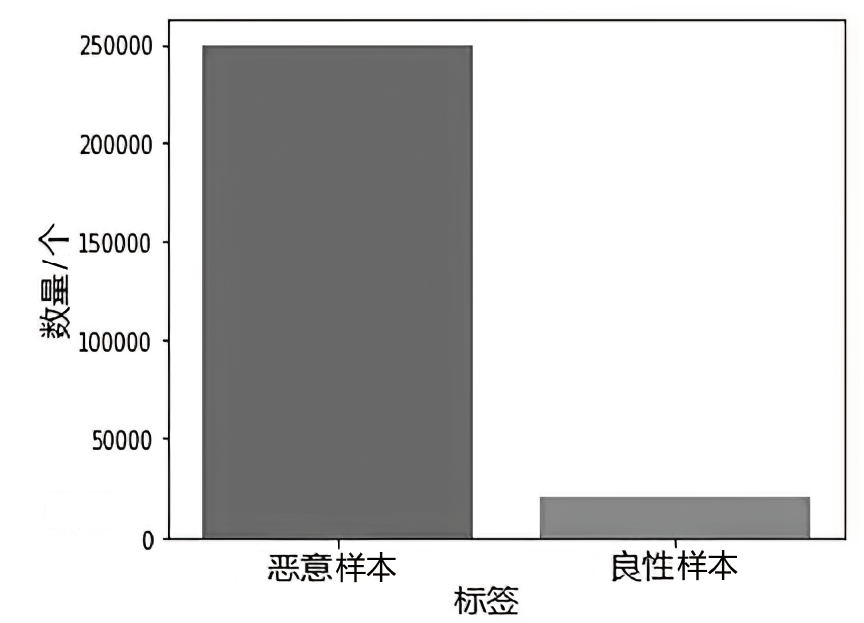
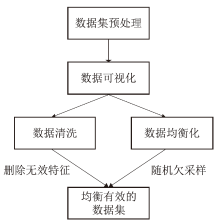
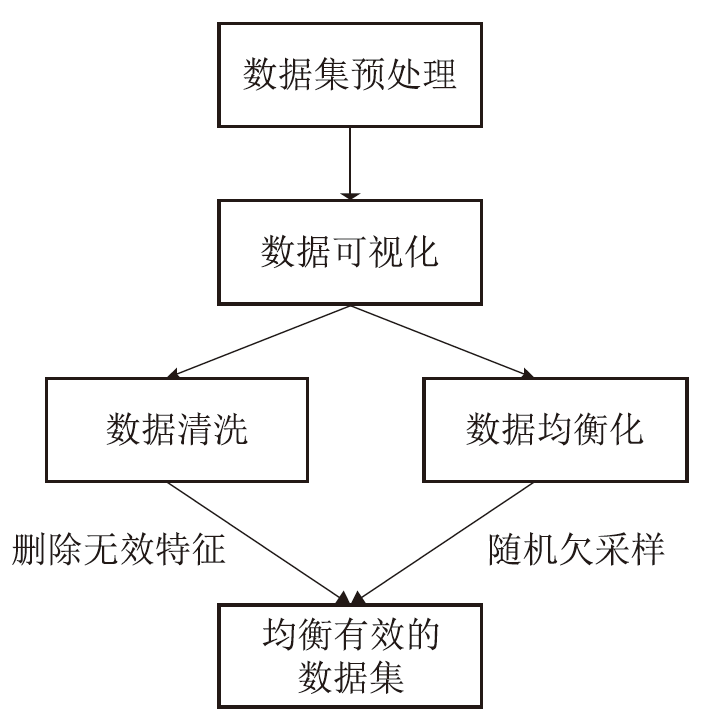
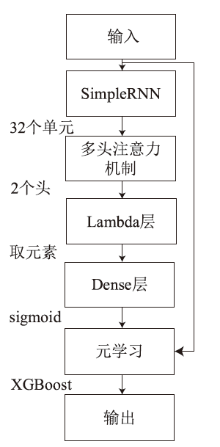
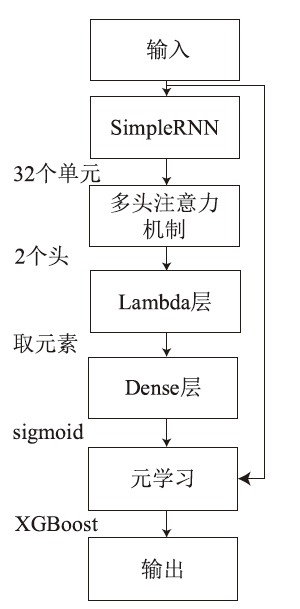
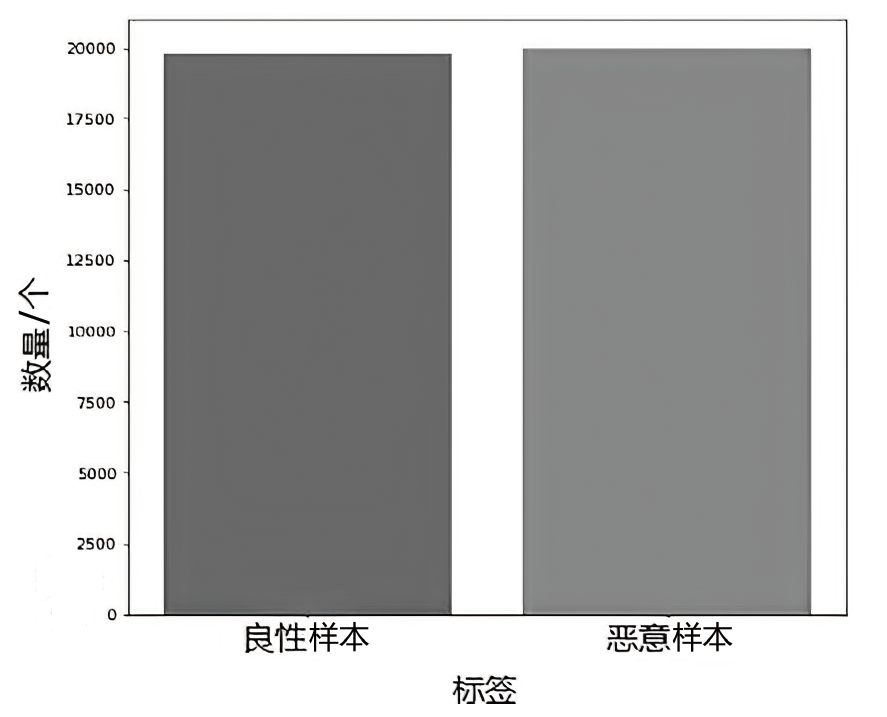
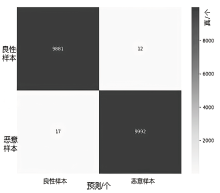
Netinfo Security ›› 2024, Vol. 24 ›› Issue (4): 520-533.doi: 10.3969/j.issn.1671-1122.2024.04.003
Previous Articles Next Articles
Design and Implementation of Malicious Traffic Detection Model
TU Xiaohan1, ZHANG Chuanhao1( ), LIU Mengran2
), LIU Mengran2
- 1. Department of Cybersecurity and Smart Police, Zhengzhou Police University, Zhengzhou 450053, China
2. Tianjin Public Security Division, Beijing Railway Public Security Bureau, Tianjin 300100, China
-
Received:2023-12-07Online:2024-04-10Published:2024-05-16
CLC Number:
Cite this article
TU Xiaohan, ZHANG Chuanhao, LIU Mengran. Design and Implementation of Malicious Traffic Detection Model[J]. Netinfo Security, 2024, 24(4): 520-533.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.04.003
| [1] | MONTAZERISHATOORI M, DAVIDSON L, KAUR G, et al. Detection of DoH Tunnels Using Time-Series Classification of Encrypted Traffic[C]// IEEE. 2020 IEEE Intl Conf on Dependable, Autonomic and Secure Computing, Intl Conf on Pervasive Intelligence and Computing, Intl Conf on Cloud and Big Data Computing, Intl Conf on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech). NewYork: IEEE, 2020: 63-70. |
| [2] | MITSUHASHI R, JIN Yong, IIDA K, et al. Malicious DNS Tunnel Tool Recognition Using Persistent DoH Traffic Analysis[J]. IEEE Transactions on Network and Service Management, 2022, 20(2): 2086-2095. |
