Netinfo Security ›› 2024, Vol. 24 ›› Issue (12): 1819-1830.doi: 10.3969/j.issn.1671-1122.2024.12.002
Previous Articles Next Articles
A Review of Incremental Intrusion Detection
JIN Zhigang( ), CHEN Xuyang, WU Xiaodong, LIU Kai
), CHEN Xuyang, WU Xiaodong, LIU Kai
- School of Electrical and Information Engineering, Tianjin University, Tianjin 300072, China
-
Received:2024-08-10Online:2024-12-10Published:2025-01-10
CLC Number:
Cite this article
JIN Zhigang, CHEN Xuyang, WU Xiaodong, LIU Kai. A Review of Incremental Intrusion Detection[J]. Netinfo Security, 2024, 24(12): 1819-1830.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.12.002
| 应用 场景 | 数据集 | 数据维度 | 攻击类别 |
|---|---|---|---|
| 通用 | KDD CUP99[ | 41 | DoS、R2L、U2R、Probe |
| NSL KDD[ | 41 | DoS、R2L、U2R、Probe | |
| UNSW NB15[ | 49 | DoS、Fuzzers、Analysis、Backdoors、Exploits、Generic、Reconnaissance、Shellcode、Worms | |
| CIC-IDS2017[ | 79 | Brute Force FTP、Brute Force SSH、DoS、Heartbleed、Web Attack、Infiltration、Botnet 、DDoS | |
| CSE-CIC-IDS2018[ | 83 | Brute Force FTP、Brute Force SSH、DoS、Heartbleed、Web Attack、Infiltration、Botnet、DDoS | |
| 物联网 | N-BaIoT[ | 23 | Scan、Junk、Flooding、COMBO、UDPplain |
| MQTT-UAD[ | 50 | DoS、MitM、Intrusion |
| 大类 | 文献 | 细分类别 | 数据集 | 所用方法 |
|---|---|---|---|---|
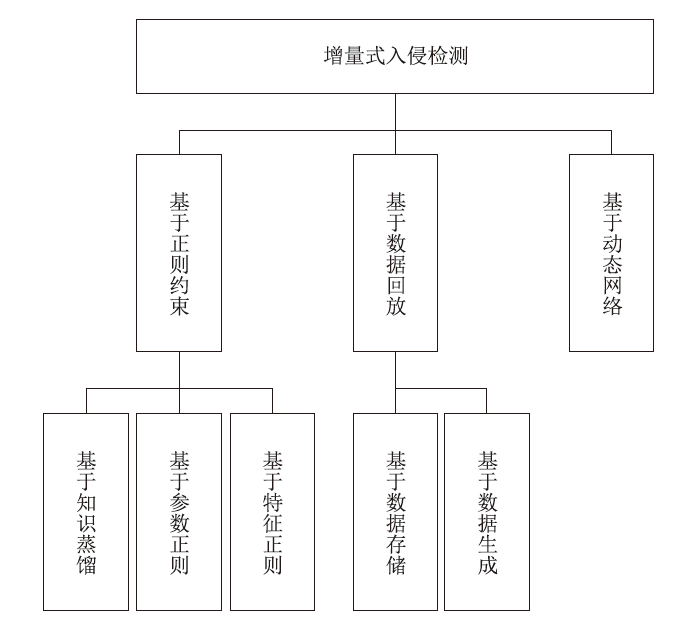
| 正则约束 | [ | 知识蒸馏 | NSL KDD/ ToN-IoT/ BoT-IoT | 一种基于联邦增量学习的开放集IDS,以Kullback-Leibler散度 作为蒸馏损失 |
| [ | 参数正则 | CIC-InvesAndMal2019 | 一种基于堆叠式去噪自动编码器的增量入侵检测方法,实现了EWC前馈神经网络 | |
| [ | 参数正则 | UNSW-NB15 | 一种基于极限学习机的增量入侵检测方法,利用旧模型参数对新模型进行约束 | |
| [ | 特征正则 | Kyoto-2006+ | 利用可对比同源样本到原型和异源样本到样本的损失函数, 实现了一种入侵检测方法 | |
| 数据回放 | [ | 数据存储 | NSL KDD/ CIC-IDS2017 | 一种基于经验回放的增量式入侵检测方法,并测试了暗经验回放方法,保存示例的输出概率 分布信息 |
| [ | 数据存储 | CIC-IDS2017 | 一种用于入侵检测系统的连续小样本学习方案,使用K-means算法选择有代表性的示例 | |
| [ | 数据存储 | CIC-IDS2017 | 一种基于GEM的增量入侵检测方法,根据梯度投影间的夹角 进行约束 | |
| [ | 数据生成 | CSE-CIC-IDS2018/ UNSW NB15 | 一种对抗辅助增强的增量式入侵检测方法,利用投影梯度下降法生成对抗样本,利用辅助BN 施加正则化约束 | |
| 动态网络 | [ | 动态网络 | CIC-IDS2017 | 一种基于堆叠广泛学习系统架构的入侵检测方法,不断堆叠学习块拓展网络 |
| [ | 动态网络 | CIC-IDS2017 | 一种基于堆叠稀疏自编码器和自组织增量神经网络的物联网入侵检测方法,学习新任务时 在网络中插入神经元 |
| [1] | China Internet Network Information Center. The 53rd Statistical Report on China’s Internet Development[EB/OL]. (2024-03-22)[2024-07-16]. https://www.cnnic.com.cn/IDR/ReportDownloads/202405/P020240509518443205347.pdf. |
| 中国互联网络信息中心. 第53次中国互联网络发展状况统计报告[EB/OL]. (2024-03-22)[2024-07-16]. https://www.cnnic.com.cn/IDR/ReportDownloads/202405/P020240509518443205347.pdf. | |
| [2] | BAI Hongpong, DENG Dongxu, XU Guangquan, et al. Research on Intrusion Detection Mechanism Based on Federated Learning[J]. Netinfo Security, 2022, 22(1): 46-54. |
| 白宏鹏, 邓东旭, 许光全, 等. 基于联邦学习的入侵检测机制研究[J]. 信息网络安全, 2022, 22(1):46-54. | |
| [3] | ANDERSON J P. Computer Security Threat Monitoring and Surveillance[M]. Washington: James P. Anderson Company, 1980. |
