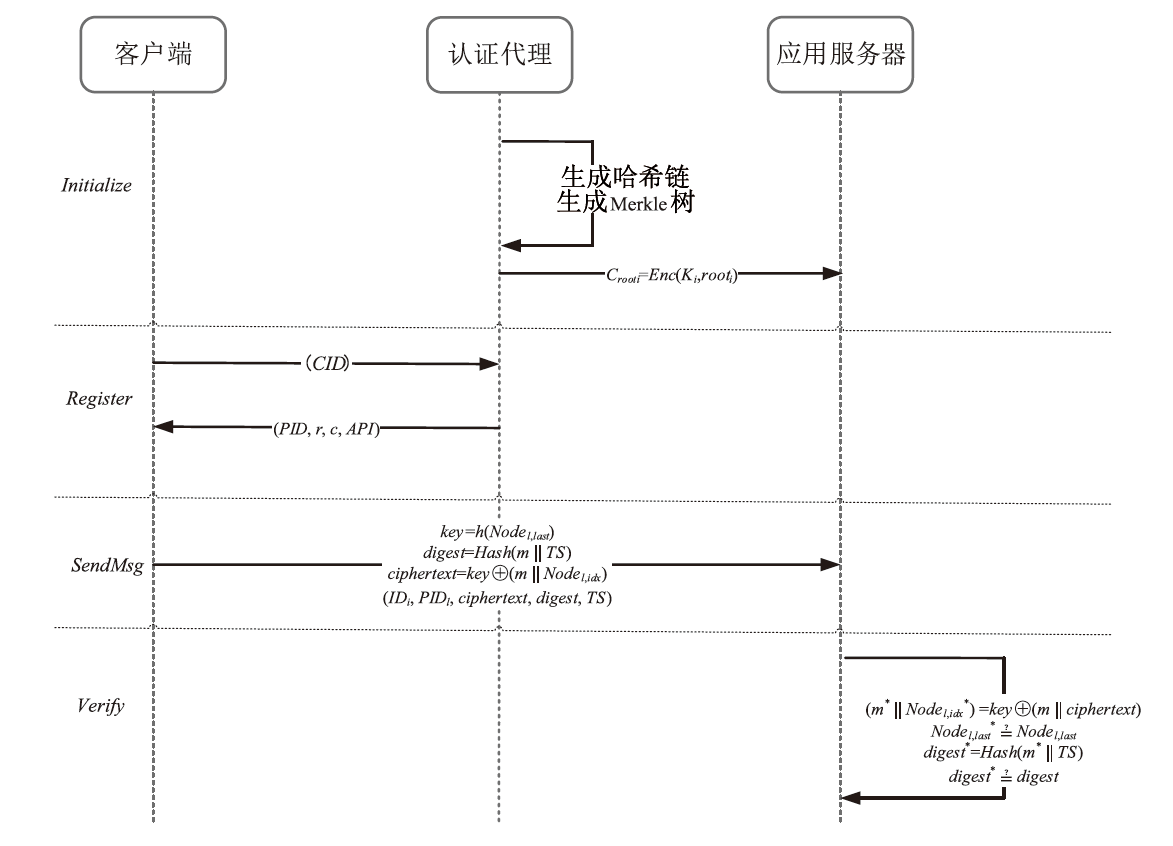
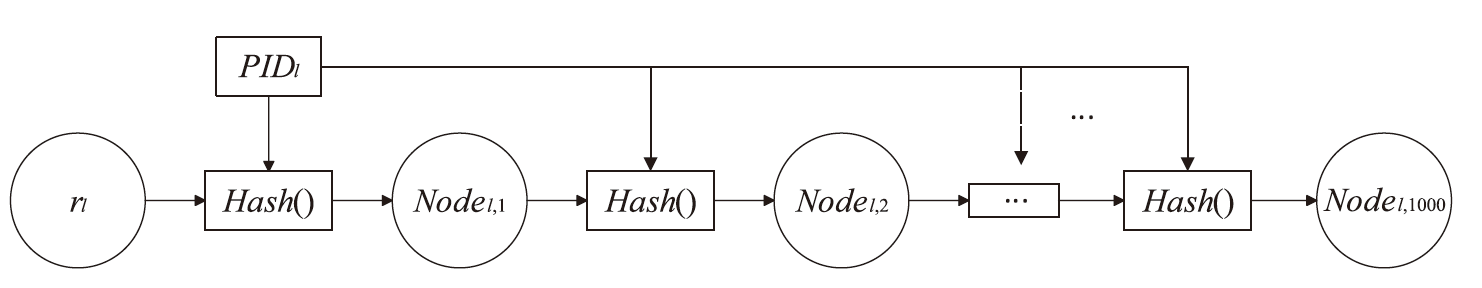
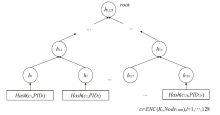
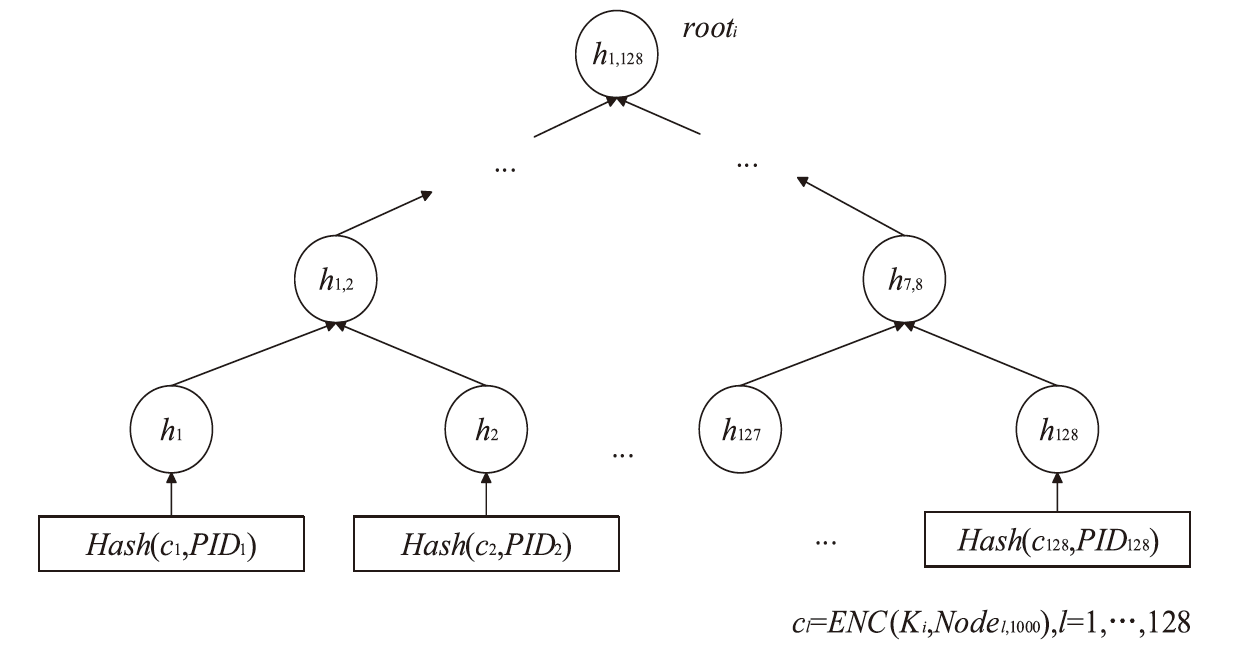
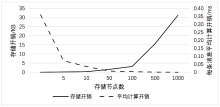
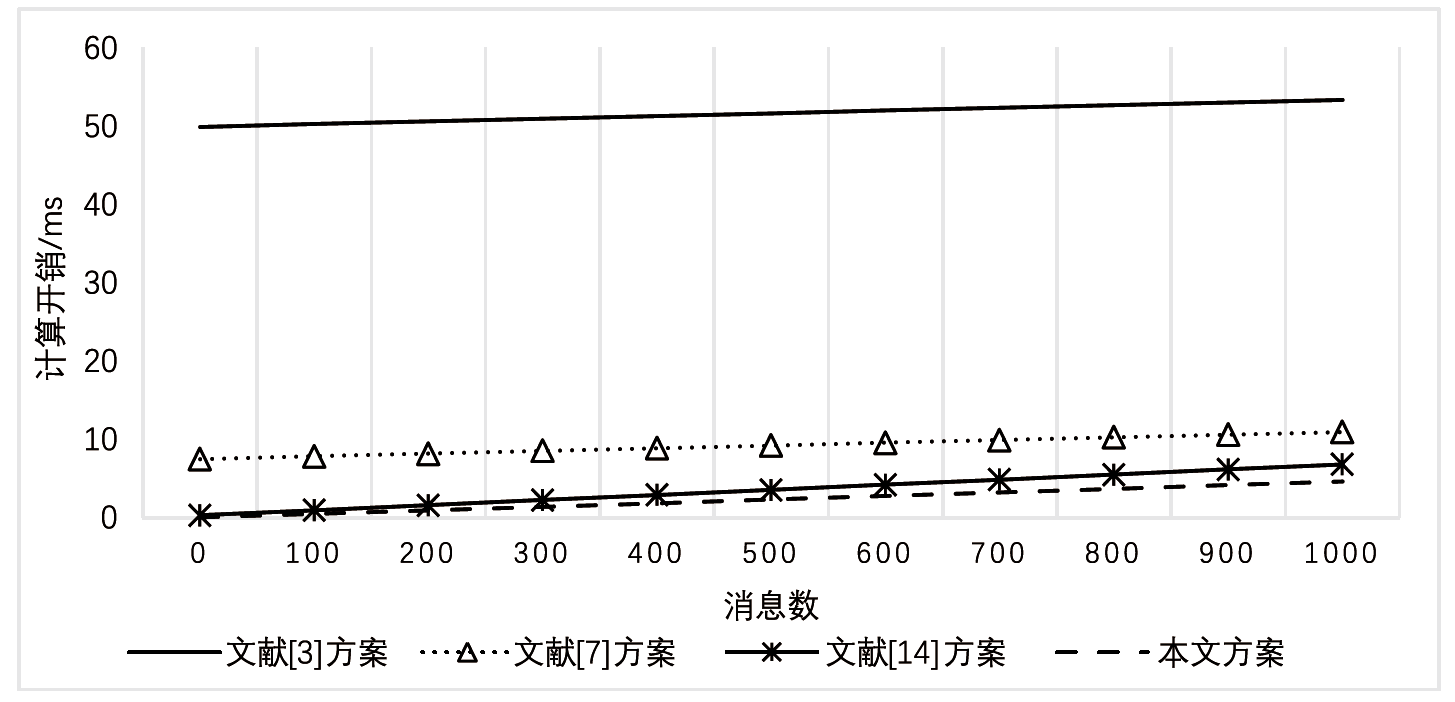
Netinfo Security ›› 2024, Vol. 24 ›› Issue (5): 709-718.doi: 10.3969/j.issn.1671-1122.2024.05.005
Previous Articles Next Articles
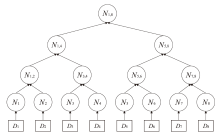
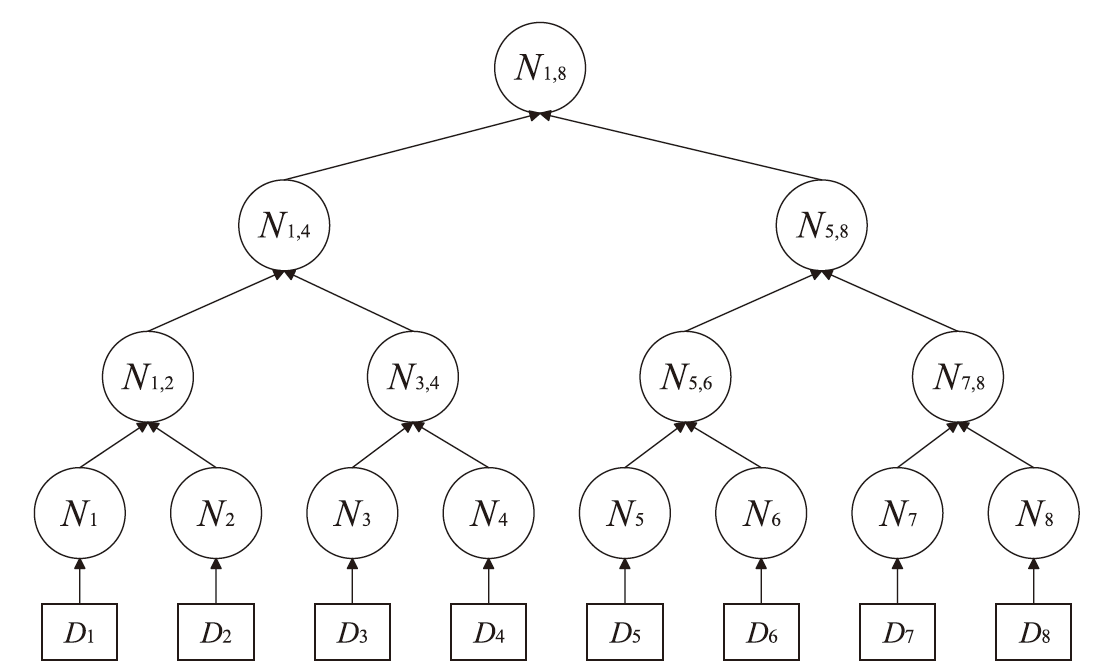
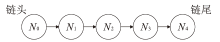
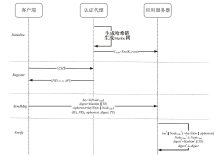
A Hierarchical Lightweight Authentication Scheme Based on Merkle Tree and Hash Chain
SHEN Zhuowei1,2, WANG Renbo1,2, SUN Xianjun3( )
)
- 1. School of Cyber Science and Engineering, Southeast University, Nanjing 211189, China
2. Key Laboratory of Computer Network and Information Integration of Ministry of Education, Southeast University, Nanjing 211189, China
