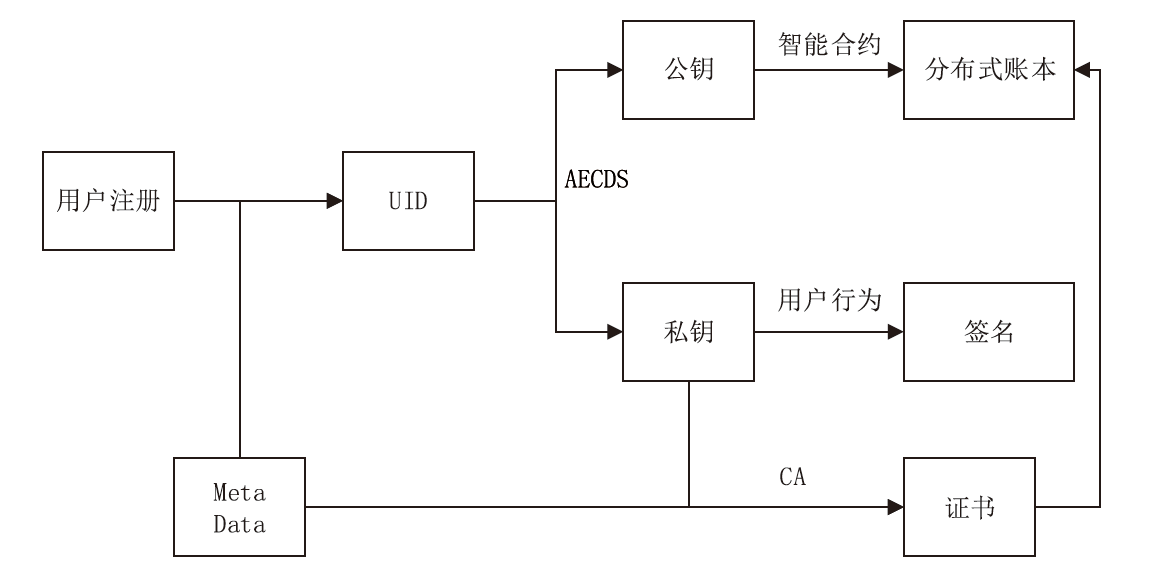
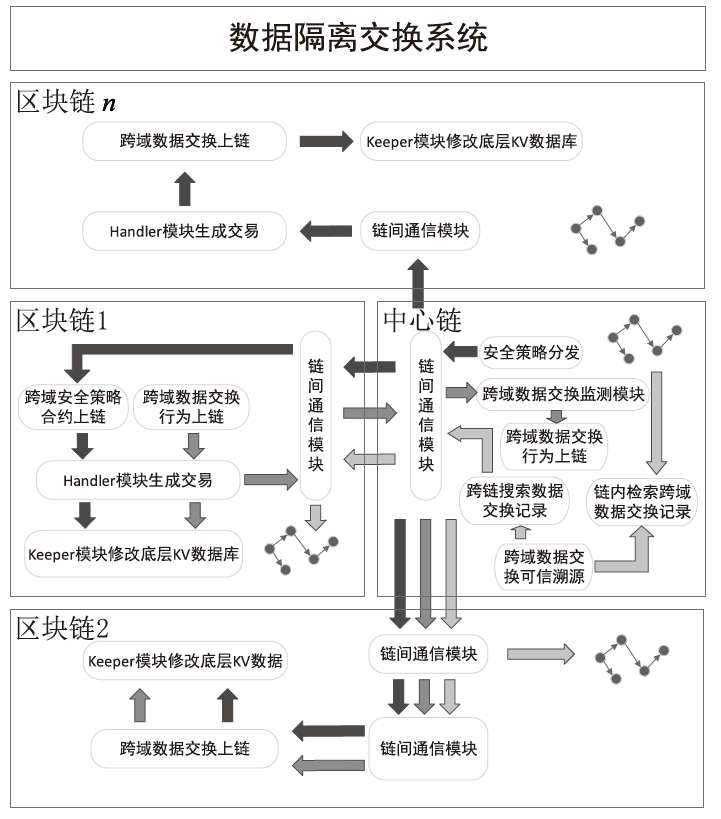
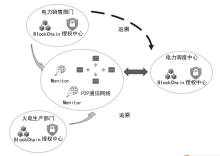
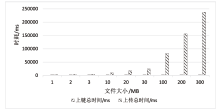
Netinfo Security ›› 2023, Vol. 23 ›› Issue (8): 52-65.doi: 10.3969/j.issn.1671-1122.2023.08.005
Previous Articles Next Articles
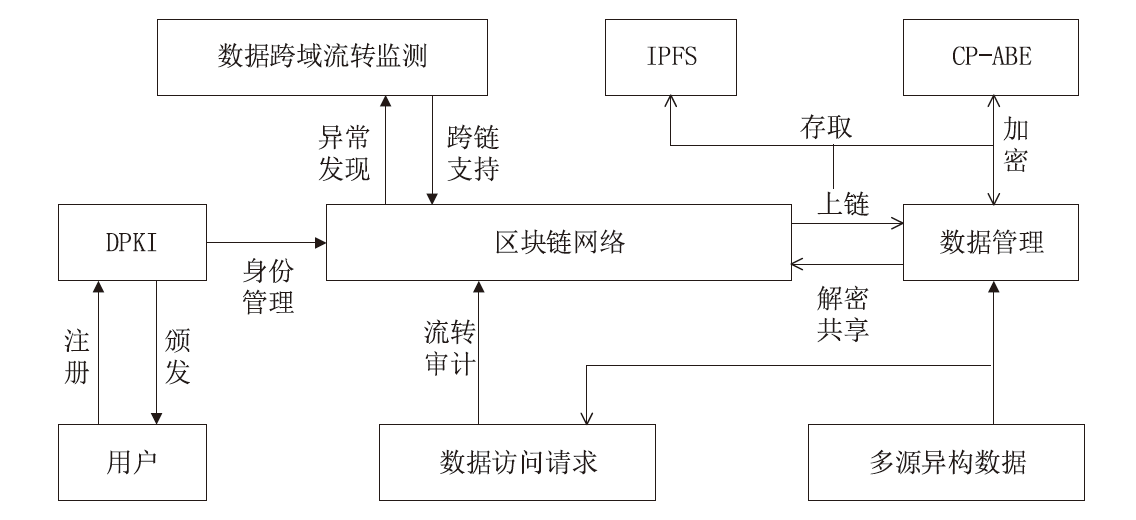
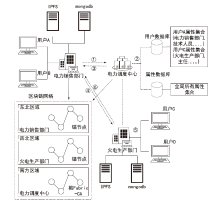
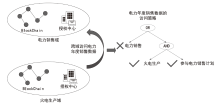
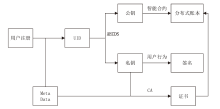
Secure Sharing of Power Application Data Based on Blockchain
QIN Sihang1,2,3,4, DAI Weiqi1,2,3( ), ZENG Haiyan4, GU Xianjun4
), ZENG Haiyan4, GU Xianjun4
- 1. School of Cyber Science and Engineering, Huazhong University of Science and Technology, Wuhan 430074, China
2. Hubei Key Laboratory of Distributed System Security, Wuhan 430074, China
3. Hubei Engineering Research Center on Big Data Security, Wuhan 430074, China
4. Wuhan Power Supply Company of State Grid Hubei Electric Power Co., Ltd., Wuhan 430010, China
-
Received:2023-05-20Online:2023-08-10Published:2023-08-08 -
Contact:DAI Weiqi E-mail:wqdai@hust.edu.cn
CLC Number:
Cite this article
QIN Sihang, DAI Weiqi, ZENG Haiyan, GU Xianjun. Secure Sharing of Power Application Data Based on Blockchain[J]. Netinfo Security, 2023, 23(8): 52-65.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.08.005
| [1] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. (2008-10-31)[2023-05-16]. https://bitcoin.org/bitcoin.pdf. |
| [2] |
DAI Chuangchuang, LUAN Haijing, YANG Xueying, et al. Overview of Blockchain Technology[J]. Computer Science, 2021, 48(11A): 500-508.
doi: 10.11896/jsjkx.201200163 |
|
代闯闯, 栾海晶, 杨雪莹, 等. 区块链技术研究综述[J]. 计算机科学, 2021, 48(11A):500-508.
