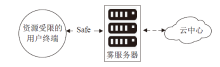
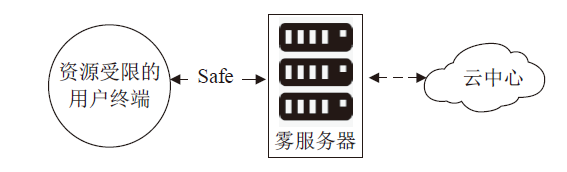
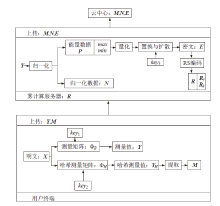
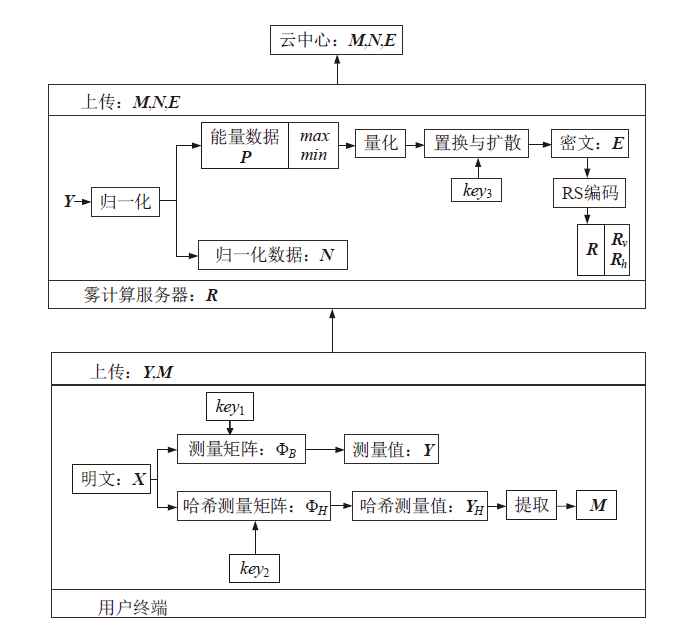
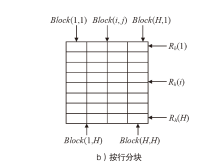
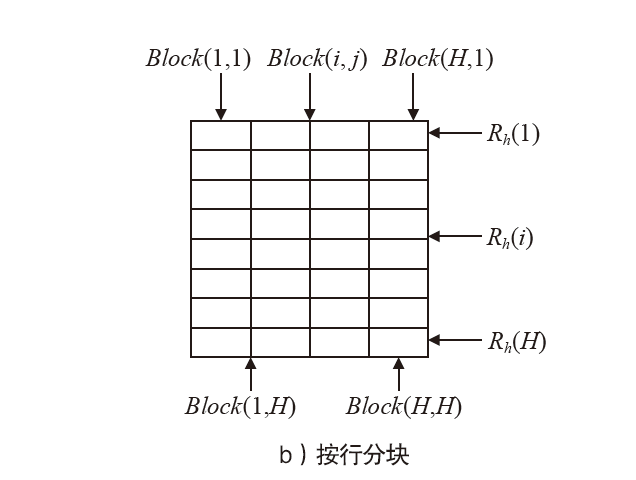
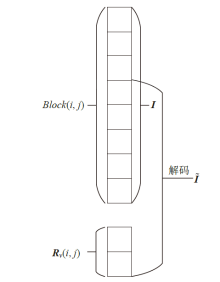
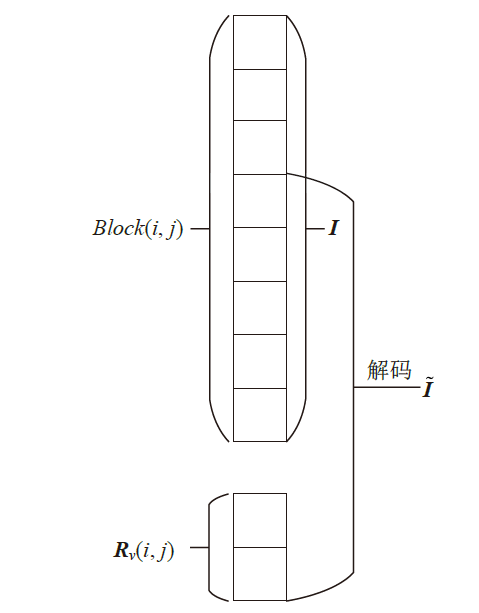
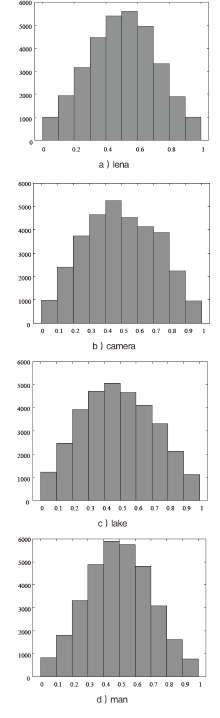
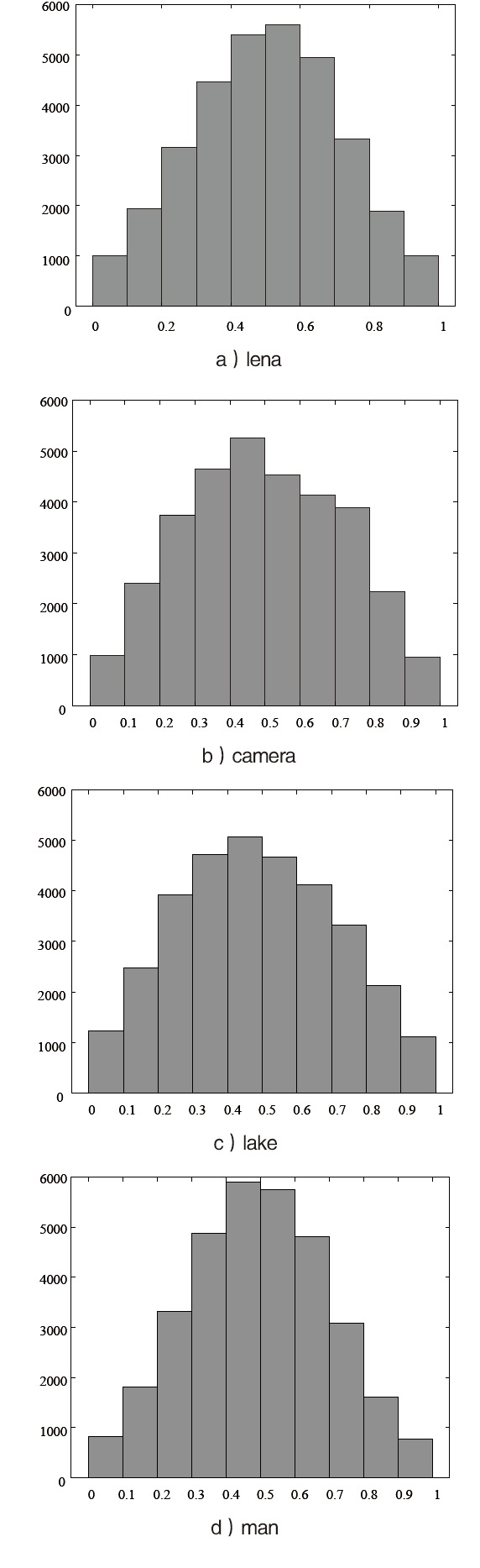
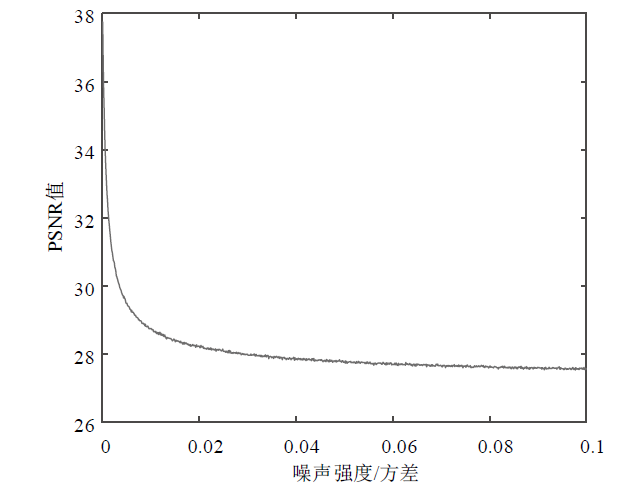
| [1] |
MELL P M, GRANCE T. The NIST Definition of Cloud Computing[EB/OL]. https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-145.pdf, 2020-07-12.
|
| [2] |
TAYADE D. Mobile Cloud Computing: Issues, Security, Advantages, Trends[J]. International Journal of Computer Science and Information Technologies, 2014,5(5):6635-6639.
|
| [3] |
BONOMI F, MILITO R, ZHU Jiang, et al. Fog Computing and Its Role in the Internet of Things[C]// ACM. The First Edition of the MCC Workshop on Mobile Cloud Computing, August 17, 2012, Helsinki, Finland. New York: ACM, 2012: 13-16.
|
| [4] |
WANG Tian, ZHOU Jiyuan, CHEN Xinlei, et al. A Three-layer Privacy Preserving Cloud Storage Scheme Based on Computational Intelligence in Fog Computing[J]. IEEE Transactions on Emerging Topics in Computational Intelligence, 2018,2(1):3-12.
doi: 10.1109/TETCI
URL
|
| [5] |
WANG Tian, MEI Yaxin, JIA Weijia, et al. Edge-based Differential Privacy Computing for Sensor-cloud Systems[EB/OL]. https://www.sciencedirect.com/science/article/abs/pii/S074373151930293X, 2020-07-14.
