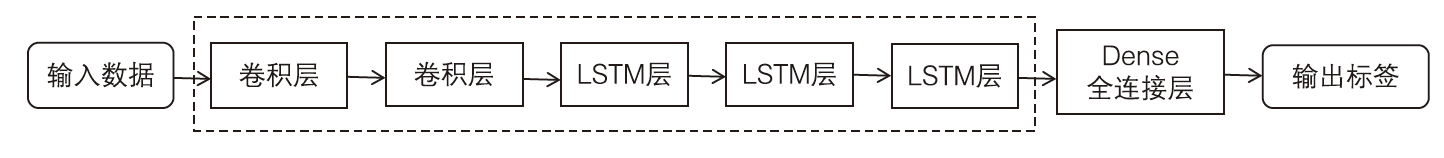
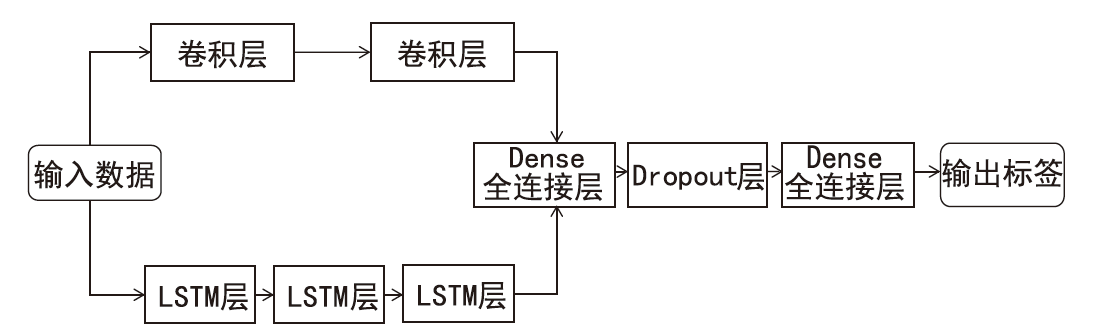
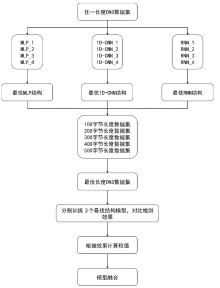
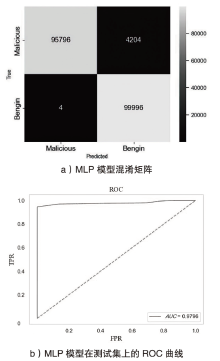
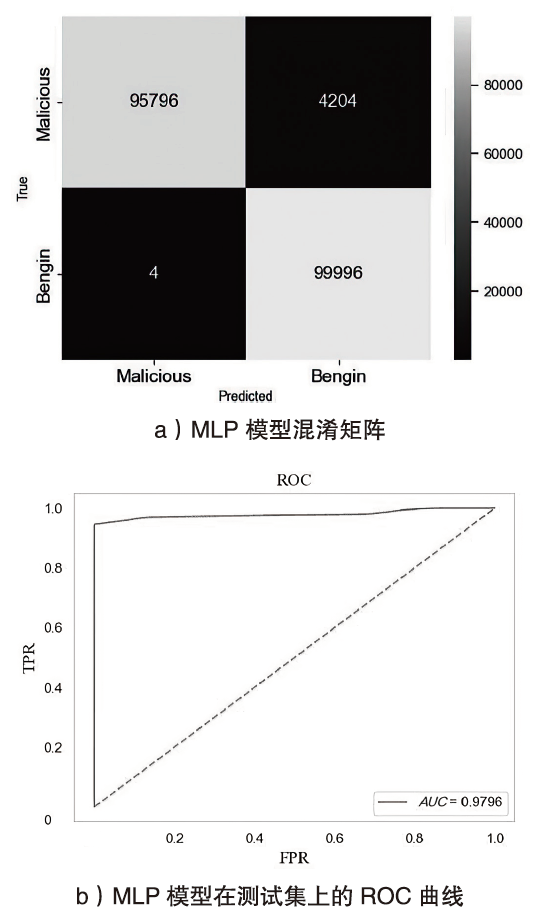
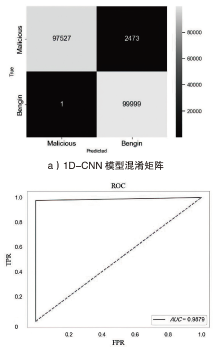
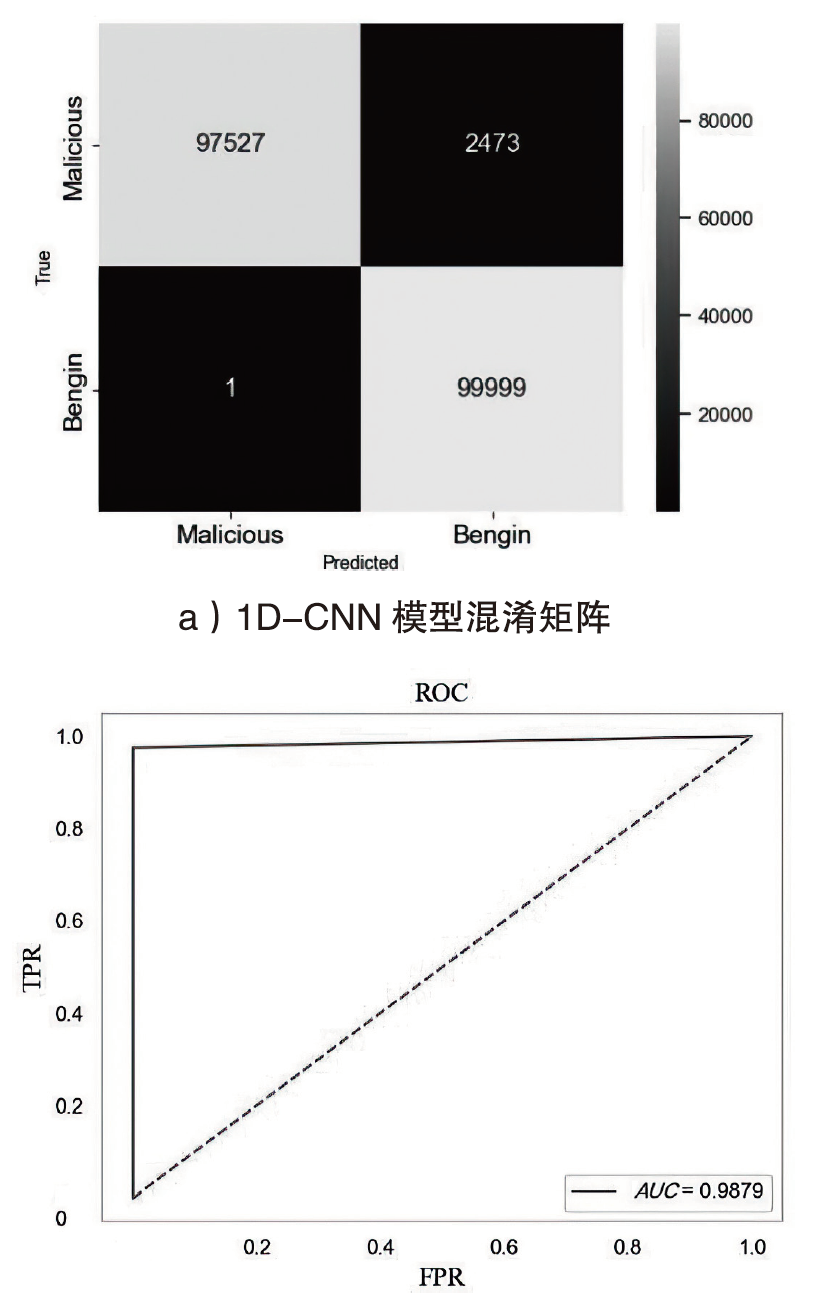
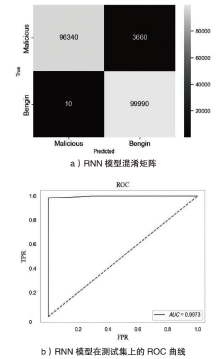
