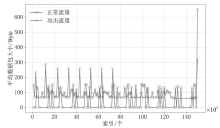
Netinfo Security ›› 2024, Vol. 24 ›› Issue (4): 509-519.doi: 10.3969/j.issn.1671-1122.2024.04.002
Previous Articles Next Articles
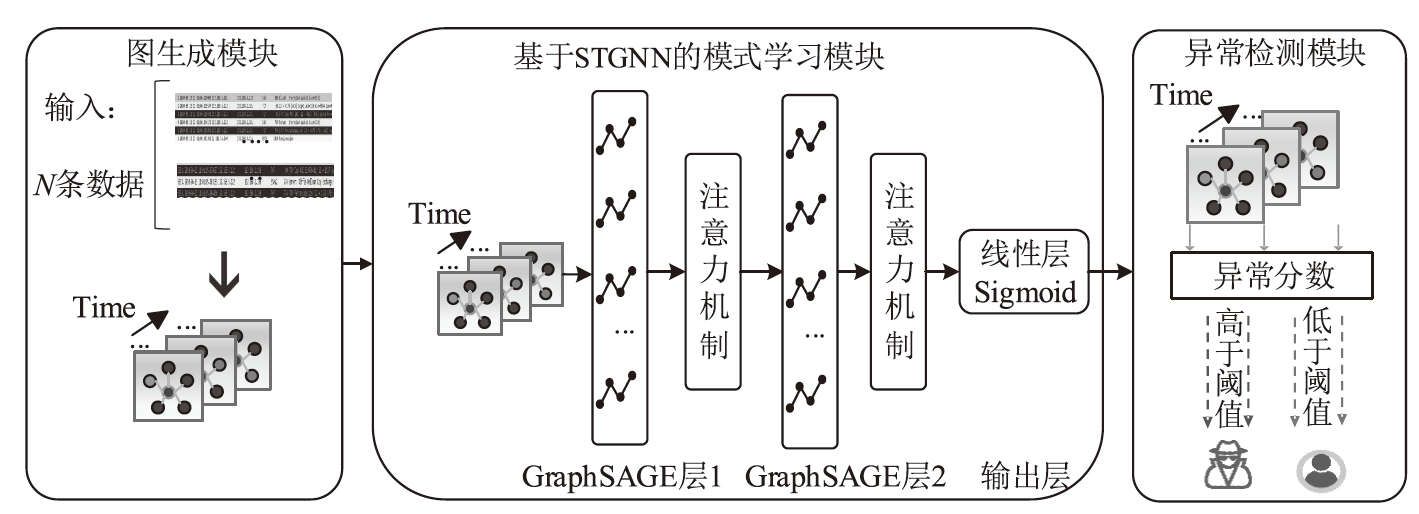
Application Layer DDoS Detection Method Based on Spatio-Temporal Graph Neural Network
WANG Jian( ), CHEN Lin, WANG Kailun, LIU Jiqiang
), CHEN Lin, WANG Kailun, LIU Jiqiang
- Beijing Key Laboratory of Security and Privacy in Intelligent Transportation, Beijing Jiaotong University, Beijing 100044, China
-
Received:2024-02-25Online:2024-04-10Published:2024-05-16
CLC Number:
Cite this article
WANG Jian, CHEN Lin, WANG Kailun, LIU Jiqiang. Application Layer DDoS Detection Method Based on Spatio-Temporal Graph Neural Network[J]. Netinfo Security, 2024, 24(4): 509-519.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.04.002
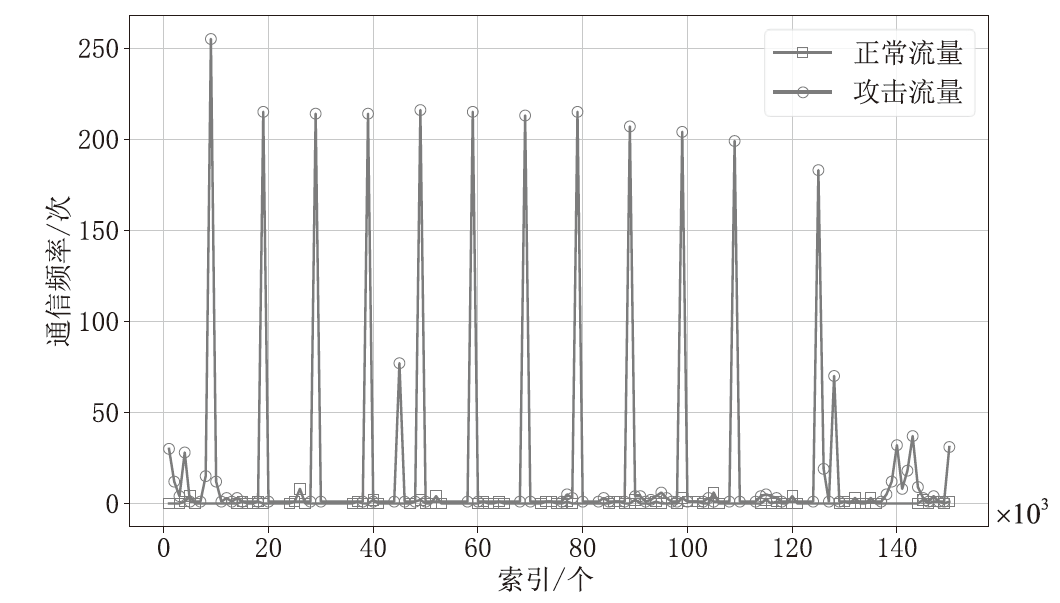
| DDoS攻击类型 | 被攻击IP | 攻击起始时间偏移 | 攻击持续时间 |
|---|---|---|---|
| slowbody2 | 75.127.97.72 | 53分钟 | 11:54:06~12:08:00 |
| slowread | 75.127.97.72 | 1小时58 分钟 | 12:59:06~13:05:50 |
| ddossim | 75.127.97.72 | 2小时22分钟 | 13:23:06~13:25:13 |
| goldeneye | 75.127.97.72 | 2小时50分钟 | 13:51:23~13:55:13 |
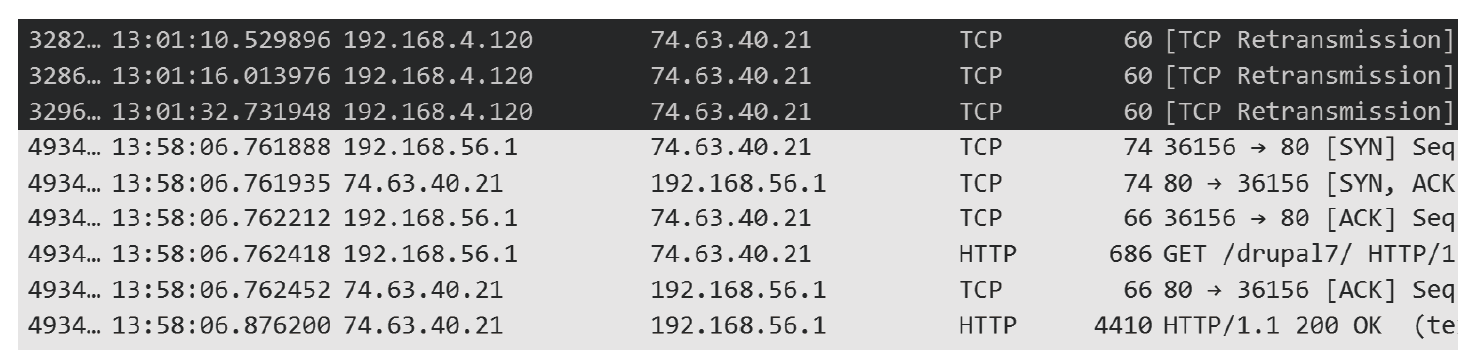
| slowheaders | 74.63.40.21 | 2小时57分钟 | 13:58:06~14:07:42 |
| rudy | 75.127.97.72 | 3小时8分钟 | 14:09:06~14:10:11 |
| ddossim | 97.74.144.108 | 3小时28分钟 | 14:29:06~14:32:15 |
| rudy | 208.113.162.153 | 3小时29分钟 | 14:30:06~14:31:11 |
| hulk | 69.84.133.138 | 4小时38分钟 | 15:39:06~15:44:25 |
| slowheaders | 67.220.214.50 | 6小时 | 17:01:06~17:10:42 |
| goldeneye | 97.74.144.108 | 7小时6分钟 | 18:07:23~18:11:13 |
| slowbody2 | 69.192.24.88 | 8小时13分钟 | 19:14:06~19:28:00 |
| slowbody2 | 97.74.144.108 | 9小时3分钟 | 20:04:06~20:18:00 |
| slowbody2 | 203.73.24.75 | 9小时9分钟 | 20:10:06~20:24:02 |
| rudy | 97.74.144.108 | 9小时20分钟 | 20:21:06~20:22:11 |
| slowread | 74.55.1.4 | 11小时2分钟 | 22:03:06~22:09:50 |
| slowheaders | 97.74.104.201 | 11小时27分钟 | 22:28:06~22:37:42 |
| hulk | 74.55.1.4 | 13小时33分钟 | 24:34:06~24:44:14 |
| hulk | 69.192.24.88 | 13小时47分钟 | 24:48:06~24:56:37 |
| slowloris | 97.74.144.108 | 15小时20分钟 | 次日2:21:06~2:23:36 |
| slowheaders | 97.74.144.108 | 15小时47分钟 | 次日2:48:06~2:57:42 |
| slowloris | 75.127.97.72 | 16小时33分钟 | 次日3:34:06~3:36:36 |
| slowheaders | 75.127.97.72 | 17小时13分钟 | 次日4:14:06~4:23:42 |
