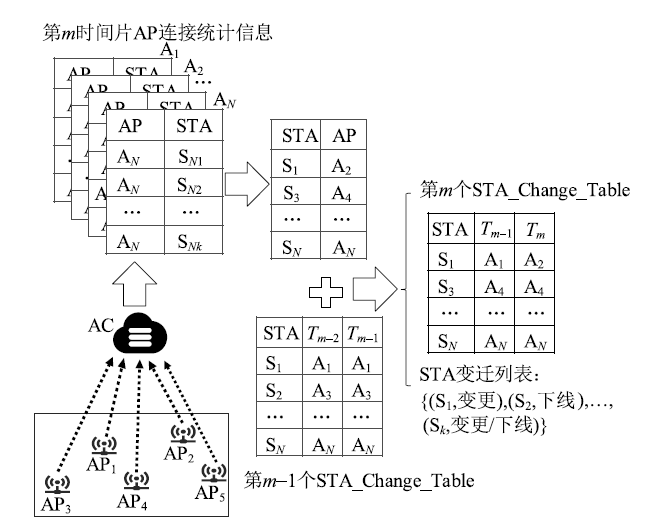
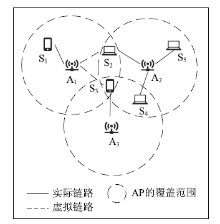
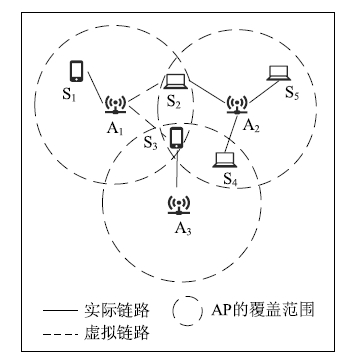
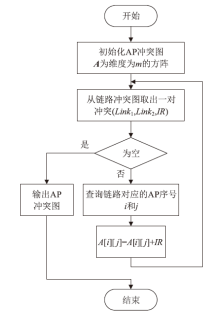
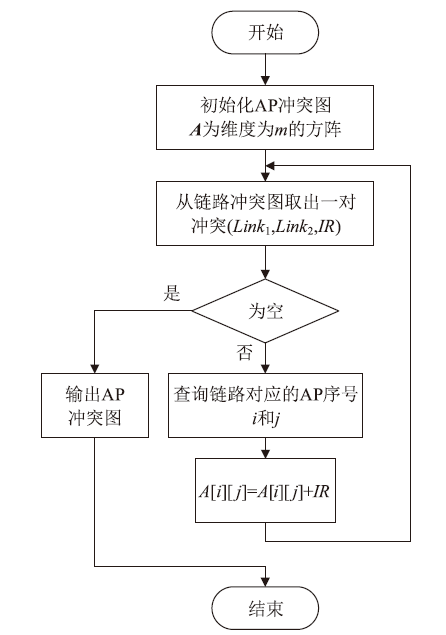
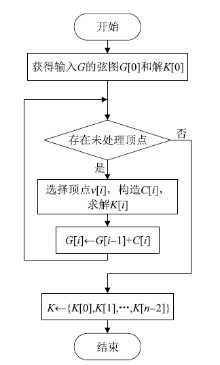
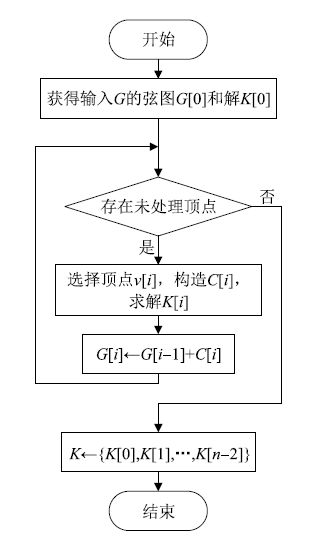
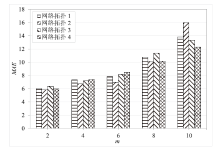
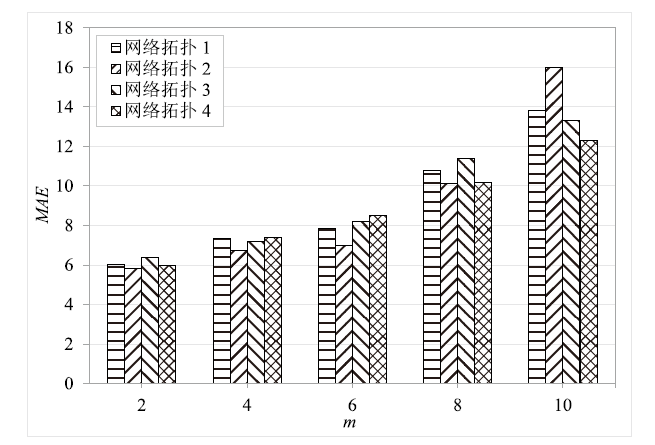
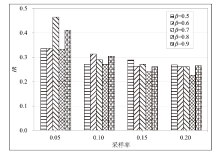
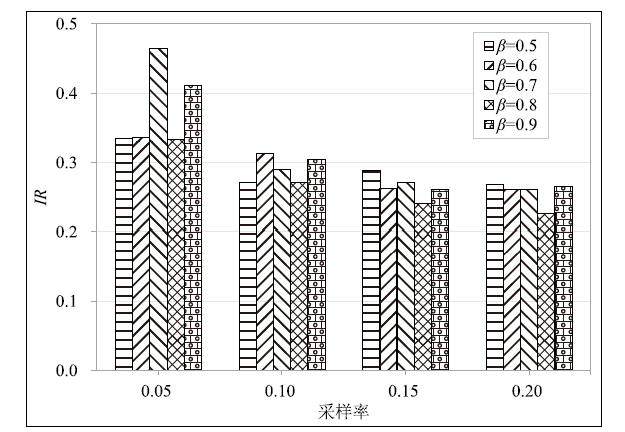
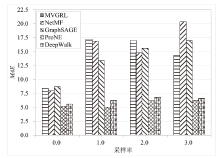
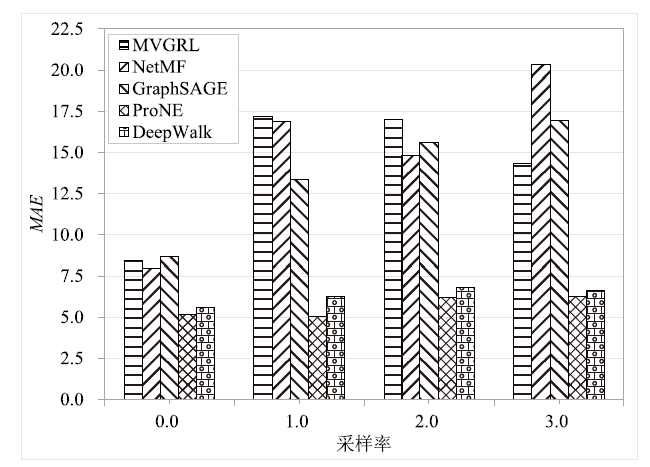
