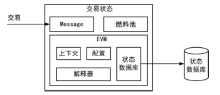
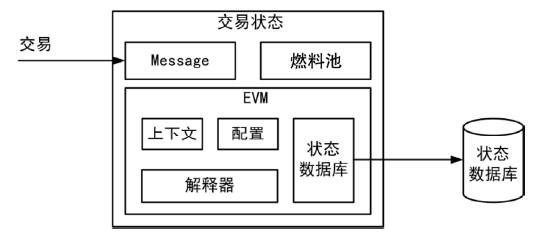
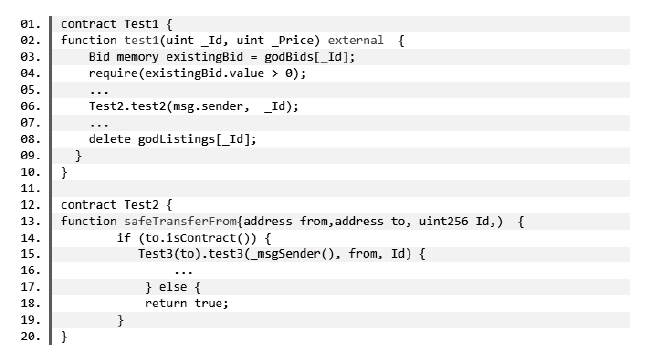
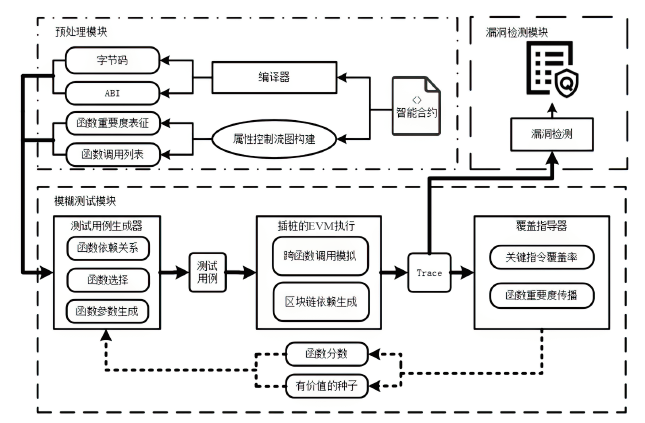
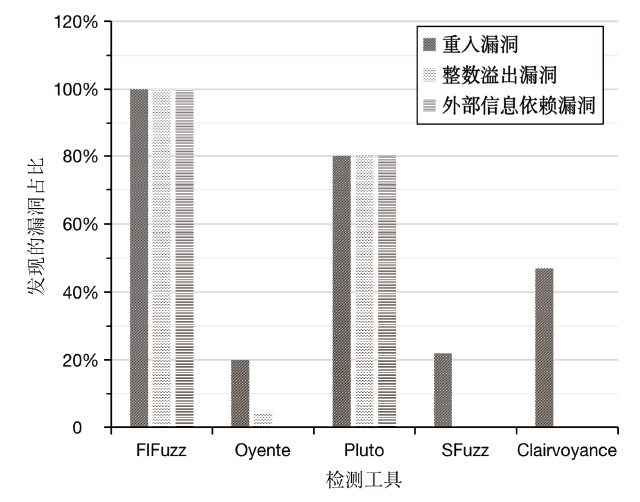
Netinfo Security ›› 2024, Vol. 24 ›› Issue (7): 1038-1049.doi: 10.3969/j.issn.1671-1122.2024.07.006
Previous Articles Next Articles
A Cross-Contract Fuzzing Scheme Based on Function Dependencies
ZHANG Liqiang1,2, LU Mengjun1,2, YAN Fei1,2( )
)
- 1. School of Cyber Science and Engineering, Wuhan University, Wuhan 430072, China
2. Key Laboratory of Aerospace Information Security and Trusted Computing of Ministry of Education, Wuhan University, Wuhan 430072, China
-
Received:2023-03-09Online:2024-07-10Published:2024-08-02
CLC Number:
Cite this article
ZHANG Liqiang, LU Mengjun, YAN Fei. A Cross-Contract Fuzzing Scheme Based on Function Dependencies[J]. Netinfo Security, 2024, 24(7): 1038-1049.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.07.006
| [1] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. (2008-10-31)[2023-03-07]. https://www.researchgate.net/publication/228640975_Bitcoin_A_Peer-to-Peer_Electronic_Cash_System. |
| [2] | UNDERWOOD S. Blockchain beyond Bitcoin[J]. Communications of the ACM, 2016, 59(11): 15-17. |
| [3] | LI Dongcheng, WONG W E, PAN S, et al. Design Principles and Best Practices of Central Bank Digital Currency[J]. International Journal of Performability Engineering, 2021, 17(5): 411-421. |
| [4] |
TIAN Zhihong, LI Mohan, QIU Meikang, et al. Block-DEF: A Secure Digital Evidence Framework Using Blockchain[J]. Information Sciences, 2019, 491: 151-165.
