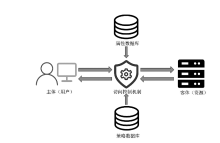
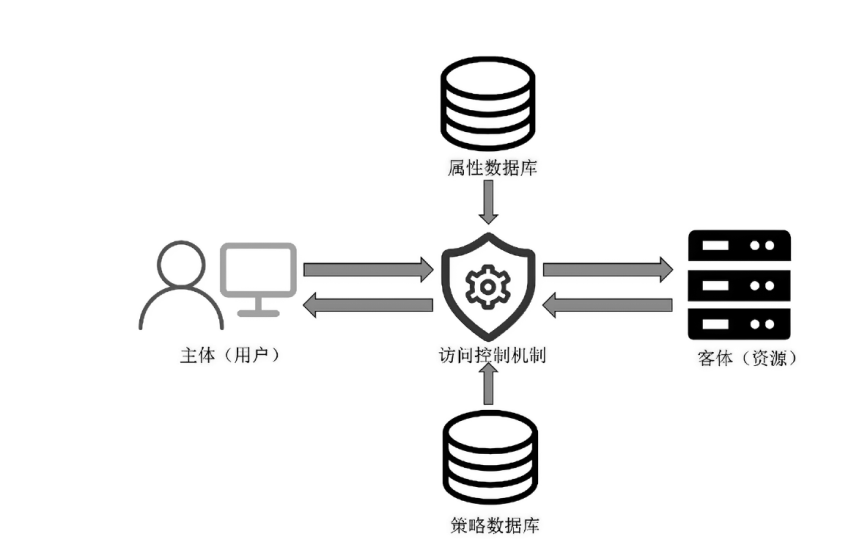
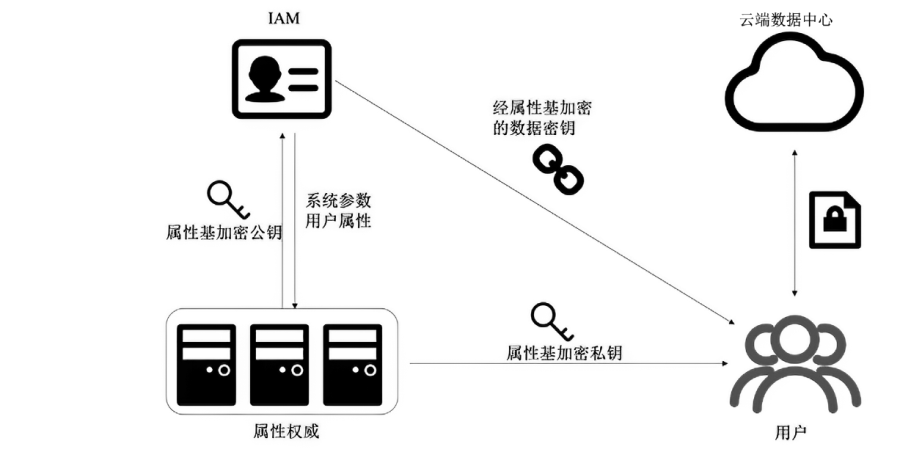
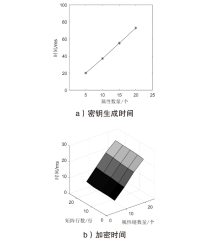
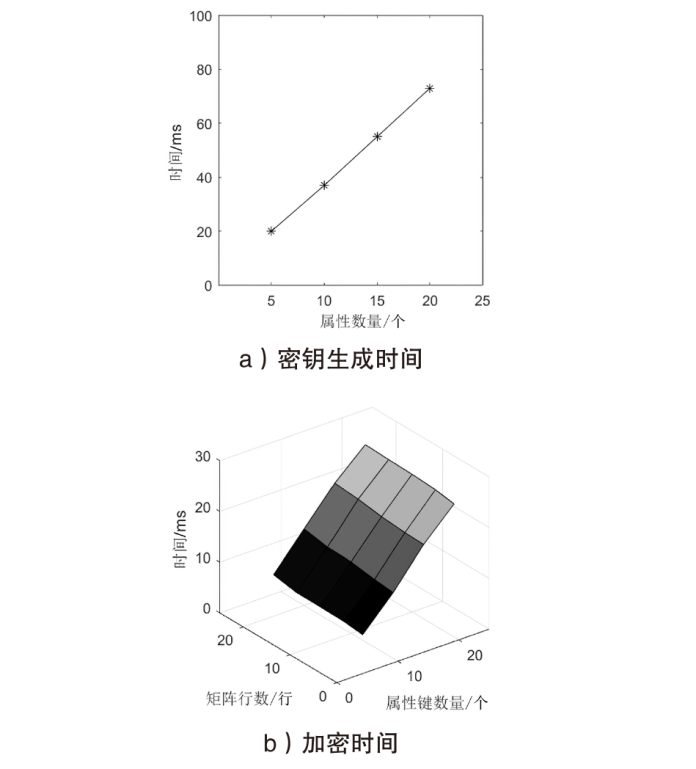
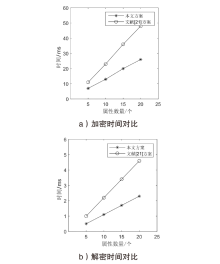
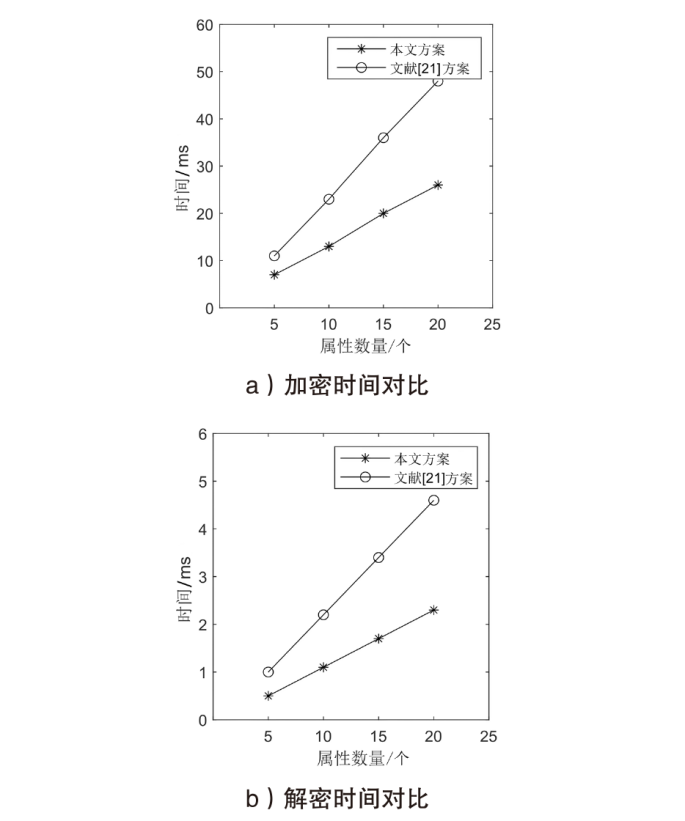
