Netinfo Security ›› 2021, Vol. 21 ›› Issue (5): 48-57.doi: 10.3969/j.issn.1671-1122.2021.05.006
Previous Articles Next Articles
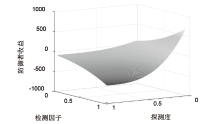
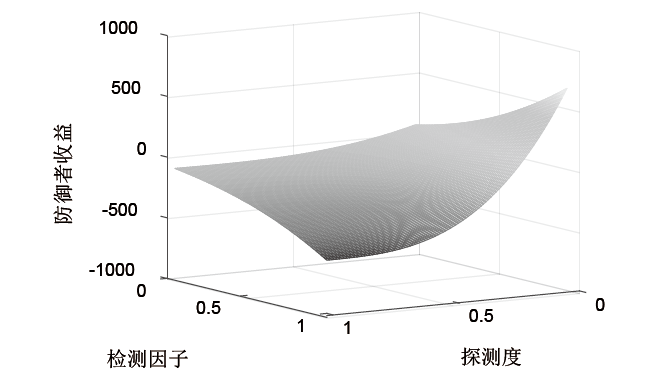
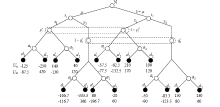
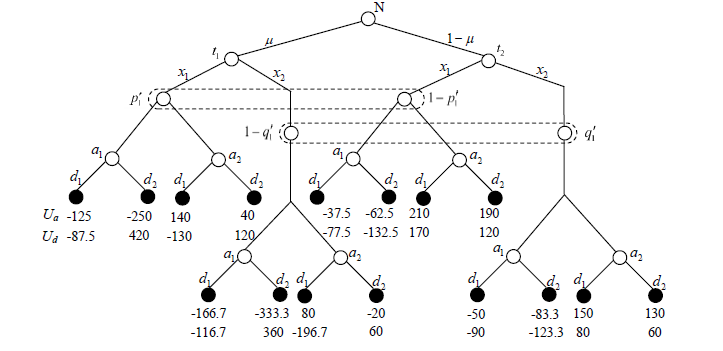
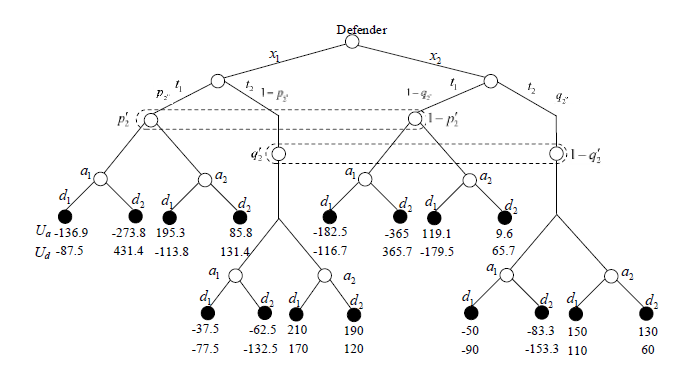
Signal Game Model and Migration Strategies for Multi-stage Platform Dynamic Defense
WANG Gang( ), WANG Zhiyi, ZHANG Enning, MA Runnian
), WANG Zhiyi, ZHANG Enning, MA Runnian
- Institute of Navigation and Communication, Air Force Engineering University, Xi’an, 710077, China
-
Received:2021-01-05Online:2021-05-10Published:2021-06-22 -
Contact:WANG Gang E-mail:wglxl@nudt.edu.cn
CLC Number:
Cite this article
WANG Gang, WANG Zhiyi, ZHANG Enning, MA Runnian. Signal Game Model and Migration Strategies for Multi-stage Platform Dynamic Defense[J]. Netinfo Security, 2021, 21(5): 48-57.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.05.006
| [1] | JAJODIA S, GHOSH A K, SWARUP V, et al. Moving Target Defense: Creating Asymmetric Uncertainty for Cyber Threats[M]. Berlin: Springer Ebooks, 2011. |
| [2] | LIU Jiang, ZHANG Hongqi, LIU Yi. Research on Optimal Selection of Moving Target Defense Policy Based on Dynamic Game with Incomplete Information[J]. Acta Electronica Sinica, 2018,46(1):82-89. |
| 刘江, 张红旗, 刘艺. 基于不完全信息动态博弈的动态目标防御最优策略选取研究[J]. 电子学报, 2018,46(1):82-89. | |
| [3] | LIU Wenyan, HUO Shumin, CHEN Yang, et al. Analysis and Study of Cyber Attack Chain Model[J]. Journal on Communications, 2018,39(S2):88-94. |
| 刘文彦, 霍树民, 陈扬, 等. 网络攻击链模型分析及研究[J]. 通信学报, 2018,39(S2):88-94. | |
| [4] | ZHANG Hengwei, HUANG Jianming. Network Defense Strategy Selection Method Based on Markov Evolutionary Game[J]. Acta Electronica Sinica 2018,46(6):1503-1509. |
| 张恒巍, 黄健明. 基于Markov演化博弈的网络防御策略选取方法[J]. 电子学报, 2018,46(6):1503-1509. | |
| [5] | ZHEN Ni, LI Qianmu, LIU Gang. Game-model-based Network Security Risk Control[J]. Computer, 2018,51(4):28-38. |
| [6] | LIU Zhuotao, HAO Jin, HU YIH-CHUN, et al. Practical Proactive DDoS-attack Mitigation via Endpoint-driven In-network Traffic Control[J]. IEEE/ACM Transactions on Networking, 2018,26(4):1-14. |
| [7] |
SONG Fei, ZHOU Yutong, WANG Yu, et al. Smart Collaborative Distribution for Privacy Enhancement in Moving Target Defense[J]. Information Sciences, 2019,479(4):593-606.