| [4] | JAY N, PEGAH M, ANWAR S M, et al. Machine Learning Based Intrusion Detection Systems for Connected Autonomous Vehicles: A Survey[J]. Peer-to-Peer Networking and Applications, 2023, 16(5): 2153-2185. |
| [5] | KAN Xiu, FAN Yixuan, FANG Zhijun, et al. A Novel IoT Network Intrusion Detection Approach Based on Adaptive Particle Swarm Optimization Convolutional Neural Network[J]. Information Sciences, 2021, 568: 147-162. |
| [6] | ZHANG Hao, XIE Dazhi, HU Yunsheng, et al. A Review of Network Anomaly Detection Based on Semi-Supervised Learning[J]. Netinfo Security, 2024, 24(4): 491-508. |
| 张浩, 谢大智, 胡云晟, 等. 基于半监督学习的网络异常检测研究综述[J]. 信息网络安全, 2024, 24(4):491-508. | |
| [7] | MASANA M, LIU Xialei, TWARDOWSKI B, et al. Class-Incremental Learning: Survey and Performance Evaluation on Image Classification[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2023, 45(5): 5513-5533. |
| [8] | LIN Huiwei, FENG Shanshan, LI Xutao, et al. Anchor Assisted Experience Replay for Online Class-Incremental Learning[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2023, 33(5): 2217-2232. |
| [9] | PUTINA A, ROSSI D. Online Anomaly Detection Leveraging Stream-Based Clustering and Real-Time Telemetry[J]. IEEE Transactions on Network and Service Management, 2021, 18(1): 839-854. |
| [10] | MCCLOSKEY M. COHEN N J. Catastrophic Interference in Connectionist Networks: the Sequential Learning Problem[M]. Amsterdam: Elsevier, 1989. |
| [11] | REBULFFI S A, KOLESNIKOV A, SPERL G, et al. iCaRL: Incremental Classifier and Representation Learning[C]// IEEE. Proceedings of the lEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2017: 2001-2010. |
| [12] | AGARWAL R, JOSHI M V. PNrule:A New Framework for Learning Classifier Models in Data Mining (A Case-Study in Network Intrusion Detection)[ C]//SIAM. The 2001 SIAM International Conference on Data Mining. Philadelphia: SIAM, 2001: 1-17. |
| [13] | CUI Kuiyong. Research on Clustering Technique in Network Intrusion Detection[C]// IEEE. 2012 International Conference on Industrial Control and Electronics Engineering. New York: IEEE, 2012: 1203-1205. |
| [14] | YANG Yu, YAN Yu, SHEN Fang, et al. Review of Intrusion Detection Based on Machine and Deep Learning[J]. Science Technology and Engineering, 2023, 23(18): 7607-7621. |
| 杨宇, 闫钰, 申芳, 等. 基于机器和深度学习的入侵检测综述[J]. 科学技术与工程, 2023, 23(18):7607-7621. | |
| [15] | LU Yijun, TENG Shaohua. Application of Sequence Embedding in Host-Based Intrusion Detection System[C]// IEEE. 2021 IEEE 24th International Conference on Computer Supported Cooperative Work in Design (CSCWD). New York: IEEE, 2021: 434-439. |
| [16] | WANG Rong, MA Chunguang, WU Peng. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network[J]. Netinfo Security, 2020, 20(4): 47-54. |
| 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4):47-54. | |
