Netinfo Security ›› 2025, Vol. 25 ›› Issue (2): 240-248.doi: 10.3969/j.issn.1671-1122.2025.02.005
Previous Articles Next Articles
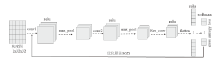
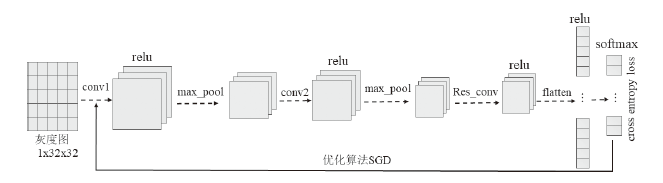
Research on Cyber Attack Detection Technology Based on Residual Convolutional Neural Network
ZHANG Shuangquan, YIN Zhonghao, ZHANG Huan, GAO Peng( )
)
- School of Cyber Science and Engineering, Nanjing University of Science and Technology, Nanjing 210094, China
-
Received:2024-11-28Online:2025-02-10Published:2025-03-07
CLC Number:
Cite this article
ZHANG Shuangquan, YIN Zhonghao, ZHANG Huan, GAO Peng. Research on Cyber Attack Detection Technology Based on Residual Convolutional Neural Network[J]. Netinfo Security, 2025, 25(2): 240-248.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.02.005
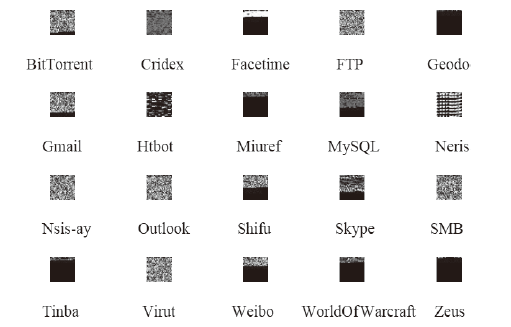
| 名称 | 所有数据个数/个 | 测试集/训练集 | 验证集 | 名称 | 所有数据个数/个 | 测试集/训练集 | 验证集 |
|---|---|---|---|---|---|---|---|
| Facetime | 5000 | 4500 | 500 | Tinba | 5000 | 4500 | 500 |
| Skype | 5000 | 4500 | 500 | Zeus | 5000 | 4500 | 500 |
| BitTorrent | 5000 | 4500 | 500 | Shifu | 5000 | 4500 | 500 |
| Gmail | 5000 | 4500 | 500 | Neris | 5000 | 4500 | 500 |
| Outlook | 5000 | 4500 | 500 | Cridex | 5000 | 4500 | 500 |
| WorldOf Warcraft | 5000 | 4500 | 500 | Nsis-ay | 5000 | 4500 | 500 |
| MySQL | 5000 | 4500 | 500 | Geodo | 5000 | 4500 | 500 |
| FTP | 5000 | 4500 | 500 | Miuref | 5000 | 4500 | 500 |
| SMB | 5000 | 4500 | 500 | Virut | 5000 | 4500 | 500 |
| 5000 | 4500 | 500 | Htbot | 5000 | 4500 | 500 | |
| 总计 | 50000 | 45000 | 5000 | 总计 | 50000 | 45000 | 5000 |
| 类别 | 召回率 | F1分数 |
|---|---|---|
| BitTorrent | 100% | 100% |
| Facetime | 100% | 100% |
| FTP | 99% | 98% |
| MySQL | 96% | 96% |
| Skype | 100% | 100% |
| SMB | 99% | 99% |
| 100% | 100% | |
| WorldOfWarcraf | 99% | 100% |
| Outlook | 100% | 99% |
| Gmail | 97% | 98% |
| Cridex | 91% | 95% |
| Geodo | 94% | 95% |
| Htbot | 99% | 98% |
| Miuref | 100% | 96% |
| Neris | 100% | 100% |
| Nsis-ay | 100% | 100% |
| Shifu | 100% | 100% |
| Tinba | 100% | 100% |
| Virut | 100% | 100% |
| Zeus | 100% | 100% |
| 类别 | 召回率 | F1分数 |
|---|---|---|
| BitTorrent | 100% | 100% |
| Facetime | 100% | 100% |
| FTP | 100% | 100% |
| MySQL | 100% | 100% |
| Skype | 100% | 100% |
| SMB | 99% | 100% |
| 100% | 100% | |
| WorldOfWarcraf | 100% | 100% |
| Outlook | 100% | 99% |
| Gmail | 99% | 100% |
| Cridex | 97% | 98% |
| Geodo | 100% | 100% |
| Htbot | 100% | 100% |
| Miuref | 98% | 98% |
| Neris | 94% | 94% |
| Nsis-ay | 98% | 98% |
| Shifu | 100% | 100% |
| Tinba | 99% | 100% |
| Virut | 95% | 95% |
| Zeus | 100% | 100% |
