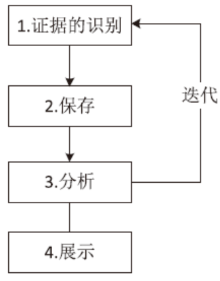
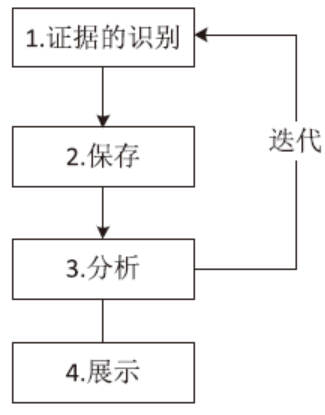
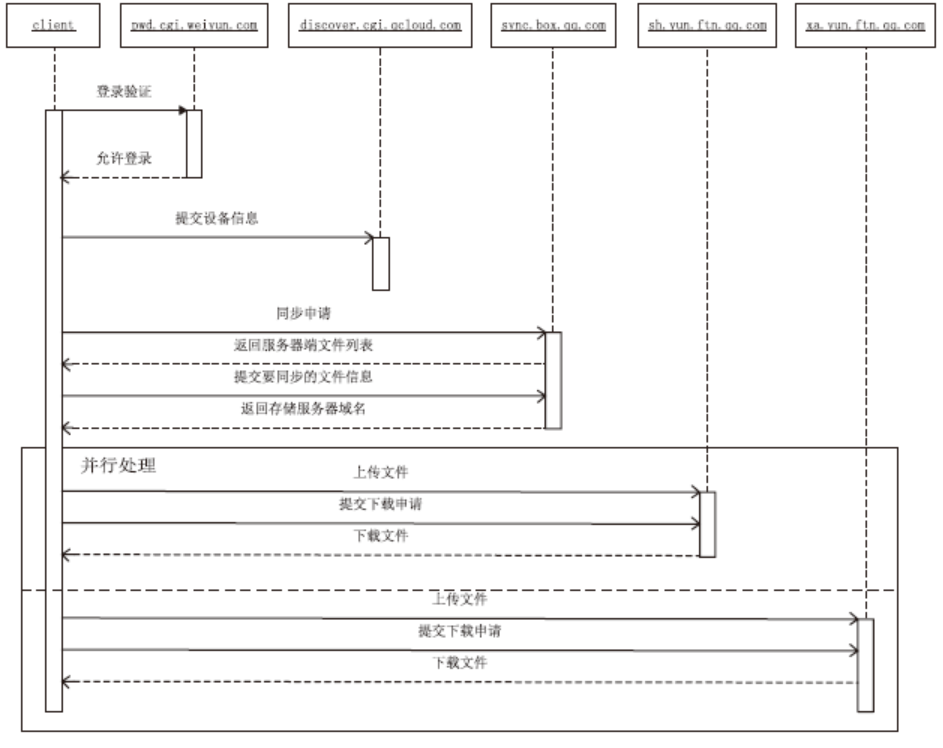
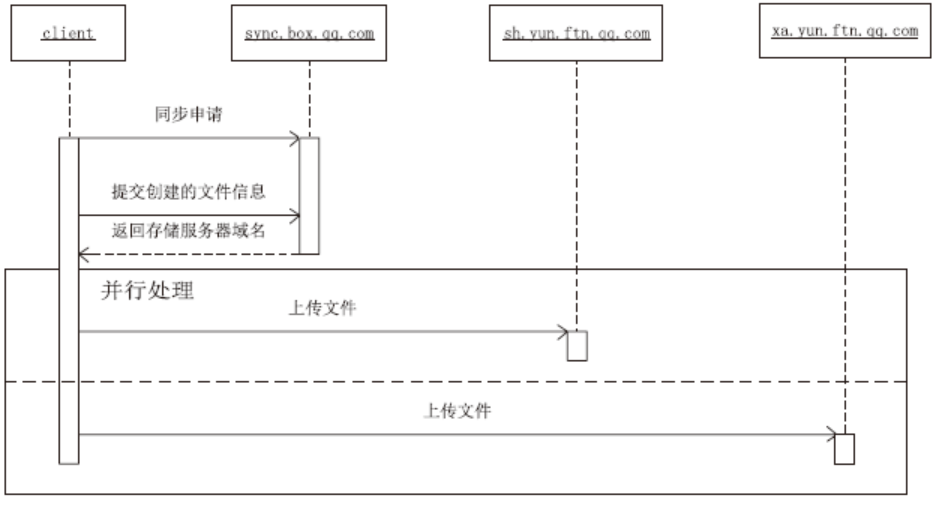
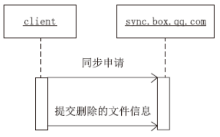
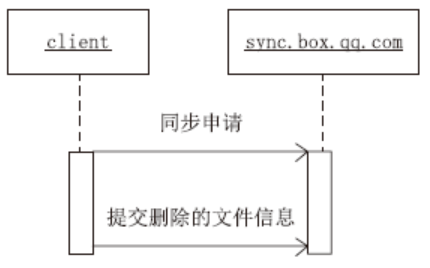
| [1] |
This could be the iCloud flaw that led to celebrity photos being leaked
|
| [2] |
Peter Mell, Timothy Grance.Cloud computing synopsis andrecommendations[M]. Gaithersburg, MD: U.S. Department ofCommerce,2012.
|
| [3] |
Waters J.Cloud-based data storage[J]. The Education Digest, 2011, 76(8):28-34.
|
| [4] |
Palme G.A road map for digital forensic research[C].DFRWS.Technical Report DTRT0010-01:2001,15-20
|
| [5] |
George Grispos, Tim Storer, William Bradley Glisson.Calm Before the Storm: The Challenges of Cloud Computing in Digital Forensics[J].International Journal of Digital Crime and Forensics,2012, 4(2):28-48
|
| [6] |
Hyunji Chung, Jungheum Park, Sangjin Lee.Digital forensic investigation of cloud storage services[J]. Digital Investigation, 2012, 9(2012):81-95