| [3] | TU Xiaohan, XU Cheng, LIU Siping, et al. Efficient Monocular Depth Estimation for Edge Devices in Internet of Things[J]. IEEE Transactions on Industrial Informatics, 2021, 17(4): 2821-2832. |
| [4] | LIN Kunda, XU Xiaolong, XIAO Fu. MFFusion: A Multi-Level Features Fusion Model for Malicious Traffic Detection Based on Deep Learning[J]. Computer Networks, 2022, 202: 108658-108667. |
| [5] | HONG Yueping, LI Qi, YANG Yanqing, et al. Graph Based Encrypted Malicious Traffic Detection with Hybrid Analysis of Multi-View Features[J]. Information Sciences, 2023, 185: 119229-119236. |
| [6] | TU Xiaohan, ZHANG Chuanhao, LIU Siping, et al. Point Cloud Segmentation of Overhead Contact Systems with Deep Learning in High-Speed Rails[J]. Journal of Network and Computer Applications, 2023, 23: 103671-103688. |
| [7] | ZHANG Pei, HE Fangzhou, ZHANG Han, et al. Real-Time Malicious Traffic Detection with Online Isolation Forest over SD-WAN[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 2076-2090. |
| [8] | KISHOR K, SINGH P, VASHISHTA R. Develop Model for Malicious Traffic Detection Using Deep Learning[J]. Micro-Electronics and Telecommunication Engineering: Proceedings of 6th ICMETE 2022. Singapore: Springer Nature Singapore, 2023: 83-91. |
| [9] | SHIN D H, AN K K, CHOI S C, et al. Malicious Traffic Detection Using K-Means[J]. The Journal of Korean Institute of Communications and Information Sciences, 2016, 41(2): 277-284. |