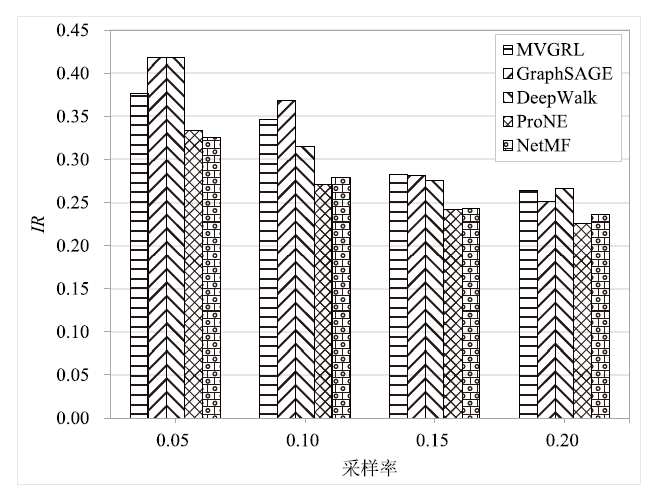
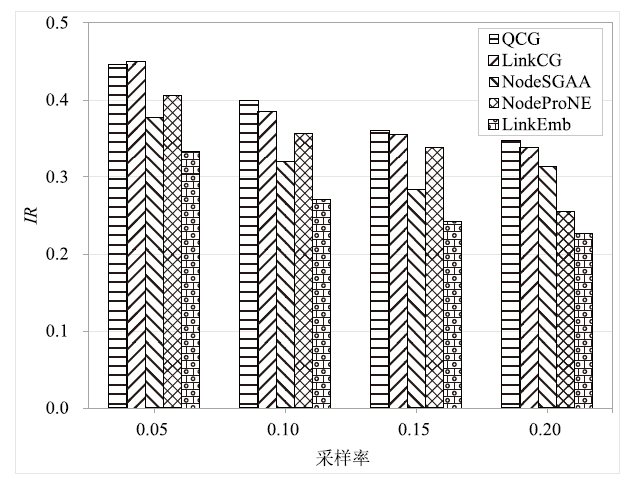
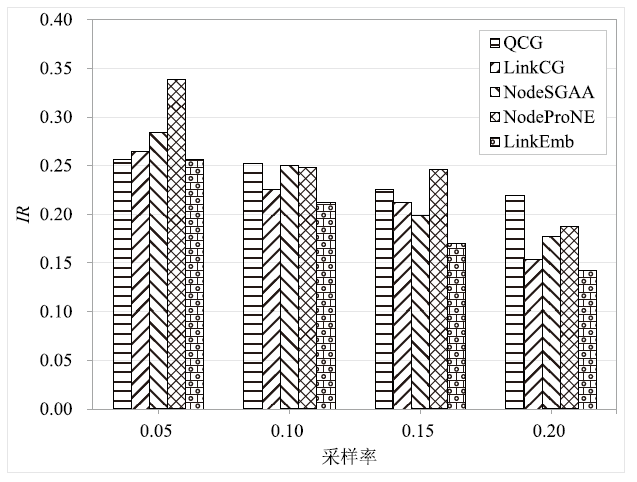
Netinfo Security ›› 2022, Vol. 22 ›› Issue (9): 76-85.doi: 10.3969/j.issn.1671-1122.2022.09.009
Previous Articles Next Articles
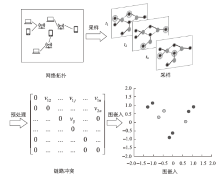
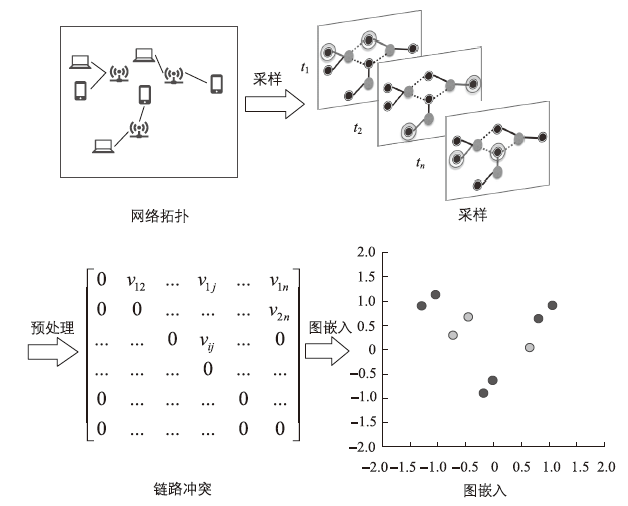
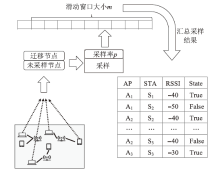
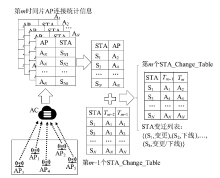
Channel Interference Measurement and Optimization Based on Link Conflict Graph Embedding
LIANG Yan1, LI Dong2, ZHAO Yizhu1, YU Junqing1,2( )
)
- 1. School of Cyber Science and Engineering, Huazhong University of Science and Technology, Wuhan 430074, China
2. Network and Computation Center, Huazhong University of Science and Technology, Wuhan 430074, China
-
Received:2022-06-20Online:2022-09-10Published:2022-11-14 -
Contact:YU Junqing E-mail:yjqing@hust.edu.cn
CLC Number:
Cite this article
LIANG Yan, LI Dong, ZHAO Yizhu, YU Junqing. Channel Interference Measurement and Optimization Based on Link Conflict Graph Embedding[J]. Netinfo Security, 2022, 22(9): 76-85.