| [1] | HU Xiaoya. Research on Lightweight Secure Communication and Data Sharing Technology for Internet of Vehicles[D]. Beijing: Beijing University of Posts and Telecommunications, 2024. |
| 胡晓雅. 面向车联网的轻量级安全通信及数据共享技术研究[D]. 北京: 北京邮电大学, 2024. | |
| [2] | ZHAO Xin, HOU Kuo, WANG Hao, et al. Design and Implementation of an Enterprise Network Monitoring System Based on SNMP and Zabbix[J]. Computer Knowledge and Technology, 2023, 19(1): 91-94. |
| 赵鑫, 侯阔, 王昊, 等. 一个基于SNMP和Zabbix的企业网络监控系统的设计与实现[J]. 电脑知识与技术, 2023, 19(1):91-94. | |
| [3] | LIU Ping, CAO Yun. Research on Network Security[J]. Journal of Xiangnan University, 2010, 31(2): 84-86. |
| 刘平, 曹云. 入侵检测在网络安全中的地位与作用[J]. 湘南学院学报, 2010, 31(2):84-86. | |
| [4] | XU Jinyan. Deep Learning-Based Intrusion Detection for Class-Oriented Unbalanced Networks[D]. Nanchang: Jiangxi Normal University, 2023. |
| 许晋俨. 基于深度学习的面向类不均衡网络入侵检测研究[D]. 南昌: 江西师范大学, 2023. | |
| [5] |
GONG Siyue, LIU Hui, WANG Baohui. Malicious Encrypted Traffic Detection Method Based on Conversation Statistical Encoder Model[J]. Computer Science, 2024, 51(11): 340-346.
doi: 10.11896/jsjkx.231000121 |
|
巩思越, 刘辉, 王宝会. 基于会话统计编码器的恶意加密流量检测方法研究[J]. 计算机科学, 2024, 51(11):340-346.
doi: 10.11896/jsjkx.231000121 |
|
| [6] | SUN Zhenhao, ZHANG Diansheng, DONG Leilei, et al. Discussion on Foreign Body Detection around Airport Based on Convolutional Neural Network[J]. Information Recording Materials, 2024, 25(2): 217-219. |
| 孙振浩, 张殿生, 董嫘嫘, 等. 基于卷积神经网络的机场周界异物检测论述[J]. 信息记录材料, 2024, 25(2):217-219. | |
| [7] | LU Da, FENG Zhonghua. Research on Network Intrusion Detection Based on Convolutional Neural Network[J]. Communications Technology, 2024, 57(5): 529-536. |
| 卢达, 冯中华. 基于卷积神经网络的网络入侵检测技术研究[J]. 通信技术, 2024, 57(5):529-536. | |
| [8] | LIU Dongqi, ZHANG Qiong, LIANG Haolan, et al. Study on Smart Grid AMI Intrusion Detection Method Based on Federated Learning[J]. Computer Science, 2024, 51(S1): 944-951. |
| 刘东奇, 张琼, 梁皓澜, 等. 基于联邦学习的智能电网AMI入侵检测方法研究[J]. 计算机科学, 2024, 51(S1):944-951. | |
| [9] | WANG Xiangyue, ZHAO Lihui. Network Intrusion Detection Model Based on Multi-Stage Feature Selection and CNN-GRU[J]. Journal of North University of China (Natural Science Edition), 2024, 45(1): 66-73. |
| 王相月, 赵利辉. 基于多阶段特征选择和CNN-GRU的网络入侵检测模型[J]. 中北大学学报(自然科学版), 2024, 45(1):66-73. | |
| [10] | CHENG Bailiang, ZHOU Hongbo, ZHONG Linhui. Intrusion Detection System Based on Anomaly and Misuse[J]. Computer Engineering and Design, 2007, 28(14): 3341-3343. |
| 程柏良, 周洪波, 钟林辉. 基于异常与误用的入侵检测系统[J]. 计算机工程与设计, 2007, 28(14):3341-3343. | |
| [11] |
SHANG Yuling, LI Peng, ZHU Feng, et al. Overview of IoT Traffic Attack Detection Technology Based on Fuzzy Logic[J]. Computer Science, 2024, 51(3): 3-13.
doi: 10.11896/jsjkx.230700130 |
|
商钰玲, 李鹏, 朱枫, 等. 基于模糊逻辑的物联网流量攻击检测技术综述[J]. 计算机科学, 2024, 51(3):3-13.
