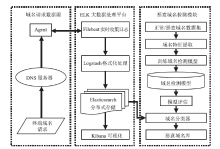
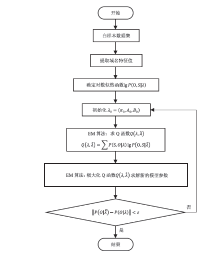
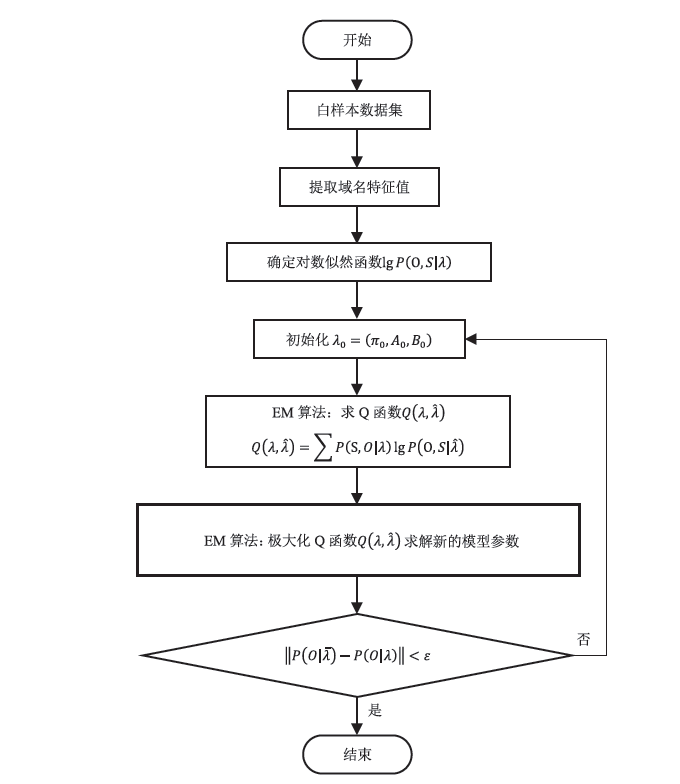
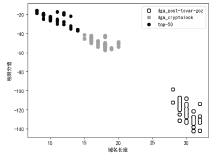
| [1] |
XU Guotian. Crack of Malicious Program Domain Name Generation Algorithm Based on DGA[J]. Netinfo Security, 2017, 17(9):4-8.
|
|
徐国天. 基于DGA的恶意程序域名生成算法破解[J]. 信息网络安全, 2017, 17(9):4-8.
|
| [2] |
McAfee Labs. Threats Report[EB/OL]. https://www.mcafee.com/enterprise/zh-cn/assets/reports/rp-quarterly-threats-nov-2020.pdf, 2020-11-13.
|
| [3] |
ACARALIA D, RAJARAJANA M, KOMNINOSA N, et al. Survey of Approaches and Features for the Identification of HTTP-based Botnet Traffic[J]. Journal of Network and Computer Applications, 2016, 16(76):1-15.
|
| [4] |
ZHAUNIAROVICH Y, KHALIL I, YU Ting, et al. A Survey on Malicious Domains Detection Through DNS Data Analysis[J]. ACM Computing Surveys, 2018, 51(4):1-35.
|
| [5] |
ZANG Xiaodong, GONG Jian, HU Xiaoyan. Malicious Domain Name Detection Based on AGD[J]. Journal on Communications, 2018, 39(7):15-25.
|
|
臧小东, 龚俭, 胡晓艳. 基于AGD的恶意域名检测[J]. 通信学报, 2018, 39(7):15-25.
|
| [6] |
JIN Jiandong, YANG Jia, ZHOU Changling, et al. Network Forensics Analysis on Email Scam Botnet[J]. Journal of Shenzhen University(Science & Engineering), 2020, 37(z1):78-83.
|
|
金建栋, 杨加, 周昌令, 等. 勒索欺诈邮件僵尸网络的检测与分析[J]. 深圳大学学报理工版, 2020, 37(z1):78-83.
