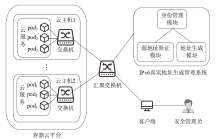
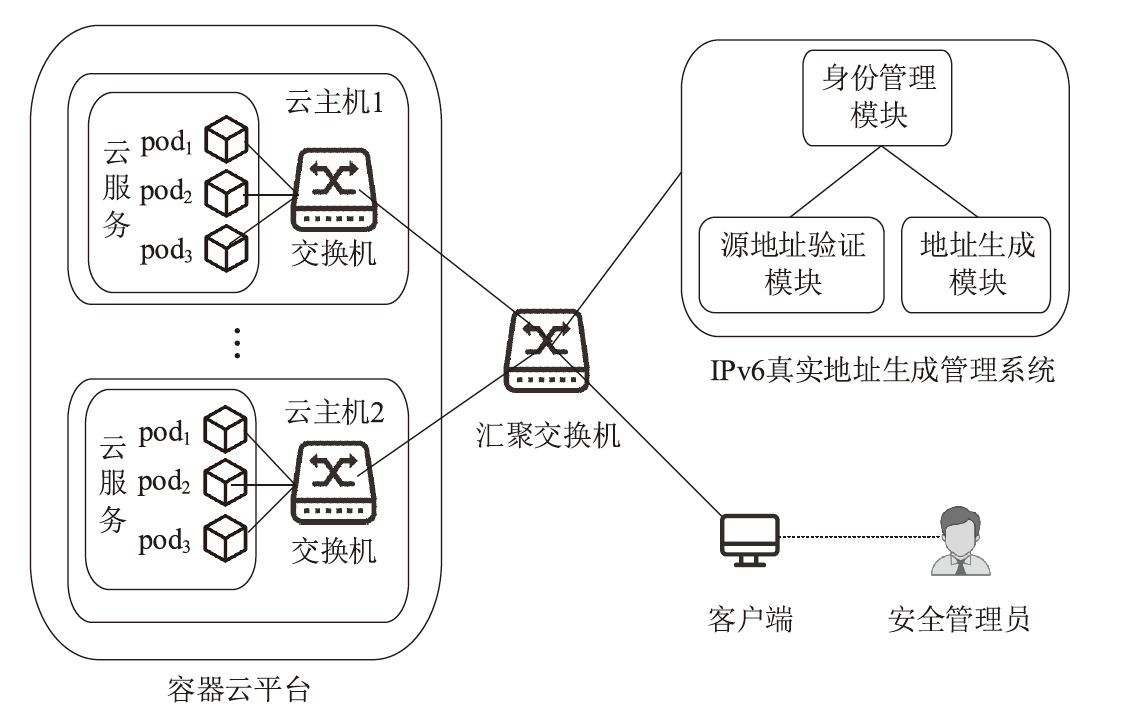
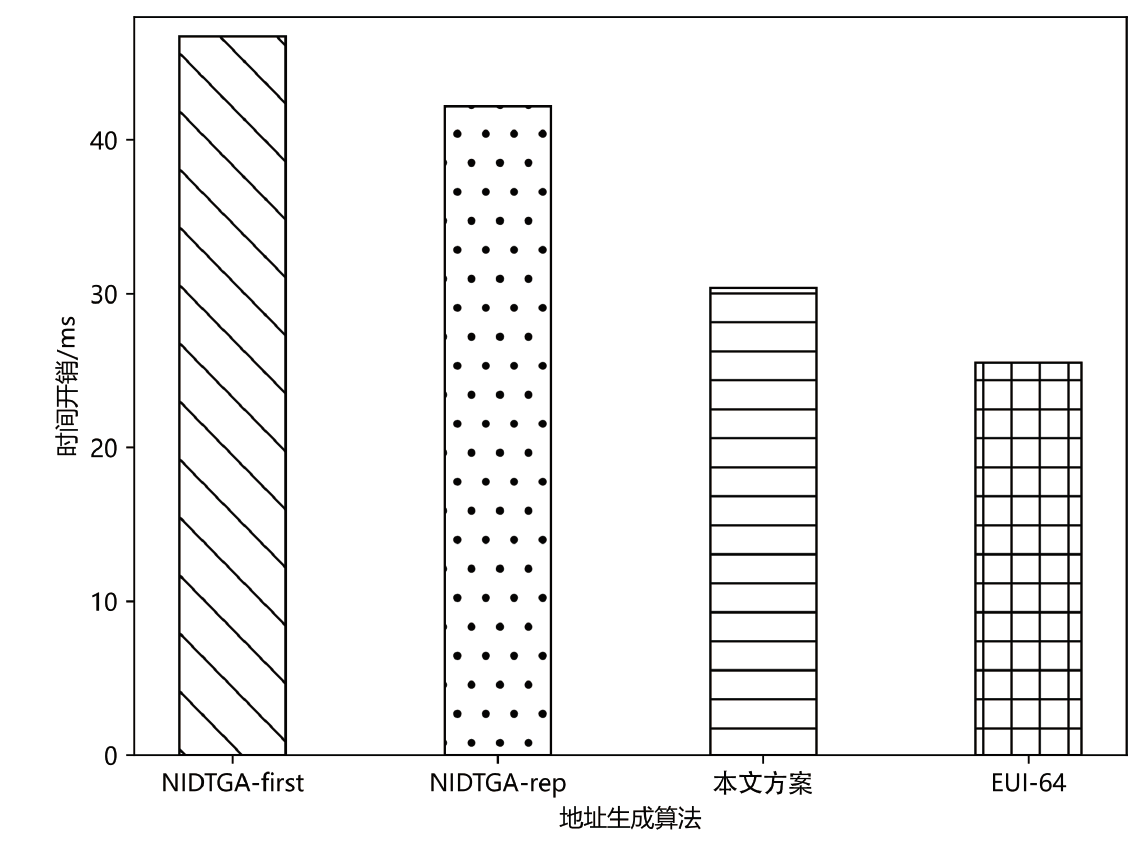
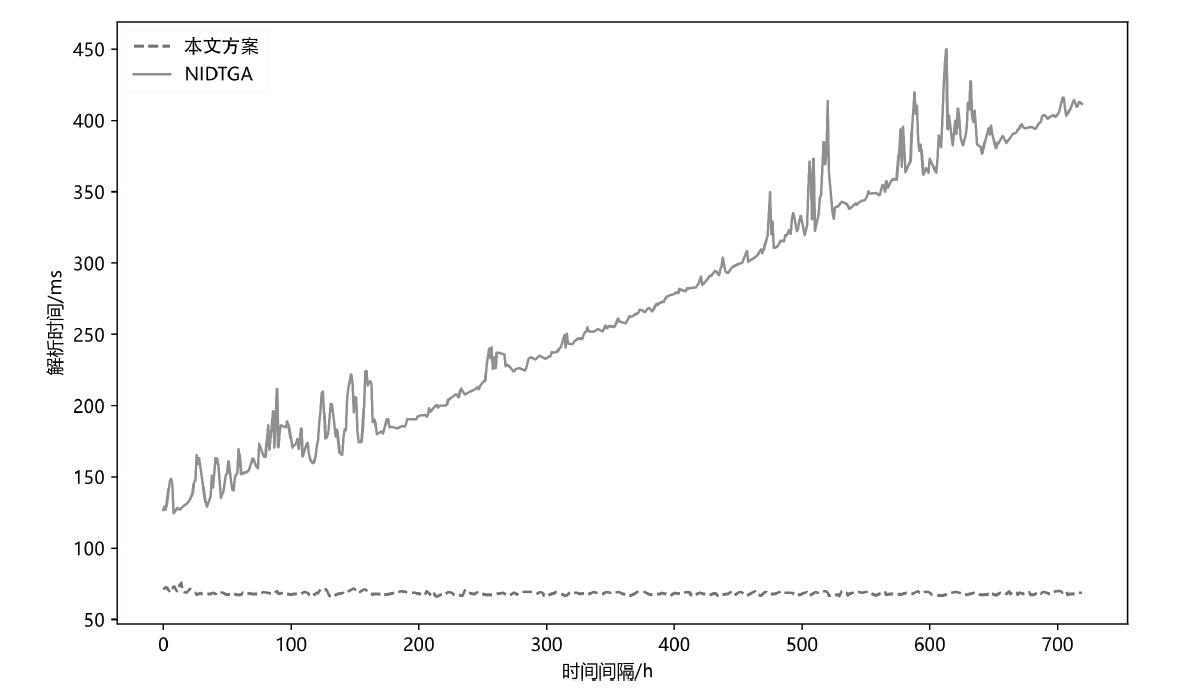
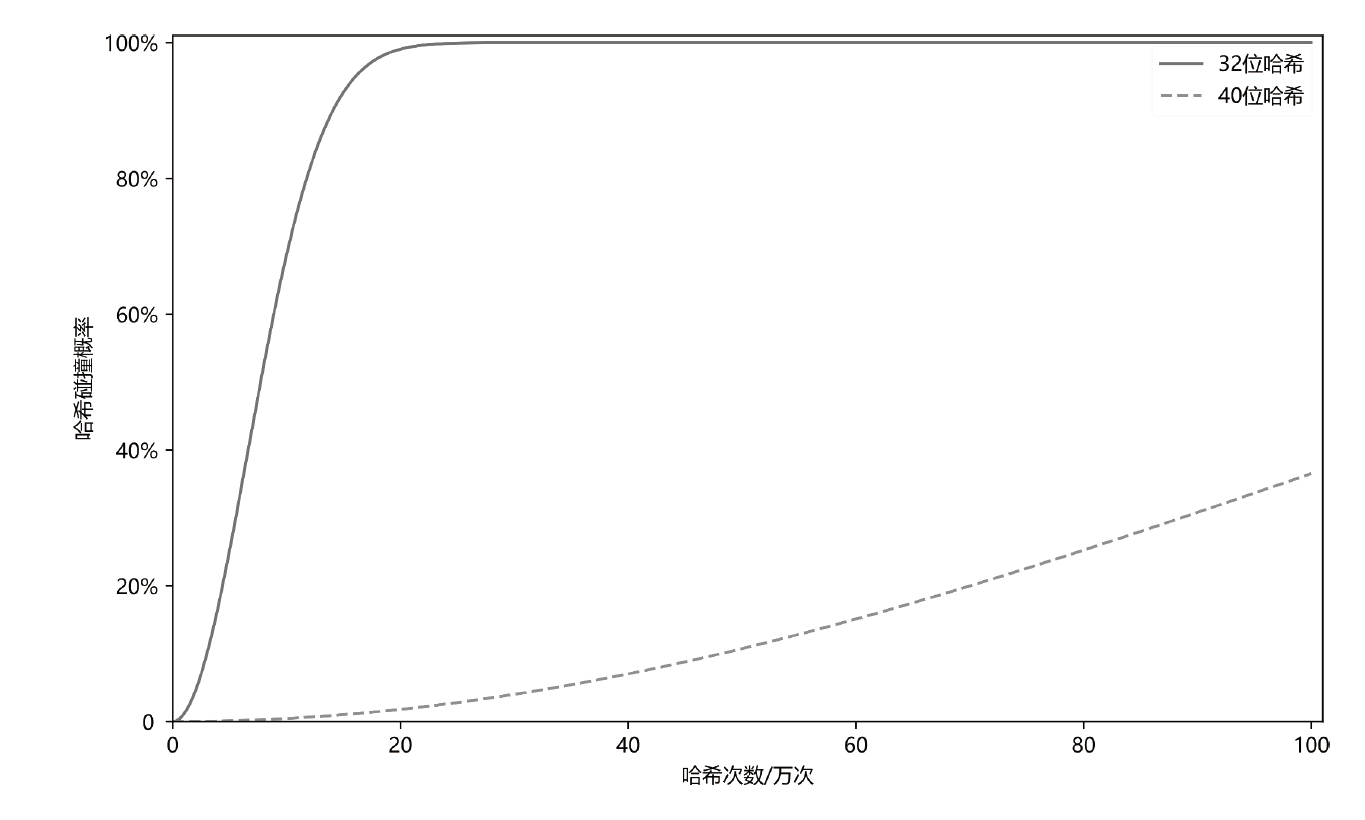
Netinfo Security ›› 2023, Vol. 23 ›› Issue (12): 21-28.doi: 10.3969/j.issn.1671-1122.2023.12.003
Previous Articles Next Articles
Endogenous Security Methods for Container Cloud Based on IPv6
LI Dong1, YU Junqing1,2( ), WEN Ruibin2, XIE Yiding2
), WEN Ruibin2, XIE Yiding2
- 1. Network and Computation Center, Huazhong University of Science and Technology, Wuhan 430074, China
2. School of Cyber Science and Engineering, Huazhong University of Science and Technology, Wuhan 430074, China