doi: 10.1016/j.ins.2019.04.011 |
| [5] | WOOD G. Ethereum: A Secure Decentralised Generalised Transaction Ledger[J]. Ethereum Project Yellow Paper, 2014, 151: 1-32. |
| [6] | NICK S. The Idea of Smart Contracts[EB/OL]. (1997-10-31)[2023-03-07]. http://www.fon.hum.uva.nl/rob/Courses/InformationInSpeech/CDROM/Literature/LOTwinterschool2006/szabo.best.vwh.net/idea.html. |
| [7] | Bitinfocharts. Ethereum Daily Transaction Chart[EB/OL]. (2023-02-16)[2023-03-07]. https://etherscan.io/chart/tx. |
| [8] | Secbit. A Disastrous Vulnerability Found in Smart Contracts of Beautychain(BEC)[ EB/OL]. (2022-08-11)[2023-03-07]. https://medium.com/secbit-media/a-disastrous-vulnerability-found-in-smart-contracts-of-beautychain-bec-dbf24ddbc30e. |
| [9] | YU Xiaoliang, AL-BATAINEH O, LO D, et al. Smart Contract Repair[J]. ACM Transactions on Software Engineering and Methodology (TOSEM), 2020, 29(4): 1-32. |
| [10] | LEE S. Blockchain Smart Contracts: More Trouble than They are Worth?[EB/OL]. (2018-07-10)[2023-03-07]. https://www.forbes.com/sites/shermanlee/2018/07/10/blockchain-smart-contracts-more-trouble-than-they-are-worth/493735e623a6. |
| [11] | CHANG S. Ethereum Smart Contracts Vulnerable to Hacks: $4 Million in Ether at Risk[EB/OL]. (2019-06-25)[2023-03-07]. https://www.investopedia.com/news/ethereum-smart-contracts-vulnerable-hacks\-4-million-ether-risk/. |
| [12] | LUU L, CHU D H, OLICKEL H, et al. Making Smart Contracts Smarter[C]// ACM. The 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 254-269. |
| [13] | RAZA A. The Binance KYC Data Breach: The Hacker Confirms the Attack[EB/OL]. (2019-03-29)[2023-03-07]. https://cryptopotato.com/the-binance-kyc-data-breach-the-hacker-confirms-the-attack/. |
| [14] | ZHENG G, GAO Longxiang, HUANG Liqun, et al. Upgradable Contract[M]. Heidelberg: Springer, 2021. |
| [15] | LI Wenkai, BU Jiuyang, LI Xiaoqi, et al. A Survey of DeFi Security: Challenges and Opportunities[J]. Journal of King Saud University-Computer and Information Sciences, 2022, 34(10): 10378-10404. |
| [16] | MCKAY J. DeFi-ing Cyber Attacks[EB/OL]. (2022-04-27)[2023-03-07]. https://tellingstorieswithdata.com/inputs/pdfs/final_paper-2022-jack_mckay. pdf. |
| [17] | NIKOLIĆ I, KOLLURI A, SERGEY I, et al. Finding the Greedy, Prodigal, and Suicidal Contracts at Scale[C]// ACM. The 34th Annual Computer Security Applications Conference. New York: ACM, 2018: 653-663. |
| [18] | JIANG Bo, LIU Ye, CHAN W K. ContractFuzzer: Fuzzing Smart Contracts for Vulnerability Detection[C]// IEEE. 2018 33rd IEEE/ACM International Conference on Automated Software Engineering (ASE). New York: IEEE, 2018: 259-269. |
| [19] | NGUYEN T D, PHAM L H, SUN Jun, et al. SFuzz: An Efficient Adaptive Fuzzer for Solidity Smart Contracts[C]// ACM. Proceedings of the ACM/IEEE 42nd International Conference on Software Engineering. New York: ACM, 2020: 778-788. |