| goldeneye | 69.192.24.88 | 19小时23分钟 | 次日6:24:23~6:28:13 |
| hulk | 75.127.97.72 | 19小时25分钟 | 次日6:26:06~6:31:25 |
| rudy | 74.55.1.4 | 20小时59分钟 | 次日8:00:06~8:01:11 |
| [1] | JANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion[J]. Netinfo Security, 2023, 23(7): 86-97. |
| 蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7):86-97. | |
| [2] | China Unicom Digital Science & Technology. Global DDoS Attack Threat Report 2023[EB/OL]. (2024-01-04)[2024-01-29]. https://www.199it.com/archives/1669730.html. |
| 联通数科. 2023年全球DDoS攻击威胁报告[EB/OL]. (2024-01-04) [2024-01-29]. https://www.199it.com/archives/1669730.html. | |
| [3] | FAN Mingyu, LI Ke. A Method to Distinguish DDoS Attack Types Based on RNN[J]. Netinfo Security, 2022, 22(7): 1-8. |
| 范明钰, 李珂. 一种基于RNN区分DDoS 攻击类型的方法[J]. 信息网络安全, 2022, 22(7):1-8. | |
| [4] | StormWall. Q1 2023 in Review: DDoS Attacks Report by Storm-Wall[EB/OL]. (2023-04-17)[2024-01-29]. https://stormwall.network/ddos-report-stormwall-q-1-2023. |
| [5] | MITTAL M, KUMAR K, BEHAL S. Deep Learning Approaches for Detecting DDoS Attacks: A Systematic Review[J]. Soft Computing, 2023, 27(18): 13039-13075. |
| [6] | DORIGUZZI-CORIN R, SIRACUSA D. FLAD: Adaptive Federated Learning for DDoS Attack Detection[EB/OL]. (2022-05-13)[2024-01-20]. https://arxiv.org/abs/2205.06661. |
| [7] | WANG Zhi, ZHANG Hao, GU Jianjun. A Hybrid Method of Joint Entropy and Multiple Clustering Based DDoS Detection in SDN[J]. Netinfo Security, 2023, 23(10): 1-7. |
| 王智, 张浩, 顾建军. SDN网络中基于联合熵与多重聚类的DDoS攻击检测[J]. 信息网络安全, 2023, 23(10):1-7. | |
| [8] | KEMP C, CALVERT C, KHOSHGOFTAAR T M, et al. An Approach to Application-Layer DoS Detection[EB/OL]. (2023-02-13)[2024-01-20]. https://journalofbigdata.springeropen.com/articles/10.1186/s40537-023-00699-3. |
| [9] | JIANG Jianguo, YU Qian, YU Min, et al. ALDD: A Hybrid Traffic-User Behavior Detection Method for Application Layer DDoS[C]// IEEE. 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering. New York: IEEE, 2018: 1565-1569. |
| [10] | SINGH K J, DE T. MLP-GA Based Algorithm to Detect Application Layer DDoS Attack[J]. Journal of Information Security and Applications, 2017, 36: 145-153. |
| [11] | ZHOU Lu, SOOD K, XIANG Yong. ERM: An Accurate Approach to Detect DDoS Attacks Using Entropy Rate Measurement[J]. IEEE Communications Letters, 2019, 23(10): 1700-1703. |