-
Received:2023-10-11Online:2023-12-10Published:2023-12-13
CLC Number:
Cite this article
LI Dong, YU Junqing, WEN Ruibin, XIE Yiding. Endogenous Security Methods for Container Cloud Based on IPv6[J]. Netinfo Security, 2023, 23(12): 21-28.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.12.003
| [1] | FERREIRA A P, SINNOTT R. A Performance Evaluation of Containers Running on Managed Kubernetes Services[C]// IEEE. 2019 IEEE International Conference on Cloud Computing Technology and Science(CloudCom). New York: IEEE, 2019: 199-208. |
| [2] | ORDABAYEVA G K, OTHMAN M, KIRGIZBAYEVA B, et al. A Systematic Review of Transition from IPV4 to IPV6[C]// ACM. 6th International Conference on Engineering & MIS 2020. New York: ACM, 2020: 1-15. |
| [3] | YUAN Lirong. Research on Practical Methods of Cyber Attack Tracing and Traceability[J]. China High and New Technology, 2022(23): 52-54. |
| 袁利荣. 网络攻击追踪溯源实践方法研究[J]. 中国高新科技, 2022(23):52-54. | |
| [4] | DE GUZMAN F E, GERARDO B D, MEDINA R P. Implementation of Enhanced Secure Hash Algorithm Towards a Secured Web Portal[C]// IEEE. 2019 IEEE 4th International Conference on Computer and Communication Systems(ICCCS). New York: IEEE, 2019: 189-192. |
| [5] | MOHAMED H, OULDMOHAMED Y, NACERA B. A Single-Packet IP Traceback: Combating DoS-DDoS Attacks[J]. EDPACS, 2022, 66(4): 1-12. |
| [6] | FAZIO P, TROPEA M, VOZNAK M, et al. On Packet Marking and Markov Modeling for IP Traceback: A Deep Probabilistic and Stochastic Analysis[EB/OL]. (2020-12-09)[2023-08-10]. https://www.sciencedirect.com/science/article/abs/pii/S1389128620311439. |
| [7] |
PATEL H, JINWALA D C. LPM: A Lightweight Authenticated Packet Marking Approach for IP Traceback[J]. Computer Networks, 2018, 140: 41-50.
doi: 10.1016/j.comnet.2018.04.014 URL |
| [8] |
NUR A Y, TOZAL M E. Record Route IP Traceback: Combating DoS Attacks and the Variants[J]. Computers & Security, 2018, 72: 13-25.
