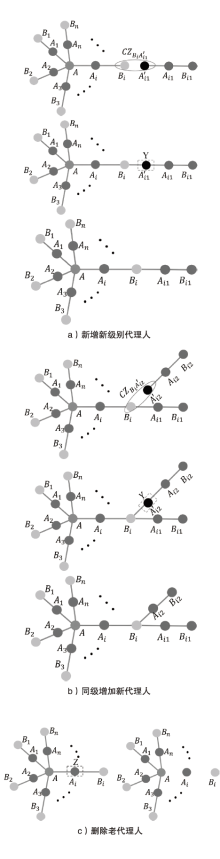
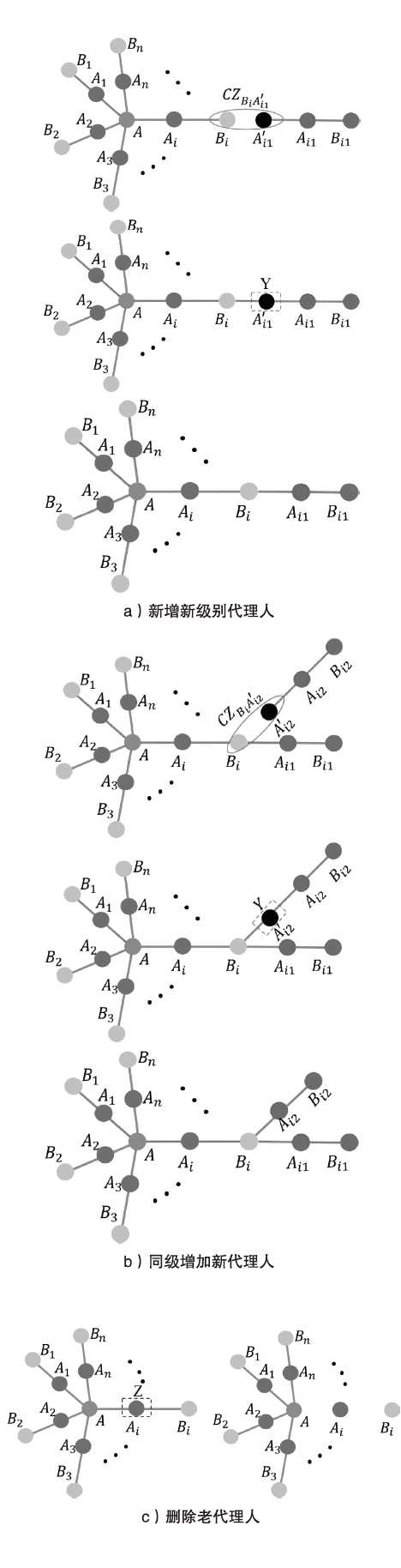
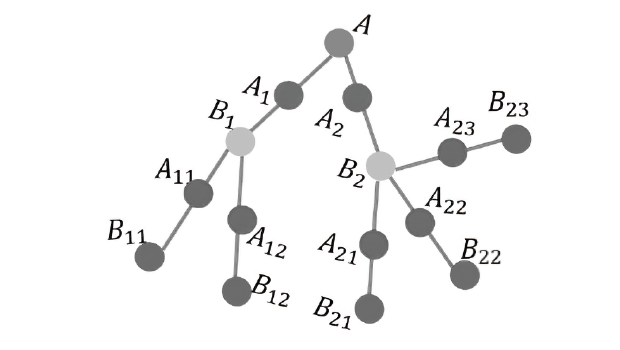
Netinfo Security ›› 2023, Vol. 23 ›› Issue (6): 34-42.doi: 10.3969/j.issn.1671-1122.2023.06.004
Previous Articles Next Articles
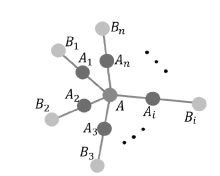
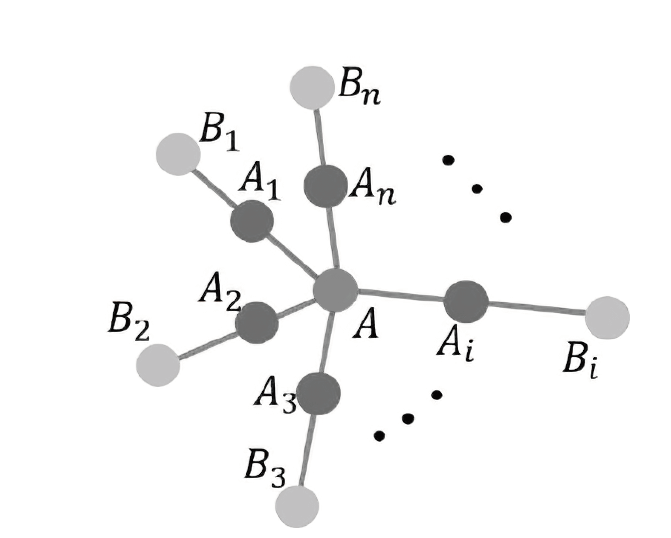
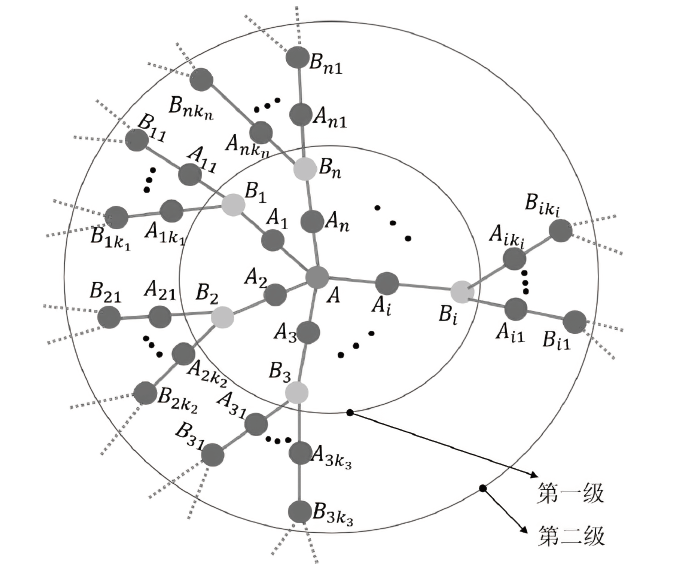
A Dynamic and Hierarchical Quantum Secret Sharing Protocol Based on Starlike Cluster States
- 1. Faculty of Information Technology, Beijing University of Technology, Beijing 100124, China
2. Beijing Key Laboratory of Trusted Computing, Beijing 100124, China
-
Received:2023-03-31Online:2023-06-10Published:2023-06-20
CLC Number:
Cite this article
YANG Yuguang, LU Jiayu. A Dynamic and Hierarchical Quantum Secret Sharing Protocol Based on Starlike Cluster States[J]. Netinfo Security, 2023, 23(6): 34-42.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.06.004
| [1] |
SHAMIR A. How to Share a Secret[J]. Commun ACM, 1979, 22(11): 612-613.
doi: 10.1145/359168.359176 URL |
| [2] | BLAKLEY G R. Safeguarding Cryptographic Keys[C]// IEEE. American Federation of Information Processing Societies-Conference Proceedings. New York: IEEE, 1979: 313-317. |
| [3] | KOTHARI S C. Generalized Linear Threshold Scheme[C]// Springer. Advances in Cryptology. Berlin:Springer, 1984: 231-241. |
| [4] |
TASSA T. Hierarchical Threshold Secret Sharing[J]. Cryptol, 2007, 20: 1-27.