doi: 10.11896/jsjkx.201200163 |
|
| [3] | LIU Mingda, CHEN Zuoning, SHI Yijuan, et al. Research Progress of Blockchain in Data Security[J]. Chinese Journal of Computers, 2021, 44(1): 1-27. |
| 刘明达, 陈左宁, 拾以娟, 等. 区块链在数据安全领域的研究进展[J]. 计算机学报, 2021, 44(1):1-27. | |
| [4] | LIANG Hejun, HAN Jingti. Research on Decentralized Transaction Consensus Mechanism of Cloud Computing Resources Based on Block Chain[J]. Computer Science, 2019, 46(11A): 548-552. |
| 梁贺君, 韩景倜. 基于区块链的云计算资源去中心化交易共识机制研究[J]. 计算机科学, 2019, 46(11A): 548-552. | |
| [5] | ALI M, KARIMIPOUR H, TARIQ M. Integration of Blockchain and Federated Learning for Internet of Things: Recent Advances and Future Challenges[EB/OL]. (2021-06-18)[2023-05-16]. https://www.sciencedirect.com/science/article/abs/pii/S0167404821001796. |
| [6] | ZHU Linkai, PENG Sheng, CAI Zhiming, et al. Research on Privacy Data Protection Based on Trusted Computing and Blockchain[J]. Security and Communication Networks, 2021(1): 1-9. |
| [7] |
LI Ting, KHAN M, SHARMA A, et al. A Secure Framework for IoT-Based Smart Climate Agriculture System: Toward Blockchain and Edge Computing[J]. Journal of Intelligent Systems, 2022, 31(1): 221-236.
doi: 10.1515/jisys-2022-0012 URL |
| [8] |
XU Guangxia, ZHANG Jiajun, CLIFF U G O, et al. An Efficient Blockchain-Based Privacy-Preserving Scheme with Attribute and Homomorphic Encryption[J]. International Journal of Intelligent Systems, 2022, 37(12): 10715-10750.
doi: 10.1002/int.v37.12 URL |
| [9] |
QIU Jing, TIAN Zhihong, DU Chunlai, et al. A Survey on Access Control in the Age of Internet of Things[J]. IEEE Internet of Things Journal, 2020, 7(6): 4682-4696.
doi: 10.1109/JIoT.6488907 URL |
| [10] | DHARANI J, SUNDARAKANTHAM K, SINGH K, et al. A Privacy-Preserving Framework for Endorsement Process in Hyperledger Fabric[EB/OL]. (2022-03-11)[2023-05-16]. https://www.sciencedirect.com/science/article/abs/pii/S0167404822000360. |
| [11] | YU Kechen, GUO Li, YAO Mengmeng. Design of Blockchain-Based High-Value Data Sharing System[J]. Netinfo Security, 2021, 21(11): 75-84. |
| 于克辰, 郭莉, 姚萌萌. 基于区块链的高价值数据共享系统设计[J]. 信息网络安全, 2021, 21(11):75-84. | |
| [12] |
HASSIJA V, CHAMOLA V, GARG S, et al. A Blockchain-Based Framework for Lightweight Data Sharing and Energy Trading in V2G Network[J]. IEEE Transactions on Vehicular Technology, 2020, 69(6): 5799-5812.
doi: 10.1109/TVT.25 URL |
| [13] | ZHANG Lihua, CAO Yu, ZHANG Ganzhe, et al. A Blockchain-Based Microgrid Data Disaster Backup Scheme in Edge Computing[J]. Security and Communication Networks, 2021, 2021(1): 1-19. |
| [14] | ZHANG Meng, WANG Shen, ZHANG Pan, et al. Protecting Data Privacy for Permissioned Blockchains Using Identity-Based Encryption[C]// IEEE. Electronic and Automation Control Conference (ITNEC). New York: IEEE, 2019: 602-605. |
| [15] |
WANG Ze, LIN Jingqiang, CAI Quanwei, et al. Blockchain-Based Certificate Transparency and Revocation Transparency[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 19(1): 681-697.
doi: 10.1109/TDSC.2020.2983022 URL |
| [16] | GUY Z, OZ N, ALEX S, et al. Decentralizing Privacy:Using Blockchain to Protect Personal Data[C]// IEEE. IEEE Security and Privacy Workshops. New York: IEEE, 2015: 180-184. |
| [17] |
SUN Hao, MAO Hanyu, ZHANG Yanfeng, et al. Development and Application of Blockchain Cross-Chain Technology[J]. Computer Science, 2022, 49(5): 287-295.
doi: 10.11896/jsjkx.210800132 |
|
孙浩, 毛瀚宇, 张岩峰, 等. 区块链跨链技术发展及应用[J]. 计算机科学, 2022, 49(5):287-295.
doi: 10.11896/jsjkx.210800132 |
|
| [18] |
YIN Zeyuan, ZHANG Bingsheng, XU Jingzhong, et al. Bool Network: An Open, Distributed, Secure Cross-Chain Notary Platform[J]. IEEE Transactions on Information Forensics and Security, 2022, 17(1): 3465-3478.
doi: 10.1109/TIFS.2022.3209546 URL |
| [19] | LIN Shaofeng, KONG Yihan, NIE Shaotao, et al. Research on Cross-Chain Technology of Blockchain[C]//IEEE. 6th International Conference on Smart Grid and Electrical Automation (ICSGEA). New York: IEEE, 2021: 405-408. |
| [20] |
ZHANG Chaodong, WANG Baosheng, DENG Wenping. Design of Supply Chain Traceability System Based on Side Chain Technology[J]. Computer Engineering, 2019, 45(11): 1-8.