| [20] | HE Jingxuan, BALUNOVIĆ M, AMBROLADZE N, et al. Learning to Fuzz from Symbolic Execution with Application to Smart Contracts[C]// ACM. The 2019 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2019: 531-548. |
| [21] | TSANKOV P, DAN A, DRACHSLER-COHEN D, et al. Securify: Practical Security Analysis of Smart Contracts[C]// ACM. The 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 67-82. |
| [22] | GRECH N, KONG M, JURISEVIC A, et al. MadMax: Surviving Out-of-Gas Conditions in Ethereum Smart Contracts[J]. Proceedings of the ACM on Programming Languages, 2018, 116(2): 1-27. |
| [23] | XUE Yinxing, MA Mingliang, LIN Yun, et al. Cross-Contract Static Analysis for Detecting Practical Reentrancy Vulnerabilities in Smart Contracts[C]// ACM. The 35th IEEE/ACM International Conference on Automated Software Engineering. New York: ACM, 2020: 1029-1040. |
| [24] | MA Fuchen, XU Zhenyang, REN Meng, et al. Pluto: Exposing Vulnerabilities in Inter-Contract Scenarios[J]. IEEE Transactions on Software Engineering, 2022, 48(11): 4380-4396. |
| [25] | LIAO Zeqin, ZHENG Zibin, CHEN Xiao, et al. SmartDagger: A Bytecode-Based Static Analysis Approach for Detecting Cross-Contract Vulnerability[C]// ACM. The 31st ACM SIGSOFT International Symposium on Software Testing and Analysis. New York: ACM, 2022: 752-764. |
| [26] | XIONG Wei, XIONG Li. Smart Contract Based Data Trading Mode Using Blockchain and Machine Learning[J]. IEEE Access, 2019, 7: 102331-102344. |
| [27] | XU Guangxia, HU Mengxiao, MA Chuang. Secure and Smart Autonomous Multi-Robot Systems for Opinion Spammer Detection[J]. Information Sciences, 2021, 576: 681-693. |
| [28] | PAGE L, BRIN S, MOTWANI R, et al. The PageRank Citation Ranking: Bringing Order to the Web[EB/OL]. (1999-11-11)[2023-03-07]. https://xueshu.baidu.com/usercenter/paper/show?paperid=189f33f55815fd274b89c7f425e3452e&site=xueshu_se. |
| [29] | FEIST J, GRIECO G, GROCE A. Slither: A Static Analysis Framework for Smart Contracts[C]// IEEE. 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB). New York: IEEE, 2019: 8-15. |
| [30] | MICHAL Z. American Fuzzy Lop (AFL)[EB/OL]. (2018-04-17)[2023-03-07]. http://lcamtuf.coredump.cx/afl/. |
| [31] | STEPHENS N, GROSEN J, SALLS C, et al. Driller: Augmenting Fuzzing through Selective Symbolic Execution[EB/OL]. (2016-02-21)[2023-03-07]. https://www.researchgate.net/publication/316906731_Driller_Augmenting_Fuzzing_Through_Selective_Symbolic_Execution. |
| [32] | GRIECO G, SONG W, CYGAN A, et al. Echidna: Effective, Usable, and Fast Fuzzing for Smart Contracts[C]// ACM. The 29th ACM SIGSOFT International Symposium on Software Testing and Analysis. New York: ACM, 2020: 557-560. |
| [33] | MUELLER B. Mythril-Reversing and Bug Hunting Framework for the Ethereum Blockchain[EB/OL]. (2022-11-03)[2023-03-07]. https://pypi.org/project/mythril/0.8.2/. |
