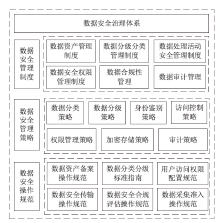
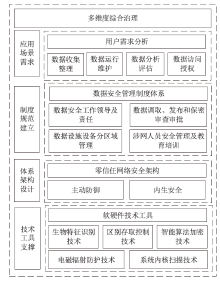
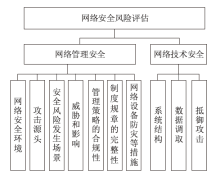
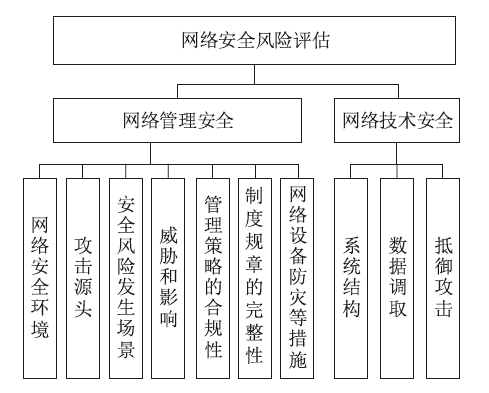
Netinfo Security ›› 2023, Vol. 23 ›› Issue (6): 104-110.doi: 10.3969/j.issn.1671-1122.2023.06.010
Previous Articles Next Articles
Research on Countermeasures for Network Security Governance
- School of International Law, China University of Political Science and Law, Beijing 102249, China
-
Received:2023-04-26Online:2023-06-10Published:2023-06-20
CLC Number:
Cite this article
SUN Chengcheng. Research on Countermeasures for Network Security Governance[J]. Netinfo Security, 2023, 23(6): 104-110.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.06.010
| [1] | XIE Yongjiang. Study on Principles of Cybersecurity Law[J]. Jinan Journal(Philosophy and Social Sciences), 2018(6): 41-52. |
| 谢永江. 论网络安全法的基本原则[J]. 暨南学报:哲学社会科学版, 2018(6): 41-52. | |
| [2] | HU Yu, LUO Xinwei, WANG Dan. The Digital Revolution: The Logic of Industrial Transformation in the New Era[M]. Beijing: Publishing House of Electronics Industry, 2022. |
| 胡煜, 罗欣伟, 王丹. 数字革命:新时代的产业转型逻辑[M]. 北京: 电子工业出版社, 2022. | |
| [3] | ZHANG Min, MA Minhu. The Cyber Security Obligations of Internet Service Providers in the Perspective of the National Security: “Guarantee” Transformation[J]. Journal of Intelligence, 2020(39): 45-53. |
| 张敏, 马民虎. 国家安全视域下网络服务提供者之网络安全义务的“保障”转型[J]. 情报杂志, 2020(39): 45-53. | |
| [4] | The National People’s Congress of the People’s Republic of China. Cybersecurity Law of the People’s Republic of China[EB/OL]. (2016-11-07)[2023-03-09]. http://www.npc.gov.cn/npc/c30834/201611/270b43e8b35e4f7ea98502b6f0e26f8a.shtml. |
| 中国人大网. 中华人民共和国网络安全法[EB/OL]. (2016-11-07)[2023-03-09]. http://www.npc.gov.cn/npc/c30834/201611/270b43e8b35e4f7ea98502b6f0e26f8a.shtml. | |
| [5] | XIAO Xiaolei, ZHAO Xuelian. Overview of the Research on Governance of Cross-Border Data Flow in China[J]. Netinfo Security, 2022, 22(10): 45-51. |
| 肖晓雷, 赵雪莲. 我国跨境数据流动治理的研究综述[J]. 信息网络安全, 2022, 22(10): 45-51. | |
| [6] | CAICT. White Paper on China’s Cyber Security Industry[EB/OL]. [2023-03-09]. http://www.caict.ac.cn/kxyj/qwfb/bps/202201/t20220124_396106.htm. |
| 中国信通院. 中国网络安全产业白皮书[EB/OL]. [2023-03-09]. http://www.caict.ac.cn/kxyj/qwfb/bps/202201/t20220124_396106.htm. | |
| [7] | YANG Heqing. Interpretation of the Cybersecurity Law of the People’s Republic of China[M]. Beijing: China Legal Publishing House, 2017. |
| 杨合庆. 《中华人民共和国网络安全法》解读[M]. 北京: 中国法制出版社, 2017. | |
| [8] | CSDN. White Paper on Data Security Governance 4.0[EB/OL]. (2022-06-09)[2023-03-09]. https://blog.csdn.net/kuankuanerfei/article/details/128038128. |
| CSDN. 数据安全治理白皮书4.0[EB/OL]. (2022-06-09)[2023-03-09]. https://blog.csdn.net/kuankuanerfei/article/details/128038128. | |
| [9] | QUE Tianshu, MO Fei. Cyber Ecological Governance Under the Overall National Security Perspective: Overall Evolution, Linkage Lineage, And Promotion Path[J]. Contemporary World and Socialism, 2021(1): 65-72. |
| 阙天舒, 莫非. 总体国家安全观下的网络生态治理——整体演化、联动谱系与推进路径[J]. 当代世界与社会主义, 2021(1): 65-72. | |
| [10] | WEN Yuheng, YU lin. Multi-Dimensional Cognition and Systematic Interpretation of the Concept of Data Security[J]. Information and Documentation Service, 2022, 43(6): 5-13. |
| 文禹衡, 于琳. 数据安全概念的多维度认知与体系化解读[J]. 情报资料工作, 2022, 43(6): 5-13. | |
| [11] | CHENG Xiao. On the Duty of Data Security[J]. Journal of Comparative Law, 2023(2): 60-73. |
