7): 77-84. |
| [10] | ZHANG Leihua, HUANG Jin, ZHANG Tao, WANG Shengyu. Portrait Intelligent Analysis Application and Algorithm Optimization in Video Investigation [J]. Netinfo Security, 2020, 20(5): 88-93. |
| [11] | GU Zhaojun, HAO Jintao, ZHOU Jingxian. Classification of Malicious Network Traffic Based on Improved Bilinear Convolutional Neural Network [J]. Netinfo Security, 2020, 20(10): 67-74. |
| [12] | Meng LI. Mobile Application Security Construction of the National Medical Products Administration [J]. Netinfo Security, 2019, 19(9): 46-50. |
| [13] | Qing HU, Benyong LIU. Speaker Recognition Algorithm Based on Convolutional Neural Networks [J]. Netinfo Security, 2016, 16(4): 55-60. |
| [14] | Lianyin WANG, Yinghao WEI, Shuangqiu XING, Chao LU. Research and Application on Cloud Security Management Service for Intelligent Terminal [J]. Netinfo Security, 2016, 16(10): 15-20. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||