| [10] | NAEEM H, CHENG Xiaochun, ULLAH F, et al. A Deep Convolutional Neural Network Stacked Ensemble for Malware Threat Classification in Internet of Things[EB/OL]. (2022-07-18)[2023-11-25]. https://www.worldscientific.com/doi/10.1142/S0218126622503029. |
| [11] | NAEEM H, DONG Shi, FALANA O J, et al. DEVELOPMENT of a Deep Stacked Ensemble with Process Based Volatile Memory Forensics for Platform Independent Malware Detection and Classification[EB/OL]. (2023-08-18)[2023-11-25]. https://www.nstl.gov.cn/paper_detail.html?id=d829128c2b7c4b8caca5389d2553aba7. |
| [12] | SHU Longhui, DONG Shi, SU Huadong, et al. Android Malware Detection Methods Based on Convolutional Neural Network: A Survey[J]. IEEE Transactions on Emerging Topics in Computational Intelligence, 2023, 7(5): 1330-1350. |
| [13] |
LUO Yantian, SUN Hancun, CHEN Xu, et al. Detecting While Accessing: A Semi-Supervised Learning-Based Approach for Malicious Traffic Detection in Internet of Things[J]. China Communications, 2023, 20(4): 302-314.
doi: 10.23919/JCC.fa.2022-0783.202304 |
| [14] | LU Gang, GUO Ronghua, ZHOU Ying, et al. Review of Malicious Traffic Feature Extraction[J]. Netinfo Security, 2018, 18(9): 9-22. |
| 鲁刚, 郭荣华, 周颖, 等. 恶意流量特征提取综述[J]. 信息网络安全, 2018, 18(9): 9-22. | |
| [15] | ZOU Futai, YU Tangda, XU Wenliang. Encrypted Malicious Traffic Detection Based on Hidden Markov Mode[J]. Journal of Software, 2022, 33(7): 2683-2698. |
| 邹福泰, 俞汤达, 许文亮. 基于隐马尔可夫模型的加密恶意流量检测[J]. 软件学报, 2022, 33(7): 2683-2698. | |
| [16] |
LI Daoquan, LU Xiaofu, YANG Qianqian. Malicious Traffic Detection Method Based on Siamese Neural Network[J]. Computer Engineering and Applications, 2022, 58(14): 89-95.