3. Security and Preventive Technology Division, The Third Research Institute of Ministry of Public Security, Shanghai 200031, China
-
Received:2024-03-06Online:2024-05-10Published:2024-06-24 -
Contact:SUN Xianjun E-mail:sxj_sun8110@163.com
CLC Number:
Cite this article
SHEN Zhuowei, WANG Renbo, SUN Xianjun. A Hierarchical Lightweight Authentication Scheme Based on Merkle Tree and Hash Chain[J]. Netinfo Security, 2024, 24(5): 709-718.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.05.005
| 身份认证(密钥协商) | 消息认证 | |||
|---|---|---|---|---|
| 客户端 | 服务器 | 客户端 | 服务器 | |
| 文献[ | 4TGm+TGa+ 5TH+TAES-enc | 4TGm+TGa+5TH+ TAES-dec+2Tbp | TAES-enc+TH | TAES-dec+TH |
| 文献[ 方案 | TGm+TGa+TAES-enc+ TAES-dec+TH | TGm+TGa+TAES-enc+ TAES-dec+TH | TAES-enc+TH | TAES-dec+TH |
| 文献[ | 129TAES-enc+ 255TH | TAES-dec+TH | TXOR | TAES-dec+ TXOR+7TH |
| 本文方案 | / | TAES-dec+7TH | TXOR+3TH | TXOR+3TH |
| [1] | YICK J, MUKHERJEE B, GHOSAL D. Wireless Sensor Network Survey[J]. Computer Networks, 2008, 52: 2292-2330. |
