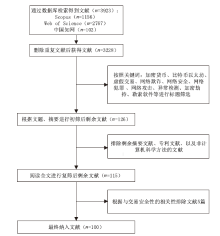
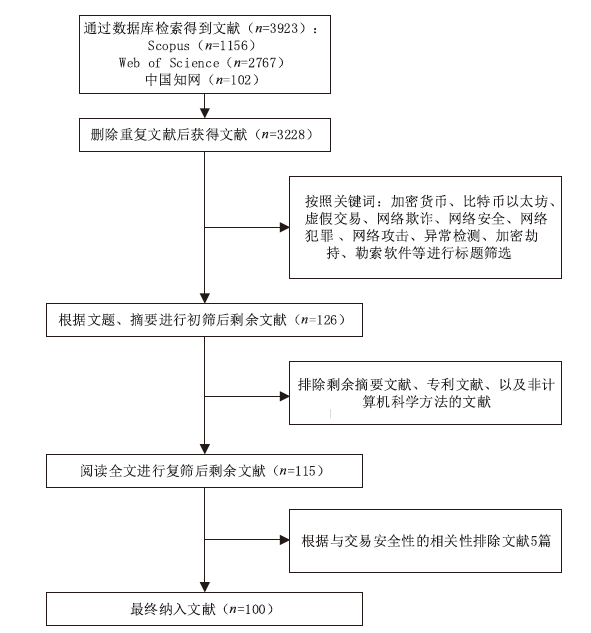
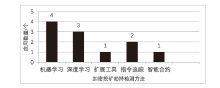
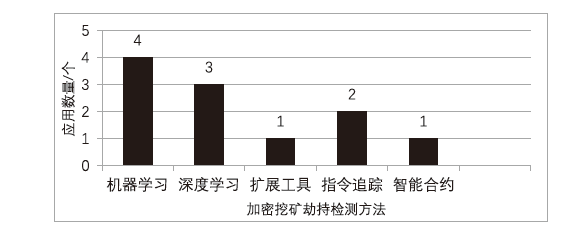
Netinfo Security ›› 2024, Vol. 24 ›› Issue (3): 330-351.doi: 10.3969/j.issn.1671-1122.2024.03.001
Previous Articles Next Articles
Security Overview of Cryptocurrency Trading Media and Processes
LIU Feng( ), JIANG Jiaqi, HUANG Hao
), JIANG Jiaqi, HUANG Hao
- School of Computer Science and Technology, East China Normal University, Shanghai 200062, China
-
Received:2023-12-01Online:2024-03-10Published:2024-04-03 -
Contact:LIU Feng E-mail:lsttoy@163.com
CLC Number:
Cite this article
LIU Feng, JIANG Jiaqi, HUANG Hao. Security Overview of Cryptocurrency Trading Media and Processes[J]. Netinfo Security, 2024, 24(3): 330-351.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.03.001
| 方案 | 安全漏洞/ 攻击 | 保密性 | 完整性 | 可用性 | 防御措施 | 年份 |
|---|---|---|---|---|---|---|
| 文献[ | 密码漏洞、恢复钱包漏洞 | √ | — | — | 安全地备份加密钱包并定期更换密钥 | 2019 |
| 文献[ | 穷举搜索的暴力破解攻击 | √ | √ | — | 修改比特币协议、构建特殊的智能合约对哈希函数漏洞进行报警 | 2019 |
| 文献[ | 移动钱包的源代码漏洞 | √ | — | — | 关注网络层面的隐私 | 2019 |
| 文献[ | 存储过程中的密钥可以明文访问或解密的漏洞 | √ | — | — | — | 2020 |
| 存储过程中的第三方可修改漏洞 | — | √ | √ | — | ||
| 监视导入过程中的复制粘贴的漏洞 | √ | — | — | — | ||
| 监听密码验证过程中的密码输入 | √ | — | — | — | ||
| 篡改钱包显示的交易信息 | — | √ | — | — | ||
| 切断钱包与区块链网络或钱包服务器的 连接 | — | — | √ | — | ||
| 文献[ | USB调试漏洞 | √ | — | — | 对复制和粘贴敏感数据等危险操作进行警告,加密钱包应该使用二维码、NFC等方式进行输入 | 2020 |
| 截图功能中的漏洞 | √ | — | — | |||
| 识别并替换 敏感信息 | √ | √ | — | |||
| 可访问性服务漏洞 | √ | — | — | |||
| 文献[ | 确定性钱包、隐身地址算法中的漏洞 | √ | — | — | 具有公开派生公钥的密钥绝缘和隐私保护签名方案 | 2022 |
| 方案 | 漏洞 类型 | 检测 技术 | FPR | FNR | 准确率 | 召回率 | 精确率 | F1值 | AUC | 年份 |
|---|---|---|---|---|---|---|---|---|---|---|
| 文献[ | 未检查的低级别调用 | SmartCheck | — | — | 0.976 | 1.00 | 0.788 | 0.881 | 0.987 | 2021 |
| 时间戳依赖 | Slither | — | — | 0.968 | 1.00 | 0.208 | 0.345 | 0.984 | ||
| 溢出 漏洞 | VeriSmart | — | — | 0.908 | 1.00 | 0.50 | 0.667 | 0.949 | ||
| 时间戳依赖 | Solhint | — | — | 0.938 | 1.00 | 0.119 | 0.213 | 0.969 | ||
| 文献[ | 拒绝 服务 | DT | — | — | 0.9118 | 0.985 | 0.506 | 0.669 | 0.945 | 2021 |
| 文献[ | 可重入 | Oyente | — | — | 0.987 | 0.935 | 0.829 | 0.879 | 0.962 | 2021 |
| 文献[ | 拒绝 服务 | RF | — | — | 0.9595 | 0.814 | 0.757 | 0.785 | 0.894 | 2021 |
| 文献[ | 领先 漏洞 | Oyente | — | — | 0.948 | 0.50 | 0.065 | 0.114 | 0.725 | 2021 |
| 时间戳依赖 漏洞 | Manticore | — | — | 0.993 | 0.40 | 0.667 | 0.50 | 0.699 | ||
| Securify | — | — | 0.993 | 0.20 | 1.00 | 0.333 | 0.6 | |||
| 拒绝 服务 | Mythril | — | — | 0.987 | 0.167 | 0.25 | 0.20 | 0.581 | ||
| 访问 控制 | 0.97 | 0.167 | 0.50 | 0.25 | 0.576 | |||||
| 文献[ | 文献中的21种安全 漏洞 | NeuCheck | 0.157 | 0.165 | — | — | — | — | — | 2021 |
| Securify | 0.167 | 0.728 | — | — | — | — | — | |||
| Mythril | 0.6000 | 0.8348 | — | — | — | — | — | |||
| 文献[ | 可重入 | RA | 0 | 0 | — | — | — | — | — | 2020 |
| 方案 | 技术 | 分类 | Acc | 精确率 | 召回率 | F1值 | 年份 |
|---|---|---|---|---|---|---|---|
| 文献[ | GB | 交易所 | — | 1.00 | 1.00 | 1.00 | 2019 |
| 混合器 | 1.00 | 1.00 | 1.00 | ||||