|
| [7] |
THAPLIYAL M, BIJALWAN A, GARG N, et al. A Generic Process Model for Botnet Forensic Analysis[EB/OL]. https://www.atlantis-press.com/proceedings/cac2s-13/6285, 2013-04-24.
|
| [8] |
ANTONAKAKIS M, PERDISCI R, NADJI Y, et al. From Throw-away Traffic to Bots: Detecting the Rise of DGA-based Malware[EB/OL]. https://dl.acm.org/doi/10.5555/2362793.2362817, 2012-08-10.
|
| [9] |
SHARIFNYA R, ABADI M. DFBotKiller: Domain-flux Botnet Detection Basedon the History of Group Activities and Failures in DNS Traffic[J]. Digital Investigation, 2015, 13(12):15-26.
doi: 10.1016/j.diin.2015.02.002
URL
|
| [10] |
ZHAO Yue. Research on Botnet Detection Method Based on DNS Traffic Characteristics[D]. Tianjin: Tianjin University, 2016.
|
|
赵越. 基于DNS流量特征的僵尸网络检测方法研究[D]. 天津:天津大学, 2016.
|
| [11] |
WAJEEHA A. Why Botnets Persist: Designing Effective Technical and Policy Interventions[J]. MIT Internet Policy Research Initiative (IPRI), 2019, 23(2):1-5.
|
| [12] |
XIONG Yan, CHENG Chuanhu, WU Jianshuang, et al. Research on Premise Selection Technology Based on Machine Learning Classification Algorithm[J]. Netinfo Security, 2021, 21(11):9-16.
|
|
熊焰, 程传虎, 武建双, 等. 基于机器学习分类算法的前提选择技术研究[J]. 信息网络安全, 2021, 21(11):9-16.
|
| [13] |
LI Deqi, HU Dasha, LIU Yunxia, et al. Research on Command Control Channel of Botnet Based on Blockchain Technology[J]. Modern Computer, 2020, 49(8):30-36.
|
|
李德奇, 胡大裟, 刘云霞, 等. 基于区块链技术的僵尸网络命令控制信道研究[J]. 现代计算机, 2020, 49(8):30-36.
|
| [14] |
LIU Yi, CAO Jianjun, DIAO Xingchun, et al. Review on Stability of Feature Selection[J]. Journal of Software, 2018, 29(9):2559-2579.
|
|
刘艺, 曹建军, 刁兴春, 等. 特征选择稳定性研究综述[J]. 软件学报, 2018, 29(9):2559-2579.
|
| [15] |
ZHANG Xiao, MEI Changlin, CHEN Degang, et al. Feature Selection in Mixed Data: A Method Using A Novel Fuzzy Rough Set-based Information Entropy[J]. Pattern Recognition, 2016, 56(1):1-15.
doi: 10.1016/j.patcog.2016.02.013
URL
|
| [16] |
ZHAO Cheng, CHEN Junxin. Reflective XSS Detection Technology Based on Hidden Markov Model[J]. Journal of Zhejiang University of Technology, 2019, 47(4):6-12.
|
|
赵澄, 陈君新. 基于隐马尔可夫模型的反射型XSS检测技术[J]. 浙江工业大学学报, 2019, 47(4):6-12.
|
| [17] |
ZHANG Xiao, YING Shi, ZHANG Tao. Collection and Service Processing Framework of Application Software Running Log[J]. Computer Engineering and Applications, 2018, 54(10):81-89, 142.
|
|
张骁, 应时, 张韬. 应用软件运行日志的收集与服务处理框架[J]. 计算机工程与应用, 2018, 54(10):81-89, 142.
|
| [18] |
JIANG Hongling, DAI Junwei. DGA Malicious Domain Name Detection Method[J]. Journal of Beijing Institute of Machinery (Natural Science Edition), 2019, 34(5):6-22.
|
|
蒋鸿玲, 戴俊伟. DGA恶意域名检测方法[J]. 北京信息科技大学学报(自然科学版), 2019, 34(5):6-22.
|
 ), XIA Lingling1,2,3
), XIA Lingling1,2,3