doi: 10.19678/j.issn.1000-3428.0055286 |
|
张朝栋, 王宝生, 邓文平. 基于侧链技术的供应链溯源系统设计[J]. 计算机工程, 2019, 45(11): 1-8.
doi: 10.19678/j.issn.1000-3428.0055286 |
|
| [21] | LI Zujian, ZHANG Zhihong. Research and Implementation of Multi-Chain Digital Wallet Based on Hash TimeLock[C]//Springer. Blockchain and Trustworthy Systems-First International Conference, BlockSys. Berlin: Springer, 2020: 175-182. |
| [22] |
YE Shaojie, WANG Xiaoyi, XU Caichao, et al. BitXHub: Side-Relay Chain Based Heterogeneous Blockchain Interoperable Platform[J]. Computer Science, 2020, 47(6): 294-302.
doi: 10.11896/jsjkx.191100055 |
|
叶少杰, 汪小益, 徐才巢, 等. BitXHub:基于侧链中继的异构区块链互操作平台[J]. 计算机科学, 2020, 47(6):294-302.
doi: 10.11896/jsjkx.191100055 |
| [1] | GONG Pengfei, XIE Sijiang, CHENG Andong. The Multi-Leader Consensus Algorithm Based on Improvements to HotStuff [J]. Netinfo Security, 2023, 23(9): 108-117. |
| [2] | ZHOU Quan, CHEN Minhui, WEI Kaijun, ZHENG Yulong. Blockchain Access Control Scheme with SM9-Based Attribute Encryption [J]. Netinfo Security, 2023, 23(9): 37-46. |
| [3] | ZHAO Jiahao, JIANG Jiajia, ZHANG Yushu. Cross-Chain Data Consistency Verification Model Based on Dynamic Merkle Hash Tree [J]. Netinfo Security, 2023, 23(9): 95-107. |
| [4] | SHAO Zhenzhe, JIANG Jiajia, ZHAO Jiahao, ZHANG Yushu. An Improved Weighted Byzantine Fault Tolerance Algorithm for Cross-Chain System [J]. Netinfo Security, 2023, 23(8): 109-120. |
| [5] | PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain [J]. Netinfo Security, 2023, 23(8): 76-85. |
| [6] | YU Huifang, QIAO Yifan, MENG Ru. Attribute-Based Anti-Quantum Threshold Ring Signcryption Scheme for Blockchain-Based Finance [J]. Netinfo Security, 2023, 23(7): 44-52. |
| [7] | GUO Rui, WEI Xin, CHEN Li. An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System [J]. Netinfo Security, 2023, 23(3): 1-12. |
| [8] | LI Chunxiao, WANG Yaofei, XU Enliang, ZHAO Yu. Enabling Privacy-Preserving Range Queries in Blockchain-Based Collaborative Databases with Bilinear Pairings [J]. Netinfo Security, 2023, 23(3): 22-34. |
| [9] | ZHANG Xuewang, ZHANG Hao, YAO Yaning, FU Jiali. Privacy Protection Scheme of Consortium Blockchain Based on Group Signature and Homomorphic Encryption [J]. Netinfo Security, 2023, 23(3): 56-61. |
| [10] | WANG Jingyu, MA Zhaofeng, XU Danheng, DUAN Pengfei. Blockchain Transaction Data Privacy-Preserving Scheme Supporting National Cryptographic Algorithm [J]. Netinfo Security, 2023, 23(3): 84-95. |
| [11] | FENG Yiting, MA Zhaofeng, XU Danheng, DUAN Pengfei. Evaluation Method for Cross-Chain Security Strength Access [J]. Netinfo Security, 2023, 23(1): 84-92. |
| [12] | ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism [J]. Netinfo Security, 2022, 22(9): 46-54. |
| [13] | ZHANG Yujian, LIU Daifu, TONG Fei. Reentrancy Vulnerability Detection in Smart Contracts Based on Local Graph Matching [J]. Netinfo Security, 2022, 22(8): 1-7. |
| [14] | HU Yi, SHE Kun. Blockchain and Smart Contract Based Dual-Chain Internet of Vehicles System [J]. Netinfo Security, 2022, 22(8): 26-35. |
| [15] | HUANG Baohua, ZHAO Weihong, PENG Li, XIE Tongyi. Efficient Blockchain PKI Model Based on MPT Index [J]. Netinfo Security, 2022, 22(8): 72-80. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||