doi: 10.3778/j.issn.1002-8331.2104-0159 |
|
李道全, 鲁晓夫, 杨乾乾. 基于孪生神经网络的恶意流量检测方法[J]. 计算机工程与应用, 2022, 58(14): 89-95.
doi: 10.3778/j.issn.1002-8331.2104-0159 |
|
| [17] | LI Hongwu, FU Xingyu, ZHU Yujia, et al. MetaIoT: Few Shot Malicious Traffic Detection in Internet of Things Networks Based on HIN[C]// IEEE. 2023 IFIP Networking Conference (IFIP Networking). New York: IEEE, 2023: 1-9. |
| [18] | HONG Jiarong, DING Mingfeng. A New Algorithm of Decision Tree Induction[J]. Chinese Journal of Computers, 1995, 18(6): 470-474. |
| 洪家荣, 丁明峰. 一种新的决策树归纳学习算法[J]. 计算机学报, 1995, 18(6): 470-474. | |
| [19] | HOU Jian, LU Hui, LIU Fangai, et al. Detection and Countermeasure of Encrypted Malicious Traffic: A Survey[J]. Journal of Software, 2024, 35(1): 333-355. |
| 侯剑, 鲁辉, 刘方爱, 等. 加密恶意流量检测及对抗综述[J]. 软件学报, 2024, 35(1): 333-355. | |
| [20] | ZHOU Chang. Research on Mining Algorithm for Web Threat Intelligence Based on Deep Learning[D]. Shanghai: Shanghai Jiao Tong University, 2018. |
| 周畅. 基于深度学习的Web威胁情报挖掘算法研究[D]. 上海: 上海交通大学, 2018. | |
| [21] | LI Zeyi, WANG Pan. Unsupervised Network Abnormal Traffie Detection Method Based on Improved KNN[J]. Journal of Nanjing University of Posts and Telecommunications (Natural Science Edition), 2022, 42(2): 560-568. |
| 李泽一, 王攀. 基于代价敏感度的改进型K近邻异常流量检测算法[J]. 南京邮电大学学报(自然科学版), 2022, 42(2): 560-568. | |
| [22] | BAO Wenbo, SHA Letian, CAO Xiaomei. Malicious Encrypted Traffic Identification Based on Feature Fusion[J]. Computer Systems and Applications, 2023, 32(1): 358-367. |
| 包文博, 沙乐天, 曹晓梅. 基于特征融合的恶意加密流量识别[J]. 计算机系统应用, 2023, 32(1): 358-367. | |
| [23] | GAO Yuanchen, XU Guosheng. Research on Network Malicious Traffic Detection Technology Based on Ensemble Learning Strategy[J]. Journal of Information Security Research, 2023, 9(8): 730-738. |
| 高源辰, 徐国胜. 基于集成学习策略的网络恶意流量检测技术研究[J]. 信息安全研究, 2023, 9(8): 730-738. | |
| [24] | TU Xiaohan, XU Cheng, LIU Siping, et al. Learning Depth for Scene Reconstruction Using an Encoder-Decoder Model[J]. IEEE Access, 2020, 99: 1-11. |
| [25] | FATIMA R A, ABID M. A Review of Recent Advances, Challenges, and Opportunities in Malicious Insider Threat Detection Using Machine Learning Methods[J]. IEEE Access, 2024, 12: 30907-30927. |
| [26] | SHERSTINSKY A. Fundamentals of Recurrent Neural Network (RNN) and Long Short-Term Memory (LSTM) Network[J]. Physica D: Nonlinear Phenomena, 2020, 404(1): 1323-1329. |
| [27] | LIN Zhouhan, FENG Minwei, SANTOS C N, et al. A Structured Self-Attentive Sentence Embedding[EB/OL]. (2017-05-09)[2023-11-15]. https://doi.org/10.48550/arXiv.1703.03130. |
| [28] | LUO Gongzhi, HOU Ruoxian, CHEN Shengyu. Malicious DoH Traffic Warning of Extreme Learning Machine Based on Neighborhood Rough Sets[J]. Nanjing University of Posts and Telecommunications (Natural Science Edition). 2022, 42(6): 79-85. |
| 骆公志, 侯若娴, 陈圣瑜. 基于邻域粗糙集的极限学习机恶意DoH流量预警[J]. 南京邮电大学学报(自然科学版), 2022, 42(6): 79-85. | |
| [29] | CHEN Tianqi, HE Tong, BENESTY M, et al. XGBoost: eXtreme Gradient Boosting[J]. R Package Version, 2015, 1(4): 1-4. |
