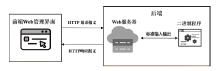
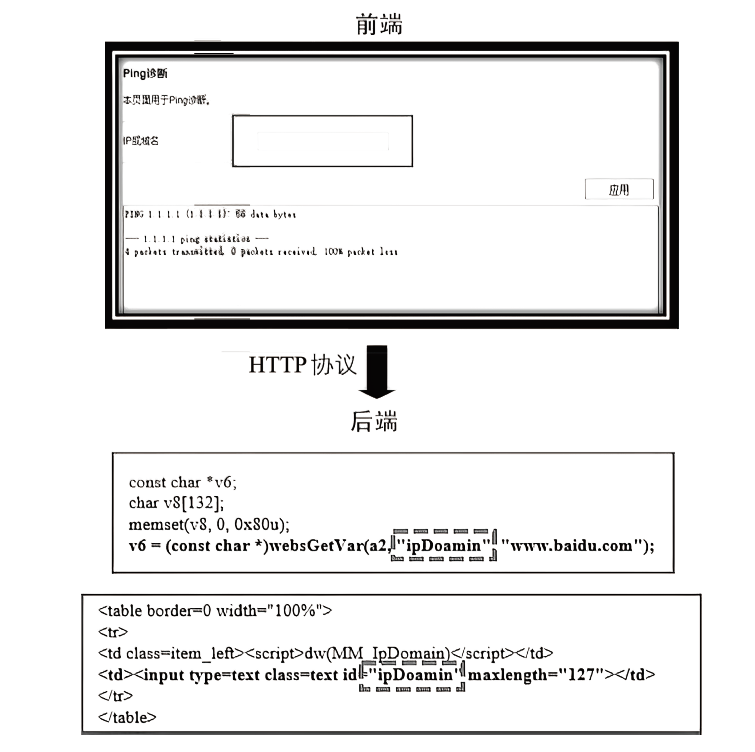
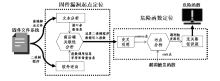
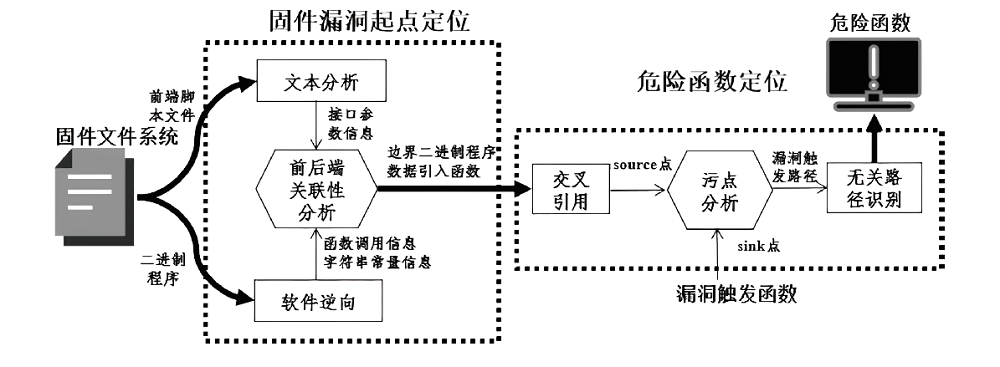
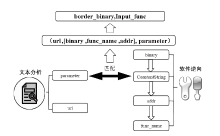
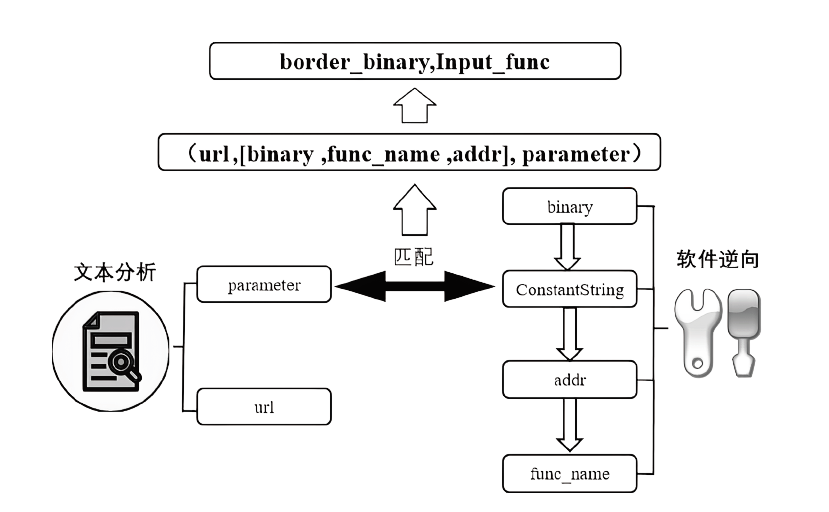
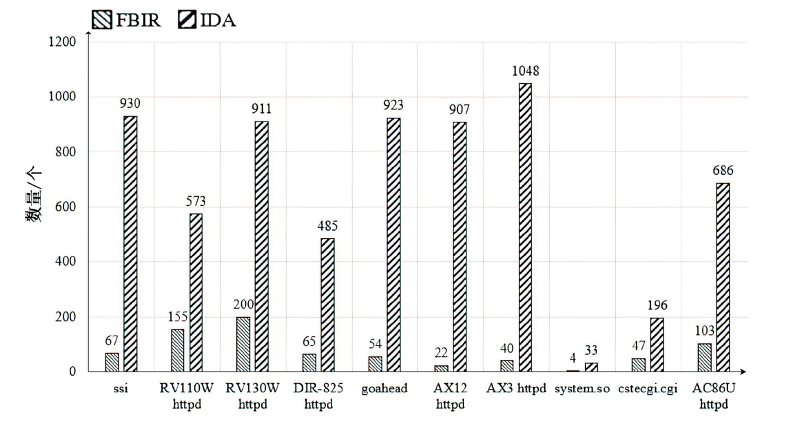
| [1] |
YU Yingchao, CHEN Zuoning, GAN Shuitao, et al. Research on the Technologies of Security Analysis Technologies on the Embedded Device Firmware[J]. Chinese Journal of Computers, 2021, 44(5): 859-881.