doi: 10.1016/j.cose.2017.08.012 URL |
| [9] |
MURUGESAN V, SELVARAJ M S, YANG M H. HPSIPT: A High-Precision Single-Packet IP Traceback Scheme[J]. Computer Networks, 2018, 143: 275-288.
doi: 10.1016/j.comnet.2018.07.013 URL |
| [10] | LIU Ying, REN Gang, WU Jianping, et al. Building an IPv6 Address Generation and Traceback System with NIDTGA in Address Driven Network[J]. Science China Information Sciences, 2015, 58(12): 1-14. |
| [11] |
KUANG Peng, LIU Ying, HE Lin, et al. IEEE 802.1x-Based User Identity-Embedded IPv6 Address Generation Scheme[J]. Telecommunications Science, 2019, 35 (12): 15-23.
doi: 10.11959/j.issn.1000-0801.2019289 |
|
况鹏, 刘莹, 何林, 等. 基于IEEE 802.1x的嵌入用户身份标识的IPv6地址生成方案[J]. 电信科学, 2019, 35(12):15-23.
doi: 10.11959/j.issn.1000-0801.2019289 |
|
| [12] | LI Zhitao, LIU Ying, REN Gang, et al. Non-Client Migration Scheme for IPv6 Address Generation System Based on Web Portal[J]. Journal of Southeast University(Natural Science Edition), 2017, 47(S1): 80-85. |
| 李智涛, 刘莹, 任罡, 等. IPv6地址生成系统基于Web Portal的无客户端迁移方案[J]. 东南大学学报(自然科学版), 2017, 47(S1):80-85. | |
| [13] |
LI Dan, QIN Lancheng, WU Jianping, et al. Internet Source Address Verification Method Based on Synchronization and Dynamic Filtering in Address Domain[J]. Telecommunications Science, 2020, 36(10): 21-28.
doi: 10.11959/j.issn.1000-0801.2020289 |
|
李丹, 秦澜城, 吴建平, 等. 基于边界路由动态同步的互联网地址域内真实源地址验证方法[J]. 电信科学, 2020, 36(10):21-28.
doi: 10.11959/j.issn.1000-0801.2020289 |
|
| [14] | WU Jiangxing. Mimetic Defense Technology to Build Endogenous Security of National Information Cyberspace[J]. Information and Communications Technologies, 2019, 13(6): 4-6. |
| 邬江兴. 拟态防御技术构建国家信息网络空间内生安全[J]. 信息通信技术, 2019, 13(6):4-6. | |
| [15] | XU Ke, FU Songtao, LI Qi, et al. The Research Progress on Intrinsic Internet Security Architecture[J]. Chinese Journal of Computers, 2021, 44(11): 2149-2172. |
| 徐恪, 付松涛, 李琦, 等. 互联网内生安全体系结构研究进展[J]. 计算机学报, 2021, 44(11):2149-2172. | |
| [16] | LUO Lunhan, LI Xiang, YU Xinsheng. Development and Application of Endogenous Security Technologies in Cyberspace in the Digital Era[J]. Electronic Technology & Software Engineering, 2021(19): 255-257. |
| 罗论涵, 李翔, 余新胜. 数字化时代网络空间内生安全技术发展与应用[J]. 电子技术与软件工程, 2021(19):255-257. | |
| [17] | LI Lingshu. Research on Key Technologies of Mimic SaaS Cloud Security Architecture[D]. Zhengzhou: PLA Strategic Support Force Information Engineering University, 2021. |
| 李凌书. 拟态SaaS云安全架构及关键技术研究[D]. 郑州: 战略支援部队信息工程大学, 2021. | |
| [18] | GUO Junli, XU Mingyang, YUAN Haoyu, et al. Introduction of Endogenous Security of Zero Trust Model[J]. Journal of Zhengzhou University(Natural Science Edition), 2022, 54(6): 51-58. |
| 郭军利, 许明洋, 原浩宇, 等. 引入内生安全的零信任模型[J]. 郑州大学学报(理学版), 2022, 54(6):51-58. | |
| [19] | DUNKELMAN O, KELLER N, RONEN E, et al. Quantum Time/Memory/Data Tradeoff Attacks[EB/OL]. [2023-08-10]. https://www.xueshufan.com/publication/3217041859. |
