Netinfo Security ›› 2024, Vol. 24 ›› Issue (3): 473-485.doi: 10.3969/j.issn.1671-1122.2024.03.012
Previous Articles Next Articles
TAP Rule Processing System Based on Federated Learning and Blockchain Technology
XUE Mingzhu, HU Liang, WANG Ming, WANG Feng( )
)
- College of Computer Science and Technology, Jilin University, Changchun 130012, China
-
Received:2023-12-20Online:2024-03-10Published:2024-04-03 -
Contact:WANG Feng E-mail:wangfeng12@mails.jlu.edu.cn
CLC Number:
Cite this article
XUE Mingzhu, HU Liang, WANG Ming, WANG Feng. TAP Rule Processing System Based on Federated Learning and Blockchain Technology[J]. Netinfo Security, 2024, 24(3): 473-485.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.03.012
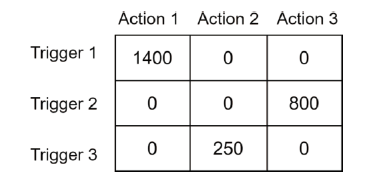
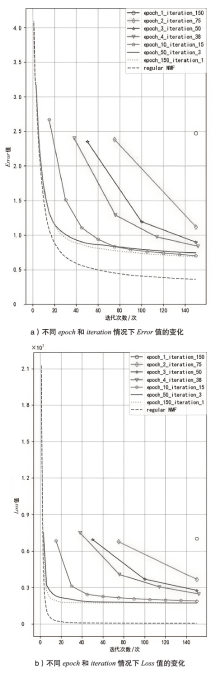
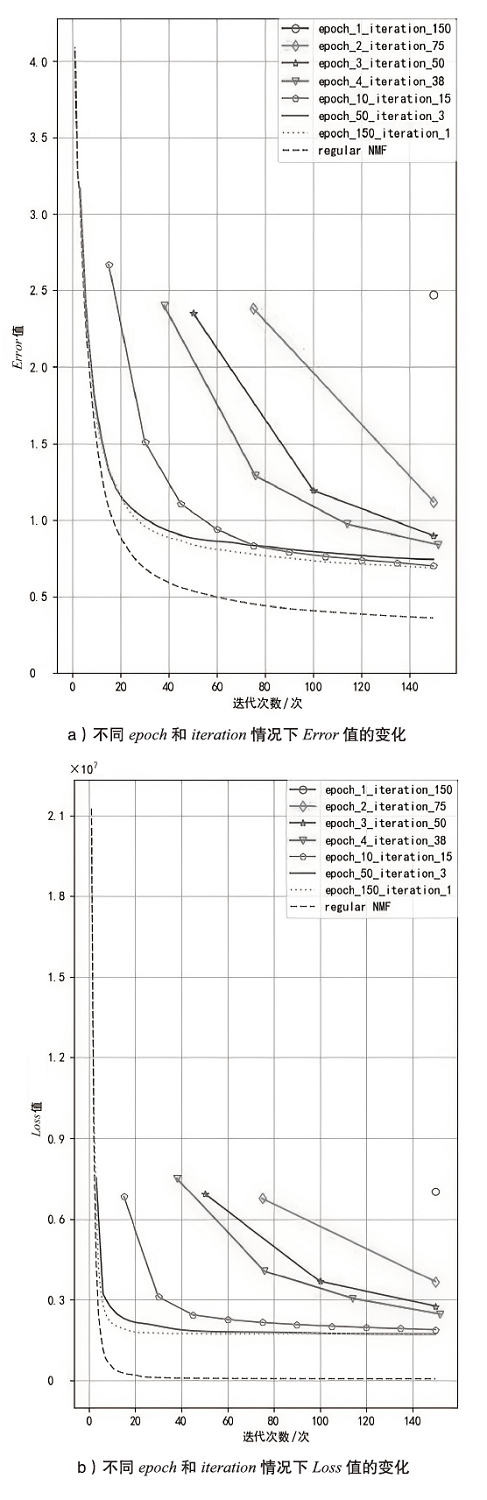
| 验证用户1 | 验证用户2 | 验证用户3 | 平均Error值 | |
|---|---|---|---|---|
| epoch_1_iteration_150 | 2.73 | 2.9 | 2.81 | 2.81 |
| epoch_2_iteration_75 | 1.83 | 1.88 | 1.86 | 1.86 |
| epoch_3_iteration_50 | 1.64 | 1.64 | 1.65 | 1.64 |
| epoch_4_iteration_38 | 1.58 | 1.57 | 1.59 | 1.58 |
| epoch_10_iteration_15 | 1.51 | 1.48 | 1.50 | 1.5 |
| epoch_50_iteration_3 | 1.53 | 1.51 | 1.54 | 1.53 |
| epoch_150_iteration_1 | 1.51 | 1.48 | 1.51 | 1.5 |
| regular NMF | 1.53 | 1.52 | 1.52 | 1.52 |
| [1] | WANG Ming, XING Yongheng, WANG Feng. Unsupervised Matrix Factorization Based Trigger Action Programming Rules Recommendation[J]. Netinfo Security, 2023, 23(2): 96-103. |
| 王明, 邢永恒, 王峰. 基于无监督非负矩阵分解的TAP规则推荐[J]. 信息网络安全, 2023, 23(2): 96-103. | |
| [2] |
CHAI Di, WANG Leye, CHEN Kai, et al. Secure Federated Matrix Factorization[J]. IEEE Intelligent Systems, 2020, 36(5): 11-20.