| [2] | BHUIYAN M N, RAHMAN M M, BILLAH M M, et al. Internet of Things (IoT): A Review of Its Enabling Technologies in Healthcare Applications, Standards Protocols, Security, and Market Opportunities[J]. IEEE Internet of Things Journal, 2021, 8(13): 10474-10498. |
| [3] | HE Debiao, ZEADALLY S, KUMAR N, et al. Anonymous Authentication for Wireless Body Area Networks with Provable Security[J]. IEEE Systems Journal, 2016, 11(4): 2590-2601. |
| [4] |
GUO Songhui, NIU Xiaopeng, WANG Yulong. Elliptic Curve Based Light-Weight Authentication and Key Agreement Scheme[J]. Computer Science, 2015, 42(1): 137-141.
doi: 10.11896/j.issn.1002-137X.2015.01.032 |
|
郭松辉, 牛小鹏, 王玉龙. 一种基于椭圆曲线的轻量级身份认证及密钥协商方案[J]. 计算机科学, 2015, 42(1): 137-141.
doi: 10.11896/j.issn.1002-137X.2015.01.032 |
|
| [5] |
CHANG Xiangmao, ZHAN Jun, WANG Zhiwei. Low-Cost Group-Based Identity Security Authentication Protocol for NB-IoT Nodes[J]. Journal on Communications, 2021, 42(12): 152-162.