| [20] | ZONG Rui, DONG Xiaoyang, WANG Xiaoyun. Collision Attacks on Round-Reduced Gimli-Hash/Ascon-Xof/Ascon-Hash[EB/OL]. [2023-08-10]. https://www.xueshufan.com/publication/2982481869. |
| [1] | FU Jing. Exploration and Practice of Security Protection of Critical Information Infrastructure of Water Conservancy [J]. Netinfo Security, 2023, 23(8): 121-127. |
| [2] | SUN Chengcheng. Research on Countermeasures for Network Security Governance [J]. Netinfo Security, 2023, 23(6): 104-110. |
| [3] | SUN Pengyu, TAN Jinglei, LI Chenwei, ZHANG Hengwei. Network Security Defense Decision-Making Method Based on Time Differential Game [J]. Netinfo Security, 2022, 22(5): 64-74. |
| [4] | JIN Bo, TANG Qianjin, TANG Qianlin. Interpretation of the Top 10 Development Trends of Network Security in 2022 by CCF Computer Security Professional Committee [J]. Netinfo Security, 2022, 22(4): 1-6. |
| [5] | CHEN Yan, WEI Xiang, LU Zhen. Research on Testing Approaches for Network Security Products in Cloud Computing Environment [J]. Netinfo Security, 2022, 22(12): 1-6. |
| [6] | BAI Hongpeng, DENG Dongxu, XU Guangquan, ZHOU Dexiang. Research on Intrusion Detection Mechanism Based on Federated Learning [J]. Netinfo Security, 2022, 22(1): 46-54. |
| [7] | GU Zhaojun, YAO Feng, DING Lei, SUI He. Network Security Test of Airport Fuel Supply Automatic Control System Based on Semi-physical Object [J]. Netinfo Security, 2021, 21(9): 16-24. |
| [8] | ZHAO Xiaolin, ZHAO Bin, ZHAO Jingjing, XUE Jingfeng. Research on Network Security Measurement Method Based on Attack Identification [J]. Netinfo Security, 2021, 21(11): 17-27. |
| [9] | WU Jiaming, XIONG Yan, HUANG Wenchao, WU Jianshuang. A Distance-based Fuzzing Mutation Method [J]. Netinfo Security, 2021, 21(10): 63-68. |
| [10] | JIN Zhigang, WANG Xinjian, LI Gen, YUE Shunmin. The Generation Method of Network Defense Strategy Combining with Attack Graph and Game Model [J]. Netinfo Security, 2021, 21(1): 1-9. |
| [11] | DONG Qiang, LUO Guoming, SHI Hongkui, ZHANG Yongyue. Research on Authentication and Key Agreement Method of IMS-based Mobile Communication Private Network [J]. Netinfo Security, 2021, 21(1): 88-96. |
| [12] | LIU Daheng, LI Hongling. Research on QR Code Phishing Detection [J]. Netinfo Security, 2020, 20(9): 42-46. |
| [13] | LI Shibin, LI Jing, TANG Gang, LI Yi. Method of Network Security States Prediction and Risk Assessment for Industrial Control System Based on HMM [J]. Netinfo Security, 2020, 20(9): 57-61. |
| [14] | LAI Jiangliang, HOU Yifan, LU Xuming. Research on Comprehensive Effectiveness Analysis of Network Security System Based on Information Metrics and Loss [J]. Netinfo Security, 2020, 20(8): 81-88. |
| [15] | RAN Jinpeng, WANG Xiang, ZHAO Shanghong, GAO Hanghang. Virtual SDN Network Embedding Algorithm Based on Fruit Fly Optimization [J]. Netinfo Security, 2020, 20(6): 65-74. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||