| 市场 | 1.00 | 1.00 | 1.00 | ||||
| 矿池 | 1.00 | 1.00 | 1.00 | ||||
| 赌博 | 0.99 | 1.00 | 0.99 | ||||
| 服务 | 1.00 | 0.93 | 0.96 | ||||
| RF | 混合器 | — | 1.00 | 1.00 | 1.00 | ||
| 赌博 | 1.00 | 1.00 | 1.00 | ||||
| 交易所 | 0.96 | 1.00 | 0.98 | ||||
| 服务 | 1.00 | 0.93 | 0.96 | ||||
| 矿池 | 1.00 | 0.92 | 0.96 | ||||
| 市场 | 1.00 | 0.85 | 0.91 | ||||
| 文献[ | GBC | 预测没有分类实体 | 0.8042 | - | 0.8083 | 0.7964 | 2019 |
| 方案 | 技术 | 分类 | Acc | 精确率 | 召回率 | F1值 | AUC | FPR | 年份 |
|---|---|---|---|---|---|---|---|---|---|
| 文献[ | RF | 良性或恶意软件 | 0.9833 | 0.9677 | 1.0000 | 0.9836 | — | — | 2023 |
| 文献[ | SAE+ DDNN | 正常或加密劫持 网站 | — | 0.9941 | 0.9910 | 0.9925 | — | — | 2022 |
| 文献[ | RNN | 良性或加密劫持 网站 | 0.9804 | — | 0.9688 | 0.9792 | — | — | 2022 |
| 文献[ | DT | 50个加密劫持恶意软件样本中,成功检测到41例 | 2020 | ||||||
| 文献[ | RF | 挖掘时:正常或 挖掘应用 | 0.9935 | 1.00 | 0.98 | — | 0.99 | — | 2019 |
| 非挖掘时:正常或 挖掘应用 | 0.99 | 1.00 | — | — | |||||
| 文献[ | SVM | BD:正常或加密 劫持 | — | — | 0.962 | — | 0.978 | 0.002 | 2019 |
| ID:正常或加密 劫持 | — | — | 0.979 | — | 0.984 | 0.011 | |||
| 文献[ | CapsNet | 正常或加密劫持 | 0.9895 | — | — | — | — | 0.0103 | 2019 |
| 方案 | 技术 | 分类 | 准确率 | 精确率 | 召回率 | F1值 | AUC | 年份 |
|---|---|---|---|---|---|---|---|---|
| 文献[ | LBPS | 正常或钓鱼 账户 | 0.9730 | 0.9813 | 0.9759 | 0.9786 | — | 2023 |
| 文献[ | LR | 正常或钓鱼 账户 | — | 0.9475 | 0.9483 | 0.9476 | — | 2023 |
| 文献[ | One-class SVM | 正常或钓鱼 节点 | — | 0.927 | 0.893 | 0.908 | — | 2022 |
| 文献[ | PDTGA | 正常或钓鱼 节点 | — | 0.8015 | 0.8876 | 0.8423 | 0.9478 | 2023 |
| 文献[ | DElightGBM | 正常或钓鱼 地址 | — | 0.8258 | 0.8390 | 0.8324 | 0.8282 | 2020 |
| 文献[ | LR | 正常或钓鱼 账户 | 0.7486 | 0.6969 | 0.8957 | 0.7803 | — | 2023 |
| 文献[ | SGCN | 正常或钓鱼 节点 | — | 0.6526 | 0.5359 | 0.5885 | 0.7683 | 2022 |
| 文献[ | GCN | 正常或钓鱼 账户 | — | 0.7294 | 0.1453 | 0.2357 | 0.5725 | 2021 |
| 文献[ | SVC | 正常或BGS 网页 | — | — | — | 0.9892 | — | 2020 |
| MLP | 正常或BGS 网页 | — | — | — | 0.9892 | — | ||
| 文献[ | RF | 正常或庞氏 智能合约 | — | 0.8368 | 0.7536 | 0.7909 | — | 2021 |
| 方案 | 技术 | 异常 | 准确率 | 精确率 | 召回率 | F1值 | Micro- F1 | Macro- F1 | FPR | 年份 |
|---|---|---|---|---|---|---|---|---|---|---|
| 文献[ | KNN | 欺诈或非欺诈交易 | — | 0.986 | 0.988 | 0.987 | — | — | — | 2021 |
| RF | — | 0.982 | 0.982 | 0.974 | — | — | — | |||
| J48 | — | 0.984 | 0.986 | 0.984 | — | — | — | |||
| 文献[ | XGBoost | 智能合约账户 | 0.9682 | — | — | — | — | — | 0.0078 | 2020 |
| 外部拥有账户 | 0.9654 | — | — | — | — | — | 0.0092 | |||
| 文献[ | GCN | 用户类型分类 | 0.92 | — | — | — | — | — | — | 2023 |
| 合法或非法 用户 | 0.85 | — | — | — | — | — | — | |||
| 文献[ | 子图 匹配 | 贪婪注资异常交易 | 0.5432 | — | 0.8125 | — | — | — | — | 2021 |
| 空投糖果异常交易 | 0.4362 | — | 0.8571 | — | — | — | — | |||
| 文献[ | LightGBM | 异常 地址 | — | — | — | — | 0.87 | 0.86 | — | 2019 |
| [1] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. (2008-10-31)[2023-09-10]. https://grothoff.org/christian/teaching/2014/2194/bitcoin.pdf. |
| [2] |
LI Yannan, SUSILO W, YANG Guomin, et al. Toward Privacy and Regulation in Blockchain-Based Cryptocurrencies[J]. IEEE Network, 2019, 33(5): 111-117.
