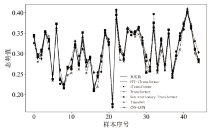
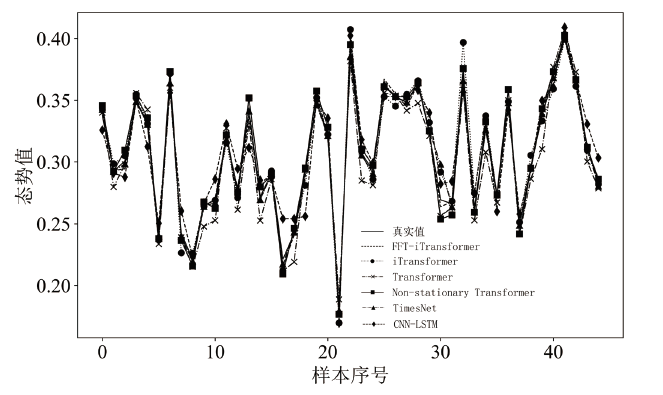
Netinfo Security ›› 2025, Vol. 25 ›› Issue (2): 228-239.doi: 10.3969/j.issn.1671-1122.2025.02.004
Previous Articles Next Articles
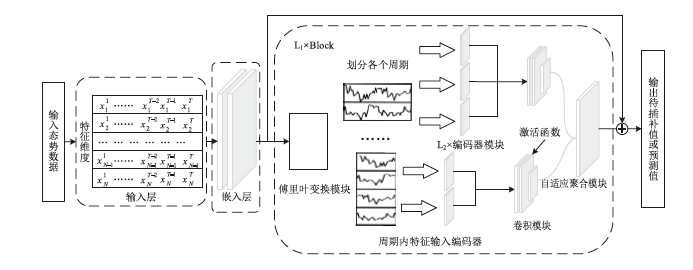
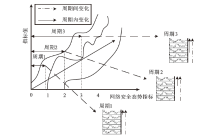
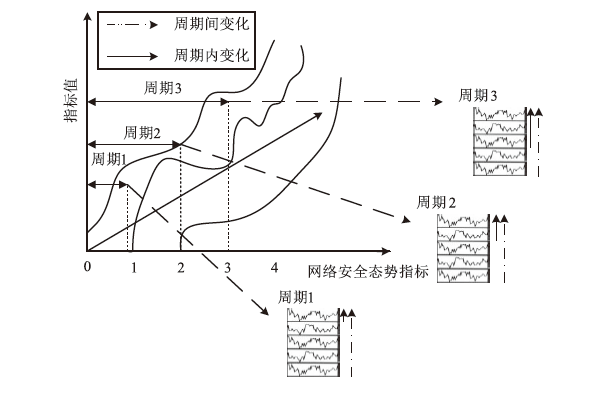
FFT-iTransformer-Based Cybersecurity Situation Awareness Feature Imputation and Prediction
ZHANG Xinyou1, GAO Zhichao2( ), FENG Li1, XING Huanlai1
), FENG Li1, XING Huanlai1
- 1. School of Computing and Artificial Intelligence, Southwest Jiaotong University, Chengdu 611756, China
2. Tangshan Institute, Southwest Jiaotong University, Tangshan 063000, China
-
Received:2024-12-02Online:2025-02-10Published:2025-03-07
CLC Number:
Cite this article
ZHANG Xinyou, GAO Zhichao, FENG Li, XING Huanlai. FFT-iTransformer-Based Cybersecurity Situation Awareness Feature Imputation and Prediction[J]. Netinfo Security, 2025, 25(2): 228-239.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.02.004
| [1] |
HE Chunrong, ZHU Jiang. Security Situation Prediction Method of GRU Neural Network Based on Attention Mechanism[J]. Systems Engineering and Electronics, 2021, 43(1): 258-266.
doi: 10.3969/j.issn.1001-506X.2021.01.32 |
|
何春蓉, 朱江. 基于注意力机制的GRU神经网络安全态势预测方法[J]. 系统工程与电子技术, 2021, 43(1): 258-266.
