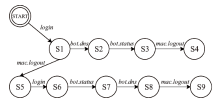
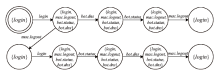
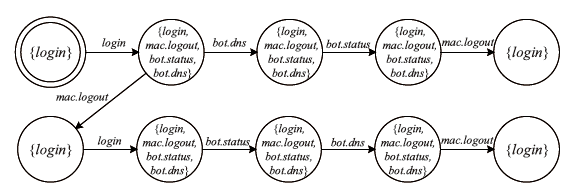
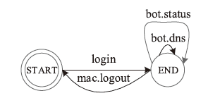
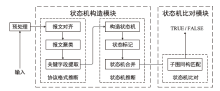
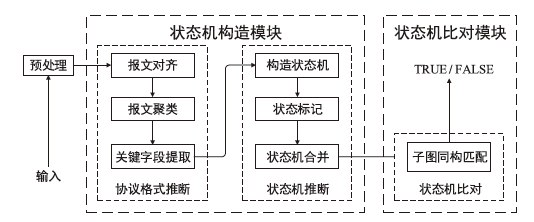
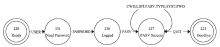
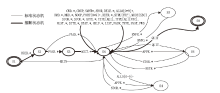
Netinfo Security ›› 2022, Vol. 22 ›› Issue (9): 1-10.doi: 10.3969/j.issn.1671-1122.2022.09.001
Previous Articles Next Articles
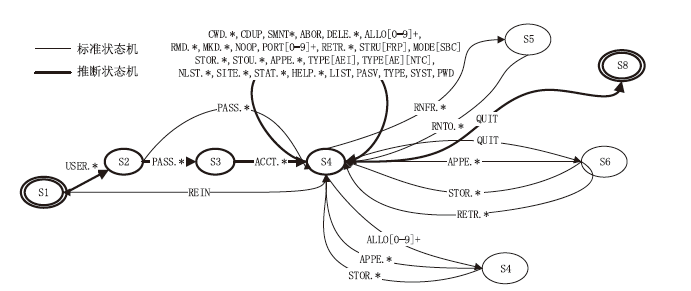
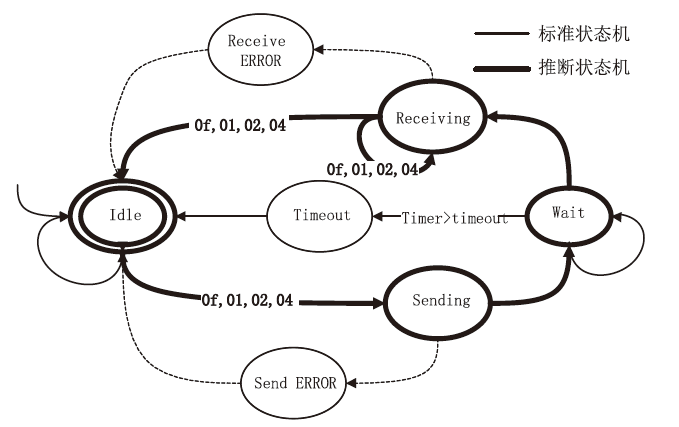
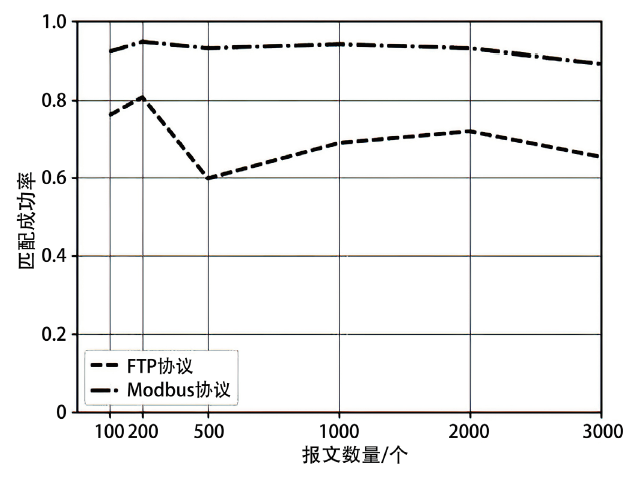
Traceability of Private Industrial Control Protocol Based on Subgraph Isomorphic Matching of Protocol State Machine
SONG Yubo1,2,3( ), CHEN Ye1,2,3, CAI Yihan1,2,3, ZHANG Bo4
), CHEN Ye1,2,3, CAI Yihan1,2,3, ZHANG Bo4
- 1. School of Cyber Science and Engineering, Southeast University, Nanjing 211189, China
2. Jiangsu Key Laboratory of Computer Networking Technology, Nanjing 211189, China
3. Network Communication and Security Purple Mountain Laboratory, Nanjing 211189, China
4. Global Energy Interconnection Research Institute Co.,Ltd., Nanjing 210003, China
-
Received:2022-06-13Online:2022-09-10Published:2022-11-14 -
Contact:SONG Yubo E-mail:songyubo@seu.edu.cn
CLC Number:
Cite this article
SONG Yubo, CHEN Ye, CAI Yihan, ZHANG Bo. Traceability of Private Industrial Control Protocol Based on Subgraph Isomorphic Matching of Protocol State Machine[J]. Netinfo Security, 2022, 22(9): 1-10.