doi: 10.1109/MIS.2020.3014880 URL |
| [3] |
SHIN H, KIM S, SHIM J, et al. Privacy Enhanced Matrix Factorization for Recommendation with Local Differential Privacy[J]. IEEE Transactions on Knowledge and Data Engineering, 2018, 30(9): 1770-1782.
doi: 10.1109/TKDE.69 URL |
| [4] | KIM S, KIM J, KOO D, et al. Efficient Privacy-Preserving Matrix Factorization via Fully Homomorphic Encryption[C]// ACM. Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security. New York: ACM, 2016: 617-628. |
| [5] | GILLIS N. The Why and How of Nonnegative Matrix Factorization[J]. Regularization, Optimization, Kernels, and Support Vector Machines, 2014, 12(257): 257-291. |
| [6] | YANG Qiang, LIU Yang, CHEN Tianjian, et al. Federated Machine Learning: Concept and Applications[J]. ACM Transactions on Intelligent Systems and Technology (TIST), 2019, 10(2): 1-19. |
| [7] | FERNANDES E, RAHMATI A, JUNG J, et al. Decentralized Action Integrity for Trigger-Action IoT Platforms[C]// Internet Society. Proceedings 2018 Network and Distributed System Security Symposium. San Diego: Network and Distributed System Security Symposium, 2018: 1-16. |
| [8] | CHEN Yunang, CHOWDHURY A R, WANG Ruizhe, et al. Data Privacy in Trigger-Action Systems[C]// IEEE. 2021 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2021: 501-518. |
| [9] |
BREVE B, CIMINO G, DEUFEMIA V. Identifying Security and Privacy Violation Rules in Trigger-Action IoT Platforms with NLP Models[J]. IEEE Internet of Things Journal, 2022, 10(6): 5607-5622.
doi: 10.1109/JIOT.2022.3222615 URL |
| [10] | MCMAHAN B, MOORE E, RAMAGE D, et al. Communication-Efficient Learning of Deep Networks from Decentralized Data[C]// PMLR.Artificial Intelligence and Statistics. New York: PMLR, 2017: 1273-1282. |
| [11] |
SUN Rui, LI Chao, WANG Wei, et al. Research Progress of Blockchain-Based Federated Learning[J]. Journal of Computer Applications, 2022, 42(11): 3413-3420.
doi: 10.11772/j.issn.1001-9081.2021111934 |
|
孙睿, 李超, 王伟, 等. 基于区块链的联邦学习研究进展[J]. 计算机应用, 2022, 42(11): 3413-3420.
doi: 10.11772/j.issn.1001-9081.2021111934 |
|
| [12] |
AONO Y, HAYASHI T, WANG Lihua, et al. Privacy-Preserving Deep Learning via Additively Homomorphic Encryption[J]. IEEE Transactions on Information Forensics and Security, 2017, 13(5): 1333-1345.
doi: 10.1109/TIFS.2017.2787987 URL |
| [13] |
KIM H, PARK J, BENNIS M, et al. Blockchained On-Device Federated Learning[J]. IEEE Communications Letters, 2019, 24(6): 1279-1283.
doi: 10.1109/COML.4234 URL |
| [14] | BOGDANOV D, LAUR S, WILLEMSON J. Sharemind: A Framework for Fast Privacy-Preserving Computations[C]// ESORICS.Computer Security-ESORICS 2008: 13th European Symposium on Research in Computer Security. Heidelberg: Springer, 2008: 192-206. |
| [15] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. (2019-07-17)[2023-12-19]. https://bitcoin.org/bitcoin.pdf. |
| [16] | XIAO Yang, ZHANG Ning, LOU Wenjing, et al. A Survey of Distributed Consensus Protocols for Blockchain Networks[J]. IEEE Communications Surveys & Tutorials, 2020, 22(2): 1432-1465. |
| [17] | SAAD S M S, RADZI R Z R M. Comparative Review of the Blockchain Consensus Algorithm between Proof of Stake (PoS) and Delegated Proof of Stake (DPoS)[ J]. International Journal of Innovative Computing, 2020, 10(2): 27-32. |
| [18] |
LAMPORT L, SHOSTAK R, PEASE M. The Byzantine Generals Problem[J]. ACM Transactions on Programming Languages and Systems, 1982, 4(3): 382-401.
