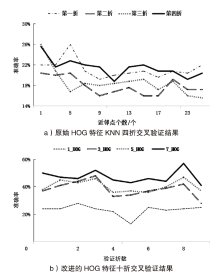
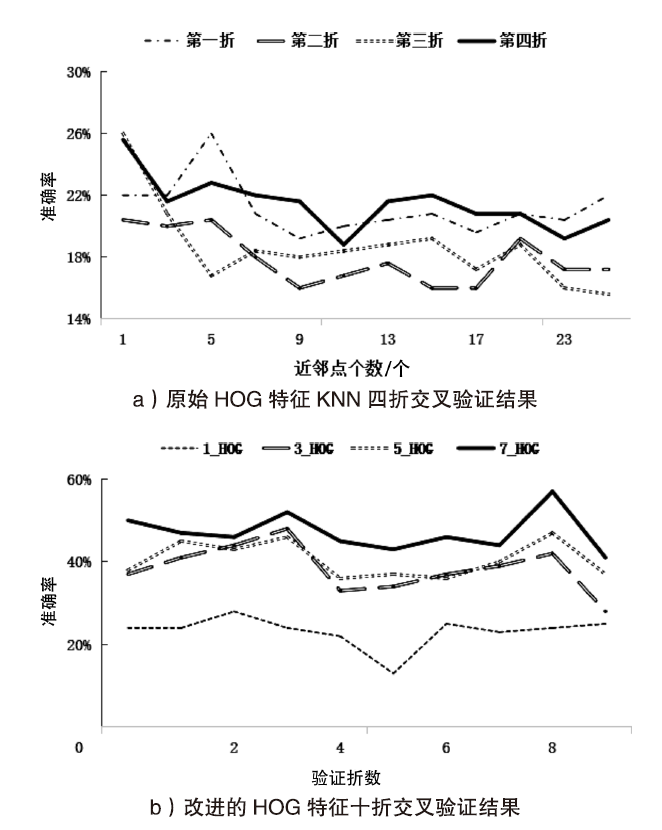
| [1] |
SZOMSZOR M N, CANTADOR I, ALANI H. Correlating User Profiles from Multiple Folksonomies [C]//ACM. 19th ACM Conference on Hypertext and Hypermedia, June 19-21, 2008, Pittsburgh, USA. New York: ACM, 2008: 33-42.
|
| [2] |
BAN M. Ransomware Detection Using Random Forest Technique[J]. ICT Express, 2020, 6(4):325-331.
doi: 10.1016/j.icte.2020.11.001
URL
|
| [3] |
TAKEUCHI Y, SAKAI K, FUKUMOTO S. Detecting Ransomware Using Support Vector Machines[C]//ICPP. 47th International Conference on Parallel Processing Companion (ICPP'18), August 13-16, 2018, Eugene, USA. New York: ACM, 2018(1): 1-6.
|
| [4] |
FIRDAUSI I, LIM C, ERWIN A, et al. Analysis of Machine Learning Techniques Used in Behavior-based Malware Detection[M]. Piscataway: IEEE Computer Society, 2010.
|
| [5] |
SHAUKAT S K, RIBEIRO V J. RansomWall: A Layered Defense System Against Cryptographic Ransomware Attacks Using Machine Learning [C]//IEEE. 2018 10th International Conference on Communication Systems & Networks (COMSNETS), January 3-7, 2018, Bengaluru, India. Piscataway: IEEE, 2018: 356-363.
|
| [6] |
SUBEDI K, BUDHATHOKI D, DASGUPTA D. Forensic Analysis of Ransomware Families Using Static and Dynamic Analysis [C]//IEEE. 2018 IEEE Security and Privacy Workshops (SPW), May 24-26, 2018, San Francisco, USA. Piscataway: IEEE, 2018: 180-185.
|
| [7] |
KANG Minggu, POOSANKAM P, YIN Heng. Renovo: A Hidden Code Extractor for Packed Executables [C]//ACM. 5th ACM Workshop on Recurring Malcode, November 2-3, 2007, Alexandria, USA. New York: ACM, 2007: 46-53.
|
| [8] |
ROYAL P, HALPIN M, DAGON D, et al. PolyUnpack: Automating the Hidden-code Extraction of Unpack-executing Malware [C]//IEEE. 22nd Computer Security Applications Conference, December 11-15, 2006, Miami, USA. Piscataway: IEEE, 2006: 289-300.
|
| [9] |
CUI Hong, YU Bo, FANG Ying. Analytical Method of High-dimensional Feature Fusion for Malware Classification[J]. Application Research of Computers, 2017, 34(4):1120-1123, 1150.
|
|
崔弘, 喻波, 方莹. 恶意代码分类的一种高维特征融合分析方法[J]. 计算机应用研究, 2017, 34(4):1120-1123, 1150.
|
| [10] |
JIANG Qianyu, WANG Fengying, JIA Lipeng. Malware Detection Method Based on Perceptual Hash Algorithm and Feature Fusion[J]. Journal of Computer Applications, 2021, 41(3):780-785.
|
|
姜倩玉, 王凤英, 贾立鹏. 基于感知哈希算法和特征融合的恶意代码检测方法[J]. 计算机应用, 2021, 41(3):780-785.
|
| [11] |
NATARAJ L, KARTHIKEYAN S, JACOB G, et al. Malware Images: Visualization and Automatic Classification[C]//VizSec. 8th International Symposium on Visualization for Cyber Security (VizSec'11), July 20-21, 2011, New York, USA. New York: ACM, 2011(4): 1-7.
|
| [12] |
HAN Xiaoguang, QU Wu, YAO Xuanxia, et al. Research on Malicious Code Variants Detection Based on Texture Fingerprint[J]. Journal on Communications, 2014, 35(8):125-136.
|
|
韩晓光, 曲武, 姚宣霞, 等. 基于纹理指纹的恶意代码变种检测方法研究[J]. 通信学报, 2014, 35(8):125-136.
|
| [13] |
LOWE D G. Distinctive Image Features from Scale-invariant Keypoints[J]. International Journal of Computer Vision, 2004, 60(2):91-110.
doi: 10.1023/B:VISI.0000029664.99615.94
URL
|
| [14] |
DALAL N, TRIGGS B. Histograms of Oriented Gradients for Human Detection[C]//IEEE. IEEE Computer Society Conference on Computer Vision and Pattern Recognition (CVPR'5), June 20-25, 2005, San Diego, USA. Piscataway: IEEE, 2005(1): 886-893.
|
| [15] |
LIU Zhigang, LI Deren, QIN Qianqing, et al. An Analytical Overview of Methods for Multi-category Support Vector Machines[J]. Computer Engineering and Applications, 2004, 40(7):10-13, 65.
|
|
刘志刚, 李德仁, 秦前清, 等. 支持向量机在多类分类问题中的推广[J]. 计算机工程与应用, 2004, 40(7):10-13, 65.
|
 ), ZUO Liming1,2, LIU Ergen1, GUO Li1,2
), ZUO Liming1,2, LIU Ergen1, GUO Li1,2