Netinfo Security ›› 2024, Vol. 24 ›› Issue (4): 626-639.doi: 10.3969/j.issn.1671-1122.2024.04.012
Previous Articles Next Articles
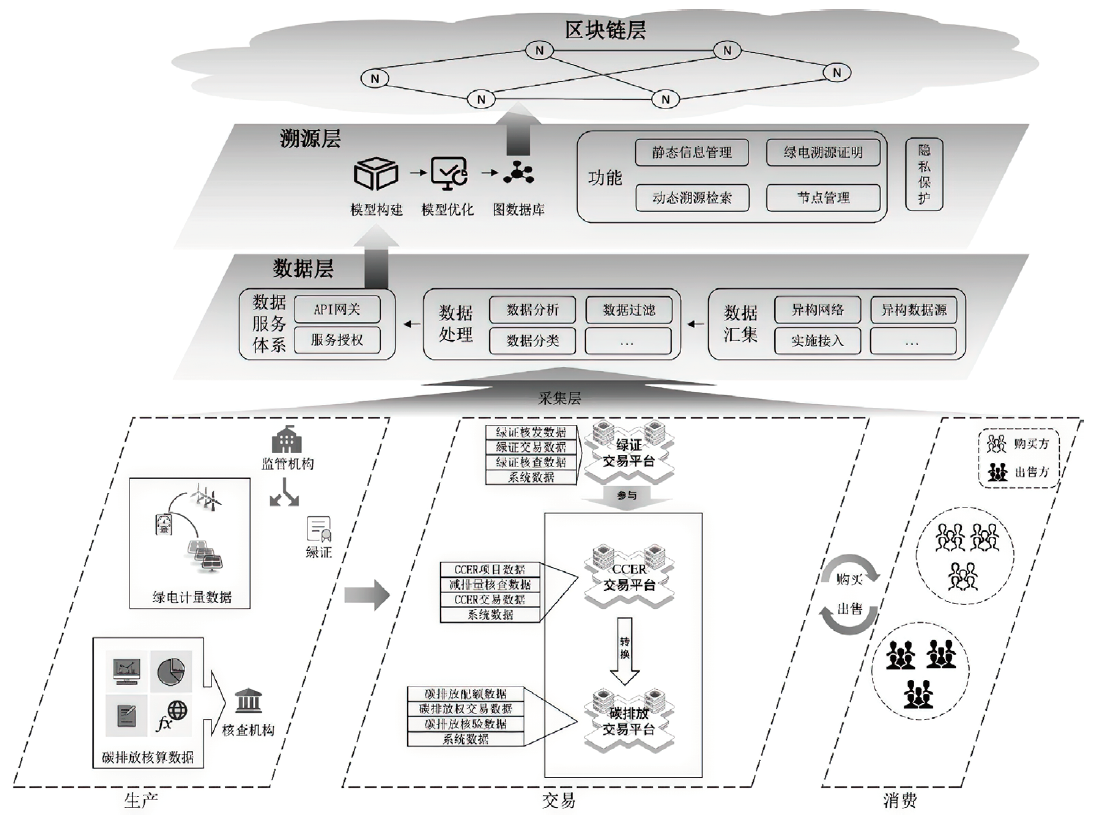
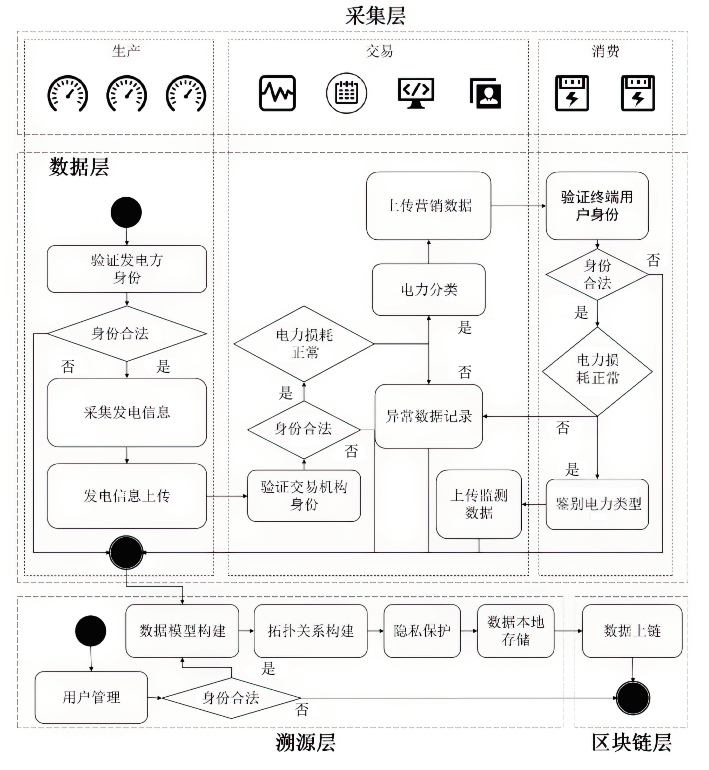
Clean Energy Data Traceability Mechanism Based on Blockchain
HU Haiyang1, LIU Chang1( ), WANG Dong2, WEI Xu3
), WANG Dong2, WEI Xu3
- 1. State Key Laboratory of Network and Switching Technology, Beijing University of Posts and Telecommunications, Beijing 100876, China
2. State Grid Digital Technology Holding Co., Ltd., Beijing 100053, China
3. State Grid Jiangsu Electric Power Co., Ltd., Nanjing 210024, China
-
Received:2023-09-12Online:2024-04-10Published:2024-05-16
CLC Number:
Cite this article
HU Haiyang, LIU Chang, WANG Dong, WEI Xu. Clean Energy Data Traceability Mechanism Based on Blockchain[J]. Netinfo Security, 2024, 24(4): 626-639.