share this article
| [1] | CARDIERI P, RAPPAPORT T S. Statistical Analysis of Co-Channel Interference in Wireless Communications Systems[J]. Wireless Communications and Mobile Computing, 2001, 1(1): 111-121. |
| [2] | JAIN K, PADHYE J, PADMANABHAN V N, et al. Impact of Interference on Multi-Hop Wireless Network Performance[J]. Wireless Networks, 2005, 11(4): 471-487. |
| [3] | DAI Hongning, WONG R C W, WANG Hao, et al. Big Data Analytics for Large-Scale Wireless Networks: Challenges and Opportunities[J]. ACM Computing Surveys, 2019, 52(5): 1-36. |
| [4] | SUI Kaixin, ZHOU Mengyu, LIU Dapeng, et al. Characterizing and Improving WiFi Latency in Large-Scale Operational Networks[C]// ACM. 14th Annual International Conference on Mobile Systems, Applications, and Services. New York: ACM, 2016: 347-360. |
| [5] | ZHANG Chengwei, HEI Xiaojun, BENSAOU B. A Measurement Study of Campus WiFi Networks Using WiFiTracer[M]. Heidelberg: Springer, 2019. |
| [6] | SUBRAMANIAN A P, GUPTA H, DAS S R, et al. Minimum Interference Channel Assignment in Multiradio Wireless Mesh Networks[J]. IEEE Transactions on Mobile Computing, 2008, 7(12): 1459-1473. |
| [7] | BIANCHI G. Performance Analysis of the IEEE 802.11 Distributed Coordination Function[J]. IEEE Journal on Selected Areas in Communications, 2000, 18(3): 535-547. |
| [8] | STOJANOVA M, BEGIN T, BUSSON A. Conflict Graph-Based Model for IEEE 802.11 Networks: A Divide-and-Conquer Approach[J]. Performance Evaluation, 2019, 130: 64-85. |
| [9] | ZHOU Xia, ZHANG Zengbin, WANG Gang, et al. Practical Conflict Graphs for Dynamic Spectrum Distribution[C]// ACM. 13rd International Conference on Measurement and Modeling of Computer Systems. New York: ACM, 2013: 5-16. |
| [10] | ZHAO Yanchao, LI Wenzhong, WU Jie, et al. Quantized Conflict Graphs for Wireless Network Optimization[C]// IEEE. 34th IEEE Conference on Computer Communications. New York: IEEE, 2015: 2218-2226. |
| [11] | LIU Jingwei, AOKI T, LI Zhetao, et al. Throughput Analysis of IEEE 802.11 WLANs with Inter-Network Interference[EB/OL]. (2020-03-24)[2021-03-12]. https://doi.org/10.3390/app10062192. |
| [12] | ABDEWEDOUD L, BUSSON A, GUÉRIN-LASSOUS I, et al. A Passive Method to Infer the Weighted Conflict Graph of an IEEE 802.11 Network[C]// Springer. 18th International Conference on Ad-Hoc Networks and Wireless. Heidelberg: Springer, 2019: 304-316. |
| [13] | LI Wenzhong, ZHANG Jinggong, ZHAO Yanchao. Conflict Graph Embedding for Wireless Network Optimization[C]// IEEE. 36th IEEE Conference on Computer Communications. New York: IEEE, 2017: 1-9. |
| [14] | CHOPRA S, RAO M R. The Partition Problem[J]. Mathematical Programming, 1993, 59(1): 87-115. |
| [15] | ZHANG Jie, DONG Yuxiao, WANG Yan, et al. ProNE: Fast and Scalable Network Representation Learning[C]// IJCAI. 28th International Joint Conference on Artificial Intelligence. San Francisco: Mogan Kaufmann, 2019: 4278-4284. |