doi: 10.11896/jsjkx.230700130 |
|
| [12] | JIAN Shijie, LU Zhigang, DU Dan, et al. Overview of Network Intrusion Detection Technology[J]. Journal of Cyber Security, 2020, 5(4): 96-122. |
| [13] | VAN G M, BOHTE S. Editorial: Artificial Neural Networks as Models of Neural Information Processing[EB/OL]. (2017-12-19)[2024-11-20]. https://doi.org/10.3389/fncom.2017.00114. |
| [14] | JIA Hanshuang, ZHANG Ka, YANG Suiming. Design of Abnormal Intrusion Detection System for Train Communication Network Based on Bidirectional AC Algorithm[J]. Computer Measurement & Control, 2024, 32(8): 14-19. |
| 贾寒霜, 张卡, 杨碎明. 基于双向AC算法的列车通信网络异常入侵检测系统设计[J]. 计算机测量与控制, 2024, 32(8):14-19. | |
| [15] | YANG Yongping, WANG Siting. Research on a Network Traffic Classification Algorithm Based on GRU and CNN[J]. Information & Computer, 2024, 36(6): 25-28. |
| 杨永平, 王思婷. 一种GRU结合CNN的网络流量分类算法研究[J]. 信息与电脑, 2024, 36(6):25-28. | |
| [16] | LIU Yufei. ConvLSTM-CNN Model Based on Mixed Balanced Sampling and Its Application in Network Security Situation Awareness[D]. Shanghai: East China Normal University, 2022. |
| 刘雨菲. 一种基于混合平衡采样的ConvLSTM-CNN模型及其在网络安全态势感知中的应用研究[D]. 上海: 华东师范大学, 2022. | |
| [17] | YANG Dongyang. Research on High-Speed Network Traffic Measurement Based on Deep Learning[D]. Suzhou: Soochow University, 2023. |
| 杨东阳. 基于深度学习的高速网络流量测量研究[D]. 苏州: 苏州大学, 2023. | |
| [18] | WANG Bo, SU Yang, ZHANG Mingshu, et al. A Deep Hierarchical Network for Packet-Level Malicious Traffic Detection[J]. IEEE Access, 2020, 8: 201728-201740. |
| [19] | SUN Fengxu, LI Aihua, SHENG Xia. Research on Encrypted Traffic Detection Technology Based on Fusion Attention Mechanism[C]// IEEE. 2024 2nd International Conference on Signal Processing and Intelligent Computing (SPIC). New York: IEEE, 2024: 158-161. |
| [20] |
WANG Yifeng, GUO Yuanbo, CHEN Qingli, et al. Method Based on Contrastive Learning for Fine-Grained Unknown Malicious Traffic Classification[J]. Journal on Communications, 2022, 43(10): 12-25.
doi: 10.11959/j.issn.1000-436x.2022180 |
|
王一丰, 郭渊博, 陈庆礼, 等. 基于对比学习的细粒度未知恶意流量分类方法[J]. 通信学报, 2022, 43(10):12-25.
doi: 10.11959/j.issn.1000-436x.2022180 |
|
| [21] |
GU Yue, LI Dan, GAO Kaihui. Research on Network Traffic Classification Based on Machine Learning and Deep Learning[J]. Telecommunications Science, 2021, 37(3): 105-113.
doi: 10.11959/j.issn.1000-0801.2021052 |
|
顾玥, 李丹, 高凯辉. 基于机器学习和深度学习的网络流量分类研究[J]. 电信科学, 2021, 37(3):105-113.