| [12] | XIE Yi, YU Shunzheng. A Large-Scale Hidden Semi-Markov Model for Anomaly Detection on User Browsing Behaviors[J]. IEEE/ACM Transactions on Networking, 2008, 17(1): 54-65. |
| [13] | PRASEED A, THILAGAM P S. Modelling Behavioural Dynamics for Asymmetric Application Layer DDoS Detection[J]. IEEE Transactions on Information Forensics and Security, 2020, 16: 617-626. |
| [14] | SARAVANAN A, BAMA S S, KADRY S, et al. A New Framework to Alleviate DDoS Vulnerabilities in Cloud Computing[J]. International Journal of Electrical & Computer Engineering, 2019, 9(5): 4163-4175. |
| [15] | GULIHAR P, GUPTA B B. Cooperative Mechanisms for Defending Distributed Denial of Service(DDoS) Attacks[EB/OL]. (2020-01-01)[2024-01-29]. https://link.springer.com/chapter/10.1007/978-3-030-22277-2_16. |
| [16] | SAKHARE S R, PATIL V D. Implementation of Captcha Mechanisms Using Deep Learning to Prevent Automated Bot Attacks[J]. Research Journal of Computer Systems and Engineering, 2023, 4(2): 1-15. |
| [17] | BHUYAN M H, BHATTACHARYYA D K, KALITA J K. An Empirical Evaluation of Information Metrics for Low-Rate and High-Rate DDoS Attack Detection[J]. Pattern Recognition Letters, 2015, 51: 1-7. |
| [18] | FORTUNATI S, GINI F, GRECO M S, et al. An Improvement of the State-of-the-Art Covariance-Based Methods for Statistical Anomaly Detection Algorithms[J]. Signal, Image and Video Processing, 2016, 10: 687-694. |
| [19] | DORIGUZZI-CORIN R, MILLAR S, SCOTT-HAYWARD S, et al. LUCID: A Practical, Lightweight Deep Learning Solution for DDoS Attack Detection[J]. IEEE Transactions on Network and Service Management, 2020, 17(2): 876-889. |
| [20] | LIU Xinqian, REN Jiadong, HE Haitao, et al. A Fast All-Packets-Based DDoS Attack Detection Approach Based on Network Graph and Graph Kernel[EB/OL]. (2021-07-01)[2024-01-20]. https://www.sciencedirect.com/science/article/pii/S1084804521001016. |
| [21] | KIPF T N, WELLING M. Semi-Supervised Classification with Graph Convolutional Networks[EB/OL]. (2016-09-09)[2024-01-25]. https://www.semanticscholar.org/paper/Semi-Supervised-Classification-with-Graph-Networks-Kipf-Welling/36eff562f65125511b5dfab68ce7f7a943c27478. |
| [22] | HAMILTON W, YING Zhitao, LESKOVEC J. Inductive Representation Learning on Large Graphs[J]. Advances in Neural Information Processing Systems, 2017, 30: 1025-1035. |