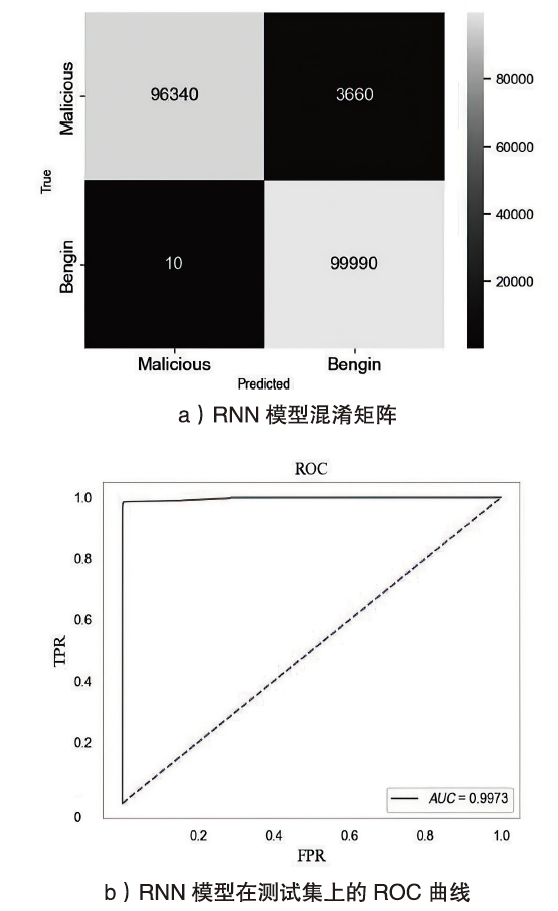
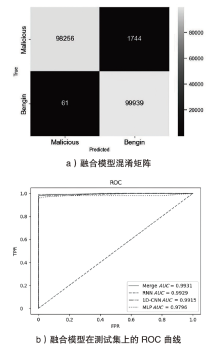
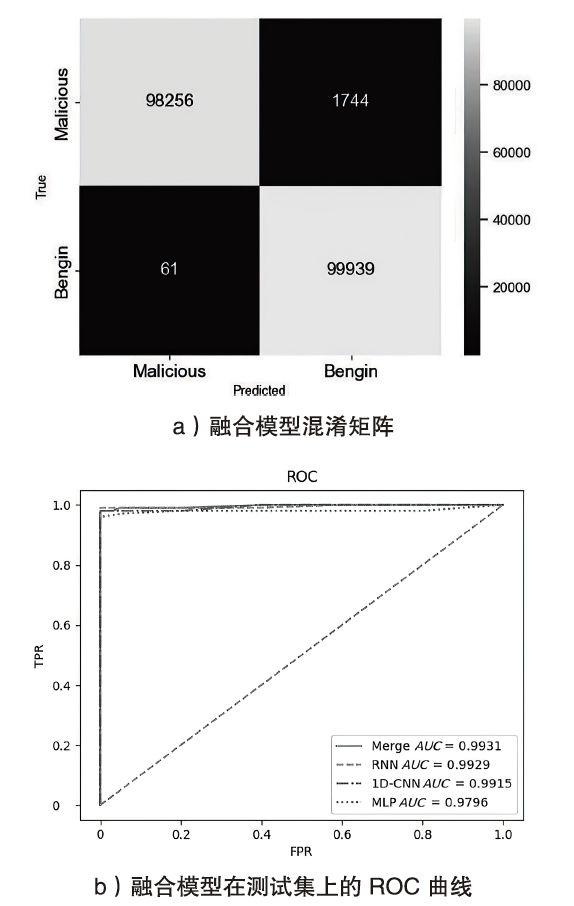
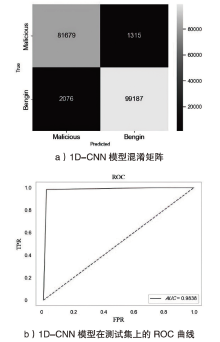
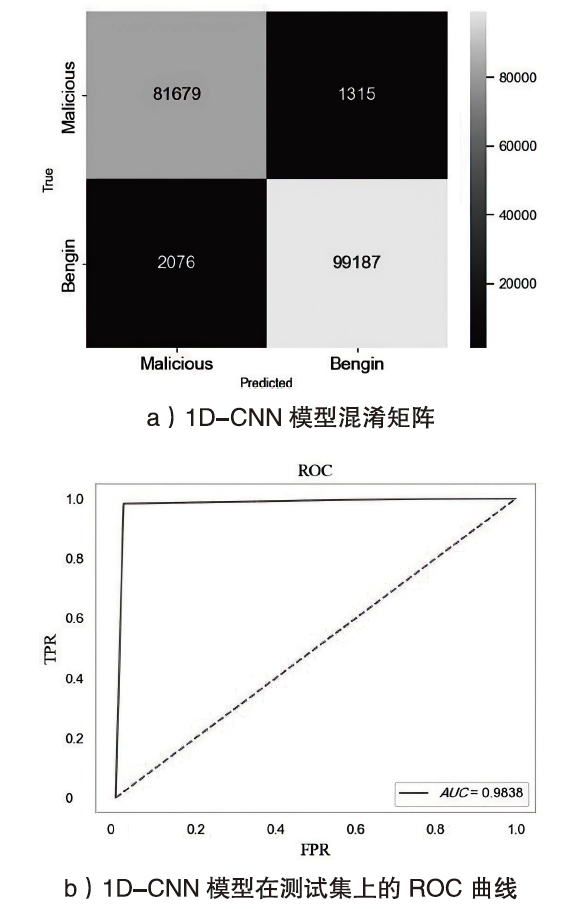
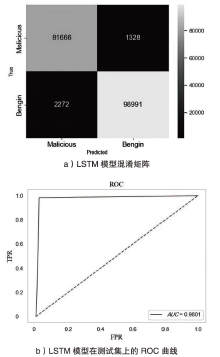
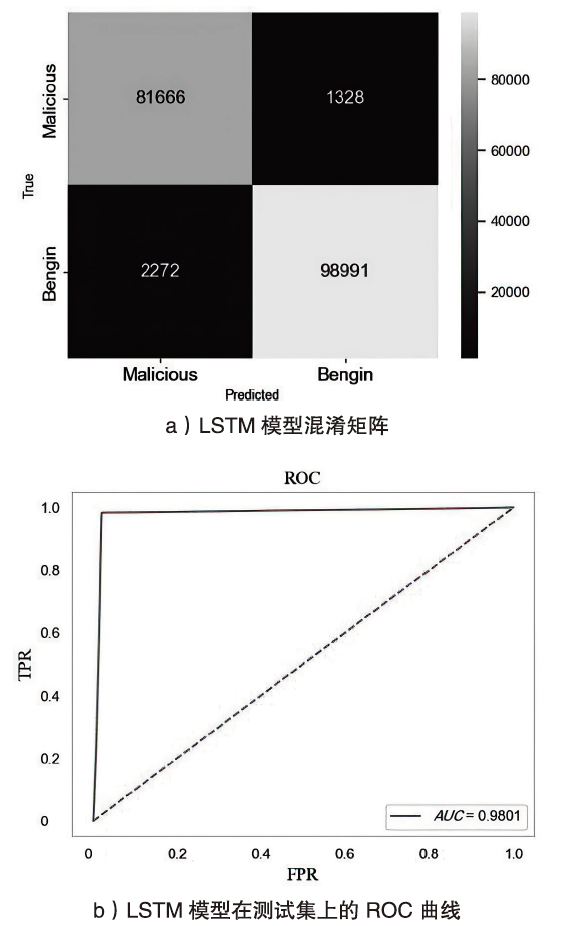
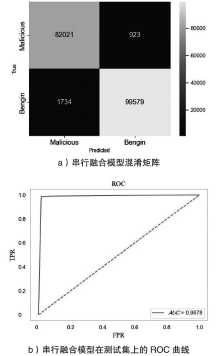