| [17] | HETTICH S, BAY S D. KDD Cup 1999 Data[EB/OL]. (1999-10-28)[2024-07-24]. http://kdd.ics.uci.edu/databases/kddcup99/kddcup99.html. |
| [18] | TAVALLAEE M, BAGHERI E, LU Wei, et al. A Detailed Analysis of the KDD CUP 99 Data Set[C]// IEEE. Second IEEE Symposium on Computational Intelligence for Security and Defense Applications (CISDA). New York: IEEE, 2009: 1-6. |
| [19] | UNSW. UNSW-NB15[EB/OL]. (2019-03-10)[2024-07-24]. http://www.cybersecurity.unsw.adfa.edu.au/AD-FA%20NB15%20Datasets. |
| [20] | SHARAFALDIN I, LASHKARI A H, GHORBANI A A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization[C]// Springer. 4th International Conference on Information Systems Security and Privacy (ICISSP). Heidelberg: Springer, 2018: 108-116. |
| [21] | MEIDAN Y, BOHADANA M, MATHOV Y, et al. N-BaIoT—Network-Based Detection of IoT Botnet Attacks Using Deep Autoencoders[J]. IEEE Pervasive Computing, 2018, 17(3): 12-22. |
| [22] | HECTOR A M, JOSE A M, JORGR O G, et al. Multiclass Classification Procedure for Detecting Attacks on MQTT-IoT Protocol[J]. Complexity, 2019, 2019(1): 6516253-6516263. |
| [23] | ZHOU Dawei, WANG Fuyun, YE Hanjia, et al. Deep Learning for Class-Incremental Learning: A Survey[J]. Chinese Journal of Computers. 2023, 46(8): 1577-1605. |
| 周大蔚, 汪福运, 叶翰嘉, 等. 基于深度学习的类别增量学习算法综述[J]. 计算机学报, 2023, 46(8):1577-1605. | |
| [24] | SUN Wenju, LI Qingyong, ZHANG Jing, et al. Survey of Incremental Learning with Deep Neural Networks[EB/OL]. (2024-06-24)[2024-07-24]. http://kns.cnki.net/kcms/detail/10.1478.G2.20240621.1608.002.html. |
| 孙文举, 李清勇, 张靖, 等. 基于深度神经网络的增量学习研究综述[EB/OL]. (2024-06-24)[2024-07-24]. http://kns.cnki.net/kcms/detail/10.1478.G2.20240621.1608.002.html. | |
| [25] | HINTON G, VINYALS O, DEAN J. Distilling the Knowledge in a Neural Network[J]. Computer Science, 2015, 14(7): 38-39. |
| [26] | XU Xiaohu, LIANG Yifei, ZHANG Xixi, et al. Self-Evolving Malware Detection for Cyber Security Using Network Traffic and Incremental Learning[C]// IEEE. 2022 9th International Conference on Dependable Systems and Their Applications (DSA). New York: IEEE, 2022: 454-463. |
| [27] | JIN Dong, CHEN Shuangwu, HE Huasen, et al. Federated Incremental Learning Based Evolvable Intrusion Detection System for Zero-Day Attacks[J]. IEEE Network, 2023, 37(1): 125-132. |
| [28] | PRASATH S, SETHI K, MOHANTY D, P. et al. Analysis of Continual Learning Models for Intrusion Detection System[J]. IEEE Access, 2022, 10: 121444-121464. |
| [29] | MACKAY D J. A Practical Bayesian Framework for Backpropagation Networks[J]. Neural Computation, 1992, 4(3): 448-472. |
| [30] | KIRKAPATRICK J, PASCANU R, RABINOWITZ N, et al. Overcoming Catastrophic Forgetting in Neural Networks[J]. Proceedings of the National Academy of Sciences, 2017, 114(13): 3521-3526. |