|
|
于颖超, 陈左宁, 甘水滔, 等. 嵌入式设备固件安全分析技术研究[J]. 计算机学报, 2021, 44(5): 859-881.
|
| [2] |
CHEN D D, EGELE M, WOO M, et al. Towards Automated Dynamic Analysis for Linux-Based Embedded Firmware[EB/OL]. (2016-01-01)[2022-03-22]. https://www.researchgate.net/publication/316904631_Towards_Automated_Dynamic_Analysis_for_Linux-based_Embedded_Firmware.
|
| [3] |
KIM M, KIM D, KIM E, et al. FirmAE: Towards Large-Scale Emulation of IoT Firmware for Dynamic Analysis[C]//ACM. Annual Computer Security Applications Conference (ACSAC’20). New York: ACM, 2020: 733-745.
|
| [4] |
ZHENG Yaowen, DAVANIAN A, YIN Heng, et al. FIRM-AFL: High-Throughput Greybox Fuzzing of IoT Firmware via Augmented Process Emulation[C]//USENIX. 28th USENIX Security Symposium. Berkeley: USENIX, 2019: 1099-1114.
|
| [5] |
CNCERT/CC, NSFOCUS. 2020 IoT Security Annual Report[EB/OL]. (2021-07-05)[2022-04-08]. https://www.nsfocus.com.cn/html/2021/134_0705/158. html.
|
|
国家互联网应急中心,绿盟科技. 2020物联网安全年报[EB/OL]. (2021- 07-05)[ 2022-04-08]. https://www.nsfocus.com.cn/html/2021/134_0705/158. html.
|
| [6] |
CHENG Kai, LI Qiang, WANG Lei, et al. DTaint: Detecting the Taint-Style Vulnerability in Embedded Device Firmware[C]//IEEE. 2018 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN). New York: IEEE, 2018: 430-441.
|
| [7] |
SHOSHITAISHVILI Y, WANG Ruoyu, SALLS C, et al. SOK: (State of ) the Art of War: Offensive Techniques in Binary Analysis[C]//IEEE. 2016 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2016: 138-157.
|
| [8] |
ZHU Lipeng, FU Xiaotong, YAO Yao, et al. FIoT: Detecting the Memory Corruption in Lightweight IoT Device Firmware[C]//IEEE. 2019 18th IEEE International Conference on Trust, Security and Privacy in Computing and Communications. New York: IEEE, 2019: 248-255.
|
| [9] |
REDINI N, MACHIRY A, WANG Ruoyu, et al. KARONTE: Detecting Insecure Multi-Binary Interactions in Embedded Firmware[C]//IEEE. 2020 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2020: 1544-1561.
|
| [10] |
CHEN Libo, WANG Yanhao, CAI Quanpu, et al. Sharing More and Checking Less: Leveraging Common Input Keywords to Detect Bugs in Embedded Systems[C]//USENIX. 30th USENIX Security Symposium. Berkeley: USENIX, 2021: 303-319.
|
| [11] |
WANG Dong, ZHANG Xiaosong, CHEN Ting, et al. Discovering Vulnerabilities in COTS IoT Devices through Blackbox Fuzzing Web Management Interface[EB/OL].(2019-11-04)[2022-03-10]. https://dl.acm.org/doi/10.1155/2019/5076324.
|
| [12] |
WANG Lei, LI Feng, LI Lian, et al. Principle and Practice of Taint Analysis[J]. Journal of Software, 2017, 28(4): 860-882.
|
|
王蕾, 李丰, 李炼, 等. 污点分析技术的原理和实践应用[J]. 软件学报, 2017, 28(4): 860-882.
|
| [13] |
DAI Zhonghua, FEI Yongkang, ZHAO Bo, et al. Research on the Localization of Firmware Vulnerability Based on Stain Tracking[J]. Journal of Shandong University(Natural Science), 2016, 51(9): 41-46.
|
|
戴忠华, 费永康, 赵波, 等. 基于污点跟踪的固件漏洞定位研究[J]. 山东大学学报(理学版), 2016, 51(9): 41-46.
|
| [14] |
ZHAO Jian, WANG Rui, LI Siqi. Research on Smart Home Vulnerability Mining Technology Based on Taint Analysis[J]. Netinfo Security, 2018, 18(6): 36-44.
|
|
赵健, 王瑞, 李思其. 基于污点分析的智能家居漏洞挖掘技术研究[J]. 信息网络安全, 2018, 18(6): 36-44.
|
| [15] |
CELIK Z B, BABUN L, SIKDER A K, et al. Sensitive Information Tracking in Commodity IoT[C]//USENIX. 27th USENIX Security Symposium. Berkeley: USENIX, 2018: 1687-1704.
|
 ), LI Yang1,2, LI Zongchao1,2
), LI Yang1,2, LI Zongchao1,2