| [23] | VELIČKOVIĆ P, CUCURULL G, CASANOVA A, et al. Graph Attention Networks[EB/OL]. (2017-10-30)[2024-01-25]. https://arxiv.org/abs/1710.10903. |
| [24] | YU Bing, YIN Haoteng, ZHU Zhanxing. Spatio-Temporal Graph Convolutional Networks: A Deep Learning Framework for Traffic Forecasting[C]// ACM. The 27th International Joint Conference on Artificial Intelligence. New York: ACM, 2018: 3634-3640. |
| [25] | HE Xiangnan, DENG Kuan, WANG Xiang, et al. LightGCN: Simplifying and Powering Graph Convolution Network for Recommendation[C]// ACM. 43rd International ACM SIGIR Conference on Research and Development in Information Retrieval. New York: ACM, 2020: 639-648. |
| [26] | SHI Chence, XU Minkai, GUO Hongyu, et al. A Graph to Graphs Framework for Retrosynthesis Prediction[C]// ACM. 37th International Conference on Machine Learning. New York: ACM, 2020: 8818-8827. |
| [27] | LIN Honggang, ZHANG Yunli, GUO Nanxin, et al. P2P Botnet Detection Method Based on Graph Neural Network[J]. Advanced Engineering Sciences, 2022, 54(2): 65-72. |
| 林宏刚, 张运理, 郭楠馨, 等. 基于图神经网络的P2P僵尸网络检测方法[J]. 工程科学与技术, 2022, 54(2):65-72. | |
| [28] | XIE Qian, HUANG Zheng, GUO Jie, et al. Spatio-Temporal Graph Convolutional Networks for DDoS Attack Detecting[C]//ACM. Machine Learning for Cyber Security:Third International Conference. New York: ACM, 2020: 153-159. |
| [29] | JAZI H H, GONZALEZ H, STAKHANOVA N, et al. Detecting HTTP-Based Application Layer DoS Attacks on Web Servers in the Presence of Sampling[J]. Computer Networks, 2017, 121: 25-36. |
| [30] | PÉREZ-DÍAZ J A, VALDOVINOS I A, CHOO K K R, et al. A Flexible SDN-Based Architecture for Identifying and Mitigating Low-Rate DDoS Attacks Using Machine Learning[J]. IEEE Access, 2020, 8: 155859-155872. |
| [31] | LIMA FILHO F S, SILVEIRA F A F, de MEDEIROS BRITO JUNIOR A, et al. Smart Detection: An Online Approach for DoS/DDoS Attack Detection Using Machine Learning[EB/OL]. (2019-10-13)[2024-02-11]. https://doi.org/10.1155/2019/1574749. |
| [32] | BAKAR R A, HUANG Xin, JAVED M S, et al. An Intelligent Agent-Based Detection System for DDoS Attacks Using Automatic Feature Extraction and Selection[EB/OL]. (2023-03-22)[2024-01-30]. https://www.mdpi.com/1424-8220/23/6/3333. |
| [1] | ZHANG Hao, XIE Dazhi, HU Yunsheng, YE Junwei. A Review of Network Anomaly Detection Based on Semi-Supervised Learning [J]. Netinfo Security, 2024, 24(4): 491-508. |
