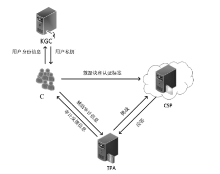
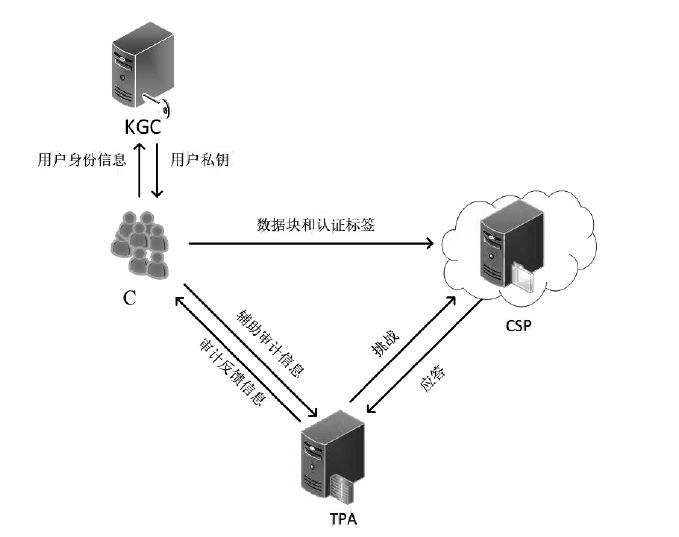
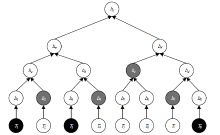
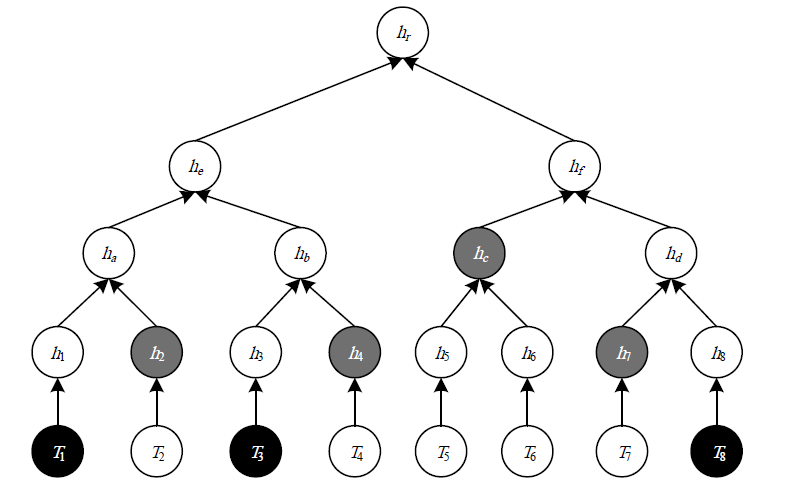
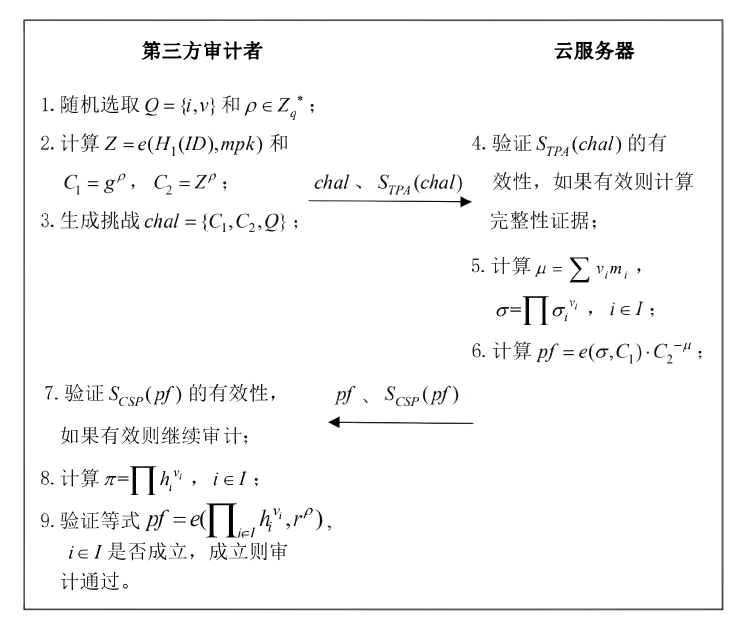
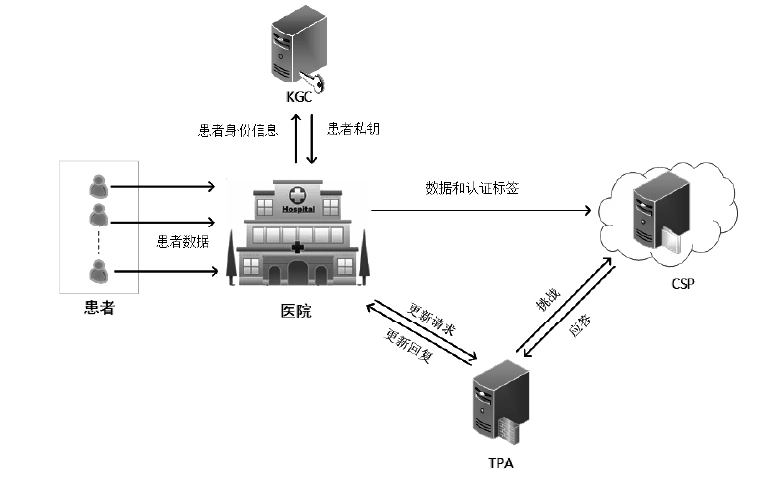
| [1] |
CHOO K K, DOMINGO F J, ZHANG Lei. Cloud Cryptography: Theory, Practice and Future Research Directions[J]. Future Generation Computer Systems, 2016, 62(9):51-53.
