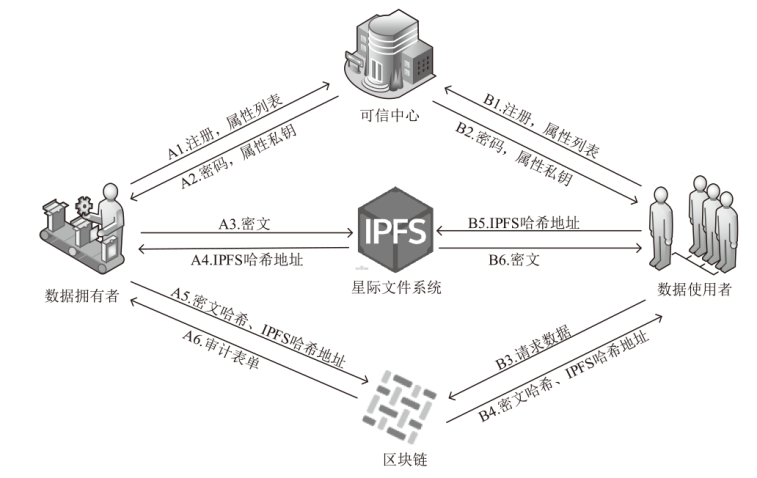
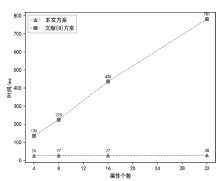
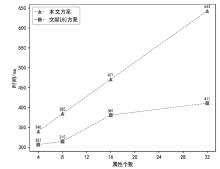
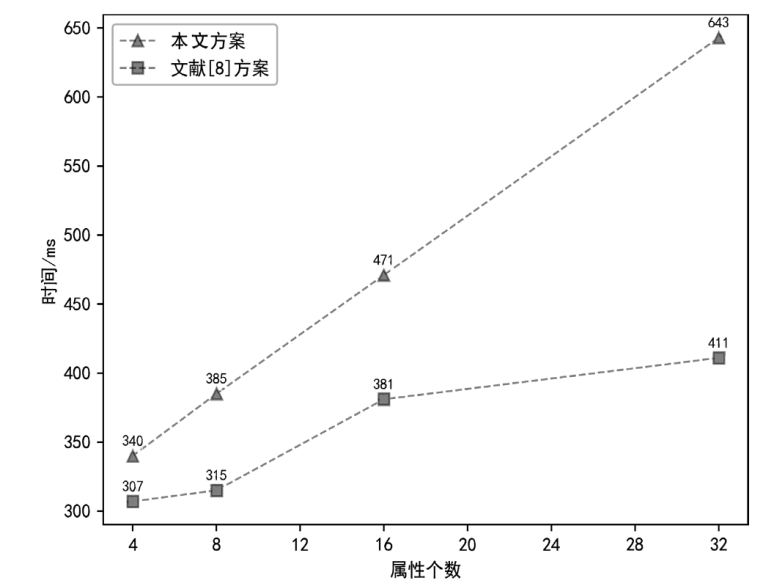
Netinfo Security ›› 2023, Vol. 23 ›› Issue (9): 37-46.doi: 10.3969/j.issn.1671-1122.2023.09.004
Previous Articles Next Articles
Blockchain Access Control Scheme with SM9-Based Attribute Encryption
ZHOU Quan1( ), CHEN Minhui2, WEI Kaijun2, ZHENG Yulong1
), CHEN Minhui2, WEI Kaijun2, ZHENG Yulong1
- 1. School of Mathematics and Information Science, Guangzhou University, Guangzhou 510006, China
2. School of Computer Science and Cyber Engineering, Guangzhou University, Guangzhou 510006, China
-
Received:2023-02-08Online:2023-09-10Published:2023-09-18 -
Contact:ZHOU Quan E-mail:zhouqq@gzhu.edu.cn
CLC Number:
Cite this article
ZHOU Quan, CHEN Minhui, WEI Kaijun, ZHENG Yulong. Blockchain Access Control Scheme with SM9-Based Attribute Encryption[J]. Netinfo Security, 2023, 23(9): 37-46.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.09.004
| 访问结构(L) | 访问矩阵(M) |
|---|---|
| ((a, b, 2),(c, d, 1), e, 2) | (1) |
(a,b,2) \\ (c,d,1) \\ e \\ \end{matrix} \right)$ | 1 & 1 \\ 1 & 2 \\ 1 & 3 \\ \end{matrix} \right)$ |
a \\ b \\ (c,d,1) \\ e \\ \end{matrix} \right)$ | 1 & 1 & 1 \\ 1 & 1 & 2 \\ 1 & 2 & 0 \\ 1 & 3 & 0 \\ \end{matrix} \right)$ |
a \\ b \\ c \\ d \\ e \\ \end{matrix} \right)$ | 1 & 1 & 1 \\ 1 & 1 & 2 \\ 1 & 2 & 0 \\ 1 & 2 & 0 \\ 1 & 3 & 0 \\ \end{matrix} \right)$ |
| [1] | WATERS B. Ciphertext-Policy Attribute-Based Encryption: An Expressive, Efficient, and Provably Secure Realization[C]// Springer. International Conference on Practice and Theory in Public Key Cryptography. Heidelberg: Springer, 2011: 53-70. |