doi: 10.1016/j.ins.2018.06.002 URL |
| [8] | TIAN Liqin, LIN Chuang. A Kind of Game-theoretic Control Mechanism of User Behavior Trust Based on Prediction in Trustworthy Network[J]. Chinese Journal of Computers, 2007,30(11):1930-1938. |
| 田立勤, 林闯. 可信网络中一种基于行为信任预测的博弈控制机制[J]. 计算机学报, 2007,30(11):1930-1938. | |
| [9] | JIANG Wei. Research on Active Defense Based on Attack-defense Game Model[D]. Harbin: Harbin Institute of Technology, 2010. |
| 姜伟. 基于攻防博弈模型的主动防御关键技术研究[D]. 哈尔滨:哈尔滨工业大学, 2010. | |
| [10] |
ZHAO Qiang, DONG Jun. An Initiative Network Defence Strategy Based on Game Theory[J]. International Journal of Applied Decision Sciences, 2018,11(2):195-209.
doi: 10.1504/IJADS.2018.090931 URL |
| [11] |
TAN Jinglei, LEI Cheng, ZHANG Hongqi, et al. Optimal Strategy Selection Approach to Moving Target Defense Based on Markov Robust Game[J]. Computers & Security, 2019,85(8):63-76.
doi: 10.1016/j.cose.2019.04.013 URL |
| [12] | ZHANG Hengwei, HUANG Shirui. Markov Differential Game Model and Its Application in Network Security[J]. Acta Electronica Sinica, 2019,47(3):606-612. |
| 张恒巍, 黄世锐. Markov微分博弈模型及其在网络安全中的应用[J]. 电子学报, 2019,47(3):606-612. | |
| [13] |
CHEN Zihan, CHENG Guang. Moving Target Defense Technology using Stackelberg-markov Asymmetrical Trilateral Game Model[J]. Journal on Computers, 2020,43(3):512-525.
doi: 10.1093/comjnl/43.6.512 URL |
| 陈子涵, 程光. 基于Stackelberg-markov非对等三方博弈模型的移动目标防御技术[J]. 计算机学报, 2020,43(3):512-525. | |
| [14] |
WU Hao, WANG Wei, WEN Changyun, et al. Game Theoretical Security Detection Strategy for Networked Systems[J]. Information Sciences, 2018,453(7):346-363.
doi: 10.1016/j.ins.2018.04.051 URL |
| [15] | ZHANG Hengwei, YANG Haopu. Defense Decision-making Method for Anti-apt Attack Based on Attack-defense Signaling Game[J]. Computer Engineering and Design, 2019,40(1):59-64. |
| 张恒巍, 杨豪璞. 基于攻防信号博弈的APT攻击防御决策方法[J]. 计算机工程与设计, 2019,40(1):59-64. | |
| [16] | WANG Zengguang, LU Yu, LI Xi, et al. Optimal Defense Strategy Selection Based on the Static Bayesian Game[J]. Journal of XiDian University, 2019,46(5):55-61. |
| 王增光, 卢昱, 李玺, 等. 静态贝叶斯博弈最优防御策略选取方法[J]. 西安电子科技大学学报, 2019,46(5):55-61. | |
| [17] | ZHANG Hengwei, LI Tao. Optimal Active Defense Based on Multi-stage Attack-Defense Signaling Game[J]. Acta Electronica Sinica, 2017,45(2):431-439. |
| 张恒巍, 李涛. 基于多阶段攻防信号博弈的最优主动防御[J]. 电子学报, 2017,45(2):431-439. | |
| [18] |
JIANG LYU, ZHANG Hengwei, WANG Jindong. Optimal Strategy Selection Method for Moving Target Defense Based on Signaling Game[J]. Journal on Communications 2019,40(6):128-137.