| [2] | YANG Zhipeng, LIU Daidong, YUAN Junyi, WEI Songjie. Research on Network Local Security Situation Fusion Method Based on Self-Attention Mechanism [J]. Netinfo Security, 2024, 24(3): 398-410. |
| [3] | JIANG Rong, LIU Haitian, LIU Cong. Unsupervised Network Intrusion Detection Method Based on Ensemble Learning [J]. Netinfo Security, 2024, 24(3): 411-426. |
| [4] | JIANG Kui, LU Lufan, SU Yaoyang, NIE Wei. SHDoS Attack Detection Research Based on Attention-GRU [J]. Netinfo Security, 2024, 24(3): 427-437. |
| [5] | ZHANG Xinyou, SUN Feng, FENG Li, XING Huanlai. Multi-View Representations for Fake News Detection [J]. Netinfo Security, 2024, 24(3): 438-448. |
| [6] | SUN Hongzhe, WANG Jian, WANG Peng, AN Yulong. Network Intrusion Detection Method Based on Attention-BiTCN [J]. Netinfo Security, 2024, 24(2): 309-318. |
| [7] | SONG Yuhan, ZHU Yuefei, WEI Fushan. An Anomaly Detection Scheme for Blockchain Transactions Based on AdaBoost Model [J]. Netinfo Security, 2024, 24(1): 24-35. |
| [8] | QIN Zhongyuan, MA Nan, YU Yacong, CHEN Liquan. Network Anomaly Detection Based on Dual Graph Convolutional Network and Autoencoders [J]. Netinfo Security, 2023, 23(9): 1-11. |
| [9] | LIU Gang, YANG Wenli, WANG Tongli, LI Yang. Differential Privacy-Preserving Dynamic Recommendation Model Based on Cloud Federation [J]. Netinfo Security, 2023, 23(7): 31-43. |
| [10] | JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion [J]. Netinfo Security, 2023, 23(7): 86-97. |
| [11] | WU Shenglin, LIU Wanggen, YAN Ming, WU Jie. A Real-Time Anomaly Detection System for Container Clouds Based on Unsupervised System Call Rule Generation [J]. Netinfo Security, 2023, 23(12): 91-102. |
| [12] | LIAO Liyun, ZHANG Bolei, WU Lifa. IoT Anomaly Detection Model Based on Cost-Sensitive Learning [J]. Netinfo Security, 2023, 23(11): 94-103. |
| [13] | ZHANG Yuchen, LI Lianghui, MA Chenyang, ZHOU Hongwei. A Log Anomaly Detection Method with Variables [J]. Netinfo Security, 2023, 23(10): 16-20. |
| [14] | LI Jiyu, FU Zhangjie, ZHANG Yubin. An Image Information Hiding Algorithm Based on Cross-Domain Adversarial Adaptation [J]. Netinfo Security, 2023, 23(1): 93-102. |
| [15] | ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism [J]. Netinfo Security, 2022, 22(9): 46-54. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||