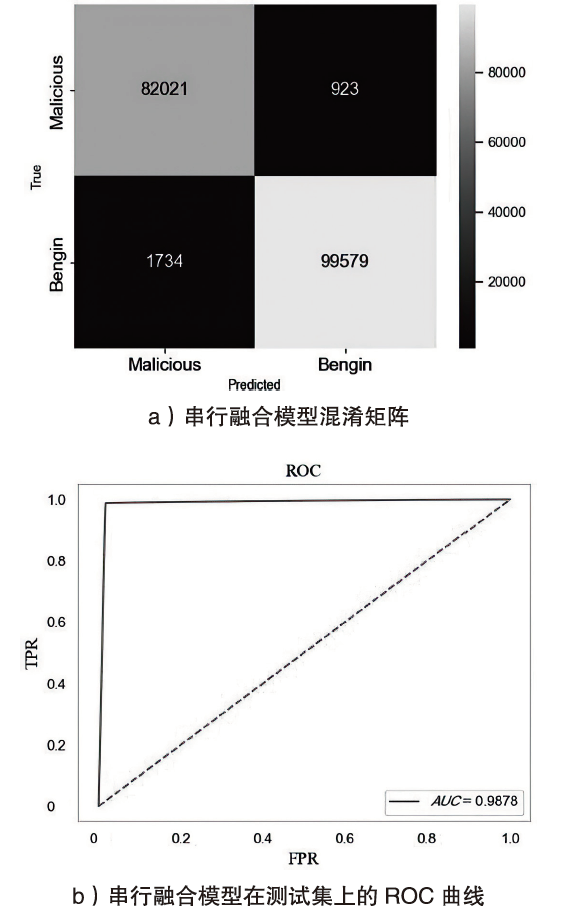
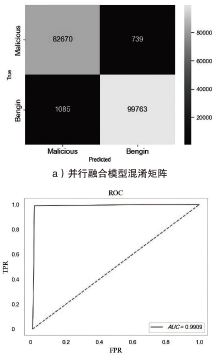
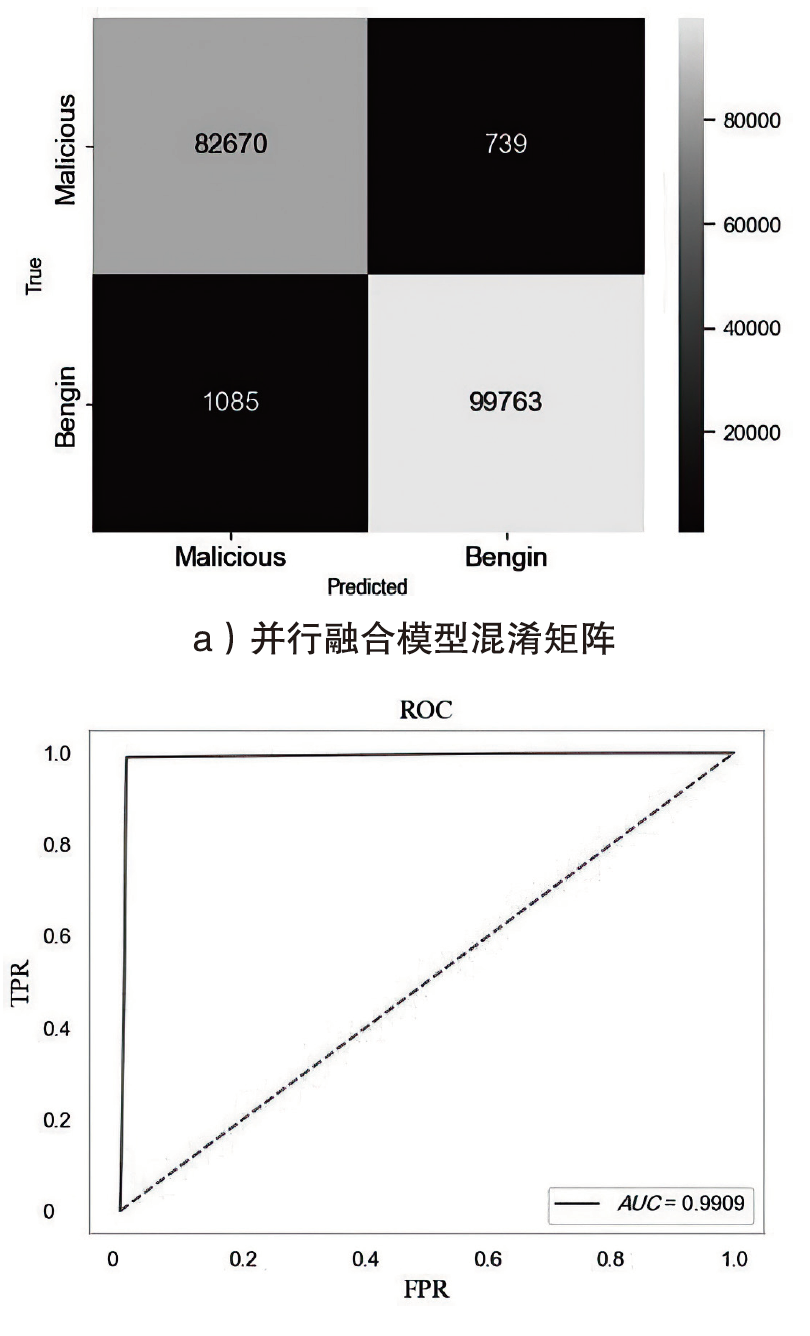
Netinfo Security ›› 2024, Vol. 24 ›› Issue (5): 694-708.doi: 10.3969/j.issn.1671-1122.2024.05.004
Previous Articles Next Articles
A Covert Tunnel and Encrypted Malicious Traffic Detection Method Based on Multi-Model Fusion
GU Guomin( ), CHEN Wenhao, HUANG Weida
), CHEN Wenhao, HUANG Weida
- College of Computer Science and Technology, Zhejiang University of Technology, Hangzhou 310023, China
-
Received:2023-12-07Online:2024-05-10Published:2024-06-24 -
Contact:GU Guomin E-mail:ggm@zjut.edu.cn
CLC Number:
Cite this article
GU Guomin, CHEN Wenhao, HUANG Weida. A Covert Tunnel and Encrypted Malicious Traffic Detection Method Based on Multi-Model Fusion[J]. Netinfo Security, 2024, 24(5): 694-708.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.05.004
| [1] |
REZAEI S, LIU XIN. Deep Learning for Encrypted Traffic Classification: An Overview[J]. IEEE Communications Magazine, 2019, 57(5): 76-81.
