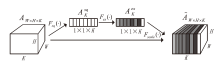
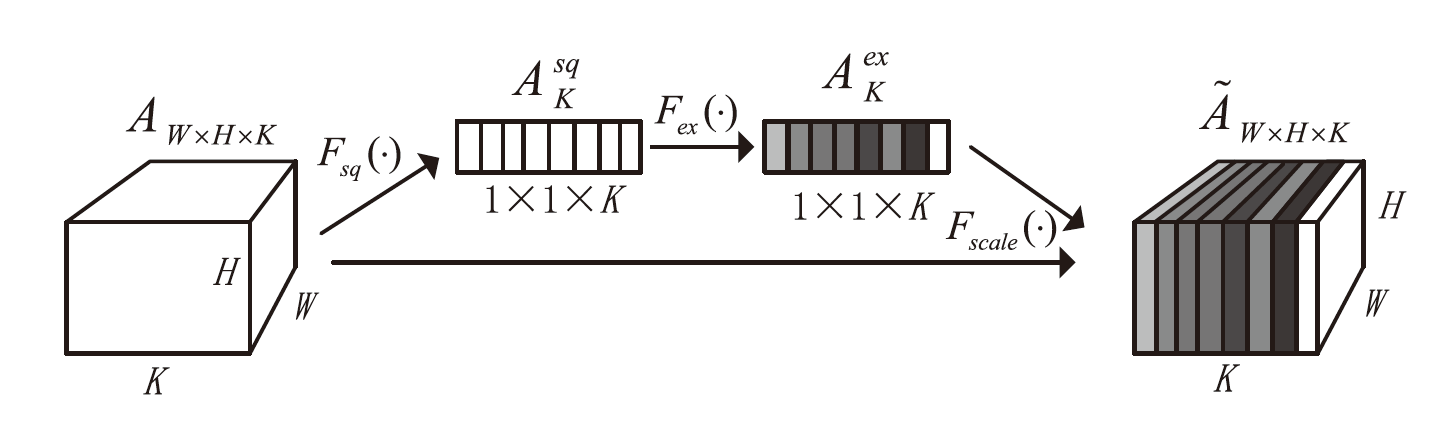
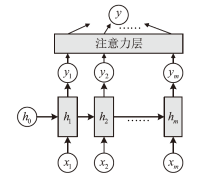
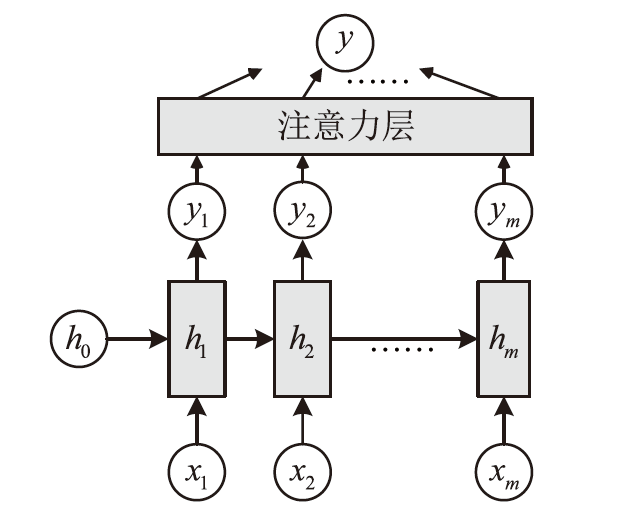
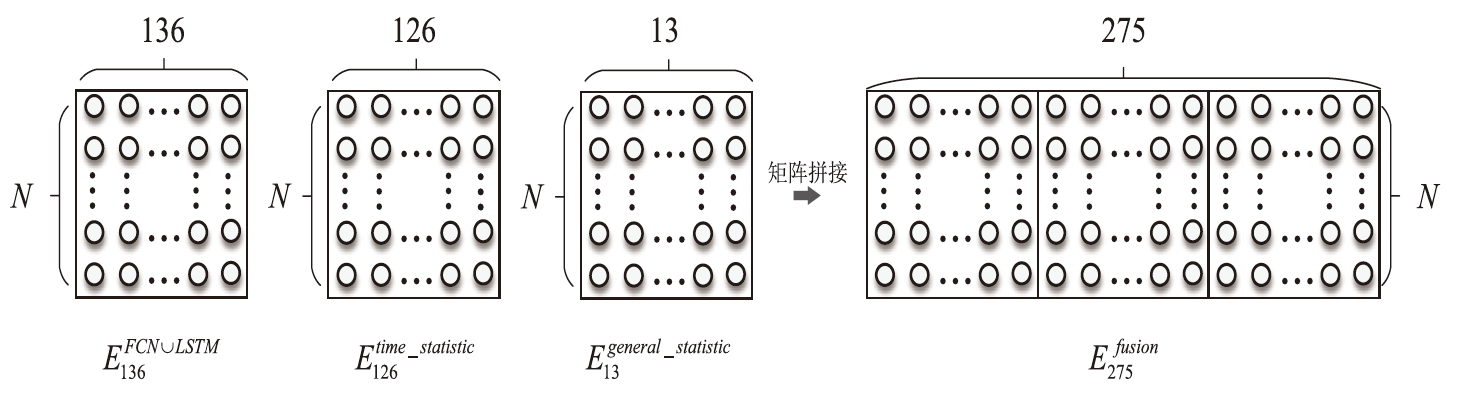
| [1] |
STEVANOVIC M, PEDERSEN J M, D'ALCONZO A, et al. On the Ground Truth Problem of Malicious DNS Traffic Analysis[J]. Computers & Security, 2015, 55: 142-158.