doi: 10.1145/357172.357176 URL |
| [19] | CASTRO M, LISKOV B. Practical Byzantine Fault Tolerance[C]// USENIX. Proceedings of the Third Symposium on Operating Systems Design and Implementation. Berkeley: USENIX, 1999: 173-186. |
| [20] | FURUKAWA J, LINDELL Y, NOF A, et al. High-Throughput Secure Three-Party Computation for Malicious Adversaries and an Honest Majority[C]// IACR. Annual International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2017: 225-255. |
| [21] | KOGIAS E K, JOVANOVIC P, GAILLY N, et al. Enhancing Bitcoin Security and Performance with Strong Consistency via Collective Signing[C]// USENIX. 25th Usenix Security Symposium (Usenix Security 16). Berkeley: USENIX, 2016: 279-296. |
| [22] |
ZHENG Zibin, XIE Shaoan, DAI Hongning, et al. Blockchain Challenges and Opportunities: A Survey[J]. International Journal of Web and Grid Services, 2018, 14(4): 352-375.
doi: 10.1504/IJWGS.2018.095647 URL |
| [23] | ZHANG Yu, WEN Jiangtao. An IoT Electric Business Model Based on the Protocol of Bitcoin[C]// IEEE.2015 18th International Conference on Intelligence in Next Generation Networks. New York: IEEE, 2015: 184-191. |
| [24] | JIN Ming. Research on Key Technologies of Federated Learning Based on Blockchain[D]. Harbin:Harbin Engineering University, 2021. |
| 金明. 基于区块链的联邦学习关键技术研究[D]. 哈尔滨: 哈尔滨工程大学, 2021. |
| [1] | ZHAI Peng, HE Jingsha, ZHANG Yu. An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment [J]. Netinfo Security, 2024, 24(2): 179-187. |
| [2] | HE Yefeng, QUAN Jiahui, LIU Yan. A Location Privacy Protection Scheme Based on Hybrid Blockchain [J]. Netinfo Security, 2024, 24(2): 229-238. |
| [3] | LIN Yihang, ZHOU Pengyuan, WU Zhiqian, LIAO Yong. Federated Learning Backdoor Defense Method Based on Trigger Inversion [J]. Netinfo Security, 2024, 24(2): 262-271. |
| [4] | JIN Zhigang, DING Yu, WU Xiaodong. Federated Intrusion Detection Algorithm with Bilateral Correction Merging Gradient Difference [J]. Netinfo Security, 2024, 24(2): 293-302. |
| [5] | WU Haotian, LI Yifan, CUI Hongyan, DONG Lin. Federated Learning Incentive Scheme Based on Zero-Knowledge Proofs and Blockchain [J]. Netinfo Security, 2024, 24(1): 1-13. |
| [6] | ZHU Guocheng, HE Debiao, AN Haoyang, PENG Cong. The Proxy Voting Scheme Based on the Blockchain and SM9 Digital Signature [J]. Netinfo Security, 2024, 24(1): 36-47. |
| [7] | ZHAO Jia, YANG Bokai, RAO Xinyu, GUO Yating. Design and Implementation of Tor Traffic Detection Algorithm Based on Federated Learning [J]. Netinfo Security, 2024, 24(1): 60-68. |
| [8] | XU Ruzhi, DAI Lipeng, XIA Diya, YANG Xin. Research on Centralized Differential Privacy Algorithm for Federated Learning [J]. Netinfo Security, 2024, 24(1): 69-79. |
| [9] | LAI Chengzhe, ZHAO Yining, ZHENG Dong. A Privacy Preserving and Verifiable Federated Learning Scheme Based on Homomorphic Encryption [J]. Netinfo Security, 2024, 24(1): 93-105. |
| [10] | GONG Pengfei, XIE Sijiang, CHENG Andong. The Multi-Leader Consensus Algorithm Based on Improvements to HotStuff [J]. Netinfo Security, 2023, 23(9): 108-117. |
| [11] | ZHOU Quan, CHEN Minhui, WEI Kaijun, ZHENG Yulong. Blockchain Access Control Scheme with SM9-Based Attribute Encryption [J]. Netinfo Security, 2023, 23(9): 37-46. |
| [12] | ZHAO Jiahao, JIANG Jiajia, ZHANG Yushu. Cross-Chain Data Consistency Verification Model Based on Dynamic Merkle Hash Tree [J]. Netinfo Security, 2023, 23(9): 95-107. |
| [13] | SHAO Zhenzhe, JIANG Jiajia, ZHAO Jiahao, ZHANG Yushu. An Improved Weighted Byzantine Fault Tolerance Algorithm for Cross-Chain System [J]. Netinfo Security, 2023, 23(8): 109-120. |
| [14] | QIN Sihang, DAI Weiqi, ZENG Haiyan, GU Xianjun. Secure Sharing of Power Application Data Based on Blockchain [J]. Netinfo Security, 2023, 23(8): 52-65. |
| [15] | PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain [J]. Netinfo Security, 2023, 23(8): 76-85. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||