share this article
| [1] | LIU Kaizheng, YANG Ming, LING Zhen, et al. On Manually Reverse Engineering Communication Protocols of Linux-Based IoT Systems[J]. IEEE, 2020, 8(8): 6815-6827. |
| [2] | FANG Weiqing, LI Peng, ZHANG Yujie, et al. Research on Optimization of Fuzzing Test of Unknown Protocol Based on Message Type[C]// Springer.International Conference on Big Data and Security.Heidelberg:Springer, 2021: 284-298. |
| [3] | BEDDOE M A. Network Protocol Analysis Using Bioinformatics Algorithms[J]. Toorcon, 2004, 26(6): 1095-1098 |
| [4] | LEITA C, MERMOUD K, DACIER M. Scriptgen: An Automated Script Generation Tool for Honeyd[C]// IEEE. Computer Security Applications Conference, 21st Annual. New York: IEEE, 2005: 203-214. |
| [5] | CUI Weidong, KANNAN J, WANG H J. Discoverer: Automatic Protocol Reverse Engineering From Network Traces[EB/OL]. (2007-8-6)[2022-06-05]. https://www.cs.purdue.edu/homes/xyzhang/fall07/Papers/discoverer.pdf |
| [6] | BOSSERT G, GUIHERY F, HIET G. Towards Automated Protocol Reverse Engineering Using Semantic information[C]// ACM. Proceedings of the 9th ACM Symposium on Information, Computer and Communications Security. New York: ACM, 2014: 51-62. |
| [7] | WANG Yiping, LI Xingjian, MENG Jiao, et al. Biprominer: Automatic Mining of Binary Protocol Features[C]// IEEE. 2011 12th International Conference on Parallel and Distributed Computing, Applications and Technologies. New York: IEEE, 2011: 179-184. |
| [8] | LUO Jianzheng, YU Shunzheng. Position-Based Automatic Reverse Engineering of Network Protocols[J]. Journal of Network and Computer Applications, 2003(3): 1070-1077. |
| [9] | CAI Jun, LUO Jianzhen, LEI Fangyuan. Analyzing Network Protocols of Application Layer Using Hidden Semi-Markov Model[J]. Mathematical Problems in Engineering, 2016(11): 1-14. |
| [10] | LIN Y D, LAI Y K, BUI Q T, et al. ReFSM: Reverse Engineering From Protocol Packet Traces to Test Generation by Extended Finite State Machines[J]. Journal of Network and Computer Applications, 2020, 171: 102819-102830. |
| [11] | KLEBER S, KOPP H, KARGL F. {NEMESYS}: Network Message Syntax Reverse Engineering by Analysis of the Intrinsic Structure of Individual Messages[EB/OL]. (2018-08-13)[2022-06-05]. https://dl.acm.org/doi/abs/10.5555/3307423.3307431. |
| [12] | YE Yapeng, ZHANG Zhuo, WANG Fei, et al. NetPlier: Probabilistic Network Protocol Reverse Engineering From Message Traces[EB/OL]. (2021-01-10)[2022-06-05]. https://www.researchgate.net/publication/350051374_NetPlier_Probabilistic_Network_Protocol_Reverse_Engineering_from_Message_Traces. |
| [13] | ULLMANN J R. An Algorithm for Subgraph Isomorphism[J]. ACM, 1976, 23(1): 31-42. |
| [14] | CORDELLA L P, FOGGIA P, SANSONE C, et al. A (Sub) Graph Isomorphism Algorithm for Matching Large Graphs[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2004, 26(10): 1367-1372. |
| [15] | NEEDLEMAN S B, Wunsch C D. A General Method Applicable to the Search for Similarities in the Amino Acid Sequence of Two Proteins[J]. Journal of Molecular Biology, 1970, 48(3): 443-453. |
