Netinfo Security ›› 2024, Vol. 24 ›› Issue (4): 640-649.doi: 10.3969/j.issn.1671-1122.2024.04.013
Previous Articles Next Articles
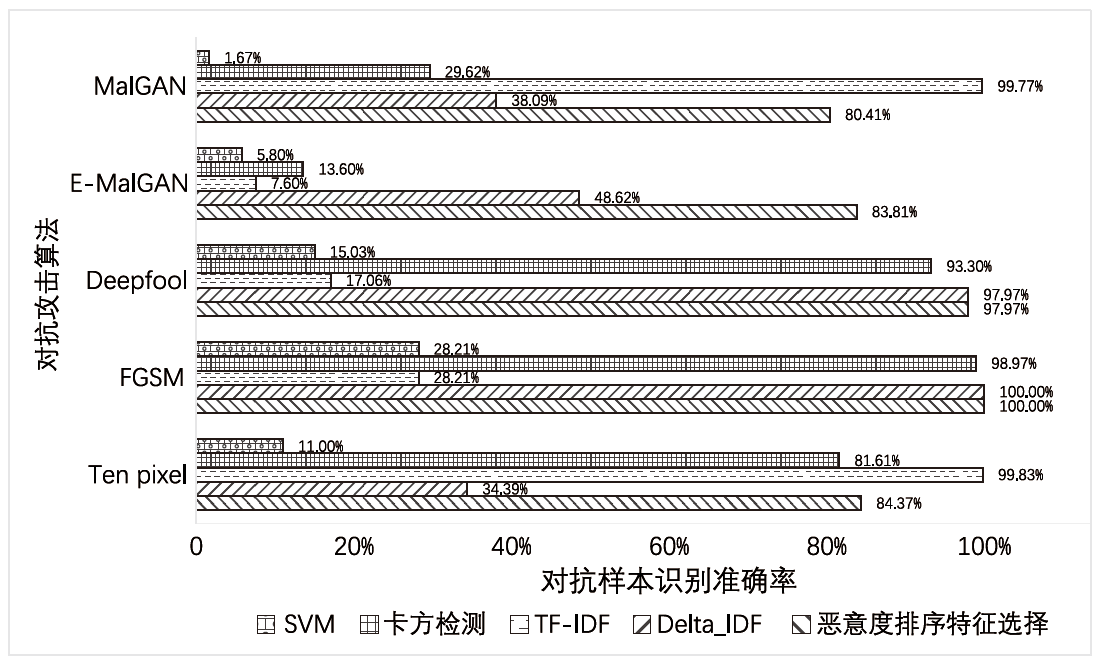
Malicious Software Adversarial Defense Model Based on Feature Severity Ranking
XU Zirong, GUO Yanping, YAN Qiao( )
)
- College of Computer Science and Software Engineering, Shenzhen University, Shenzhen 518060, China
-
Received:2023-11-14Online:2024-04-10Published:2024-05-16
CLC Number:
Cite this article
XU Zirong, GUO Yanping, YAN Qiao. Malicious Software Adversarial Defense Model Based on Feature Severity Ranking[J]. Netinfo Security, 2024, 24(4): 640-649.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.04.013
| [1] | CHRISTIAAN B, SANDEEP C, TAYLOR D, et al. McAfee Labs Threats Report: November 2020[EB/OL]. (2020-11-10)[2023-11-10]. https://www.trellix.com/enterprise/zh-cn/assets/reports/rp-quarterly-threats-nov-2020.pdf. |
| [2] | GOODFELLOW I J, SHLENS J, SZEGEDY C. Explaining and Harnessing Adversarial Examples[EB/OL]. (2014-12-20)[2023-11-10]. https://arxiv.org/abs/1412.6572. |
| [3] | FENG Yu, ANAND S, DILLIG I, et al. Apposcopy: Semantics-Based Detection of Android Malware through Static Analysis[C]// ACM. 22nd ACM SIGSOFT International Symposium on the Foundations of Software Engineering. New York: ACM, 2014: 576-587. |
| [4] | FENG Yu, BASTANI O, MARTINS R, et al. Automated Synthesis of Semantic Malware Signatures Using Maximum Satisfiability[EB/OL]. (2016-08-22)[2023-11-10]. https://arxiv.org/abs/1608.06254. |
| [5] | ARZT S, RASTHOFER S, FRITZ C, et al. FlowDroid: Precise Context, Flow, Field, Object-Sensitive and Lifecycle-Aware Taint Analysis for Android Apps[J]. ACM SIGPLAN Notices, 2014, 49(6): 259-269. |
| [6] | PANDITA R, XIAO Xusheng, YANG Wei, et al. WHYPER: Towards Automating Risk Assessment of Mobile Applications[C]// USENIX. 22nd USENIX Security Symposium (USENIX Security 13). Berkeley: USENIX, 2013: 527-542. |
| [7] | TEUFL P, FERK M, FITZEK A, et al. Malware Detection by Applying Knowledge Discovery Processes to Application Metadata on the Android Market (Google Play)[J]. Security & Communication Networks, 2016, 9(5): 389-419. |
| [8] | ZHANG Mu, DUAN Yue, YIN Heng, et al. Semantics-Aware Android Malware Classification Using Weighted Contextual API Dependency Graphs[C]// ACM. 2014 ACM SIGSAC Conference on Computer and Communications Security(CCS). New York: ACM, 2014: 1105-1116. |
| [9] | YUAN Zhenlong, LU Yongqiang, WANG Zhaoguo, et al. Droid-Sec: Deep Learning in Android Malware Detection[J]. ACM SIGCOMM Computer Communication Review, 2014, 44(4): 371-372. |
| [10] | PEYNIRCI G, EMINAĞAOĞLU M, KARABULUT K. Feature Selection for Malware Detection on the Android Platform Based on Differences of IDF Values[J]. Journal of Computer Science and Technology, 2020, 35(4): 946-962. |