share this article
| [1] | YANG Yongming. Strong Momentum of Global Renewable Energy Development[N]. China Electric Power News, 2023-07-25(3). |
| 杨永明. 全球可再生能源发展势头强劲[N]. 中国电力报, 2023-07-25 (3). | |
| [2] | RAZMJOO A, GANDOMI A H, PAZHOOHESH M, et al. The Key Role of Clean Energy and Technology in Smart Cities Devel-Opment[EB/OL]. (2022-09-05)[2023-10-14]. https://doi.org/10.1016/j.esr.2022.100943. |
| [3] | HU Ruyi, YANG Chunchen, QI Hujia, et al. Data Fusion and Sharing Platform Based on Big Data of Electricity Marketing[J]. Industrial Control Computer, 2020, 33(3): 110-112. |
| 胡如一, 杨春晨, 戚胡佳, 等. 基于电力营销大数据的数据融合共享平台研究与应用[J]. 工业控制计算机, 2020, 33(3): 110-112. | |
| [4] | GU Bin, ZOU Yunfeng, SHAN Chao, et al. Research on Power Data Security Distribution and Traceability Technology Based on Digital Watermarking[J]. Information Technology, 2023(11): 99-104. |
| 顾斌, 邹云峰, 单超, 等. 基于数字水印的电力数据安全分发与溯源技术研究[J]. 信息技术, 2023(11): 99-104. | |
| [5] | AGUNG A, HANDAYANI R. Blockchain for Smart Grid[J]. Journal of King Saud University-Computer and Information Sciences, 2022, 34(3): 666-675. |
| [6] | D’ANTONIO S, NARDONE R, RUSSO N, et al. A Tamper-Resistant Storage Framework for Smart Grid Security[C]// IEEE. 2023 31st Euromicro International Conference on Parallel, Distributed and Network-Based Processing (PDP). New York: IEEE, 2023: 100-103. |
| [7] | MOLLAH M B, ZHAO J, NIYATO D, et al. Blockchain for Future Smart Grid: A Comprehensive Survey[J]. IEEE Internet of Things Journal, 2020, 8(1): 18-43. |
| [8] | XU J, DUAN Y. Pricing and Greenness Investment for Green Products with Government Subsidies: When to Apply Blockchain T-echnology?[EB/OL]. (2021-12-08)[2023-10-14]. https://doi.org/10.1016/j.elerap.2021.101108. |
| [9] | ZHOU Yuanjian, QING Dongmei, LIU Yining, et al. Design of Electronic Warehouse Receipts System Based on Blockchain[J]. Netinfo Security, 2019, 19(6): 84-90. |
| 周元健, 秦冬梅, 刘忆宁, 等. 基于区块链的可信仓单系统设计[J]. 信息网络安全, 2019, 19(6): 84-90. | |
| [10] | XIE Tingyu, LI Zhiyong, QU Haipeng. Traceability Method of Power Battery Energy Storage Transaction Based on Blockchain[J]. Netinfo Security, 2021(S1): 186-189. |
| 谢廷宇, 李志勇, 曲海鹏. 基于区块链的动力电池储能交易溯源方法[J]. 信息网络安全, 2021(S1): 186-189. | |
| [11] | GAO Y, CHEN X, DU X. A Big Data Provenance Model for Data Security Supervision Based on PROV-DM Model[J]. IEEE Access, 2020, 8: 38742-38752. |
| [12] | BATLAJERY B V. Modeling and Generating Marketplace Activities with PROV-DM[C]// IEEE. 2021 4th International Conference on Artificial Intelligence for Industries (AI4I). New York: IEEE, 2021: 91-94. |
| [13] | LI J, QIAO Z, PENG J. Asymmetric Group Key Agreement Protocol Based on Blockchain and Attribute for Industrial Internet of Things[J]. IEEE Transactions on Industrial Informatics, 2022, 18(11): 8326-8335. |
| [14] | XU D, ZHENG M, JIANG L, et al. Lightweight and Unobtrusive Data Obfuscation at IoT Edge for Remote Inference[J]. IEEE Internet of Things Journal, 2020, 7(10): 9540-9551. |
| [15] | JIANG Nan, WANG Weiqi, WANG Jian. Research on Personal Information Protection Method Based on Smart Contract[J]. Netinfo Security, 2020, 20(11): 22-31. |
| 姜楠, 王玮琦, 王健. 基于智能合约的个人隐私数据保护方法研究[J]. 信息网络安全, 2020, 20(11): 22-31. | |