doi: 10.11959/j.issn.1000-0801.2021052 |
|
| [22] | YAN Jianwei, ZHAO Yuan, ZHANG Lewei, et al. Recognition of Rosa Roxbunghii in Natural Environment Based on Improved Faster RCNN[J]. Transactions of the Chinese Society of Agricultural Engineering, 2019, 35(18): 143-150. |
| 闫建伟, 赵源, 张乐伟, 等. 改进Faster-RCNN自然环境下识别刺梨果实[J]. 农业工程学报, 2019, 35(18):143-150. | |
| [23] | DONG Shuqin, ZHANG Bin. Network Traffic Anomaly Detection Method Based on Deep Features Learning[J]. Journal of Electronics & Information Technology, 2020, 42(3): 695-703. |
| 董书琴, 张斌. 基于深度特征学习的网络流量异常检测方法[J]. 电子与信息学报, 2020, 42(3):695-703. | |
| [24] | HWANG R, PENG M, NGUYEN V L, et al. An LSTM-Based Deep Learning Approach for Classifying Malicious Traffic at the Packet Level[J]. Applied Sciences, 2019, 9(16): 3414-3427. |
| [25] | HUANG Hong, ZHANG Xingxing, LU Ye, et al. BSTFNet: An Encrypted Malicious Traffic Classification Method Integrating Global Semantic and Spatiotemporal Features[J]. Computers, Materials & Continua, 2024, 78(3): 3929-3951. |
| [26] | WANG Wei, ZHU Ming, ZENG Xuewen, et al. Malware Traffic Classification Using Convolutional Neural Network for Representation Learning[C]// IEEE. 2017 International Conference on Information Networking (ICOIN). New York: IEEE, 2017: 712-717. |
| [27] | GARG S, KAUR K, KUMAR N, et al. Hybrid Deep-Learning-Based Anomaly Detection Scheme for Suspicious Flow Detection in SDN: A Social Multimedia Perspective[J]. IEEE Transactions on Multimedia, 2019, 21(3): 566-578. |
| [28] | GUO Shuai, LIU Yao, SU Yang. Network Traffic Anomaly Detection Method Based on CAE and LSTM[EB/OL]. (2021-09-01)[2024-11-20]. https://doi.org/10.1088/1742-6596%2F2025%2F1%2F012025. |
| [1] | GU Guomin, CHEN Wenhao, HUANG Weida. A Covert Tunnel and Encrypted Malicious Traffic Detection Method Based on Multi-Model Fusion [J]. Netinfo Security, 2024, 24(5): 694-708. |
| [2] | TU Xiaohan, ZHANG Chuanhao, LIU Mengran. Design and Implementation of Malicious Traffic Detection Model [J]. Netinfo Security, 2024, 24(4): 520-533. |
| [3] | XUE Yu, ZHANG Yixuan. Survey on Deep Neural Architecture Search [J]. Netinfo Security, 2023, 23(9): 58-74. |
| [4] | YUAN Wenxin, CHEN Xingshu, ZHU Yi, ZENG Xuemei. HTTP Payload Covert Channel Detection Method Based on Deep Learning [J]. Netinfo Security, 2023, 23(7): 53-63. |
| [5] | JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion [J]. Netinfo Security, 2023, 23(7): 86-97. |
| [6] | ZHAO Xiaolin, WANG Qiyao, ZHAO Bin, XUE Jingfeng. Research on Anonymous Traffic Classification Method Based on Machine Learning [J]. Netinfo Security, 2023, 23(5): 1-10. |
| [7] | ZHAO Caidan, CHEN Jingqian, WU Zhiqiang. Automatic Modulation Recognition Algorithm Based on Multi-Channel Joint Learning [J]. Netinfo Security, 2023, 23(4): 20-29. |
| [8] | QIN Yifang, ZHANG Jian, LIANG Chen. Research on Feature Extraction Technology of Electronic Medical Record Data Based on Neural Networks [J]. Netinfo Security, 2023, 23(10): 70-76. |
| [9] | LIU Guangjie, DUAN Kun, ZHAI Jiangtao, QIN Jiayu. Mobile Traffic Application Recognition Based on Multi-Feature Fusion [J]. Netinfo Security, 2022, 22(7): 18-26. |
| [10] | WANG Haoyang, LI Wei, PENG Siwei, QIN Yuanqing. An Intrusion Detection Method of Train Control System Based on Ensemble Learning [J]. Netinfo Security, 2022, 22(5): 46-53. |
| [11] | LIU Feng, YANG Chengyi, YU Xincheng, QI Jiayin. Spectral Graph Convolutional Neural Network for Decentralized Dual Differential Privacy [J]. Netinfo Security, 2022, 22(2): 39-46. |
| [12] | LIN Faxin, ZHANG Jian. Design and Implementation of Abnormal Behavior Detection System for Virtualization Platform [J]. Netinfo Security, 2022, 22(11): 62-67. |
| [13] | ZHANG Zhi, LI Xin, YE Naifu, HU Kaixi. CAPTCHA Security Enhancement Method Incorporating Multiple Style Migration and Adversarial Examples [J]. Netinfo Security, 2022, 22(10): 129-135. |
| [14] | GAO Changfeng, XIAO Yanhui, TIAN Huawei. Image Camera Fingerprint Extraction Algorithm Based on MPRNet [J]. Netinfo Security, 2022, 22(10): 15-23. |
| [15] | LIU Jiayin, LI Fujuan, MA Zhuo, XIA Lingling. Malware Classification Method Based on Multi-Scale Convolutional Neural Network [J]. Netinfo Security, 2022, 22(10): 31-38. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||