| [31] | HASAN N, RAHMAN S I, SHOHAG M S A. dAEMD: Deep Autoencoder Based Malware Detection from Android Network Flows[C]// IEEE. 2023 26th International Conference on Computer and Information Technology (ICCIT). New York: IEEE, 2023: 1-7. |
| [32] | GYAMFI E, JURCUT A D. Novel Online Network Intrusion Detection System for Industrial IoT Based on OI-SVDD and AS-ELM[J]. IEEE Internet of Things Journal, 2023, 10(5): 3827-3839. |
| [33] | CHATHOTH A K, NECCIAI C P, JAGANNATHA A. Differentially Private Federated Continual Learning with Heterogeneous Cohort Privacy[C]// IEEE. 2022 IEEE International Conference on Big Data (Big Data). New York: IEEE, 2022: 5682-5691. |
| [34] | WU Yixuan, NIE Laisen, XIONG Xuanrui, et al. Incremental Update Intrusion Detection for Industry 5.0 Security: A Graph Attention Network-Enabled Approach[J]. IEEE Transactions on Consumer Electronics, 2024, 70(1): 2004-2017. |
| [35] | YANG Jingyu, SHEN Yi, DENG Linan. Continual Contrastive Anomaly Detection under Natural Data Distribution Shifts[C]// IEEE. 2023 8th International Conference on Automation, Control and Robotics Engineering (CACRE). New York: IEEE, 2023: 144-149. |
| [36] | WU Xiaodong, JIN Zhigang, CHEN Xuyang, et al. Adversarial Learning-Augmented Incremental Intrusion Detection System[EB/OL]. (2024-06-17)[2024-07-24]. http://kns.cnki.net/kcms/detail/23.1235.t.20240615.2327.002.html. |
| 武晓栋, 金志刚, 陈旭阳, 等. 对抗学习辅助增强的增量式入侵检测系统[EB/OL]. (2024-06-17)[2024-07-24]. http://kns.cnki.net/kcms/detail/23.1235.t.20240615.2327.002.html. | |
| [37] | WANG Wenjie, ZHANG Chunying, WANG Liya, et al. Incremental Intrusion Detection Model Based on Combination of IPCA and CN[J]. Journal of North China University of Science and Technology(Natural Science Edition), 2023, 45(3): 90-100. |
| 王文杰, 张春英, 王立亚, 等. 融合IPCA和CNN的增量入侵检测模型[J]. 华北理工大学学报(自然科学版), 2023, 45(3):90-100. | |
| [38] | DU Lei, GU Zhanoquan, WANG Ye, et al. A Few-Shot Class-Incremental Learning Method for Network Intrusion Detection[J]. IEEE Transactions on Network and Service Management, 2024, 21(2): 2389-2401. |
| [39] | NUGRAHA B, YADAV K, PATIL P, et al. Improving the Detection of Unknown DDoS Attacks through Continual Learning[C]// IEEE. 2023 IEEE International Conference on Cyber Security and Resilience (CSR). New York: IEEE, 2023: 477-483. |
| [40] | SIRITHARAGUL K, SODSEE S. Applying Modified Convolutional Neural Networks for Detecting Intrusion[C]// IEEE. 2023 7th International Conference on Information Technology (InCIT). New York: IEEE, 2023: 446-451. |
| [41] | KIM H, KIM D D, CHO J H, et al. Continual Learning with Network Intrusion Dataset[C]// IEEE. 2022 IEEE International Conference on Big Data (Big Data). New York: IEEE, 2022: 6702-6704. |
| [42] | FABER K, SNIEZYNSKI B, CORIZZO R. Distributed Continual Intrusion Detection: A Collaborative Replay Framework[C]// IEEE. 2023 IEEE International Conference on Big Data (BigData). New York: IEEE, 2023: 3255-3256. |