| [16] | WAN Z, ZHOU Y, REN K. Zk-AuthFeed: Protecting Data Feed to Smart Contracts with Authenticated Zero Knowledge Proof[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 20(2): 1335-1347. |
| [17] | SIGWART M, BORKOWSKI M, PEISE M, et al. A Secure and Extensible Blockchain-Based Data Provenance Framework for the Internet of Things[J]. Personal and Ubiquitous Computing, 2020: 1-15. |
| [18] | HONAR P, RASHID M, ALAM F, et al. IoT Big Data Provenance Scheme Using Blockchain on Hadoop Ecosystem[J]. Journal of Big Data, 2021, 8: 1-26. |
| [19] | SIDDIQUI M, SYED T, NADEEM A, et al. BlockTrack-L: A Lightweight Blockchain-Based Provenance Message Tracking in IoT[J]. International Journal of Advanced Computer Science and Applications, 2020, 11(4): 463-470. |
| [1] | SHI Runhua, YANG Jingyi, WANG Pengbo, LIU Huawei. Online/Off line Cross-Domain Identity Authentication Scheme Based on Blockchain in Vehicle to Grid [J]. Netinfo Security, 2024, 24(4): 587-601. |
| [2] | XUE Mingzhu, HU Liang, WANG Ming, WANG Feng. TAP Rule Processing System Based on Federated Learning and Blockchain Technology [J]. Netinfo Security, 2024, 24(3): 473-485. |
| [3] | ZHAI Peng, HE Jingsha, ZHANG Yu. An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment [J]. Netinfo Security, 2024, 24(2): 179-187. |
| [4] | HE Yefeng, QUAN Jiahui, LIU Yan. A Location Privacy Protection Scheme Based on Hybrid Blockchain [J]. Netinfo Security, 2024, 24(2): 229-238. |
| [5] | WU Haotian, LI Yifan, CUI Hongyan, DONG Lin. Federated Learning Incentive Scheme Based on Zero-Knowledge Proofs and Blockchain [J]. Netinfo Security, 2024, 24(1): 1-13. |
| [6] | ZHU Guocheng, HE Debiao, AN Haoyang, PENG Cong. The Proxy Voting Scheme Based on the Blockchain and SM9 Digital Signature [J]. Netinfo Security, 2024, 24(1): 36-47. |
| [7] | GONG Pengfei, XIE Sijiang, CHENG Andong. The Multi-Leader Consensus Algorithm Based on Improvements to HotStuff [J]. Netinfo Security, 2023, 23(9): 108-117. |
| [8] | ZHOU Quan, CHEN Minhui, WEI Kaijun, ZHENG Yulong. Blockchain Access Control Scheme with SM9-Based Attribute Encryption [J]. Netinfo Security, 2023, 23(9): 37-46. |
| [9] | ZHAO Jiahao, JIANG Jiajia, ZHANG Yushu. Cross-Chain Data Consistency Verification Model Based on Dynamic Merkle Hash Tree [J]. Netinfo Security, 2023, 23(9): 95-107. |
| [10] | SHAO Zhenzhe, JIANG Jiajia, ZHAO Jiahao, ZHANG Yushu. An Improved Weighted Byzantine Fault Tolerance Algorithm for Cross-Chain System [J]. Netinfo Security, 2023, 23(8): 109-120. |
| [11] | QIN Sihang, DAI Weiqi, ZENG Haiyan, GU Xianjun. Secure Sharing of Power Application Data Based on Blockchain [J]. Netinfo Security, 2023, 23(8): 52-65. |
| [12] | PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain [J]. Netinfo Security, 2023, 23(8): 76-85. |
| [13] | YU Huifang, QIAO Yifan, MENG Ru. Attribute-Based Anti-Quantum Threshold Ring Signcryption Scheme for Blockchain-Based Finance [J]. Netinfo Security, 2023, 23(7): 44-52. |
| [14] | ZHANG Xiaoxu, SHI Runhua. An Access Control Scheme for Verifying the Correctness of Outsourcing Encrypted Data in EHR System [J]. Netinfo Security, 2023, 23(5): 85-94. |
| [15] | GUO Rui, WEI Xin, CHEN Li. An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System [J]. Netinfo Security, 2023, 23(3): 1-12. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||