| [34] | TIKHOMIROV S, VOSKRESENSKAYA E, IVANITSKIY I, et al. SmartCheck: Static Analysis of Ethereum Smart Contracts[C]// IEEE. 2018 IEEE/ACM 1st International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB). New York: IEEE, 2018: 9-16. |
| [35] | XU Guangxia, WU Xinkai, LIU Jun, et al. A Community Detection Method Based on Local Optimization in Social Networks[J]. IEEE Network, 2020, 34(4): 42-48. |
| [1] | LIU Feng, JIANG Jiaqi, HUANG Hao. Security Overview of Cryptocurrency Trading Media and Processes [J]. Netinfo Security, 2024, 24(3): 330-351. |
| [2] | QIN Sihang, DAI Weiqi, ZENG Haiyan, GU Xianjun. Secure Sharing of Power Application Data Based on Blockchain [J]. Netinfo Security, 2023, 23(8): 52-65. |
| [3] | LI Chunxiao, WANG Yaofei, XU Enliang, ZHAO Yu. Enabling Privacy-Preserving Range Queries in Blockchain-Based Collaborative Databases with Bilinear Pairings [J]. Netinfo Security, 2023, 23(3): 22-34. |
| [4] | ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism [J]. Netinfo Security, 2022, 22(9): 46-54. |
| [5] | ZHANG Yujian, LIU Daifu, TONG Fei. Reentrancy Vulnerability Detection in Smart Contracts Based on Local Graph Matching [J]. Netinfo Security, 2022, 22(8): 1-7. |
| [6] | HU Yi, SHE Kun. Blockchain and Smart Contract Based Dual-Chain Internet of Vehicles System [J]. Netinfo Security, 2022, 22(8): 26-35. |
| [7] | WANG Jian, HUANG Jun. Smart Contract-Based Log Secure Storage and Fair Access Method [J]. Netinfo Security, 2022, 22(7): 27-36. |
| [8] | YU Kechen, GUO Li, YIN Hongwei, YAN Xuesong. The High-Value Data Sharing Model Based on Blockchain and Game Theory for Data Centers [J]. Netinfo Security, 2022, 22(6): 73-85. |
| [9] | HUA Jingyu, HUANG Daming. Survey of Formal Specification Methods in Theorem Proving of Ethereum Smart Contract [J]. Netinfo Security, 2022, 22(5): 11-20. |
| [10] | FENG Jingyu, ZHANG Qi, HUANG Wenhua, HAN Gang. A Cyber Threat Intelligence Sharing Scheme Based on Cross-Chain Interaction [J]. Netinfo Security, 2022, 22(5): 21-29. |
| [11] | LI Peng, ZHENG Tiantian, XU He, ZHU Feng. RFID Security Authentication Protocol Based on Blockchain Technology [J]. Netinfo Security, 2021, 21(5): 1-11. |
| [12] | WANG Jian, YU Hang, HAN Zhen, HAN Lei. Access Control Methods of Data Sharing in Cloud Storage Based on Smart Contract [J]. Netinfo Security, 2021, 21(11): 40-47. |
| [13] | YU Kechen, GUO Li, YAO Mengmeng. Design of Blockchain-based High-value Data Sharing System [J]. Netinfo Security, 2021, 21(11): 75-84. |
| [14] | WU Jiaming, XIONG Yan, HUANG Wenchao, WU Jianshuang. A Distance-based Fuzzing Mutation Method [J]. Netinfo Security, 2021, 21(10): 63-68. |
| [15] | JIANG Nan, WANG Weiqi, WANG Jian. Research on Personal Information Protection Method Based on Smart Contract [J]. Netinfo Security, 2020, 20(11): 22-31. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||