| [43] | XU Hao, WANG Yongjun. A Continual Few-Shot Learning Method via Meta-Learning for Intrusion Detection[C]// IEEE. 2022 IEEE 4th International Conference on Civil Aviation Safety and Information Technology (ICCASIT). New York: IEEE, 2022: 1188-1194. |
| [44] | FABER K, CORIZZO R, SNIEZYNSKI B, et al. Active Lifelong Anomaly Detection with Experience Replay[C]// IEEE. 2022 IEEE 9th International Conference on Data Science and Advanced Analytics (DSAA). New York: IEEE, 2022: 1-10. |
| [45] | AGBEDANU P R, MUSABE R, RWIGEMA J, et al. IPCA-SAMKNN: A Novel Network IDS for Resource Constrained Devices[C]// IEEE. 2022 2nd International Seminar on Machine Learning, Optimization, and Data Science (ISMODE). New York: IEEE, 2022: 540-545. |
| [46] | ELDHAI A M, HAMDAN M, KHAN S, et al. Traffic Classification Based on Incremental Learning Algorithms for the Software-Defined Networks[C]// IEEE. 2022 International Conference on Frontiers of Information Technology (FIT). New York: IEEE, 2022: 338-343. |
| [47] | ZHANG Chenyun, LIU Jin, ZHI Jiamao, et al. OceanCL-IDS: A Continual Learning-Based Intrusion Detection System for Ocean-Going Ship-Satellite Communication Network[C]// IEEE. 2023 7th International Conference on Transportation Information and Safety (ICTIS). New York: IEEE, 2023: 1150-1155. |
| [48] | SABEEL U, HEYDARI S S, EL-KHATIB K, et al. Incremental Adversarial Learning for Polymorphic Attack Detection[J]. IEEE Transactions on Machine Learning in Communications and Networking, 2024, 2: 869-887. |
| [49] | PASIKHANI A M, CLARK J A, GOPE P. Adversarial RL-Based IDS for Evolving Data Environment in 6LoWPAN[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 3831-3846. |
| [50] | XU Xiaohu, ZHANG Xixi, ZHANG Qianyun, et al. Advancing Malware Detection in Network Traffic with Self-Paced Class Incremental Learning[J]. IEEE Internet of Things Journal, 2024, 11(12): 21816-21826. |
| [51] | HE Xiaoqiang, CHEN Qianbin, WANG Weili, et al. Stacked Broad Learning System Empowered FCL Assisted by DTN for Intrusion Detection in UAV Networks[C]// IEEE. 2023 IEEE Global Communications Conference. New York: IEEE, 2023: 5372-5377. |
| [52] | HE Xiaoqiang, TANG Lun, WANG Weili, et al. Federated Continuous Learning Based on Stacked Broad Learning System Assisted by Digital Twin Networks: An Incremental Learning Approach for Intrusion Detection in UAV Networks[J]. IEEE Internet of Things Journal, 2023, 10(22): 19825-19838. |
| [53] | ZHAO Yuxin, BI Zixiang, XU Guosheng, et al. Tree-IDS: An Incremental Intrusion Detection System for Connected Vehicles[C]// IEEE. 2023 IEEE 48th Conference on Local Computer Networks (LCN). New York: IEEE, 2023: 1-4. |
| [54] |
LIU Qiang, ZHANG Ying, ZHOU Weixiang, et al. Adaptive Class Incremental Learning-Based IoT Intrusion Detection System[J]. Computer Engineering, 2023, 49(2): 169-174.