| [16] | WANG Guanglei, HASSAN H. Exploiting Sparsity for the Min k-Partition Problem[J]. Mathematical Programming Computation, 2020, 12(1): 109-130. |
| [1] | ZHANG Zhenghui, CHEN Xingshu, LUO Yonggang, WU Tianxiong. A Job Performance Evaluation Method under Spark Platform [J]. Netinfo Security, 2022, 22(9): 86-95. |
| [2] | HU Yujia, DAI Zhengyi, SUN Bing. Differential-Linear Cryptanalysis of the SIMON Algorithm [J]. Netinfo Security, 2022, 22(9): 63-75. |
| [3] | ZHANG Xuewang, LIU Yufan. Identity Traceable Anonymous Authentication Scheme for Nodes in the Perception Layer of IoT [J]. Netinfo Security, 2022, 22(9): 55-62. |
| [4] | ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism [J]. Netinfo Security, 2022, 22(9): 46-54. |
| [5] | WEN Weiping, LIU Chengjie, SHI Lin. A Null Pointer Reference Mining System Based on Data Flow Tracing [J]. Netinfo Security, 2022, 22(9): 40-45. |
| [6] | TONG Xiaojun, MAO Ning, ZHANG Miao, WANG Zhu. Image Encryption Algorithm Based on Henon Mapping and Improved Lifting Wavelet Transform [J]. Netinfo Security, 2022, 22(9): 31-39. |
| [7] | ZHANG Min, XU Chunxiang, ZHANG Jianhua. Research on Authentication Key Agreement Protocol Based on Multi-Factor in Internet of Drones [J]. Netinfo Security, 2022, 22(9): 21-30. |
| [8] | YU Jing, YUAN Shuguang, YUAN Yulin, CHEN Chi. A Robust Watermarking Technology Based on k-Anonymity Dataset [J]. Netinfo Security, 2022, 22(9): 11-20. |
| [9] | SONG Yubo, CHEN Ye, CAI Yihan, ZHANG Bo. Traceability of Private Industrial Control Protocol Based on Subgraph Isomorphic Matching of Protocol State Machine [J]. Netinfo Security, 2022, 22(9): 1-10. |
| [10] | LIU Lingxiang, PAN Zulie, LI Yang, LI Zongchao. Firmware Vulnerability Static Localization Method Based on Front-End and Back-End Correlation Analysis [J]. Netinfo Security, 2022, 22(8): 44-54. |
| [11] | GAO Bo, CHEN Lin, YAN Yingjian. Research on Side Channel Attack Based on CNN-MGU [J]. Netinfo Security, 2022, 22(8): 55-63. |
| [12] | WEI Songjie, LI Chenghao, SHEN Haotong, ZHANG Wenzhe. Research and Application of Network Anonymous Traffic Detection Method Based on Deep Forest [J]. Netinfo Security, 2022, 22(8): 64-71. |
| [13] | HUANG Baohua, ZHAO Weihong, PENG Li, XIE Tongyi. Efficient Blockchain PKI Model Based on MPT Index [J]. Netinfo Security, 2022, 22(8): 72-80. |
| [14] | TONG Xiaojun, SU Yuyue, ZHANG Miao, WANG Zhu. Lightweight Cipher Algorithm Based on Chaos and Improved Generalized Feistel Structure [J]. Netinfo Security, 2022, 22(8): 8-18. |
| [15] | GU Zhaojun, LIU Tingting, GAO Bing, SUI He. Anomaly Detection of Imbalanced Data in Industrial Control System Based on GAN-Cross [J]. Netinfo Security, 2022, 22(8): 81-89. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||