doi: 10.3969/j.issn.1001-506X.2021.01.32 |
|
| [2] | AMIRI M, JENSEN R. Missing Data Imputation Using Fuzzy-Rough Methods[J]. Neurocomputing, 2016, 205: 152-164. |
| [3] | BARTHOLOMEW D J. Time Series Analysis Forecasting and Control[J]. Journal of the Operational Research Society, 1971, 22(2): 199-201. |
| [4] | HAMZAÇEBI C. Improving Artificial Neural Networks’ Performance in Seasonal Time Series Forecasting[J]. Information Sciences, 2008, 178(23): 4550-4559. |
| [5] | WANG Jun, DU Wenjie, CAO Wei, et al. Deep Learning for Multivariate Time Series Imputation: A Survey[EB/OL]. (2024-02-06)[2024-11-11]. https://doi.org/10.48550/arXiv.240.04059. |
| [6] | CHE Zhengping, PURUSHOTHAM S, CHO K, et al. Recurrent Neural Networks for Multivariate Time Series with Missing Values[EB/OL]. (2018-04-17)[2024-11-11]. https://pubmed.ncbi.nlm.nih.gov/29666385/. |
| [7] | WU Haixu, HU Tengge, LIU Yong, et al. TimesNet: Temporal 2D-Variation Modeling for General Time Series Analysis[EB/OL]. (2023-04-12)[2024-11-11]. https://doi.org/10.48550/arXiv.2210.02186. |
| [8] | CINI A, MARISCA I, ALIPPI C. Filling the G_ap_s: Multivariate Time Series Imputation by Graph Neural Networks[EB/OL]. (2022-02-10)[2024-11-11]. https://doi.org/10.48550/arXiv.2108.00298. |
| [9] | LIU Yong, WU Haixu, WANG Jianmin, et al. Non-Stationary Transformers[C]// ACM. Proceedings of the 36th International Conference on Neural Information Processing Systems. New York: ACM, 2022: 9881-9889. |
| [10] |
HU Jingjing, MA Dongyan, LIU Chen, et al. Network Security Situation Prediction Based on MR-SVM[J]. IEEE Access, 2019, 7: 130937-130945.
doi: 10.1109/ACCESS.2019.2939490 |
| [11] |
ZHAO Dongmei, WU Yaxing, ZHANG Hongbin. Network Security Situation Prediction Based on IPSO-BiLSTM[J]. Computer Science, 2022, 49(7): 357-362.
doi: 10.11896/jsjkx.210900103 |
|
赵冬梅, 吴亚星, 张红斌. 基于IPSO-BiLSTM的网络安全态势预测[J]. 计算机科学, 2022, 49(7): 357-362.
doi: 10.11896/jsjkx.210900103 |
|
| [12] |
SUN Junfeng, LI Chenghai, CAO Bo. Network Security Situation Prediction Based on TCN-BiLSTM[J]. Systems Engineering and Electronics, 2023, 45(11): 3671-3679.
doi: 10.12305/j.issn.1001-506X.2023.11.36 |
|
孙隽丰, 李成海, 曹波. 基于TCN-BiLSTM的网络安全态势预测[J]. 系统工程与电子技术, 2023, 45(11): 3671-3679.
doi: 10.12305/j.issn.1001-506X.2023.11.36 |
|
| [13] | ZHAO Dongmei, LI Zhijian. Network Security Situation Prediction Based on Transformer[J]. Journal of Huazhong University of Science and Technology (Natural Science Edition), 2022, 50(5): 46-52. |
| 赵冬梅, 李志坚. 基于Transformer的网络安全态势预测[J]. 华中科技大学学报(自然科学版), 2022, 50(5): 46-52. | |
| [14] | LIU Yong, HU Tengge, ZHANG Haoran, et al. iTransformer: Inverted Transformers are Effective for Time Series Forecasting[EB/OL]. (2024-03-14)[2024-11-11]. https://doi.org/10.48550/arXiv.2310.06625. |
| [15] | ZHANG Jianhui, TENG Jie, LI Xiuhui, et al. Short-Term Prediction of Photovoltaic Power Based on Meteorological Features and Improved Transformer[J]. Journal of Engineering for Thermal Energy and Power, 2024, 39(8): 146-154. |
| 张建辉, 滕婕, 李秀慧, 等. 基于气象特征和改进Transformer的光伏功率短期预测[J]. 热能动力工程, 2024, 39(8): 146-154. | |
| [16] | ZHOU Tian, MA Ziqing, WEN Qingsong, et al. FEDformer: Frequency Enhanced Decomposed Transformer for Long-Term Series Forecasting[EB/OL]. (2022-06-16)[2024-11-11]. https://doi.org/10.48550/arXiv.2201.12740. |
| [17] | LIU Shizhan, YU Hang, LIAO Cong, et al. Pyraformer: Low-Complexity Pyramidal Attention for Long-Range Time Series Modeling and Forecasting[EB/OL]. (2023-02-14)[2024-11-11]. https://openreview.net/forum?id=0EXmFzUn5I. |
| [18] | DAS A, KONG Weihao, LEACH A, et al. Long-Term Forecasting with TIDE: Time-Series Dense Encoder[EB/OL]. (2024-04-04)[2024-11-11]. https://doi.org/10.48550/arXiv.2304.08424. |
| [19] | SZEGEDY C, LIU Wei, JIA Yangqing, et al. Going Deeper with Convolutions[C]// IEEE. 2015 IEEE Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2015: 1-9. |
| [20] | WU Haixu, XU Jiehui, WANG Jianmin, et al. Autoformer: Decomposition Transformers with Auto-Correlation for Long-Term Series Forecasting[EB/OL]. (2022-01-07)[2024-11-11]. https://doi.org/10.48550/arXiv.2106.13008. |