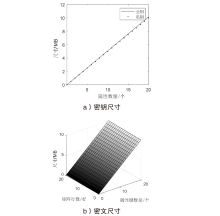
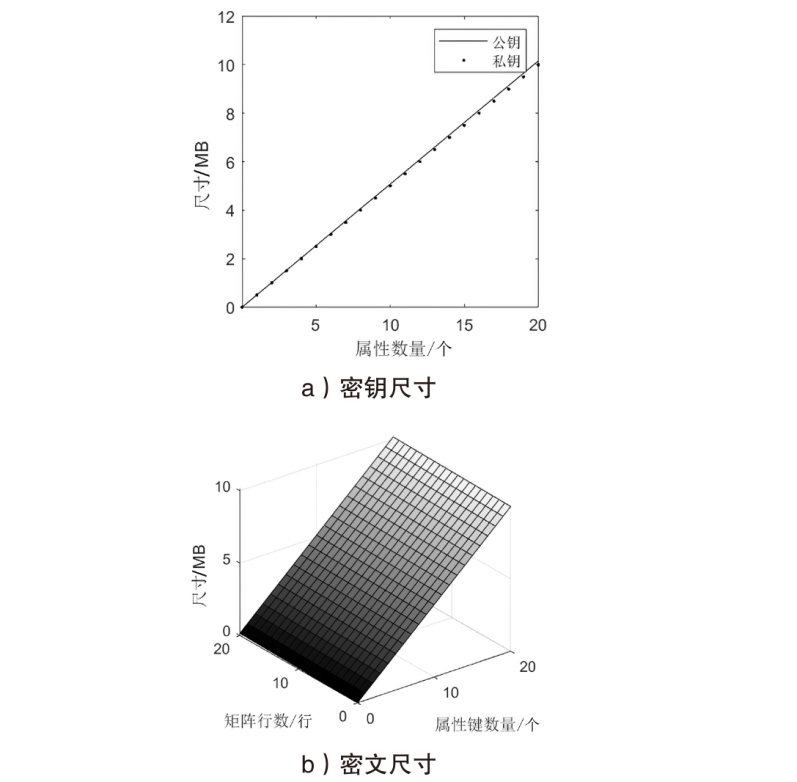
| [1] |
HU V C, FERRAIOLO D, KUHN R, et al. Guide to Attribute Based Access Control (ABAC) Definition and Considerations[EB/OL]. (2019-08-02)[2023-05-10]. https://nvlpubs.nist.gov/nistpubs/specialpublications/NIST.SP.800-162.pdf.