doi: 10.1109/MNET.2019.1800271 |
| [3] |
SHIH D, WU Tingwei, HSU T H, et al. Verification of Cryptocurrency Mining Using Ethereum[J]. IEEE Access, 2020, 8: 120351-120360.
doi: 10.1109/Access.6287639 URL |
| [4] | HE Daojing, LI Shihao, LI Cong, et al. Security Analysis of Cryptocurrency Wallets in Android-Based Applications[J]. IEEE Network, 2020, 34(6): 114-119. |
| [5] | LI Cong, HE Daojing, LI Shihao, et al. Android-Based Cryptocurrency Wallets: Attacks and Countermeasures[C]// IEEE. 3rd IEEE International Conference on Blockchain. New York: IEEE, 2020: 9-16. |
| [6] |
VOLETY T, SAINI S, MCGHIN T, et al. Cracking Bitcoin Wallets: I Want What You Have in the Wallets[J]. Future Generation Computer Systems, 2019, 91(2): 136-143.
doi: 10.1016/j.future.2018.08.029 URL |
| [7] | KIKTENKO E O, KUDINOV M A, FEDOROV A K. Detecting Brute-Force Attacks on Cryptocurrency Wallets[C]// University of Seville. 22nd International Conference on Business Information Systems. Heidelberg: Springer, 2019: 232-242. |
| [8] | BIRYUKOV A, TIKHOMIROV S. Security and Privacy of Mobile Wallet Users in Bitcoin, Dash, Monero, and Zcash[J]. Pervasive and Mobile Computing, 2019(10): 59-71. |
| [9] |
LIU Zhen, YANG Guomin, WONG D S, et al. Secure Deterministic Wallet and Stealth Address: Key-Insulated and Privacy-Preserving Signature Scheme with Publicly Derived Public Key[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 19(5): 2934-2951.
doi: 10.1109/TDSC.2021.3078463 URL |
| [10] | BACK H, OH J, KIM C, et al. A Model for Detecting Cryptocurrency Transactions with Discernible Purpose[C]// IEEE. 11th International Conference on Ubiquitous and Future Networks. New York: IEEE, 2019: 713-717. |
| [11] |
HE Xiaojian, LIN Jinfu, LI Kangzi, et al. A Novel Cryptocurrency Wallet Management Scheme Based on Decentralized Multi-Constrained Derangement[J]. IEEE Access, 2019, 7: 185250-185263.
doi: 10.1109/ACCESS.2019.2961183 |
| [12] | SHBAIR W M, GAVRILOV E, STATE R. HSM-Based Key Management Solution for Ethereum Blockchain[C]// IEEE. 3rd IEEE International Conference on Blockchain and Cryptocurrency. New York: IEEE, 2021: 1-3. |
| [13] | PRAITHEESHAN P, PAN L, DOSS R. Security Evaluation of Smart Contract-Based On-Chain Ethereum Wallets[C]// University of Seville. 14th International Conference on Network and System Security. Heidelberg: Springer, 2020: 22-41. |
| [14] |
CHEN Jialan, LIN Dan, WU Jiajing. Do Cryptocurrency Exchanges Fake Trading Volumes? An Empirical Analysis of Wash Trading Based on Data Mining[J]. Physica A-Statistical Mechanics and Its Applications, 2022, 586: 126405-126418.
doi: 10.1016/j.physa.2021.126405 URL |
| [15] | VICTOR F, WEINTRAUD A M. Detecting and Quantifying Wash Trading on Decentralized Cryptocurrency Exchanges[C]// ACM. 30th World Wide Web Conference. New York: ACM, 2021: 23-32. |
| [16] | OOSTHOEK K, DOERR C. From Hodl to Heist: Analysis of Cyber Security Threats to Bitcoin Exchanges[C]// IEEE. IEEE International Conference on Blockchain and Cryptocurrency. New York: IEEE, 2020: 1-9. |
| [17] |
OOSTHOEK K, DOERR C. Cyber Security Threats to Bitcoin Exchanges: Adversary Exploitation and Laundering Techniques[J]. IEEE Transactions on Network and Service Management, 2021, 18(2): 1616-1628.