|
| [7] |
Ben Martini, Kim-Kwang Raymond Choo. Cloud storage forensics: ownCloud as a case study[J].Digital Investigation, 2013,8(2013):1-13
|
| [8] |
Ben Martini, Kim-Kwang Raymond Choo. An integrated conceptual digital forensic framework for cloud computing[J]. Digital Investigation, 2012,9(2012):71-80
|
| [9] |
杨波,姜建国. 试析云取证面临的挑战[J]. 保密科学技术,2014,7: 46-49
|
| [10] |
RFC2616-1999, Hypertext Transfer Protocol -- HTTP/1.1[S].
|
| [11] |
吴轩亮. 三网融合下城域网DDoS攻击的监测及防范技术研究[J]. 信息网络安全,2012,(3):45-48.
|
| [12] |
黄华军,钱亮,王耀钧. 基于异常特征的钓鱼网站URL检测技术[J]. 信息网络安全,2012,(1):23-25.
|
| [13] |
黄俊强,方舟,王希忠. 基于Snort-wireless的分布式入侵检测系统研究与设计[J]. 信息网络安全,2012,(2):23-26.
|
| [14] |
池水明,周苏杭. DDoS攻击防御技术研究[J]. 信息网络安全,2012,(5):27-31.
|
| [15] |
黄华军,王耀钧,姜丽清. 网络钓鱼防御技术研究[J]. 信息网络安全,2012,(4):30-35.
|
| [16] |
方欣,万扬,文霞等.基于协议分析技术的网络入侵检测系统中DDoS攻击的方法研究[J]. 信息网络安全,2012,(4):36-38.
|
| [17] |
范光远,辛阳. 防火墙审计方案的分析与设计[J]. 信息网络安全,2012,(3):81-84.
|