doi: 10.1111/j.1460-2466.1990.tb02266.x URL |
| 蒋侣, 张恒巍, 王晋东. 基于信号博弈的移动目标防御最优策略选取方法[J]. 通信学报, 2019,40(6):128-137. | |
| [19] | WANG Zhiyi, WANG Gang, CHEN Tongrui, et al. Platform Dynamic Defense Evolution Game Model and State Migration Strategy[J]. Journal of Air Force Engineering University(Natural Science Edition), 2020,21(3):85-92+98. |
| 王志屹, 王刚, 陈彤睿, 等. 平台动态防御演化博弈模型和状态迁移策略[J]. 空军工程大学学报(自然科学版), 2020,21(3):85-92+98. |
| [1] | LI Peng, ZHENG Tiantian, XU He, ZHU Feng. RFID Security Authentication Protocol Based on Blockchain Technology [J]. Netinfo Security, 2021, 21(5): 1-11. |
| [2] | ZHENG Jun, NIE Rong, WANG Shouxin, TAN Yu’an. Attribute Weight Snapshot Selection Strategy Based on Docker Container Fault Recovery [J]. Netinfo Security, 2021, 21(5): 12-18. |
| [3] | ZHOU Yousheng, ZHONG Tianqi. Blockchain-based Fair Exchange Scheme [J]. Netinfo Security, 2021, 21(5): 19-30. |
| [4] | WU Chi, SHUAI Junlan, LONG Tao, YU Junqing. Research on Detection Method of User Abnormal Operation Based on Linux Shell Commands [J]. Netinfo Security, 2021, 21(5): 31-38. |
| [5] | GU Zhaojun, CAI Chang, WANG Ming. The Masking Method of Civil Aviation Passenger Data Based on Improved Format-preserving Encryption [J]. Netinfo Security, 2021, 21(5): 39-47. |
| [6] | LIU Zi’ang, HUANG Yuanyuan, MA Jiali, ZHOU Rui. Design and Implementation of Monitoring Platform for Medical Data Abuse Based on Blockchain [J]. Netinfo Security, 2021, 21(5): 58-66. |
| [7] | XU Wanshan, ZHANG Jianbiao, YUAN Yilin, LI Zheng. Research on Trusted Server Startup Method Based on BMC [J]. Netinfo Security, 2021, 21(5): 67-73. |
| [8] | WANG Kaixuan, TENG Yajun, WANG Qiongxiao, WANG Wei. Research on the Application of SM Algorithms of Implicit Certificate [J]. Netinfo Security, 2021, 21(5): 74-81. |
| [9] | REN Shixuan, WANG Maoyu, ZHAO Hui. An Improved Method of Backdoor Attack in DNN [J]. Netinfo Security, 2021, 21(5): 82-89. |
| [10] | ZHANG Jun, WANG Yongjie, ZHANG Jingye, YANG Lin. Cascading Failure Model for Inter-domain Routing System Based on Optimal Valid Path [J]. Netinfo Security, 2021, 21(5): 90-99. |
| [11] | WANG Jian, ZHAO Manli, CHEN Zhihao, SHI Bo. An Authentication Scheme for Conditional Privacy Preserving Based on Pseudonym in Intelligent Transportation [J]. Netinfo Security, 2021, 21(4): 49-61. |
| [12] | ZHENG Hongying, LI Lin, XIAO Di. Secret Image Transmission and Tamper Recovery Based on Compressed Sensing for Fog Computing [J]. Netinfo Security, 2021, 21(4): 10-20. |
| [13] | YOU Wenting, ZHANG Leyou, YE Yadi, LI Hui. Privacy-preserving Attribute-based Dynamic Broadcast Encryption Mechanism in Multi-user Communication System [J]. Netinfo Security, 2021, 21(4): 21-30. |
| [14] | SONG Yubo, MA Wenhao, HU Aiqun, WANG Junbo. A Covert Channel Communication Method Based on Pixel Offset Encoding and Decoding Technique [J]. Netinfo Security, 2021, 21(4): 31-38. |
| [15] | CAI Manchun, WANG Tengfei, YUE Ting, LU Tianliang. ARF-based Tor Website Fingerprint Recognition Technology [J]. Netinfo Security, 2021, 21(4): 39-48. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||