| [30] | ULLAH I, MAHMOUD Q H. Design and Development of RNN Anomaly Detection Model for IoT Networks[J]. IEEE Access, 2022, 10: 62722-62750. |
| [31] | ANITHA T, AANJANKUMAR S, POONKUNTRAN S, et al. A Novel Methodology for Malicious Traffic Detection in Smart Devices Using Bi-LSTM-CNN-Dependent Deep Learning Methodology[J]. Neural Computing and Applications, 2023, 35(27): 20319-20338. |
| [1] | JIANG Rong, LIU Haitian, LIU Cong. Unsupervised Network Intrusion Detection Method Based on Ensemble Learning [J]. Netinfo Security, 2024, 24(3): 411-426. |
| [2] | ZHANG Yuchen, ZHANG Yawen, WU Yue, LI Cheng. A Method of Feature Extraction for Network Traffic Based on Time-Frequency Diagrams and Improved E-GraphSAGE [J]. Netinfo Security, 2023, 23(9): 12-24. |
| [3] | ZHAO Xiaolin, WANG Qiyao, ZHAO Bin, XUE Jingfeng. Research on Anonymous Traffic Classification Method Based on Machine Learning [J]. Netinfo Security, 2023, 23(5): 1-10. |
| [4] | XING Lingkai, ZHANG Jian. Research and Implementation on Abnormal Behavior Detection Technology of Virtualization Platform Based on HPC [J]. Netinfo Security, 2023, 23(10): 64-69. |
| [5] | QIN Yifang, ZHANG Jian, LIANG Chen. Research on Feature Extraction Technology of Electronic Medical Record Data Based on Neural Networks [J]. Netinfo Security, 2023, 23(10): 70-76. |
| [6] | ZHAO Xinhe, XIE Yongheng, WAN Yueliang, WANG Jinmiao. Detection and Identification Model of Gambling Websites Based on Multi-Modal Data [J]. Netinfo Security, 2023, 23(10): 77-82. |
| [7] | FAN Mingyu, LI Ke. A Method to Distinguish DDoS Attack Types Based on RNN [J]. Netinfo Security, 2022, 22(7): 1-8. |
| [8] | WANG Haoyang, LI Wei, PENG Siwei, QIN Yuanqing. An Intrusion Detection Method of Train Control System Based on Ensemble Learning [J]. Netinfo Security, 2022, 22(5): 46-53. |
| [9] | Jian KANG, Jie WANG, Zhengxu LI, Guangda ZHANG. A Model for Anomaly Intrusion Detection with Different Feature Extraction Strategies in IoT [J]. Netinfo Security, 2019, 19(9): 21-25. |
| [10] | Zewen MA, Yang LIU, Hongping XU, Hang YI. DoS Traffic Identification Technology Based on Integrated Learning [J]. Netinfo Security, 2019, 19(9): 115-119. |
| [11] | Hui LI, Shice NI, Jia XIAO, Tianzhong ZHAO. Emotion Classification Technology for Online Video Comments on the Internet [J]. Netinfo Security, 2019, 19(5): 61-68. |
| [12] | Xudong WANG, Xiangzhan YU, Hongli ZHANG. Research on Traffic Identification Technology for Unknown Protocols [J]. Netinfo Security, 2019, 19(10): 74-83. |
| [13] | Weiping WEN, Jingwei LI, Yingnan JIAO, Hailin LI. A Vulnerability Detection Method Based on Random Detection Algorithm and Information Aggregation [J]. Netinfo Security, 2019, 19(1): 1-7. |
| [14] | Gang LU, Ronghua GUO, Ying ZHOU, Jun WANG. Review of Malicious Traffic Feature Extraction [J]. Netinfo Security, 2018, 18(9): 1-9. |
| [15] | Chenxi MA, Xingshu CHEN, Wenxian WANG, Haizhou WANG. Chinese Event Detection Based on Recurrent Neural Network [J]. Netinfo Security, 2018, 18(5): 75-81. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||