| [21] | LI Peng, GE Ruzhe, DONG Cun, et al. Adaptive SOH Estimation Method Based on the Transpose Transformer Model for Electrochemical Energy Storage[EB/OL]. (2024-08-12)[2024-11-11]. https://doi.org/10.13336/j.1003-6520.hve.20240555. |
| 李鹏, 葛儒哲, 董存, 等. 基于转置Transformer模型的电化学储能自适应SOH估计方法[EB/OL]. (2024-08-12)[2024-11-11]. https://doi.org/10.13336/j.1003-6520.hve.20240555. | |
| [22] | DONG Shi, SHU Longhui, XIA Qinyu, et al. Device Identification Method for Internet of Things Based on Spatial-Temporal Feature Residuals[J]. IEEE Transactions on Services Computing, 2024, 17(6): 3400-3416. |
| [23] | National Internet Emergency Center. The Cybersecurity Information and Dynamics Weekly Report from 2013 to 2022[EB/OL]. (2022-04-20)[2024-11-11]. https://www.cert.org.cn/publish/main/44/index_20.html. |
| 国家互联网应急中心. 2013年至2022年网络安全信息与动态周报[EB/OL]. (2022-04-20)[2024-11-11]. https://www.cert.org.cn/publish/main/44/index_20.html. | |
| [24] | MUNKHDALAI L, MUNKHDALAI T, PARK K H, et al. An End-to-End Adaptive Input Selection with Dynamic Weights for Forecasting Multivariate Time Series[J]. IEEE Access, 2019, 7: 99099-99114. |
| [25] | XIA Qinyu, DONG Shi, PENG Tao. An Abnormal Traffic Detection Method for IoT Devices Based on Federated Learning and Depthwise Separable Convolutional Neural Networks[C]// IEEE. 2022 IEEE International Performance, Computing, and Communications Conference (IPCCC). New York: IEEE, 2022: 352-359. |
| [1] | LI Hailong, CUI Zhian, SHEN Xieyang. Overview of Anomaly Analysis and Detection Methods for Network Traffic [J]. Netinfo Security, 2025, 25(2): 194-214. |
| [2] | YANG Zhipeng, LIU Daidong, YUAN Junyi, WEI Songjie. Research on Network Local Security Situation Fusion Method Based on Self-Attention Mechanism [J]. Netinfo Security, 2024, 24(3): 398-410. |
| [3] | HE Kaiyu, WANG Bin, YU Zhe, CHEN Fang. Research on ARP Spoofing Attack and Hardware Defense [J]. Netinfo Security, 2024, 24(10): 1604-1610. |
| [4] | FU Jing. Exploration and Practice of Security Protection of Critical Information Infrastructure of Water Conservancy [J]. Netinfo Security, 2023, 23(8): 121-127. |
| [5] | SUN Chengcheng. Research on Countermeasures for Network Security Governance [J]. Netinfo Security, 2023, 23(6): 104-110. |
| [6] | LI Dong, YU Junqing, WEN Ruibin, XIE Yiding. Endogenous Security Methods for Container Cloud Based on IPv6 [J]. Netinfo Security, 2023, 23(12): 21-28. |
| [7] | SUN Pengyu, TAN Jinglei, LI Chenwei, ZHANG Hengwei. Network Security Defense Decision-Making Method Based on Time Differential Game [J]. Netinfo Security, 2022, 22(5): 64-74. |
| [8] | JIN Bo, TANG Qianjin, TANG Qianlin. Interpretation of the Top 10 Development Trends of Network Security in 2022 by CCF Computer Security Professional Committee [J]. Netinfo Security, 2022, 22(4): 1-6. |
| [9] | CHEN Yan, WEI Xiang, LU Zhen. Research on Testing Approaches for Network Security Products in Cloud Computing Environment [J]. Netinfo Security, 2022, 22(12): 1-6. |
| [10] | BAI Hongpeng, DENG Dongxu, XU Guangquan, ZHOU Dexiang. Research on Intrusion Detection Mechanism Based on Federated Learning [J]. Netinfo Security, 2022, 22(1): 46-54. |
| [11] | GU Zhaojun, YAO Feng, DING Lei, SUI He. Network Security Test of Airport Fuel Supply Automatic Control System Based on Semi-physical Object [J]. Netinfo Security, 2021, 21(9): 16-24. |
| [12] | ZHAO Xiaolin, ZHAO Bin, ZHAO Jingjing, XUE Jingfeng. Research on Network Security Measurement Method Based on Attack Identification [J]. Netinfo Security, 2021, 21(11): 17-27. |
| [13] | WU Jiaming, XIONG Yan, HUANG Wenchao, WU Jianshuang. A Distance-based Fuzzing Mutation Method [J]. Netinfo Security, 2021, 21(10): 63-68. |
| [14] | JIN Zhigang, WANG Xinjian, LI Gen, YUE Shunmin. The Generation Method of Network Defense Strategy Combining with Attack Graph and Game Model [J]. Netinfo Security, 2021, 21(1): 1-9. |
| [15] | DONG Qiang, LUO Guoming, SHI Hongkui, ZHANG Yongyue. Research on Authentication and Key Agreement Method of IMS-based Mobile Communication Private Network [J]. Netinfo Security, 2021, 21(1): 88-96. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||