doi: 10.1109/TNSM.2020.3046145 URL |
| [18] | BENTOV I, JI Yan, ZHANG Fan, et al. Tesseract: Real-Time Cryptocurrency Exchange Using Trusted Hardware[C]// ACM. ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2019: 1521-1538. |
| [19] | BUTERIN V. Ethereum: A Next-Generation Smart Contract and Decentralized Application Platform[EB/OL]. (2014-01-21)[2023-10-10]. https://github.com/ethereum/wiki/wiki/White-Paper. |
| [20] | LU Ning, WANG Bin, ZHANG Yongxin, et al. NeuCheck: A More Practical Ethereum Smart Contract Security Analysis Tool[J]. Software-Practice & Experience, 2021, 51(10): 2065-2084. |
| [21] | XIA Pengcheng, WANG Haoyu, GAO Bingyu, et al. Trade or Trick? Detecting and Characterizing Scam Tokens on Uniswap Decentralized Exchange[C]// ACM. ACM SIGMETRICS/Performance Conference. New York: ACM, 2022: 23-49. |
| [22] |
JI S, KIM D, IM H. Evaluating Countermeasures for Verifying the Integrity of Ethereum Smart Contract Applications[J]. IEEE Access, 2021, 9: 90029-90042.
doi: 10.1109/ACCESS.2021.3091317 URL |
| [23] | SOUSA JOSE E A, OLIVEIRA V C, ALMEIDA VALADARES J, et al. Fighting Under-Price DoS Attack in Ethereum with Machine Learning Techniques[J]. ACM SIGMETRICS Performance Evaluation Review, 2021, 48(4): 24-37. |
| [24] | CHINEN Y, YANAI N, CRUZ J P, et al. RA: Hunting for Re-Entrancy Attacks in Ethereum Smart Contracts via Static Analysis[C]// IEEE. 3rd IEEE International Conference on Blockchain. New York: IEEE, 2020: 327-336. |
| [25] | LEE S, CHO E S. Lightweight Extension of an Execution Environment for Safer Function Calls in Solidity/Ethereum Virtual Machine Smart Contracts[C]// IEEE. 28th IEEE International Conference on Software Analysis, Evolution and Reengineering. New York: IEEE, 2021: 689-695. |
| [26] | GAO Jianbo, LIU Han, LIU Chao, et al. EASYFLOW: Keep Ethereum Away from Overflow[C]// IEEE. IEEE/ACM 41st International Conference on Software Engineering-Software Engineering in Practice. New York: IEEE, 2019: 23-26. |
| [27] | AQUILINA S J, CASINO F, VELLA M, et al. EtherClue: Digital Investigation of Attacks on Ethereum Smart Contracts[J]. Blockchain-Research and Applications, 2021, 2(4): 1016-1029. |
| [28] | MAVRIDOU A, LASZKA A, STACHTIARI E, et al. VeriSolid: Correct-by-Design Smart Contracts for Ethereum[C]// University of Seville. 23rd International Conference on Financial Cryptography and Data Security. Heidelberg: Springer, 2019: 446-465. |
| [29] | IVANOV N, LOU J, CHEN Ting, et al. Targeting the Weakest Link: Social Engineering Attacks in Ethereum Smart Contracts[C]// ACM. 16th ACM ASIA Conference on Computer and Communications Security. New York: ACM, 2021: 787-801. |
| [30] | CAMINO R D, TORRES C F, BADEN M, et al. A Data Science Approach for Detecting Honeypots in Ethereum[C]// IEEE. 2020 IEEE International Conference on Blockchain and Cryptocurrency. New York: IEEE, 2020: 1-9. |
| [31] | HARA K, TAKAHASHI T, ISHIMAKI M, et al. Machine-Learning Approach Using Solidity Bytecode for Smart-Contract Honeypot Detection in the Ethereum[C]// IEEE. 21st IEEE International Conference on Software Quality, Reliability and Security. New York: IEEE, 2021: 652-659. |
| [32] | HARA K, SATO T, IMAMURA M, et al. Profiling of Malicious Users Using Simple Honeypots on the Ethereum Blockchain Network[C]// IEEE. 2020 IEEE International Conference on Blockchain and Cryptocurrency. New York: IEEE, 2020: 1-3. |
| [33] | CHENG Zhen, HOU Xinrui, LI Runhuai, et al. Towards a First Step to Understand the Cryptocurrency Stealing Attack on Ethereum[C]// USENIX. 22nd International Symposium on Research in Attacks, Intrusions and Defenses. Berkeley: USENIX, 2019: 47-60. |
| [34] |
ZHANG Lingyue, LI Huilin, LI Yannan, et al. An Efficient Linkable Group Signature for Payer Tracing in Anonymous Cryptocurrencies[J]. Future Generation Computer Systems, 2019, 101: 29-38.
doi: 10.1016/j.future.2019.05.081 |
| [35] |
LIN Chao, HE Debiao, HUANG Xinyi, et al. DCAP: A Secure and Efficient Decentralized Conditional Anonymous Payment System Based on Blockchain[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 2440-2452.
doi: 10.1109/TIFS.10206 URL |
| [36] |
YIN HAO, LANGENHELDT K C, HARLEV M A, et al. Regulating Cryptocurrencies: A Supervised Machine Learning Approach to De-Anonymizing the Bitcoin Blockchain[J]. Journal of Management Information Systems, 2019, 36(1): 37-73.
doi: 10.1080/07421222.2018.1550550 URL |
| [37] | OLA F, EGUIMENDIA M, BRUSE J L, et al. Cascading Machine Learning to Attack Bitcoin Anonymity[C]// IEEE. 2nd IEEE International Conference on Blockchain. New York: IEEE, 2019: 10-17. |
| [38] |
ZHANG Yuhang, WANG Jun, LUO Jie. Heuristic-Based Address Clustering in Bitcoin[J]. IEEE Access, 2020, 8: 210582-210591.