| [11] | CHEN Sen, XUE Minhui, FAN Lingling, et al. Automated Poisoning Attacks and Defenses in Malware Detection Systems: An Adversarial Machine Learning Approach[J]. Computers & Security, 2018(73): 326-344. |
| [12] | LI Xiangjun, KONG Ke, XU Su, et al. Feature Selection-Based Android Malware Adversarial Sample Generation and Detection Method[J]. IET Information Security, 2021, 15(6): 401-416. |
| [13] | HU Weiwei, TAN Ying. Generating Adversarial Malware Examples for Black-Box Attacks Based on GAN[C]// Springer. Data Mining and Big Data-7th International Conference (DMBD 2022). Heidelberg: Springer, 2022: 409-423. |
| [14] | KAWAI M, OTA K, DONG Mianxing. Improved MalGAN: Avoiding Malware Detector by Leaning Cleanware Features[C]// IEEE. The 1st International Conference on Artificial Intelligence in Information and Communication (ICAIIC). New York: IEEE, 2019: 40-45. |
| [15] | LI Heng, ZHOU Shiyao, YUAN Wei, et al. Adversarial-Example Attacks Toward Android Malware Detection System[J]. IEEE Systems Journal, 2019, 14(1): 653-656. |
| [16] | ONWUZURIKE L, MARICONTI E, ANDRIOTIS P, et al. MaMaDroid: Detecting Android Malware by Building Markov Chains of Behavioral Models (Extended Version)[J]. ACM Transaction on Information and System Security, 2019, 22(2): 1-34. |
| [17] | CHEN Xiao, LI Chaoran, WANG Derui, et al. Android HIV: A Study of Repackaging Malware for Evading Machine-Learning Detection[J]. IEEE Transactions on Information Forensics and Security, 2019(15): 987-1001. |
| [18] | PAPERNOT N, MCDANIEL P, JHA S, et al. The Limitations of Deep Learning in Adversarial Settings[C]// IEEE. The 1st IEEE European Symposium on Security and Privacy (Euro S&P). New York: IEEE, 2016: 372-387. |
| [19] | CARLINI N, WAGNER D. Towards Evaluating the Robustness of Neural Networks[C]// IEEE. The 38th IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2017: 39-57. |
| [20] | SZEGEDY C, ZAREMBA W, SUTSKEVER I, et al. Intriguing Properties of Neural Networks[EB/OL]. (2014-02-19)[2023-11-10]. https://arxiv.org/abs/1312.6199. |
| [21] | RATHORE H, SAHAY S K, NIKAM P, et al. Robust Android Malware Detection System against Adversarial Attacks Using Q-Learning[J]. Information Systems Frontiers, 2021, 23(4): 867-882. |
| [22] | RATHORE H, SAHAY S K, DHILLON J, et al. Designing Adversarial Attack and Defence for Robust Android Malware Detection Models[C]// IEEE. The 51st Annual IEEE/IFIP International Conference on Dependable Systems and Networks(DSN). New York: IEEE, 2021: 29-32. |
| [23] | TAHERI R, JAVIDAN R, POORANIAN Z. Adversarial Android Malware Detection for Mobile Multimedia Applications in IoT Environments[J]. Multimedia Tools and Applications, 2021, 80(11): 16713-16729. |