| [2] | GM/T 0044-2016 Information Security Technology-Identity-Based Cryptographic Algorithms SM9[S]. Beijing: Standards Press of China, 2016. |
| GM/T 0044-2016 SM9标识密码算法[S]. 北京: 中国标准出版社, 2016. | |
| [3] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. (2008-10-31)[2023-01-11]. https://bitcoin.org/bitcoin.pdf. |
| [4] | ZHU Liehuang, GAO Feng, SHEN Meng, et al. Survey on Privacy Preserving Techniques for Blockchain Technology[J]. Journal of Computer Research and Development, 2017, 54(10): 2170-2186. |
| 祝烈煌, 高峰, 沈蒙, 等. 区块链隐私保护研究综述[J]. 计算机研究与发展, 2017, 54(10): 2170-2186. | |
| [5] | ZHANG Yunru, HE Debiao, CHOO K. BaDS: Blockchain-Based Architecture for Data Sharing with ABS and CP-ABE in IoT[J]. Wireless Communications and Mobile Computing, 2018(7): 1-9. |
| [6] | PINNO O, GREGIO A, BONA L. ControlChain: Blockchain As A Central Enabler for Access Control Authorizations in the IoT[C]// IEEE. Globecom IEEE Global Communications Conference. New York: IEEE, 2017: 1-6. |
| [7] |
WANG Qiange, HE Pu, NIE Tiezheng, et al. Survey of Data Storage and Query Techniques in Blockchain Systems[J]. Computer Science, 2018, 45(12): 12-18.
doi: 10.11896/j.issn.1002-137X.2018.12.002 |
| 王千阁, 何蒲, 聂铁铮, 等. 区块链系统的数据存储与查询技术综述[J]. 计算机科学, 2018, 45(12): 12-18. | |
| [8] |
JI Honghan, ZHANG Hongjie, SHAO Lisong, et al. An Efficient Attribute-Based Encryption Scheme Based on SM9 Encryption Algorithm for Dispatching and Control Cloud[J]. Connection Science, 2021, 33(4): 1094-1115.
doi: 10.1080/09540091.2020.1858757 URL |
| [9] |
WANG Hao, SONG Yujiao. Secure Cloud-Based EHR System Using Attribute-Based Cryptosystem and Blockchain[J]. Journal of Medical Systems, 2018, 42(8): 1-9.