|
| [6] |
DONOHO D L. Compressed Sensing[J]. IEEE Transactions on Information Theory, 2006,52(4):1289-1306.
doi: 10.1109/TIT.2006.871582
URL
|
| [7] |
GAN Lu. Block Compressed Sensing of Natural Images[C]// IEEE. 15th International Conference on Digital Signal Processing, August 1-4, 2007, Cardiff, UK. New Jersey: IEEE, 2007: 403-406.
|
| [8] |
BARANIUK R, DAVENPORT M, DEVORE R, et al. A Simple Proof of the Restricted Isometry Property for Random Matrices[J]. Constructive Approximation, 2008,28(3):253-263.
doi: 10.1007/s00365-007-9003-x
URL
|
| [9] |
CANDES E J, TAO T. Near-optimal Signal Recovery from Random Projections: Universal Encoding Strategies?[J]. IEEE Transactions on Information Theory, 2006,52(12):5406-5425.
doi: 10.1109/TIT.2006.885507
URL
|
| [10] |
BIANCHI T, BIOGLIO V, MAGLI E, et al. Analysis of One-time Random Projections for Privacy Preserving Compressed Sensing[J]. IEEE Transactions on Information Forensics and Security, 2016,11(2):313-327.
doi: 10.1109/TIFS.2015.2493982
URL
|
| [11] |
CHEN Junxin, ZHANG Yu, LIN Qi, et al. Exploiting Chaos-based Compressed Sensing and Cryptographic Algorithm for Image Encryption and Compression[J]. Optics & Laser Technology, 2018,99(1):238-248.
|
| [12] |
ZHOU Kanglei, FAN Jingjing, FAN Haiju, et al. Secure Image Encryption Scheme Using Double Random-phase Encoding and Compressed Sensing[EB/OL]. https://www.sciencedirect.com/science/article/abs/pii/S0030399219309648, 2020-08-12.
|
| [13] |
CHAI Xiuli, FU Xianglong, GAN Zhihua, et al. An Efficient Chaos-based Image Compression and Encryption Scheme Using Block Compressive Sensing and Elementary Cellular Automata[EB/OL]. https://link.springer.com/article/10.1007/s00521-018-3913-3#article-info, 2018-12-29.
|
| [14] |
LIU Zhanqiang, WANG Licheng, WANG Xianmin, et al. Secure Remote Sensing Image Registration Based on Compressed Sensing in Cloud Setting[EB/OL]. https://ieeexplore.ieee.org/document/8663267, 2019-03-08.
|
| [15] |
XIE Dong, CHEN Fulong, LUO Yonglong, et al. One-to-many Image Encryption with Privacy-preserving Homomorphic Outsourced Decryption Based on Compressed Sensing[EB/OL]. https://www.sciencedirect.com/science/article/abs/pii/S1051200419301332, 2020-08-20.
|
| [16] |
ZHANG Yushu, XIANG Yong, ZHANG L Y, et al. Efficiently and Securely Outsourcing Compressed Sensing Reconstruction to a Cloud[EB/OL]. https://www.sciencedirect.com/science/article/abs/pii/S0020025519304293, 2020-08-20.
|
| [17] |
ZHANG Yushu, WANG Ping, FANG Liming, et al. Secure Transmission of Compressed Sampling Data Using Edge Clouds[J]. IEEE Transactions on Industrial Informatics, 2020,16(10):6641-6651.
doi: 10.1109/TII.9424
URL
|
| [18] |
KANG Liwei, LU Chunshien, HSU C Y, et al. Compressive Sensing-based Image Hashing[C]// IEEE. 16th IEEE International Conference on Image Processing, November 7-10, 2009, Cairo, Egypt. New Jersey: IEEE, 2009: 1285-1288.
|
| [19] |
WU T, RULAND C. An Improved Authenticated Compressive Sensing Imaging[C]// IEEE. 12th International Conference on Semantic Computing, January 31-February 2, 2018, Laguna Hills, CA, USA. New Jersey: IEEE, 2018: 164-171.
|
| [20] |
BIANCHI T, BIOGLIO V, MAGLI E. On the Security of Random Linear Measurements[C]// IEEE. IEEE International Conference on Acoustics, Speech and Signal Processing, May 4-9, 2014, Florence, Italy. New Jersey: IEEE, 2014: 3992-3996.
|
| [21] |
PLANK J S. T1: Erasure Codes for Storage Applications[EB/OL]. http://ecee.colorado.edu/ecen5653/ecen5653/papers/Erasure-Code-Overview-FAST-2005.pdf, 2020-09-10.
|
| [22] |
PAK C, HUANG L. A New Color Image Encryption Using Combination of the 1D Chaotic Map[EB/OL]. https://dl.acm.org/doi/abs/10.5555/3085606.3085775, 2020-09-14.
|
 )
)