| [24] | CHEN Yiming, YANG C H, CHEN G C. Using Generative Adversarial Networks for Data Augmentation in Android Malware Detection[C]// IEEE. The 2021 IEEE Conference on Dependable and Secure Computing(DSC). New York: IEEE, 2021: 1-8. |
| [25] | LI Heng, ZHOU Shiyao, YUAN Wei, et al. Robust Android Malware Detection against Adversarial Example Attacks[C]// ACM. The Web Conference 2021 (WWW’21). New York: ACM, 2021: 3603-3612. |
| [26] | CHEN Lingwei, HOU Shifu, YE Yanfang. SecureDroid: Enhancing Security of Machine Learning-Based Detection against Adversarial Android Malware Attacks[C]// ACM. The 33rd Annual Computer Security Applications Conference (ACSAC’17). New York: ACM, 2017: 362-372. |
| [27] | CLINE W C, MANDAR D B, SIDDHARTH A B, et al. DefenseDroid: A Modern Approach to Android Malware Detection[EB/OL]. (2021-12-07)[2023-11-10]. https://github.com/DefenseDroid/DefenseDroid. |
| [28] | MAHDAVIFAR S, KADIR A F A, FATEMI R, et al. Dynamic Android Malware Category Classification Using Semi-Supervised Deep Learning[C]// IEEE. 2020 IEEE International Conference on Dependable, Autonomic and Secure Computing, International Conference on Pervasive Intelligence and Computing, International Conference on Cloud and Big Data Computing, International Conference on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech). New York: IEEE, 2020: 515-522. |
| [29] | MAHDAVIFAR S, ALHADIDI D, GHORBANI A. Effective and Efficient Hybrid Android Malware Classification Using Pseudo-Label Stacked Auto-Encoder[J]. Journal of Network and Systems Management, 2022, 30(1): 1-34. |
| [30] | WANG Haoyu, SI Junjun, LI Hao, et al. RmvDroid: Towards a Reliable Android Malware Dataset with App Metadata[C]// IEEE. 16th International Conference on Mining Software Repositories (MSR2019). New York: IEEE, 2019: 404-408. |
| [31] | ALLIX K, BISSYANDÉ T F, KLEIN J, et al. AndroZoo: Collecting Millions of Android Apps for the Research Community[C]// IEEE. 2016 IEEE/ACM 13th International Conference on Mining Software Repositories (MSR2016). New York: IEEE, 2016: 468-471. |
| [32] | MOOSAVI-DEZFOOLI S M, FAWZI A, FROSSARD P. Deepfool: A Simple and Accurate Method to Fool Deep Neural Networks[C]// IEEE. 2016 IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2016: 2574-2582. |
| [33] | SU Jiawei, VARGAS D V, SAKURAI K. One Pixel Attack for Fooling Deep Neural Networks[J]. IEEE Transactions on Evolutionary Computation, 2019, 23(5): 828-841. |
| [34] | WILSON E B, HILFERTY M M. The Distribution of Chi-Square[J]. National Academy of Sciences of the United States of America, 1931, 17(12): 684-688. |