doi: 10.1007/s10916-017-0844-y URL |
| [10] |
POURNAGHI S M, BAYAT M, FARJAMI Y. MedSBA: A Novel and Secure Scheme to Share Medical Data Based on Blockchain Technology and Attribute-Based Encryption[J]. Journal of Ambient Intelligence and Humanized Computing, 2020, 11(11): 4613-4641.
doi: 10.1007/s12652-020-01710-y |
| [11] |
TIAN Youliang, YANG Kedi, WANG Zuan, et al. Algorithm of Blockchain Data Provenance Based on ABE[J]. Journal on Communications, 2019, 40(11): 101-111.
doi: 10.11959/j.issn.1000-436x.2019222 |
|
田有亮, 杨科迪, 王缵, 等. 基于属性加密的区块链数据溯源算法[J]. 通信学报, 2019, 40(11): 101-111.
doi: 10.11959/j.issn.1000-436x.2019222 |
|
| [12] |
CHENG Lichen, LIU Jiqiang, XU Guangquan, et al. SCTSC: A Semicentralized Traffic Signal Control Mode with Attribute-Based Blockchain in IoVs[J]. IEEE Transactions on Computational Social Systems, 2019, 6(6): 1373-1385.
doi: 10.1109/TCSS.6570650 URL |
| [13] | ZOU Yipeng, PENG Tao, ZHONG Wentao, et al. Reliable and Controllable Data Sharing Based on Blockchain[C]// Springer. Inernational Conference on Ubiquitous Security. Heidelberg: Springer, 2021: 229-240. |
| [14] | WANG Tong, MA Wenping, LUO Wei. Information Sharing and Secure Multi-Party Computing Model Based on Block-Chain[J]. Computer Science, 2019, 46(9): 162-168. |
| 王童, 马文平, 罗维. 基于区块链的信息共享及安全多方计算模型[J]. 计算机科学, 2019, 46(9): 162-168. | |
| [15] | ZHANG Guochao, WANG Ruijin. Blockchain Sharding Storage Model Based on Threshold Secret Sharing[J]. Computer Applications, 2019, 39(9): 2617-2622. |
| 张国潮, 王瑞锦. 基于门限秘密共享的区块链分片存储模型[J]. 计算机应用, 2019, 39(9): 2617-2622. | |
| [16] | PENG Yanqing, DU Min, LI Feifei, et al. FalconDB: Blockchain-Based Collaborative Database[C]// ACM. ACM SIGMOD International Conference on Management of Data. New York: ACM, 2020: 637-652. |
| [17] |
GUO Yu, XIE Hongcheng, MIAO Yinbin, et al. Fedcrowd: A Federated and Privacy-Preserving Crowdsourcing Platform on Blockchain[J]. IEEE Transactions on Services Computing, 2020, 15(4): 2060-2073.
doi: 10.1109/TSC.2020.3031061 URL |
| [18] | WANG Mingyue, GUO Yu, ZHANG Chen, et al. MedShare: A Privacy-Preserving Medical Data Sharing System by Using Blockchain[J]. IEEE Transactions on Services Computing, 2021, 9: 438-451. |
| [19] |
GUO Yu, ZHANG Chen, WANG Cong, et al. Towards Public Verifiable and Forward-Privacy Encrypted Search by Using Blockchain[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 5: 1-16.
doi: 10.1109/TDSC.2008.9 URL |
| [20] |
SHI Yang, MA Zhiyuan, QIN Rufu, et al. Implementation of an Attribute-Based Encryption Scheme Based on SM9[J]. Applied Sciences, 2019, 9(15): 3074-3088.