doi: 10.1109/Access.6287639 URL |
| [39] | BIRYUKOV A, TIKHOMIROV S. Deanonymization and Linkability of Cryptocurrency Transactions Based on Network Analysis[C]// IEEE. 4th IEEE European Symposium on Security and Privacy. New York: IEEE, 2019: 172-184. |
| [40] | BIRYUKOV A, TIKHOMIROV S. Transaction Clustering Using Network Traffic Analysis for Bitcoin and Derived Blockchains[C]// IEEE. IEEE Conference on Computer Communications. New York: IEEE, 2019: 204-209. |
| [41] | ZHANG Zongyang, YIN Jiayuan, LIU Yizhong, et al. Deanonymization of Litecoin through Transaction-Linkage Attacks[C]// IEEE. 11th International Conference on Information and Communication Systems. New York: IEEE, 2020: 59-65. |
| [42] | KARA I, AYDOS M. Cyber Fraud: Detection and Analysis of the Crypto-Ransomware[C]// IEEE. 11th IEEE Annual Ubiquitous Computing, Electronics and Mobile Communication Conference. New York: IEEE, 2020: 764-769. |
| [43] |
ZHENG Rui, WANG Qiuyun, LIN Zhuopang, et al. Cryptocurrency Malware Detection in Real-World Environment: Based on Multi-Results Stacking Learning[J]. Applied Soft Computing, 2022, 124: 109044-109058.
doi: 10.1016/j.asoc.2022.109044 URL |
| [44] | KHARRAZ A, MA Z, MURLEY P, et al. OUTGUARD: Detecting In-Browser Covert Cryptocurrency Mining in the Wild[C]// ACM. World Wide Web Conference. New York: ACM, 2019: 840-852. |
| [45] | NING Rui, WANG Cong, XIN Chunsheng, et al. CapJack: Capture In-Browser Crypto-Jacking by Deep Capsule Network through Behavioral Analysis[C]// IEEE. IEEE Conference on Computer Communications. New York: IEEE, 2019: 1873-1881. |
| [46] | TAHIR R, DURRANI S, AHMED F, et al. The Browsers Strike Back: Countering Cryptojacking and Parasitic Miners on the Web[C]// IEEE. IEEE Conference on Computer Communications. New York: IEEE, 2019: 703-711. |
| [47] | RAZALI M A, MOHD S S. CMBlock: In-Browser Detection and Prevention Cryptojacking Tool Using Blacklist and Behavior-Based Detection Method[C]// University of Seville. 6th International Visual Informatics Conference. Heidelberg: Springer, 2019: 404-414. |
| [48] | TANANA D. Behavior-Based Detection of Cryptojacking Malware[C]// IEEE. 2020 Ural Symposium on Biomedical Engineering, Radioelectronics and Information Technology. New York: IEEE, 2020: 543-556. |
| [49] |
LACHTAR N, ELKHAIL A A, BACHA A, et al. A Cross-Stack Approach Towards Defending against Cryptojacking[J]. IEEE Computer Architecture Letters, 2020, 19(2): 126-129.
doi: 10.1109/CA-L.10208 URL |
| [50] | LACHTAR N, ELKHAIL A A, BACHA A, et al. An Application Agnostic Defense against the Dark Arts of Cryptojacking[C]// IEEE. 51st Annual IEEE/IFIP International Conference on Dependable Systems and Networks. New York: IEEE, 2021: 314-325. |
| [51] | HERNANDEZ-SUAREZ A, SANCHEZ-PEREZ G, TOSCANO-MEDINA L K, et al. Detecting Cryptojacking Web Threats: An Approach with Autoencoders and Deep Dense Neural Networks[J]. Applied Sciences-Basel, 2022, 12(7): 3234-3245. |
| [52] |
YING Qianjin, YU Yulei, TIAN Donghai, et al. CJSpector: A Novel Cryptojacking Detection Method Using Hardware Trace and Deep Learning[J]. Journal of Grid Computing, 2022, 20(3): 31-48.
doi: 10.1007/s10723-022-09621-2 |
| [53] | CAO Chuanbo, GUO Chun, SHEN Guowei, et al. Cryptomining Malware Early Detection Method in Behavioral Diversity Period[J]. ACTC Electronica Sinica, 2023, 51(7): 1850-1858. |
|
曹传博, 郭春, 申国伟, 等. 面向行为多样期的挖矿恶意软件早期检测方法[J]. 电子学报, 2023, 51(7): 1850-1858.
doi: 10.12263/DZXB.20220926 |
|
| [54] |
ZIMBA A, WANG Zhaoshun, MULENGA M. Cryptojacking Injection: A Paradigm Shift to Cryptocurrency-Based Web-Centric Internet Attacks[J]. Journal of Organizational Computing and Electronic Commerce, 2019, 29(1): 40-59.
doi: 10.1080/10919392.2019.1552747 URL |
| [55] | DI T G, NGO C N. Are You a Favorite Target For Cryptojacking? A Case-Control Study on The Cryptojacking Ecosystem[C]// IEEE. 5th IEEE European Symposium on Security and Privacy. New York: IEEE, 2020: 515-520. |
| [56] | CHEN Weili, XU Yuejin, ZHENG Zibin, et al. Detecting Pump & Dump Schemes on Cryptocurrency Market Using an Improved Apriori Algorithm[C]// IEEE. 13th IEEE International Conference on Service-Oriented System Engineering (SOSE)/ 10th International Workshop on Joint Cloud Computing (JCC)/ IEEE International Workshop on Cloud Computing in Robotic Systems. New York: IEEE, 2019: 293-298. |
| [57] |
MIRTAHERI M, ABU-EL-HAIJA S, MORSTATTER F, et al. Identifying and Analyzing Cryptocurrency Manipulations in Social Media[J]. IEEE Transactions on Computational Social Systems, 2021, 8(3): 607-617.
doi: 10.1109/TCSS.2021.3059286 URL |
| [58] | XU Jiahua, LIVSHITS Benjamin. The Anatomy of a Cryptocurrency Pump-and-Dump Scheme[C]// USENIX. 28th USENIX Security Symposium. Berkeley: USENIX, 2019: 1609-1622. |
| [59] |
NIZZOLI L, TARDELLI S, AVVENUTI M, et al. Charting the Landscape of Online Cryptocurrency Manipulation[J]. IEEE Access, 2020, 8: 113230-113245.