doi: 10.1080/0161-119691884735 URL |
| [5] |
FARRAS O, PADRO C. Ideal Hierarchical Secret Sharing Schemes[J]. IEEE Transactions on Information Theory, 2012, 58(5): 3273-3286.
doi: 10.1109/TIT.2011.2182034 URL |
| [6] | TRAVERSO G, DEMIREL D, BUCHMANN J. Dynamic and Verifiable Hierarchical Secret Sharing[C]// Springer. International Conference on Information Theoretic Security. Berlin:Springer, 2016: 299-319. |
| [7] |
CHEN Qi, TANG Chunming, LIN Zhiqiang. Efficient Explicit Constructions of Multipartite Secret Sharing Schemes[J]. IEEE Transactions on Information Theory, 2021, 68: 601-636.
doi: 10.1109/TIT.2021.3123102 URL |
| [8] |
ZHANG En, LI Ming, YIU S, et al. Fair Hierarchical Secret Sharing Scheme Based on Smart Contract[J]. Information Sciences, 2021, 546: 166-179.
doi: 10.1016/j.ins.2020.07.032 URL |
| [9] |
YUAN Jiangtao, YANG Jing, WANG Chenyu, et al. A New Efficient Hierarchical Multi-Secret Sharing Scheme Based on Linear Homogeneous Recurrence Relations[J]. Information Sciences, 2022, 592: 36-49.
doi: 10.1016/j.ins.2022.01.053 URL |
| [10] |
WANG Xinwen, XIA Lixin, WANG Zhiyong, et al. Hierarchical Quantum-Information Splitting[J]. Optics Communications, 2010, 283(6): 1196-1199.
doi: 10.1016/j.optcom.2009.11.015 URL |
| [11] |
WANG Xinwen, ZHANG Dengyu, TANG Shiqing, et al. Hierarchical Quantum Information Splitting with Six-Photon Cluster States[J]. International Journal of Theoretical Physics, 2010, 49: 2691-2697.