doi: 10.3390/app9153074 URL |
| [21] | SAHAI A, WATERS B. Fuzzy Identity-Based Encryption[C]// Springer. Annual International Conference on Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2005: 457-473. |
| [22] | GOYAL V, PANDEY O, SAHAI A, et al. Attribute-Based Encryption for Fine-Grained Access Control of Encrypted Data[C]// ACM. ACM Conference on Computer and Communications Security. New York: ACM, 2006: 89-98. |
| [23] | BETHENCOURT J, SAHAI A, WATERS B. Ciphertext-Policy Attribute-Based Encryption[C]// IEEE. IEEE Symposium on Security and Privacy. New York: IEEE, 2007: 321-334. |
| [24] | LIU Zhen, CAO Zhenfu. On Efficiently Transferring the Linear Secret-Sharing Scheme Matrix in Ciphertext-Policy Attribute-Based Encryption[EB/OL]. [2023-01-11]. https://citeseerx.ist.psu.edu/document?repid=rep1&type=pdf&doi=8f0502461693d016c6a46b73ad20f4fc23f45c54. |
| [1] | GONG Pengfei, XIE Sijiang, CHENG Andong. The Multi-Leader Consensus Algorithm Based on Improvements to HotStuff [J]. Netinfo Security, 2023, 23(9): 108-117. |
| [2] | ZHAO Jiahao, JIANG Jiajia, ZHANG Yushu. Cross-Chain Data Consistency Verification Model Based on Dynamic Merkle Hash Tree [J]. Netinfo Security, 2023, 23(9): 95-107. |
| [3] | SHAO Zhenzhe, JIANG Jiajia, ZHAO Jiahao, ZHANG Yushu. An Improved Weighted Byzantine Fault Tolerance Algorithm for Cross-Chain System [J]. Netinfo Security, 2023, 23(8): 109-120. |
| [4] | QIN Sihang, DAI Weiqi, ZENG Haiyan, GU Xianjun. Secure Sharing of Power Application Data Based on Blockchain [J]. Netinfo Security, 2023, 23(8): 52-65. |
| [5] | PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain [J]. Netinfo Security, 2023, 23(8): 76-85. |
| [6] | YU Huifang, QIAO Yifan, MENG Ru. Attribute-Based Anti-Quantum Threshold Ring Signcryption Scheme for Blockchain-Based Finance [J]. Netinfo Security, 2023, 23(7): 44-52. |
| [7] | SHI Runhua, XIE Chenlu. Verifiable Outsourcing EMR Scheme with Attribute-Based Encryption in Cloud-Edge Environments [J]. Netinfo Security, 2023, 23(7): 9-21. |
| [8] | ZHANG Xiaoxu, SHI Runhua. An Access Control Scheme for Verifying the Correctness of Outsourcing Encrypted Data in EHR System [J]. Netinfo Security, 2023, 23(5): 85-94. |
| [9] | LI Li, ZHU Jiangwen, YANG Chunyan. Overview of Research on the Revocable Mechanism of Attribute-Based Encryption [J]. Netinfo Security, 2023, 23(4): 39-50. |
| [10] | GUO Rui, WEI Xin, CHEN Li. An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System [J]. Netinfo Security, 2023, 23(3): 1-12. |
| [11] | LI Chunxiao, WANG Yaofei, XU Enliang, ZHAO Yu. Enabling Privacy-Preserving Range Queries in Blockchain-Based Collaborative Databases with Bilinear Pairings [J]. Netinfo Security, 2023, 23(3): 22-34. |
| [12] | ZHANG Xuewang, ZHANG Hao, YAO Yaning, FU Jiali. Privacy Protection Scheme of Consortium Blockchain Based on Group Signature and Homomorphic Encryption [J]. Netinfo Security, 2023, 23(3): 56-61. |
| [13] | WANG Jingyu, MA Zhaofeng, XU Danheng, DUAN Pengfei. Blockchain Transaction Data Privacy-Preserving Scheme Supporting National Cryptographic Algorithm [J]. Netinfo Security, 2023, 23(3): 84-95. |
| [14] | FENG Yiting, MA Zhaofeng, XU Danheng, DUAN Pengfei. Evaluation Method for Cross-Chain Security Strength Access [J]. Netinfo Security, 2023, 23(1): 84-92. |
| [15] | ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism [J]. Netinfo Security, 2022, 22(9): 46-54. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||