doi: 10.1109/Access.6287639 URL |
| [60] |
HAMRICK J T, ROUHI F, MUKHERJEE A K, et al. An Examination of the Cryptocurrency Pump-and-Dump Ecosystem[J]. Information Processing & Management, 2021, 58(4): 102506-102518.
doi: 10.1016/j.ipm.2021.102506 URL |
| [61] | PHILLIPS ROSS C, GORSE D. Predicting Cryptocurrency Price Bubbles Using Social Media Data and Epidemic Modelling[C]// IEEE. IEEE Symposium Series on Computational Intelligence. New York: IEEE, 2017: 394-400. |
| [62] |
SHU Min, ZHU Wei. Real-Time Prediction of Bitcoin Bubble Crashes[J]. Physica A-Statistical Mechanics and Its Applications, 2020, 548: 124477-124489.
doi: 10.1016/j.physa.2020.124477 URL |
| [63] |
WEN Tingke, XIAO Yuanxing, WANG Anqi, et al. A Novel Hybrid Feature Fusion Model for Detecting Phishing Scam on Ethereum Using Deep Neural Network[J]. Expert Systems with Applications, 2023, 211: 118463-118473.
doi: 10.1016/j.eswa.2022.118463 URL |
| [64] | LI Jinghao, LI Hexiao, CHENG Na, et al. Multi-Channel Walk Embedding Based Ethereum Phishing Scam Detection Method[C]// IEEE. IEEE 28th International Conference on Parallel and Distributed Systems. New York: IEEE, 2023: 289-295. |
| [65] |
WU Jiajing, YUAN Qi, LIN Dan, et al. Who Are the Phishers? Phishing Scam Detection on Ethereum via Network Embedding[J]. IEEE Transactions on Systems Man Cybernetics-Systems, 2022, 52(2): 1156-1166.
doi: 10.1109/TSMC.2020.3016821 URL |
| [66] |
WANG Lei, XU Ming, CHENG Hao. Phishing Scams Detection via Temporal Graph Attention Network in Ethereum[J]. Information Processing & Management, 2023, 60(4): 103412-103421.
doi: 10.1016/j.ipm.2023.103412 URL |
| [67] | CHEN Weili, GUO Xiongfeng, CHEN Zhiguang, et al. Phishing Scam Detection on Ethereum: Towards Financial Security for Blockchain Ecosystem[J]. IJCAI International Joint Conference on Artificial Intelligence, 2020: 4506-4512. |
| [68] |
WAN Yun, XIAO Feng. Early-Stage Phishing Detection on the Ethereum Transaction Network[J]. Soft Computing, 2022, 27(7): 3707-3719.
doi: 10.1007/s00500-022-07661-0 |
| [69] | TANG Junjing, ZHAO Gansen, ZOU Bangqi. Semi-Supervised Graph Convolutional Network for Ethereum Phishing Scam Recognition[C]// Xiamen University. 3rd International Conference on Electronics and Communication; Network and Computer Technology (ECNCT). Bellingham: SPIE-INT SOC Optical Engineering, 2021: 12167-12181. |
| [70] | CHEN Liang, PENG Jiaying, LIU Yang, et al. Phishing Scams Detection in Ethereum Transaction Network[J]. ACM Transactions on Internet Technology, 2021, 21(1): 1-16. |
| [71] | BADAWI E, JOURDAN G, BOCHMANN G, et al. An Automatic Detection and Analysis of the Bitcoin Generator Scam[C]// IEEE. 5th IEEE European Symposium on Security and Privacy. New York: IEEE, 2020: 407-416. |
| [72] | YU Shanqing, JIN Jie, XIE Yunyi, et al. Ponzi Scheme Detection in Ethereum Transaction Network[J]. Communications in Computer and Information Science, 2021: 175-186. |
| [73] |
SAYEED S, MARCO-GISBERT H. Assessing Blockchain Consensus and Security Mechanisms against the 51% Attack[J]. Applied Sciences, 2019, 9(9): 1788-1798.
doi: 10.3390/app9091788 URL |
| [74] | GUPTA K D, RAHMAN A, POUDYAL S, et al. A Hybrid POW-POS Implementation against 51 Percent Attack in Cryptocurrency System[C]// IEEE. 2019 IEEE International Conference on Cloud Computing Technology and Science. New York: IEEE, 2019: 396-403. |
| [75] | SUHYEON L, SEUNGJOO K. Proof-of-Stake at Stake:Predatory, Destructive Attack on PoS Cryptocurrencies[C]// ACM. 3rd Workshop on Cryptocurrencies and Blockchains for Distributed Systems. New York: ACM, 2020: 7-11. |
| [76] |
WANG Qiuhua, XIA Tianyu, WANG Dong, et al. Sdos: Selfish Mining-Based Denial-of-Service Attack[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 3335-3349.