doi: 10.1109/MCOM.2019.1800819 |
| [2] | TANG Zhengzhi, ZENG Xuewen, GUO Zhichuan, et al. Malware Traffic Classification Based on Recurrence Quantification Analysis[J]. International Journal of Networking and Security, 2020, 22(3): 449-459. |
| [3] | WU Kemeng, ZHANG Yongzheng, TAO Yin. TDAE: Autoencoder-Based Automatic Feature Learning Method for the Detection of DNS Tunnel[C]// IEEE. 2020 IEEE International Conference on Communications (ICC)2020. New York: IEEE, 2020: 1-7. |
| [4] | YAN Chuyu, GAO Songfeng, WANG Baohui. Research on Encrypted Malicious Traffic Detection[J]. New Industrialization, 2021, 11(10): 59-61. |
| 闫楚玉, 高嵩峰, 王宝会. 加密恶意流量检测研究[J]. 新型工业化, 2021, 11(10):59-61. | |
| [5] | ANDERSON B, MCGREW D. Identifying Encrypted Malware Traffic with Contextual Flow Data[C]// ACM. Proceedings of the 2016 ACM Workshop on Artificial Intelligence and Security. New York: ACM, 2016: 35-46. |
| [6] | LI Yanmiao, GUO Hao, HOU Jiangang, et al. A Survey of Encrypted Malicious Traffic Detection[C]// IEEE. 2021 International Conference on Communications, Computing, Cybersecurity, and Informatics (CCCI). New York: IEEE, 2021: 1-7. |
| [7] | WANG Wei, ZHU Ming, ZENG Xuewen, et al. Malware Traffic Classification Using Convolutional Neural Network for Representation Learning[C]// IEEE. 2017 International Conference on Information Networking (ICOIN). New York: IEEE, 2017: 712-717. |
| [8] | RADIVILOVA T, KIRICHENKO L, AGEYEV D, et al. Decrypting SSL/TLS Traffic for Hidden Threats Detection[C]// IEEE. 2018 IEEE 9th International Conference on Dependable Systems, Services and Technologies (DESSERT). New York: IEEE, 2018: 143-146. |
| [9] | KILIC F, ECKERT C. iDeFEND: Intrusion Detection Framework for Encrypted Network Data[C]// Springer. Cryptology and Network Security. Heidelberg: Springer, 2015: 111-118. |
| [10] | ZHANG Han, PAPADOPOULOS C, MASSEY D. Detecting Encrypted Botnet Traffic[C]// IEEE. 2013 Proceedings IEEE INFOCOM. New York: IEEE, 2013: 3453-3458. |
| [11] | HU Bin. Research on Detection of Malicious SSL/TLS Encrypted Traffic[D]. Shanghai: Shanghai Jiao Tong University, 2020. |
| 胡斌. 恶意 SSL/TLS 加密流量检测研究[D]. 上海: 上海交通大学, 2020. | |
| [12] | SHEKHAWAT A S. Analysis of Encrypted Malicious Traffic[EB/OL]. (2018-05-18)[2023-09-05]. https://scholarworks.sjsu.edu/etd_projects/622/. |
| [13] | LEE I, ROH H, LEE W. Encrypted Malware Traffic Detection Using Incremental Learning[C]// IEEE. IEEE INFOCOM 2020-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York: IEEE, 2020: 1348-1349. |
| [14] | LI Li, REN Yifei, LOU Jiapeng. A Method for Malicious Encrypted Traffic Detection Based on Ensemble Learning[J]. Journal of Beijing Electronic Science and Technology Institute, 2021, 29(2): 8-16. |
| 李莉, 任逸飞, 娄嘉鹏. 一种基于集成学习的恶意加密流量检测方法[J]. 北京电子科技学院学报, 2021, 29(2):8-16. | |
| [15] | LUO Ziming, XU Shubin, LIU Xiaodong. A TLS Malicious Encrypted Traffic Detection Scheme Based on Machine Learning[J]. Journal of Network and Information Security, 2020, 6(1): 77-83. |
| 骆子铭, 许书彬, 刘晓东. 基于机器学习的TLS恶意加密流量检测方案[J]. 网络与信息安全学报, 2020, 6(1):77-83. | |
| [16] | JIANG Peng. Analysis and Detection of C&C Encrypted Channel Network Behavior Under APT Attacks[D]. Shanghai: Shanghai Normal University, 2018. |
| 姜鹏. APT 攻击下的 C&C 加密信道网络行为分析与检测[D]. 上海: 上海师范大学, 2018. | |
| [17] | PRASSE P, MACHLICA L, PEVNÝ T, et al. Malware Detection by Analysing Network Traffic with Neural Networks[C]// IEEE. 2017 IEEE Security and Privacy Workshops (SPW). New York: IEEE, 2017: 205-210. |