doi: 10.1007/s10773-010-0461-8 URL |
| [12] |
WANG Xinwen, ZHANG Dengyu, TANG Shiqing, et al. Multiparty Hierarchical Quantum-Information Splitting[EB/OL]. (2011-09-19)[2023-03-20]. https://doi.org/10.48550/arXiv.1101.3700.
doi: https://doi.org/10.48550/arXiv.1101.3700 |
| [13] |
BAI Mingqiang, MO Zhiwen. Hierarchical Quantum Information Splitting with Eight-Qubit Cluster States[J]. Quantum Information Processing, 2013, 12: 1053-1064.
doi: 10.1007/s11128-012-0440-5 URL |
| [14] | PENG Jiayin, MO Zhiwen. Hierarchical and Probabilistic Quantum State Sharing with a Nonmaximally Four-Qubit Cluster State[J]. International Journal of Quantum Information, 2013, 11(1): 135-145. |
| [15] |
XU Gang, WANG Cong, YANG Yixian. Hierarchical Quantum Information Splitting of an Arbitrary Two-Qubit State via the Cluster State[J]. Quantum Information Processing, 2014, 13: 43-57.
doi: 10.1007/s11128-013-0670-1 URL |
| [16] |
ZHA Xinwei, MIAO Ning, WANG Huifang. Hierarchical Quantum Information Splitting of an Arbitrary Two-Qubit Using a Single Quantum Resource[J]. International Journal Theoretical Physics, 2019, 58: 2428-2434.
doi: 10.1007/s10773-019-04134-3 |
| [17] | PENG Jiayin, BAI Mingqiang, MO Zhiwen. Hierarchical and Probabilistic Quantum State Sharing via a Non-Maximally Entangled $|\chi $ State[EB/OL]. (2014-12-03)[2023-03-20]. http://www.cnki.com.cn/Article/CJFDTotal-ZGWL201401011.htm. |
| [18] | QIN Huawang, TANG W K S, TSO R. Hierarchical Quantum Secret Sharing Based on Special High-Dimensional Entangled State[J]. IEEE Journal of Selected Topics in Quantum Electronics, 2020, 26(3): 53-68. |
| [19] |
MISHRA S, SHUKLA C, PATHAK A, et al. An Integrated Hierarchical Dynamic Quantum Secret Sharing Protocol[J]. International Journal of Theoretical Physics, 2015, 54(9): 3143-3154.
doi: 10.1007/s10773-015-2552-z URL |
| [20] |
LAI Hong, PIEPRZYK J, PAN Lei. Dynamic Hierarchical Quantum Secret Sharing Based on the Multiscale Entanglement Renormalization Ansatz[EB/OL]. (2022-10-18)[2023-03-20]. https://doi.org/10.1103/PhysRevA.106.052403.
doi: https://doi.org/10.1103/PhysRevA.106.052403 |
| [21] | CHEN Qing, CHENG Jianhua, WANG Kelin, et al. Efficient Construction of Two-Dimensional Cluster States with Probabilistic Quantum Gates[J]. Physical Review A, 2006, 73(1): 23-28. |
| [22] | FUJII K, TOKUNAGA Y. Fault-Tolerant Topological One-Way Quantum Computation with Probabilistic Two-Qubit Gates[J]. Physical Review Letters, 2010, 105(25): 1-5. |
| [23] | FUJII K, YAMAMOTO K. Topological One-Way Quantum Computation on Verified Logical Cluster States[J]. Physical Review A, 2010, 82(6): 1-4. |
| [24] |
JIA Hengyue, WEN Qiaoyan, GAO Fei, et al. Dynamic Quantum Secret Sharing[J]. Physics Letters A, 2012, 376(10), 1035-1041.
doi: 10.1016/j.physleta.2012.02.004 URL |
| [25] |
YANG Yuguang, LIU Zhichao, LI Jian, et al. Theoretically Extensible Quantum Digital Signature with Starlike Cluster States[J]. Quantum Information Processing, 2017, 16(1): 1-15.
doi: 10.1007/s11128-016-1481-y URL |
| [26] | HEIN M, EISERT J, and Briegel H J. Multi-Party Entanglement in Graph States[EB/OL]. (2005-08-09)[2023-03-20]. https://arxiv.org/pdf/quant-ph/0307130. pdf. |
| [27] |
JENNEWEIN T, SIMON C, WWIHS G, et al. Quantum Cryptography with Entangled Photons. Physical Review Letters, 2000, 84(20): 4729-4732.
pmid: 10990782 |
| [28] |
GOBBY C, YUAN Zhiliang, SHIELDS A J. Quantum Key Distribution over 122km Standard Telecom Fiber[J]. Applied Physics Letters, 2004, 84: 3762-3764.
