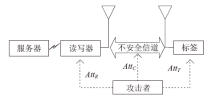
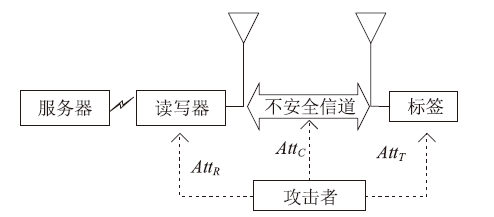
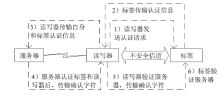
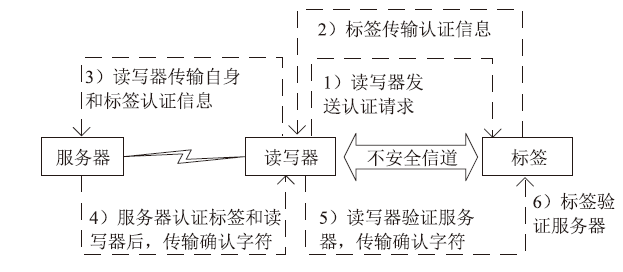
| [1] |
BONO S, GREEN M, STUBBLEFIELD A, et al. Security Analysis of a Cryptographically-enabled RFID Device[EB/OL]. https://www.researchgate.net/publication/228651694_Security_analysis_of_a_cryptographically-enabled_RFID_device, 2019 -8-9.
|
| [2] |
DOSS R, SUNDARESAN S, ZHOU W. Apractical Quadratic Residues Based Scheme for Authentication and Privacy in Mobile RFID Systems[J]. Ad Hoc Networks, 2013,11(1):383-396.
|
| [3] |
YANG Yulong, PENG Changgen, ZHOU Zhou. Mobile RFID Security Authentication Protocol Based on Edwards Curve[J]. Journal of Communications, 2014,35(11):132-137.
|
|
杨玉龙, 彭长根, 周洲, 等. 基于Edwards曲线的移动RFID安全认证协议[J]. 通信学报, 2014,35(11):132-137.
|
| [4] |
SANDHYA M, RANGASWAMY T R. A Secure and Effecient Authentication Protocol for Mobile RFID Systems[J]. Journal of Digital Information Management, 2011,9(3):99-105.
|
| [5] |
LIU Peng, ZHANG Changhong, OU Qingyu. Hash Function-based Mobile Radio Frequency Identification Mutual Authentication Security Protocol Involves[J]. Computer Application, 2013,33(5):1350-1352.
|
|
刘鹏, 张昌宏, 欧庆于. 基于Hash函数的移动射频识别互认证安全协议涉及[J]. 计算机应用, 2013,33(5):1350-1352.
|
| [6] |
WANG Guowei, JIA Zongpu, PENG Weiping. Mobile RFID Two-way Authentication Protocol Based on Dynamic Shared Key[J]. Journal of Electronics, 2017,45(3):612-618.
|
|
王国伟, 贾宗璞, 彭维平. 基于动态共享密钥的移动RFID双向认证协议[J]. 电子学报, 2017,45(3):612-618.
|
| [7] |
SUN Ziwen, LI Song. Lightweight RFID Mobile Authentication Protocol Using PUF to Protect Location Privacy[J]. Computer Science and Exploration, 2019,13(3):418-428.
|
|
孙子文, 李松. 采用PUF保护位置隐私的轻量级RFID移动认证协议[J]. 计算机科学与探索, 2019,13(3):418-428.
|
| [8] |
PAPPU R. Physical One-way Function[EB/OL]. https://www.docin.com/p-1684681622.html, 2019 -8-11.
|
| [9] |
CHIOU S Y, CHANG S Y. An Enhanced Authentication Scheme in Mobile RFID System[EB/OL]. https://www.researchgate.net/publication/321861476_An_Enhanced_Authentication_Scheme_in_Mobile_RFID_System, 2019 -8-12.
|
| [10] |
RONG Huigui, MO Jinxia, CHANG Bingguo, et al. Key Distribution and Recovery Algorithm Based on Shamir Secret Sharing[J]. Journal of Communications, 2015,36(3):60-69.
|
|
荣辉桂, 莫进侠, 常炳国, 等. 基于Shamir秘密共享的密钥分发与恢复算法[J]. 通信学报, 2015,36(3):60-69.
|
| [11] |
VAUDENAY S. On privacy models for RFID[M]. Advances in Cryptology-ASIACRYPT 2007. Heidelberg: Springer, 2007: 68-87.
|
| [12] |
SHAMIR A. How to Share A Secret[J]. Communications of the ACM, 1979,22(11):612-613.
|
| [13] |
LIU Y, EZERMAN M F, WANG H. Double Verification Protocol via Secret Sharing for Low-cost RFID Tags[EB/OL]. https://www.onacademic.com/detail/journal_1000040419206110_45fd.html, 2019 -8-11.
|
| [14] |
ARMKNECHT F, MAES R, SADEGHI A, et al. A Formalization of the Security Features of Physical Functions [C]// 2011 IEEE Symposium. Security and Privacy, May 22-25, 2011, Berkeley, CA, USA. New Jersey: IEEE, 2011: 397-412.
|
| [15] |
LI Changting, ZHANG Qinglong, LIU Zongbin. FROPUF: Extract More Entropy from FPGA-based Oscillator Ring PUF[J]. Journal of Information Security, 2018,3(1):16-30.
|
| [16] |
ALAGHEBAND M R, AREF M R. Simulation-based Traceability Analysis of RFID Authentication Protocols[M]. California: Kluwer Academic Publishers, 2014.
|
 ), ZHANG Xiangyang1
), ZHANG Xiangyang1