| [35] | HIEMSTRA D. A Probabilistic Justification for Using TF×IDF Term Weighting in Information Retrieval[J]. International Journal on Digital Libraries, 2000, 3(2): 131-139. |
| [1] | ZHANG Guanghua, LIU Yichun, WANG He, HU Boning. Defense Scheme for Removing Deep Neural Network Backdoors Based on JSMA Adversarial Attacks [J]. Netinfo Security, 2024, 24(4): 545-554. |
| [2] | ZHONG Jing, FANG Bing, ZHU Jiang. Recent Research of Feature Selection Algorithms Based on Sparse Matrix Structure [J]. Netinfo Security, 2024, 24(3): 352-362. |
| [3] | YANG Zhipeng, LIU Daidong, YUAN Junyi, WEI Songjie. Research on Network Local Security Situation Fusion Method Based on Self-Attention Mechanism [J]. Netinfo Security, 2024, 24(3): 398-410. |
| [4] | JIANG Rong, LIU Haitian, LIU Cong. Unsupervised Network Intrusion Detection Method Based on Ensemble Learning [J]. Netinfo Security, 2024, 24(3): 411-426. |
| [5] | FENG Guangsheng, JIANG Shunpeng, HU Xianlang, MA Mingyu. New Research Progress on Intrusion Detection Techniques for the Internet of Things [J]. Netinfo Security, 2024, 24(2): 167-178. |
| [6] | ZHAO Pengcheng, YU Junqing, LI Dong. An Optimal Algorithm for Traffic Scheduling in SRv6 Network Based on Deep Learning [J]. Netinfo Security, 2024, 24(2): 272-281. |
| [7] | JIN Zhigang, DING Yu, WU Xiaodong. Federated Intrusion Detection Algorithm with Bilateral Correction Merging Gradient Difference [J]. Netinfo Security, 2024, 24(2): 293-302. |
| [8] | XUE Yu, ZHANG Yixuan. Survey on Deep Neural Architecture Search [J]. Netinfo Security, 2023, 23(9): 58-74. |
| [9] | SHEN Hua, TIAN Chen, GUO Sensen, MU Zhiying. Research on Adversarial Machine Learning-Based Network Intrusion Detection Method [J]. Netinfo Security, 2023, 23(8): 66-75. |
| [10] | LI Chenwei, ZHANG Hengwei, GAO Wei, YANG Bo. Transferable Image Adversarial Attack Method with AdaN Adaptive Gradient Optimizer [J]. Netinfo Security, 2023, 23(7): 64-73. |
| [11] | LIU Yuxiao, CHEN Wei, ZHANG Tianyue, WU Lifa. Explainable Anomaly Traffic Detection Based on Sparse Autoencoders [J]. Netinfo Security, 2023, 23(7): 74-85. |
| [12] | JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion [J]. Netinfo Security, 2023, 23(7): 86-97. |
| [13] | ZHAO Caidan, CHEN Jingqian, WU Zhiqiang. Automatic Modulation Recognition Algorithm Based on Multi-Channel Joint Learning [J]. Netinfo Security, 2023, 23(4): 20-29. |
| [14] | TAN Liuyan, RUAN Shuhua, YANG Min, CHEN Xingshu. Educational Data Classification Based on Deep Learning [J]. Netinfo Security, 2023, 23(3): 96-102. |
| [15] | XU Zhanyang, CHENG Luofei, CHENG Jianchun, XU Xiaolong. A Scheme of Optimizing Deep Learning Model Using Bi-ADMM [J]. Netinfo Security, 2023, 23(2): 54-63. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||