doi: 10.1109/TIFS.2022.3202696 URL |
| [77] | ROSENFELD M. Analysis of Bitcoin Pooled Mining Reward Systems[EB/OL]. (2011-12-22)[2023-09-03]. https://arxiv.org/pdf/1112.4980.pdf. |
| [78] | SHI Hongwei, WANG Shengling, HU Qin, et al. Fee-Free Pooled Mining for Countering Pool-Hopping Attack in Blockchain[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 18(4): 1580-1590. |
| [79] | TRAN M, CHOI I, MOON G J, et al. A Stealthier Partitioning Attack against Bitcoin Peer-to-Peer Network[C]// IEEE. 41st IEEE Symposium on Security and Privacy. New York: IEEE, 2020: 894-909. |
| [80] | FAN Wenjun, CHANG S Y, ZHOU Xiaobo, et al. ConMan: A Connection Manipulation-Based Attack against Bitcoin Networking[C]// IEEE. IEEE Conference on Communications and Network Security. New York: IEEE, 2021: 101-109. |
| [81] | PERAZZO P, ARENA A, DINI G. An Analysis of Routing Attacks against IOTA Cryptocurrency[C]// IEEE. 3rd IEEE International Conference on Blockchain. New York: IEEE, 2020: 517-524. |
| [82] | MATZUTT R, HILLER J, HENZE M, et al. A Quantitative Analysis of the Impact of Arbitrary Blockchain Content on Bitcoin[C]// Springer. 22nd International Conference on Financial Cryptography and Data Security. Heidelberg: Springer, 2018: 420-438. |
| [83] | SATO T, IMAMURA M, OMOTE K. Threat Analysis of Poisoning Attack against Ethereum Blockchain[C]// Springer. Information Security Theory and Practice International Conference. Heidelberg: Springer, 2019: 139-154. |
| [84] | RAJPUT U, ABBAS F, HUSSAIN R, et al. A Simple Yet Efficient Approach to Combat Transaction Malleability in Bitcoin[C]// Springer. 15th International Workshop on Information Security Applications. Heidelberg: Springer, 2014: 27-37. |
| [85] |
PÉREZ-SOLÀ C, DELGADO-SEGURA S, NAVARRO-ARRIBAS G, et al. Double-Spending Prevention for Bitcoin Zero-Confirmation Transactions[J]. International Journal of Information Security, 2019, 18(4): 451-463.
doi: 10.1007/s10207-018-0422-4 |
| [86] |
GOLDSMTH D, GRAUER K, SHMALO Y. Analyzing Hack Subnetworks in the Bitcoin Transaction Graph[J]. Applied Network Science, 2020, 5: 22-35.
doi: 10.1007/s41109-020-00261-7 |
| [87] |
SILVEIRA A, BETARTE G, CRISTIA M, et al. A Formal Analysis of the Mimblewimble Cryptocurrency Protocol[J]. Sensors, 2021, 21(17): 5951-5963.
doi: 10.3390/s21175951 URL |
| [88] |
YANG Xiao, LAU W, YE Qingqing, et al. Practical Escrow Protocol for Bitcoin[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 3023-3034.
doi: 10.1109/TIFS.10206 URL |
| [89] | NAUMENKO G, MAXWELL G, WUILLE P, et al. Erlay: Efficient Transaction Relay for Bitcoin[C]// ACM. ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2019: 817-831. |
| [90] | FENG Qi, HE Debiao, LUO Min, et al. Practical Secure Two-Party EdDSA Signature Generation with Key Protection and Applications in Cryptocurrency[C]// IEEE.19th IEEE International Conference on Trust, Security and Privacy in Computing and Communications. New York: IEEE, 2020-2021: 137-147. |
| [91] |
FENG Xiaoqin, MA Jianfeng, WANG Huaxiong, et al. An Accessional Signature Scheme With Unmalleable Transaction Implementation to Securely Redeem Cryptocurrencies[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 4144-4156.
doi: 10.1109/TIFS.2023.3293402 URL |
| [92] | LIN Yujing, WU Powei, HSU Chenghan, et al. An Evaluation of Bitcoin Address Classification Based on Transaction History Summarization[C]// IEEE. 1st IEEE International Conference on Blockchain and Cryptocurrency. New York: IEEE, 2019: 302-310. |
| [93] | IBRAHIM R F, MOHAMMAD E A, ABABNEH M. Illicit Account Detection in the Ethereum Blockchain Using Machine Learning[C]// IEEE. 2021 International Conference on Information Technology. New York: IEEE, 2021: 488-493. |
| [94] | KUMAR N, SINGH A, HANDA A, et al. Detecting Malicious Accounts on the Ethereum Blockchain with Supervised Learning[C]// Springer. 4th International Symposium on Cyber Security Cryptography and Machine Learning. Heidelberg: Springer, 2020: 94-109. |
| [95] |
NERURKAR P. Illegal Activity Detection on Bitcoin Transaction Using Deep Learning[J]. Soft Computing, 2023, 27(9): 5503-5520.
doi: 10.1007/s00500-022-07779-1 |
| [96] | SHEN Meng, SANG Anqi, ZHU Liehuang, et al. Abnormal Transaction Behavior Recognition Based on Motivation Analysis in Blockchain Digital Currency[J]. Chinese Journal of Computers, 2021, 44(1): 193-208. |
| 沈蒙, 桑安琪, 祝烈煌, 等. 基于动机分析的区块链数字货币异常交易行为识别方法[J]. 计算机学报, 2021, 44(1): 193-208. | |
| [97] |
WAHRSTATTER A, GOMES J J, KHAN S, et al. Improving Cryptocurrency Crime Detection: Coinjoin Community Detection Approach[J]. IEEE Transactions on Dependable and Secure Computing, 2023, 20(6): 4946-4956.
doi: 10.1109/TDSC.2023.3238412 URL |
| [98] | SUN Hanyi, RUAN Na, LIU Hanqing. Ethereum Analysis via Node Clustering[C]// Springer. 13th International Conference on Network and System Security. Heidelberg: Springer, 2019: 114-129. |
| [99] |
LIN Dan, WU Jiajing, QI Xuan, et al. Xuan Ethereum Transaction Tracking: Inferring Evolution of Transaction Networks via Link Prediction[J]. Physica A-Statistical Mechanics and Its Applications, 2022, 600: 127504-127516.
doi: 10.1016/j.physa.2022.127504 URL |
| [100] | BHARGAVI M S, KATTI S M, SHILPA M, et al. Transactional Data Analytics for Inferring Behavioural Traits in Ethereum Blockchain Network[C]// IEEE. IEEE 16th International Conference on Intelligent Computer Communication and Processing. New York: IEEE, 2020: 485-490. |
| [101] |
KAMYAR S L, JAFARZADEH G S, ELHAMBAKHSH F, et al. Monitoring Blockchain Cryptocurrency Transactions to Improve the Trustworthiness of the Fourth Industrial Revolution (Industry 4.0)[J]. Algorithms, 2020, 13(12): 312-323.