doi: 10.1016/j.cose.2015.09.004
URL
|
| [2] |
XU Guotian, SHENG Zhenwei. DGA Malicious Domain Name Detection Method Based on Fusion of CNN and LSTM[J]. Netinfo Security, 2021, 21(10): 41-47.
|
|
徐国天, 盛振威. 基于融合CNN与LSTM的DGA恶意域名检测方法[J]. 信息网络安全, 2021, 21(10): 41-47.
|
| [3] |
SCHUPPEN S, TEUBERT D, HERRMANN P, et al. FANCI: Feature-Based Automated NXDomain Classification and Intelligence[C]// ACM. In Proceedings of the 27th USENIX Conference on Security Symposium (SEC'18). Berkeley: USENIX Association, 2018: 1165-1181.
|
| [4] |
ZHOU Changling, CHEN Kai, GONG Xuxiao, et al. Detection of Fast-Flux Domains Based on Passive DNS Analysis[J]. Acta Scientiarum Naturalium Universitatis Pekinensis, 2016, 52(3): 396-402.
|
|
周昌令, 陈恺, 公绪晓, 等. 基于Passive DNS的速变域名检测[J]. 北京大学学报:自然科学版, 2016, 52(3): 396-402.
|
| [5] |
HAN Chunyu, ZHANG Yongzheng, ZHANG Yu. Fast-Flucos: Malicious Domain Name Detection Method for Fast-Flux Based on DNS Traffic[J]. Journal on Communications, 2020, 41(5): 37-47.
doi: 10.11959/j.issn.1000-436x.2020094
|
|
韩春雨, 张永铮, 张玉. Fast-Flucos:基于DNS流量的fast-flux恶意域名检测方法[J]. 通信学报, 2020, 41(5): 37-47.
doi: 10.11959/j.issn.1000-436x.2020094
|
| [6] |
TRUONG D T, CHENG Guang. Detecting Domain-Flux Botnet Based on DNS Traffic Features in Managed Network[J]. Security and Communication Networks, 2016, 9(14): 2338-2347.
doi: 10.1002/sec.v9.14
URL
|
| [7] |
CHO D X, NAM H H. A Method of Monitoring and Detecting APT Attacks Based on Unknown Domains[J]. Procedia Computer Science, 2019, 150: 316-323.
doi: 10.1016/j.procs.2019.02.058
URL
|
| [8] |
RAHBARINIA B, PERDISCI R, ANTONAKAKIS M. Segugio: Efficient Behavior-Based Tracking of Malware-Control Domains in Large ISP Networks[C]// IEEE. 45th Annual IEEE/IFIP International Conference on Dependable Systems and Networks. New York: IEEE, 2015: 403-414.
|
| [9] |
MA Zhen, LI Qiang, MENG Xiangyu. Discovering Suspicious APT Families through a Large-Scale Domain Graph in Information-Centric IoT[J]. IEEE Access, 2019, 7: 13917-13926.
doi: 10.1109/ACCESS.2019.2894509
|
| [10] |
WANG Xiaoqi, LI Qiang, YAN Guanghua, et al. Detection of Covert and Suspicious DNS Behavior in Advanced Persistent Threats[J]. Journal of Computer Research and Development, 2017, 54(10): 2334-2343.
|
|
王晓琪, 李强, 闫广华, 等. 高级持续性威胁中隐蔽可疑DNS行为的检测[J]. 计算机研究与发展, 2017, 54(10): 2334-2343.
|
| [11] |
ZHAO Guodong, XU Ke, XU Lei, et al. Detecting APT Malware Infections Based on Malicious DNS and Traffic Analysis[J]. IEEE Access, 2015, 3: 1132-1142.
doi: 10.1109/ACCESS.2015.2458581
URL
|
| [12] |
BILGE L, KIRDA E, KRUEGEL C, et al. EXPOSURE: Finding Malicious Domains Using Passive DNS Analysis[EB/OL]. [2023-04-12]. https://xueshu.baidu.com/usercenter/paper/show?paperid=bd8bbc9b0308c49ed70c2b50ecc94c49.
|
| [13] |
TAN Guolin, ZHANG Peng, LIU Qingyun, et al. Domainobserver: A lightweight Solution for Detecting Malicious Domains Based on Dynamic Time Warping[C]// Springer. International Conference on Computational Science. Berlin:Springer, 2018: 208-220.
|
| [14] |
KDOSHA O E, ROSENTHAL G, COHEN K, et al. REMaDD: Resource-Efficient Malicious Domains Detector in Large-Scale Networks[J]. IEEE Access, 2020, 8: 66327-66337.
doi: 10.1109/Access.6287639
URL
|
| [15] |
TAN Guolin, ZHANG Peng, ZHANG Lei, et al. Learning from Time Series with Outlier Correction for Malicious Domain Identification[C]// IEEE. 2019 IEEE International Symposium on Software Reliability Engineering Workshops (ISSREW). New York: IEEE, 2019: 42-46.
|
| [16] |
LONG J, SHELHAMER E, DARRELL T. Fully Convolutional Networks for Semantic Segmentation[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2015: 3431-3440.
|
| [17] |
HOCHREITER S, SCHMIDHUBER J. Long Short-Term Memory[J]. Neural Computation, 1997, 9(8): 1735-1780.
doi: 10.1162/neco.1997.9.8.1735
pmid: 9377276
|
 )
)