| [18] | CHEN Lin, JIANG Yixi, KUANG Xiaoyun, et al. Deep Learning Detection Method of Encrypted Malicious Traffic for Power Grid[C]// IEEE. 2020 IEEE International Conference on Energy Internet (ICEI). New York: IEEE, 2020: 86-91. |
| [19] | ZENG Yi, GU Huaxi, WEI Wenting, et al. $ Deep-Full-Range $: A Deep Learning Based Network Encrypted Traffic Classification and Intrusion Detection Framework[J]. IEEE Access, 2019, 7: 45182-45190. |
| [20] | WANG Yue, ZHOU Anmin, LIAO Shan, et al. A Comprehensive Survey on DNS Tunnel Detection[EB/OL]. (2021-10-09)[2023-09-07]. https://www.sciencedirect.com/science/article/pii/S1389128621003248. |
| [21] | CROTTI M, DUSI M, GRINGOLI F, et al. Detecting Http Tunnels with Statistical Mechanisms[C]// IEEE. 2007 IEEE International Conference on Communications. New York: IEEE, 2007: 6162-6168. |
| [22] | DUSI M, CROTTI M, GRINGOLI F, et al. Tunnel Hunter: Detecting Application-Layer Tunnels with Statistical Fingerprinting[J]. Computer Networks, 2009, 53(1): 81-97. |
| [23] | CASAS P, MAZEL J, OWEZARSKI P. MINETRAC: Mining Flows for Unsupervised Analysis & Semi-Supervised Classification[C]// IEEE. 2011 23rd International Teletraffic Congress (ITC). New York: IEEE, 2011: 87-94. |
| [24] | WANG Hao. Research on Anomaly DNS Traffic Detection Based on Machine Learning[D]. Nanjing: Nanjing University of Posts and Telecommunications, 2019. |
| 王浩. 基于机器学习的异常 DNS 流量检测研究[D]. 南京: 南京邮电大学, 2019. | |
| [25] | SAKARKAR G, KOLEKAR M K H, PAITHANKAR K, et al. Advance Approach for Detection of DNS Tunneling Attack from Network Packets Using Deep Learning Algorithms[J]. Advances in Distributed Computing and Artificial Intelligence Journal, 2021, 10(3): 241-266. |
| [26] | SHERIDAN S, KEANE A. Detection of DNS Based Covert Channels[EB/OL]. (2015-01-01)[2023-09-05]. https://www.researchgate.net/publication/282931276_Detection_of_DNS_based_covert_channels. |
| [27] | LIU Xiaolei, ZHANG Qiongyin, REN Lei, et al. Exploration of DNS Tunneling Trojan Detection Technology Based on Communication Behavior Analysis[J]. Science and Technology Information, 2018, 16(34): 17-18. |
| 刘晓蕾, 张琼尹, 任磊, 等. 基于通信行为分析的DNS隧道木马检测技术探究[J]. 科技资讯, 2018, 16(34):17-18. | |
| [28] | NADLER A, AMINOV A, SHABTAI A. Detection of Malicious and Low Throughput Data Exfiltration over the DNS Protocol[J]. Computers & Security, 2019, 80: 36-53. |
| [29] | QI Cheng, CHEN Xiaojun, XU Cui, et al. A Bigram Based Real Time DNS Tunnel Detection Approach[J]. Procedia Computer Science, 2013, 17: 852-860. |
| [30] | YU Bin, SMITH L, THREEFOOT M, et al. Behavior Analysis Based DNS Tunneling Detection and Classification with Big Data Technologies[C]// IoTBD. Behavior Analysis Based DNS Tunneling Detection and Classification with Big Data Technologies. Rome: IoTBD, 2016: 284-290. |
| [31] | CHEN Shaojie, LANG Bo, LIU Hongyu, et al. DNS Covert Channel Detection Method Using the LSTM Model[EB/OL]. (2021-01-28)[2023-09-05]. https://www.sciencedirect.com/science/article/pii/S0167404820303680. |
| [32] | WANG Qi, XIE Kun, MA Yan, et al. DNS Tunnel Detection Based on Log Statistical Features[J]. Journal of Zhejiang University (Engineering Science), 2020, 54(9): 1753-1760. |
| 王琪, 谢坤, 马严, 等. 基于日志统计特征的 DNS 隧道检测[J]. 浙江大学学报(工学版), 2020, 54(9):1753-1760. | |
| [33] | LIN Huaqing, LIU Gao, YAN Zheng. Detection of Application-Layer Tunnels with Rules and Machine Learning[C]// Springer. International Conference on Security, Privacy and Anonymity in Computation, Communication and Storage. Heidelberg: Springer, 2019: 441-455. |
| [34] |
ZHANG Meng, SUN Haoliang, YANG Peng. DNS Covert Channel Recognition Based on Improved Convolutional Neural Network[J]. Journal on Communications, 2020, 41(1): 169-179.