| 程啸. 论数据安全保护义务[J]. 比较法研究, 2023(2): 60-73. | |
| [12] | MA Zhongfa, HU Ling. The Inprovement of China’s Legal System of Data Security Protection[J]. Science Technology and Law, 2021(2): 1-7. |
| 马忠法, 胡玲. 论我国数据安全保护法律制度的完善[J]. 科技与法律, 2021(2): 1-7. | |
| [13] | Office of the Central Cyberspace Affairs Commission. Measures for the Security Assessment of Outbound Data Transfer[EB/OL]. (2022-07-07)[2023-03-09]. http://www.cac.gov.cn/2022-07/07/c_1658811536396503.htm. |
| 中共中央网络安全和信息化委员会办公室. 数据出境安全评估办法[EB/OL]. (2022-07-07)[2023-03-09]. http://www.cac.gov.cn/2022-07/07/c_1658811536396503.htm. | |
| [14] | SHI Yewei. International Trade Rules in Cross-Border Data Flows: Regulation, Compatibility and Development[J]. Journal of Comparative Law, 2020(4): 173-183. |
| 时业伟. 跨境数据流动中的国际贸易规则:规制、兼容与发展[J]. 比较法研究, 2020(4): 173-183. |
| [1] | HUANG Jie, HE Chengjun. Service Protection Scheme Based on Software Defined Perimeter [J]. Netinfo Security, 2023, 23(6): 1-10. |
| [2] | WANG Xiaodi, HUANG Cheng, LIU Jiayong. A Survey of Cyber Security Open-Source Intelligence Knowledge Graph [J]. Netinfo Security, 2023, 23(6): 11-21. |
| [3] | XIE Ying, ZENG Zhu, HU Wei, DING Xuyang. A False Data Injection Attack Detecting and Compensating Method [J]. Netinfo Security, 2023, 23(6): 22-33. |
| [4] | YANG Yuguang, LU Jiayu. A Dynamic and Hierarchical Quantum Secret Sharing Protocol Based on Starlike Cluster States [J]. Netinfo Security, 2023, 23(6): 34-42. |
| [5] | LI Zhihua, WANG Zhihao. IoT Device Identification Method Based on LCNN and LSTM Hybrid Structure [J]. Netinfo Security, 2023, 23(6): 43-54. |
| [6] | TANG Yu, ZHANG Chi. A Privacy Protection Scheme for Information-Centric Networking Based on Intel SGX [J]. Netinfo Security, 2023, 23(6): 55-65. |
| [7] | LUO Yinuo, YAO Si, CHEN Jie, DONG Xiaoli. Software Tamper Resistance Scheme Based on White-Box CLEFIA Implementation [J]. Netinfo Security, 2023, 23(6): 66-73. |
| [8] | JIANG Zenghui, ZENG Weijun, CHEN Pu, WU Shitao. Review of Adversarial Samples for Modulation Recognition [J]. Netinfo Security, 2023, 23(6): 74-90. |
| [9] | WU Shangyuan, SHEN Guowei, GUO Chun, CHEN Yi. Threat Intelligence-Driven Dynamic Threat Hunting Method [J]. Netinfo Security, 2023, 23(6): 91-103. |
| [10] | ZHAO Jun, REN Yi, LI Bao, TAN Yusong. Research on the Supply Chain Security Risk Assessment Methods for Mixed Source Operating System [J]. Netinfo Security, 2023, 23(5): 50-61. |
| [11] | PEI Bei, ZHANG Shuihai, LYU Chunli. A Proactive Multi-Secret Sharing Scheme for Cloud Storage [J]. Netinfo Security, 2023, 23(5): 95-104. |
| [12] | CHEN Zitong, JIA Peng, LIU Jiayong. Identification Method of Malicious Software Hidden Function Based on Siamese Architecture [J]. Netinfo Security, 2023, 23(5): 62-75. |
| [13] | QIN Baodong, CHEN Congzheng, HE Junjie, ZHENG Dong. Multi-Keyword Searchable Encryption Scheme Based on Verifiable Secret Sharing [J]. Netinfo Security, 2023, 23(5): 32-40. |
| [14] | MAO Hongjing, CHENG Yukun, HU Honggang. Multiple Persistent Faults Analysis with Unknown Faults [J]. Netinfo Security, 2023, 23(5): 41-49. |
| [15] | ZHAO Xiaolin, WANG Qiyao, ZHAO Bin, XUE Jingfeng. Research on Anonymous Traffic Classification Method Based on Machine Learning [J]. Netinfo Security, 2023, 23(5): 1-10. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||