doi: 10.1063/1.1738173 URL |
| [29] | JIA Hengyue, LIU Kangting, WU Xia, et al. Quantum Cheque Protocol Based on Bell States[J]. Netinfo Security, 2022, 22(6): 38-43. |
| 贾恒越, 刘康婷, 武霞, 等. 基于Bell态的量子支票协议[J]. 信息网络安全, 2022, 22(6): 38-43. | |
| [30] | LIU Lu, LI Zhihui, LU Dianjun, et al. Quantum Secret Sharing Scheme Based on Linear Codes[J]. Netinfo Security, 2021, 21(8): 62-69. |
| 刘璐, 李志慧, 芦殿军, 等. 基于线性码的量子秘密共享方案[J]. 信息网络安全, 2021, 21(8): 62-69. | |
| [31] | XIE Sijiang, GAO Qiong, FENG Yan. A Multiple Paths Routing Scheme with Least Number of Public Nodes Based on Trust Relaying Quantum Key Distribution Network[J]. Netinfo Security, 2021, 21(7): 35-42. |
| 谢四江, 高琼, 冯雁. 基于可信中继量子密钥分发网络的最少公共节点多路径路由方案[J]. 信息网络安全, 2021, 21(7): 35-42. |
| [1] | ZHANG Zhenghui, CHEN Xingshu, LUO Yonggang, WU Tianxiong. A Job Performance Evaluation Method under Spark Platform [J]. Netinfo Security, 2022, 22(9): 86-95. |
| [2] | GUO Baoxia, WANG Jiahui, MA Limin, ZHANG Wei. Research on Dynamic Access Control Model of Sensitive Data Based on Zero Trust [J]. Netinfo Security, 2022, 22(6): 86-93. |
| [3] | ZHANG Wei, XU Zhigang, CHEN Yunfang, HUANG Haiping. Design and Implementation of a SDN Honeynet Based on Dynamic Docker [J]. Netinfo Security, 2022, 22(4): 40-48. |
| [4] | SHI Runhua, WANG Shuhao, LI Kunchang. A Lightweight Cross-domain Mutual Authentication Scheme in V2G Networks [J]. Netinfo Security, 2022, 22(3): 20-28. |
| [5] | YI Zhengge, YUAN Wenyong, LI Ruifeng, YANG Xiaoyuan. Identity-based and Dynamic Operating Solution for Cloud Storage [J]. Netinfo Security, 2022, 22(2): 86-95. |
| [6] | LIU Lu, LI Zhihui, LU Dianjun, YAN Chenhong. Quantum Secret Sharing Scheme Based on Linear Codes [J]. Netinfo Security, 2021, 21(8): 62-69. |
| [7] | WANG Gang, WANG Zhiyi, ZHANG Enning, MA Runnian. Signal Game Model and Migration Strategies for Multi-stage Platform Dynamic Defense [J]. Netinfo Security, 2021, 21(5): 48-57. |
| [8] | HUANG Changhui, HU Guangjun, LI Haiwei. Research on Unknown Threat Blocking Technology of Web Application Based on URL Intelligent Whitelist [J]. Netinfo Security, 2021, 21(3): 1-6. |
| [9] | LI Jiawei, WU Kehe, ZHANG Bo. Research on Anomaly Detection of Power Industrial Control System Based on Gaussian Mixture Clustering [J]. Netinfo Security, 2021, 21(3): 53-63. |
| [10] | DING Jianli, CHEN Pan, MA Yong. Research on Dynamic Desensitization Method of Civil Aviation Passenger Information Based on Generalized FPE Encryption [J]. Netinfo Security, 2021, 21(2): 45-52. |
| [11] | WEI Zhanzhen, PENG Xingyuan, ZHAO Hong. Resource Access Control Scheme Based on User Credit in SDN [J]. Netinfo Security, 2021, 21(10): 33-40. |
| [12] | WANG Juan, YANG Hongyuan, FAN Chengyang. A SDN Dynamic Honeypot with Multi-phase Attack Response [J]. Netinfo Security, 2021, 21(1): 27-40. |
| [13] | CHEN Fucai, ZHOU Mengli, LIU Wenyan, LIANG Hao. Feedback Control Method for Mimic Defense in Cloud Environment [J]. Netinfo Security, 2021, 21(1): 49-56. |
| [14] | ZHOU Zhining, WANG Binjun, ZHAI Yiming, TONG Xin. Spam Filtering Model Based on ALBERT Dynamic Word Vector [J]. Netinfo Security, 2020, 20(9): 107-111. |
| [15] | HAN Lei, CHEN Wuping, ZENG Zhiqiang, ZENG Yingming. Research on Hierarchical Network Structure and Application of Blockchain [J]. Netinfo Security, 2020, 20(9): 112-116. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||