doi: 10.11959/j.issn.1000-436x.2020017 |
|
张猛, 孙昊良, 杨鹏. 基于改进卷积神经网络识别 DNS 隐蔽信道[J]. 通信学报, 2020, 41(1):169-179.
doi: 10.11959/j.issn.1000-436x.2020017 |
|
| [35] | FARNHAM G, ATLASIS A. Detecting DNS Tunneling[J]. SANS Institute InfoSec Reading Room, 2013, 9: 1-32. |
| [36] | CHEN Yang, LI Xiaoyong. A High Accuracy DNS Tunnel Detection Method without Feature Engineering[C]// IEEE. 2020 16th International Conference on Computational Intelligence and Security (CIS). New York: IEEE, 2020: 374-377. |
| [37] | GARCIA S, GRILL M, STIBOREK J, et al. An Empirical Comparison of Botnet Detection Methods[J]. Computers & Security, 2014, 45: 100-123. |
| [1] | WEN Weiping, ZHANG Shichen, WANG Han, SHI Lin. Linux Malicious Application Detection Scheme Based on Virtual Machine Introspection [J]. Netinfo Security, 2024, 24(5): 657-666. |
| [2] | LI Zhihua, CHEN Liang, LU Xulin, FANG Zhaohui, QIAN Junhao. Lightweight Detection Method for IoT Mirai Botnet [J]. Netinfo Security, 2024, 24(5): 667-681. |
| [3] | YANG Zhipeng, WANG Juan, MA Chenjun, KANG Yunfeng. Python Sandbox Escape Defense Mechanism Based on Third-Party Library Isolation [J]. Netinfo Security, 2024, 24(5): 682-693. |
| [4] | SHEN Zhuowei, WANG Renbo, SUN Xianjun. A Hierarchical Lightweight Authentication Scheme Based on Merkle Tree and Hash Chain [J]. Netinfo Security, 2024, 24(5): 709-718. |
| [5] | TIAN Zhao, NIU Yajie, SHE Wei, LIU Wei. A Reputation Evaluation Method for Vehicle Nodes in V2X [J]. Netinfo Security, 2024, 24(5): 719-731. |
| [6] | SHI Runhua, DENG Jiapeng, YU Hui, KE Weiyang. Electronic Voting Scheme Based on Public Key Cryptography of Quantum Walks [J]. Netinfo Security, 2024, 24(5): 732-744. |
| [7] | GUO Jiansheng, GUAN Feiting, LI Zhihui. A Dynamic (t,n) Threshold Quantum Secret Sharing Scheme with Cheating Identification [J]. Netinfo Security, 2024, 24(5): 745-755. |
| [8] | LI Yuxin, HUANG Wenchao, WANG Jionghan, XIONG Yan. Analysis Method of Monero Payment Protocol Based on Tamarin [J]. Netinfo Security, 2024, 24(5): 756-766. |
| [9] | ZHANG Shuya, CHEN Liangguo, CHEN Xingshu. An Automatic Discovery Method for Heuristic Log Templates [J]. Netinfo Security, 2024, 24(5): 767-777. |
| [10] | ZHANG Changlin, TONG Xin, TONG Hui, YANG Ying. A Survey of Large Language Models in the Domain of Cybersecurity [J]. Netinfo Security, 2024, 24(5): 778-793. |
| [11] | WANG Wei, HU Yongtao, LIU Qingtao, WANG Kailun. Research on Softwaization Techniques for ERT Trusted Root Entity in Railway Operation Environment [J]. Netinfo Security, 2024, 24(5): 794-801. |
| [12] | GUO Zimeng, ZHU Guangjie, YANG Yijie, SI Qun. Research on Railway Network Security Performance Based on APT Characteristics [J]. Netinfo Security, 2024, 24(5): 802-811. |
| [13] | ZHANG Hao, XIE Dazhi, HU Yunsheng, YE Junwei. A Review of Network Anomaly Detection Based on Semi-Supervised Learning [J]. Netinfo Security, 2024, 24(4): 491-508. |
| [14] | WANG Jian, CHEN Lin, WANG Kailun, LIU Jiqiang. Application Layer DDoS Detection Method Based on Spatio-Temporal Graph Neural Network [J]. Netinfo Security, 2024, 24(4): 509-519. |
| [15] | TU Xiaohan, ZHANG Chuanhao, LIU Mengran. Design and Implementation of Malicious Traffic Detection Model [J]. Netinfo Security, 2024, 24(4): 520-533. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||