doi: 10.1016/j.future.2016.04.017
URL
|
| [2] |
GUO Chunmei, BI Xueyao, YANG Fan. Research and Trend of Cloud Computing SecurityTechnology[J]. Netinfo Security, 2010, 10(4):18-19.
|
|
郭春梅, 毕学尧, 杨帆. 云计算安全技术研究与趋势[J]. 信息网络安全, 2010, 10(4):18-19.
|
| [3] |
LI Yong, YAO GE, LEI Linan, et al. LBT-based Cloud Data Integrity Verification Scheme[J]. Journal of Tsinghua University(Science and Technology), 2016, 56(5):504-510.
|
|
李勇, 姚戈, 雷丽楠, 等. 基于多分支路径树的云存储数据完整性验证机制[J]. 清华大学学报:自然科学版, 2016, 56(5):504-510.
|
| [4] |
COPPOLINO L, D'ANTONIO S, MAZZEO G, et al. Cloud Security: Emerging Threats and Current Solutions[J]. Computers & Electrical Engineering, 2016, 59(4):124-140.
|
| [5] |
RAHMAN N H. A Survey of Information Security Incident Handling in the Cloud[J]. Computers & Security, 2015, 49(3):45-69.
doi: 10.1016/j.cose.2014.11.006
URL
|
| [6] |
JUELS A, KALISKI J B S. PoRs: Proofs of Retrievability for Large Files[C]// ACM. ACM Conference on Computer and Communications Security (CCS’ 07), October 28, 2007, Alexandria, Virginia, USA. New York: ACM Press, 2007: 584-597.
|
| [7] |
ATENIESE G, BURNS R, CURTMOLA R, et al. Provable Data Possession at Untrusted Stores[C]// ACM. ACM Conference on Computer and Communications Security (CCS’ 07), October 28, 2007, Alexandria, Virginia, USA. New York: ACM Press, 2007: 598-609.
|
| [8] |
WANG Qian, WANG Cong, REN Kui, et al. Enabling Public Auditability and Data Dynamics for Storage Security in Cloud Computing[J]. Parallel and Distributed Systems, IEEE Transactions, 2011, 22(5):847-859
doi: 10.1109/TPDS.2010.183
URL
|
| [9] |
WANG Tao, YANG Bo, LIU Hongyu, et al. An Alternative Approach to Public Cloud Data Auditing Supporting Data Dynamics[J]. Soft Computing, 2019, 23(13):4939-4953.
doi: 10.1007/s00500-018-3155-4
URL
|
| [10] |
GUO Wei, ZHANG Hua, QIN Sujuan, et al. Outsourced Dynamic Provable Data Possession with Batch Update for Secure Cloud Storage[J]. Future Generation Computer Systems, 2019, 95(6):309-322.
doi: 10.1016/j.future.2019.01.009
URL
|
| [11] |
GENTRY C, RAMZAN Z. Identity-based Aggregate Signatures[C]// Springer-verlag. Public Key Cryptography-PKC 2006, 9th International Conference on Theory and Practice of Public-Key Cryptography, April 24-26, 2006, New York, USA. Heidelberg: Springer, 2006: 257-273.
|
| [12] |
ZHAO Jining, XU Chunxiang, LI Fagen, et al. Identity-based Public Verification with Privacy-preserving for Data Storage Security in Cloud Computing[J]. Ieice Transactions on Fundamentals of Electronics Communications & Computer Sciences, 2013, 96(12):2709-2716.
|
| [13] |
WANG Huaqun, WU Qianhong, QIN Bo, et al. Identity-based Remote Data Possession Checking in Public Clouds[J]. IET Information Security, 2014, 8(2):114-121.
doi: 10.1049/ise2.v8.2
URL
|
| [14] |
WANG Huaqun. Identity-based Distributed Provable Data Possession in Multicloud Storage[J]. IEEE Transactions on Services Computing, 2015, 8(2):328-340.
doi: 10.1109/TSC.4629386
URL
|
| [15] |
YU Yong, XUE Liang, AUM H, et al. Cloud Data Integrity Checking with An Identity-based Auditing Mechanism from RSA[J]. Future Generation Computer Systems, 2016, 62(9):85-91.
doi: 10.1016/j.future.2016.02.003
URL
|
| [16] |
YU Yong, MH A, ATENIESE G, et al. Identity-based Remote Data Integrity Checking With Perfect Data Privacy Preserving for Cloud Storage[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(4):767-778.
doi: 10.1109/TIFS.2016.2615853
URL
|
| [17] |
RABANINEJAD R, RAJABZADEHASAAR M, AHMADIAN A M. et al. An identity-based Online/Offline Secure Cloud Storage Auditing Scheme[J]. Cluster Comput, 2020, 23(6):1455-1468.
doi: 10.1007/s10586-019-03000-5
URL
|
| [18] |
MERKLE R C. A Certified Digital Signature[C]// Springer. Advances in Cryptology-CRYPTO ’89, 9th Annual International Cryptology Conference, August 20-24, 1989, Santa Barbara, California, USA. New York: Springer-Verlag, 1989: 218-238.
|
 )
)