| [16] | KAUFMAN L, ROUSSEEUW P J. Finding Groups in Data: An Introduction to Cluster Analysis[M]. New Jersey: John Wiley & Sons, 2009. |
| [17] | ANTUNES J, NEVES N. Automatically Complementing Protocol Specifications From Network Traces[EB/OL]. (2011-5-11)[2022-06-07]. https://doi.org/10.1145/1978582.1978601. |
| [1] | ZHANG Zhenghui, CHEN Xingshu, LUO Yonggang, WU Tianxiong. A Job Performance Evaluation Method under Spark Platform [J]. Netinfo Security, 2022, 22(9): 86-95. |
| [2] | LIANG Yan, LI Dong, ZHAO Yizhu, YU Junqing. Channel Interference Measurement and Optimization Based on Link Conflict Graph Embedding [J]. Netinfo Security, 2022, 22(9): 76-85. |
| [3] | HU Yujia, DAI Zhengyi, SUN Bing. Differential-Linear Cryptanalysis of the SIMON Algorithm [J]. Netinfo Security, 2022, 22(9): 63-75. |
| [4] | ZHANG Xuewang, LIU Yufan. Identity Traceable Anonymous Authentication Scheme for Nodes in the Perception Layer of IoT [J]. Netinfo Security, 2022, 22(9): 55-62. |
| [5] | ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism [J]. Netinfo Security, 2022, 22(9): 46-54. |
| [6] | WEN Weiping, LIU Chengjie, SHI Lin. A Null Pointer Reference Mining System Based on Data Flow Tracing [J]. Netinfo Security, 2022, 22(9): 40-45. |
| [7] | TONG Xiaojun, MAO Ning, ZHANG Miao, WANG Zhu. Image Encryption Algorithm Based on Henon Mapping and Improved Lifting Wavelet Transform [J]. Netinfo Security, 2022, 22(9): 31-39. |
| [8] | ZHANG Min, XU Chunxiang, ZHANG Jianhua. Research on Authentication Key Agreement Protocol Based on Multi-Factor in Internet of Drones [J]. Netinfo Security, 2022, 22(9): 21-30. |
| [9] | YU Jing, YUAN Shuguang, YUAN Yulin, CHEN Chi. A Robust Watermarking Technology Based on k-Anonymity Dataset [J]. Netinfo Security, 2022, 22(9): 11-20. |
| [10] | LIU Lingxiang, PAN Zulie, LI Yang, LI Zongchao. Firmware Vulnerability Static Localization Method Based on Front-End and Back-End Correlation Analysis [J]. Netinfo Security, 2022, 22(8): 44-54. |
| [11] | GAO Bo, CHEN Lin, YAN Yingjian. Research on Side Channel Attack Based on CNN-MGU [J]. Netinfo Security, 2022, 22(8): 55-63. |
| [12] | WEI Songjie, LI Chenghao, SHEN Haotong, ZHANG Wenzhe. Research and Application of Network Anonymous Traffic Detection Method Based on Deep Forest [J]. Netinfo Security, 2022, 22(8): 64-71. |
| [13] | HUANG Baohua, ZHAO Weihong, PENG Li, XIE Tongyi. Efficient Blockchain PKI Model Based on MPT Index [J]. Netinfo Security, 2022, 22(8): 72-80. |
| [14] | TONG Xiaojun, SU Yuyue, ZHANG Miao, WANG Zhu. Lightweight Cipher Algorithm Based on Chaos and Improved Generalized Feistel Structure [J]. Netinfo Security, 2022, 22(8): 8-18. |
| [15] | GU Zhaojun, LIU Tingting, GAO Bing, SUI He. Anomaly Detection of Imbalanced Data in Industrial Control System Based on GAN-Cross [J]. Netinfo Security, 2022, 22(8): 81-89. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||