doi: 10.19678/j.issn.1000-3428.0063917 |
|
刘强, 张颖, 周卫祥, 等. 自适应类增量学习的物联网入侵检测系统[J]. 计算机工程, 2023, 49(2):169-174.
doi: 10.19678/j.issn.1000-3428.0063917 |
|
| [55] | WU Shuguang, WANG Hongyan, YAN Nanjiang, et al. Research in Network Anomaly Detection Based on SOINN Incremental Autoencoders[J]. Journal of Ordnance Equipment Engineering, 2023, 44(5): 239-248. |
| 吴署光, 王宏艳, 颜南江, 等. 基于SOINN增量自编码器的网络异常检测研究[J]. 兵器装备工程学报, 2023, 44(5):239-248. |
| [1] | LIU Lianhai, LI Huiye, MAO Donghui. CBAM-CNN Network-Based Intrusion Detection Method Using Image Convex Hull Features [J]. Netinfo Security, 2024, 24(9): 1422-1431. |
| [2] | ZHANG Hao, XIE Dazhi, HU Yunsheng, YE Junwei. A Review of Network Anomaly Detection Based on Semi-Supervised Learning [J]. Netinfo Security, 2024, 24(4): 491-508. |
| [3] | JIANG Rong, LIU Haitian, LIU Cong. Unsupervised Network Intrusion Detection Method Based on Ensemble Learning [J]. Netinfo Security, 2024, 24(3): 411-426. |
| [4] | FENG Guangsheng, JIANG Shunpeng, HU Xianlang, MA Mingyu. New Research Progress on Intrusion Detection Techniques for the Internet of Things [J]. Netinfo Security, 2024, 24(2): 167-178. |
| [5] | JIN Zhigang, DING Yu, WU Xiaodong. Federated Intrusion Detection Algorithm with Bilateral Correction Merging Gradient Difference [J]. Netinfo Security, 2024, 24(2): 293-302. |
| [6] | SUN Hongzhe, WANG Jian, WANG Peng, AN Yulong. Network Intrusion Detection Method Based on Attention-BiTCN [J]. Netinfo Security, 2024, 24(2): 309-318. |
| [7] | LI Jiao, ZHANG Yuqing, WU Yabiao. Data Augmentation Method via Large Language Model for Relation Extraction in Cybersecurity [J]. Netinfo Security, 2024, 24(10): 1477-1483. |
| [8] | SHEN Hua, TIAN Chen, GUO Sensen, MU Zhiying. Research on Adversarial Machine Learning-Based Network Intrusion Detection Method [J]. Netinfo Security, 2023, 23(8): 66-75. |
| [9] | PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain [J]. Netinfo Security, 2023, 23(8): 76-85. |
| [10] | WANG Xiaodi, HUANG Cheng, LIU Jiayong. A Survey of Cyber Security Open-Source Intelligence Knowledge Graph [J]. Netinfo Security, 2023, 23(6): 11-21. |
| [11] | LIU Changjie, SHI Runhua. A Smart Grid Intrusion Detection Model for Secure and Efficient Federated Learning [J]. Netinfo Security, 2023, 23(4): 90-101. |
| [12] | GAO Qingguan, ZHANG Bo, FU Anmin. An Advanced Persistent Threat Detection Method Based on Attack Graph [J]. Netinfo Security, 2023, 23(12): 59-68. |
| [13] | JIN Zhigang, LIU Kai, WU Xiaodong. A Review of IDS Research in Smart Grid AMI Field [J]. Netinfo Security, 2023, 23(1): 1-8. |
| [14] | WANG Huazhong, TIAN Zilei. Intrusion Detection Method of ICS Based on Improved CGAN Algorithm [J]. Netinfo Security, 2023, 23(1): 36-43. |
| [15] | LIU Xiangyu, LU Tianliang, DU Yanhui, WANG Jingxiang. Lightweight IoT Intrusion Detection Method Based on Feature Selection [J]. Netinfo Security, 2023, 23(1): 66-72. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||