|
| [2] |
SAHAI A, WATERS B. Fuzzy Identity-Based Encryption[C]// IACR. 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer, 2005: 457-473.
|
| [3] |
CHEN L, MOODY D, LIU Yikai. Post-Quantum Cryptography[EB/OL]. (2022-06-05)[2023-05-10]. https://csrc.nist.gov/projects/post-quantum-cryptography.
|
| [4] |
DATTA P, KOMARGOSKI I, WATERS B. Decentralized Multi-Authority ABE for NC1 from Computational-BDH[J]. Journal of Cryptology, 2023, 36(6): 1-31.
doi: 10.1007/s00145-022-09441-3
|
| [5] |
BONEH D, GENTRY C, GORBUNOV S, et al. Fully Key-Homomorphic Encryption, Arithmetic Circuit ABE and Compact Garbled Circuits[C]// IACR. 33rd Annual International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer, 2014: 533-556.
|
| [6] |
BRAKERSKI D, VAIKUNTANATHAN V. Lattice-Inspired Broadcast Encryption and Succinct Ciphertext-Policy ABE[EB/OL]. (2021-04-26)[2023-05-10]. https://eprint.iacr.org/2020/191.
|
| [7] |
WEE H. Optimal Broadcast Encryption and CP-ABE from Evasive Lattice Assumptions[C]// IACR. 41st Annual International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer, 2022: 217-241.
|
| [8] |
DATTA P, KOMARGODSKI I, WATERS B. Decentralized Multi-Authority ABE for DNFs from LWE[C]// IACR. 40th Annual International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer, 2021: 177-209.
|
| [9] |
WATERS B, WEE H, WU D. Multi-Authority ABE from Lattices without Random Oracles[C]// IACR. Theory of Cryptography:20th International Conference. Berlin: Springer, 2022: 651-679.
|
| [10] |
BEIMEL A. Secure Schemes for Secret Sharing and Key Distribution[D]. Israel: Israel Institute of Technology, 1996.
|
| [11] |
LYUBASHEVSKY V, MICCIANCIO D. Generalized Compact Knapsacks are Collision Resistant[C]// EATCS. Automata, Languages and Programming:33rd International Colloquium. Berlin: Springer, 2006: 144-155.
|
| [12] |
LYUBASHEVSKY V, PEIKERT C, Regev O. On Ideal Lattices and Learning with Errors over Rings[J]. Journal of the ACM, 2013, 60(6): 1-35.
|
| [13] |
STEHLÉ D, STEINFELD R, TANAKA K, et al. Efficient Public-Key Encryption Based on Ideal Lattices[C]// IACR. 15th International Conference on the Theory and Application of Cryptology and Information Security. Berlin: Springer, 2009: 617-635.
|
| [14] |
PEIKERT C, ROSEN A. Efficient Collision-Resistant Hashing from Worstcase Assumptions on Cyclic Lattices[C]// IACR. Theory of Cryptography: Third Theory of Cryptography Conference. Berlin: Springer, 2006: 145-166.
|
| [15] |
AJTAI M. Generating Hard Instances of Lattice Problems[C]// ACM. STOC96:ACM Symposium on Theory of Computing. New York: ACM, 1996: 99-108.
|
| [16] |
AJTAI M. Generating Hard Instances of the Short Basis Problem[C]// EATCS. Automata, Languages and Programming:26th International Colloquium. Berlin: Springer, 1999: 1-9.
|
| [17] |
MICCIANCIO D, PEIKERT C. Trapdoors for Lattices: Simpler, Tighter, Faster, Smaller[C]// IACR. 31st Annual International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer, 2012: 700-718.
|
| [18] |
GENISE N, MICCIANCIO D. Faster Gaussian Sampling for Trapdoor Lattices with Arbitrary Modulus[C]// IACR. 37th Annual International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer, 2018: 174-203.
|
| [19] |
BERT P, FOUQUE P, ROUX-LANGLOS A, et al. Practical Implementation of Ring-SIS/LWE Based Signature and IBE[C]// Springer. Post-Quantum Cryptography 9th International Conference. Berlin: Springer, 2018: 271-291.
|
| [20] |
CARLOS A, BARRIER J, GUELTON S, et al. NFLlib: NTT-Based Fast Lattice Library[C]// Springer EMC Corporation. RSA Conference 2016. Berlin: Springer, 2016: 341-356.
|
| [21] |
YANG Yang, SUN Jianguo, LIU Zechao, et al. Practical Revocable and Multi-Authority CP-ABE Scheme from RLWE for Cloud Computing[J]. Journal of Information Security and Applications, 2022, 65(2): 1-12.
|
 ), WANG Zhangyi1
), WANG Zhangyi1