doi: 10.3390/a13120312 URL |
| [102] | LI Shengnan, YANG Zhao, TESSONE C J. Proof-of-Work Cryptocurrency Mining: A Statistical Approach to Fairness[C]// IEEE. CIC International Conference on Communications in China (ICCC). New York: IEEE, 2020: 156-161. |
| [103] |
FAN Wenjun, HONG H J, KIM J, et al. Lightweight and Identifier-Oblivious Engine for Cryptocurrency Networking Anomaly Detection[J]. IEEE Transactions on Dependable and Secure Computing, 2023, 20(2): 1302-1318.
doi: 10.1109/TDSC.2022.3152937 URL |
| [104] |
WU Jiajing, LIU Jieli, CHEN Weili, et al. Detecting Mixing Services via Mining Bitcoin Transaction Network with Hybrid Motifs[J]. IEEE Transactions on Systems Man Cybernetics-Systems, 2022, 52(4): 2237-2249.
doi: 10.1109/TSMC.2021.3049278 URL |
| [105] | KAZI A T, TAHMIN N, SYED A H. Enhanced Cryptocurrency Security by Time-Based Token Multi-Factor Authentication Algorithm[C]// IEEE. 1st International Conference on Robotics, Electrical and Signal Processing Techniques. New York: IEEE, 2019: 308-312. |
| [106] |
YU Yong, DING Yujie, ZHAO Yanqi, et al. LRCoin: Leakage-Resilient Cryptocurrency Based on Bitcoin for Data Trading in IoT[J]. IEEE Internet of Things Journal, 2019, 6(3): 4702-4710.
doi: 10.1109/JIOT.2018.2878406 |
| [107] | CHEN Ting, ZHANG Yufei, LI Zihao, et al. TokenScope: Automatically Detecting Inconsistent Behaviors of Cryptocurrency Tokens in Ethereum[C]// ACM. ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2019: 1503-1520. |
| [108] |
LIU Bin, GAO Zhifeng, XIAO Di, et al. Quantum Identity Authentication in the Counterfactual Quantum Key Distribution Protocol[J]. Entropy, 2019, 21(5): 518-533.
doi: 10.3390/e21050518 URL |
| [109] |
ZHOU L, WANG Shengtao, CHOI S, et al. Quantum Approximate Optimization Algorithm: Performance, Mechanism, and Implementation on Near-Term Devices[J]. Physical Review X, 2020, 10(2): 21067-21082.
doi: 10.1103/PhysRevX.10.021067 URL |
| [1] | QIN Sihang, DAI Weiqi, ZENG Haiyan, GU Xianjun. Secure Sharing of Power Application Data Based on Blockchain [J]. Netinfo Security, 2023, 23(8): 52-65. |
| [2] | LI Chunxiao, WANG Yaofei, XU Enliang, ZHAO Yu. Enabling Privacy-Preserving Range Queries in Blockchain-Based Collaborative Databases with Bilinear Pairings [J]. Netinfo Security, 2023, 23(3): 22-34. |
| [3] | ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism [J]. Netinfo Security, 2022, 22(9): 46-54. |
| [4] | ZHANG Yujian, LIU Daifu, TONG Fei. Reentrancy Vulnerability Detection in Smart Contracts Based on Local Graph Matching [J]. Netinfo Security, 2022, 22(8): 1-7. |
| [5] | HU Yi, SHE Kun. Blockchain and Smart Contract Based Dual-Chain Internet of Vehicles System [J]. Netinfo Security, 2022, 22(8): 26-35. |
| [6] | WANG Jian, HUANG Jun. Smart Contract-Based Log Secure Storage and Fair Access Method [J]. Netinfo Security, 2022, 22(7): 27-36. |
| [7] | YU Kechen, GUO Li, YIN Hongwei, YAN Xuesong. The High-Value Data Sharing Model Based on Blockchain and Game Theory for Data Centers [J]. Netinfo Security, 2022, 22(6): 73-85. |
| [8] | HUA Jingyu, HUANG Daming. Survey of Formal Specification Methods in Theorem Proving of Ethereum Smart Contract [J]. Netinfo Security, 2022, 22(5): 11-20. |
| [9] | FENG Jingyu, ZHANG Qi, HUANG Wenhua, HAN Gang. A Cyber Threat Intelligence Sharing Scheme Based on Cross-Chain Interaction [J]. Netinfo Security, 2022, 22(5): 21-29. |
| [10] | LI Peng, ZHENG Tiantian, XU He, ZHU Feng. RFID Security Authentication Protocol Based on Blockchain Technology [J]. Netinfo Security, 2021, 21(5): 1-11. |
| [11] | WANG Jian, YU Hang, HAN Zhen, HAN Lei. Access Control Methods of Data Sharing in Cloud Storage Based on Smart Contract [J]. Netinfo Security, 2021, 21(11): 40-47. |
| [12] | YU Kechen, GUO Li, YAO Mengmeng. Design of Blockchain-based High-value Data Sharing System [J]. Netinfo Security, 2021, 21(11): 75-84. |
| [13] | JIANG Nan, WANG Weiqi, WANG Jian. Research on Personal Information Protection Method Based on Smart Contract [J]. Netinfo Security, 2020, 20(11): 22-31. |
| [14] | Yuanjian ZHOU, Dongmei QING, Yining LIU, Songzhan LV. Design of Electronic Warehouse Receipts System Based on Blockchain [J]. Netinfo Security, 2019, 19(6): 84-90. |
| [15] | Wenming WANG, Chongyang SHI, Yinghao WANG, Dejian WEI. Research on Transaction and Security Based on Blockchain Technology [J]. Netinfo Security, 2019, 19(5): 1-9. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||