doi: 10.11959/j.issn.1000-436x.2021228 |
|
常相茂, 占俊, 王志伟. 低开销的NB-IoT节点群组身份安全认证协议[J]. 通信学报, 2021, 42(12): 152-162.
doi: 10.11959/j.issn.1000-436x.2021228 |
|
| [6] | LI Tong, ZHOU Xiaoming, REN Shuai, et al. Light-Weight Mutual Authentication Protocol for Mobile Edge Computing[J]. Netinfo Security, 2021, 21(11): 58-64. |
| 李桐, 周小明, 任帅, 等. 轻量化移动边缘计算双向认证协议[J]. 信息网络安全, 2021, 21(11): 58-64. | |
| [7] | TAN Yawen, WANG Jiadai, LIU Jiajia, et al. Blockchain-Assisted Distributed and Lightweight Authentication Service for Industrial Unmanned Aerial Vehicles[J]. IEEE Internet of Things Journal, 2022, 9(18): 16928-16940. |
| [8] | KHASHAN O A, KHAFAJAH N M. Efficient Hybrid Centralized and Blockchain-Based Authentication Architecture for Heterogeneous IoT Systems[J]. Journal of King Saud University Computer and Information Sciences, 2023, 35(2): 726-739. |
| [9] | DEBNATH S, CHATTOPADHYAY A, DUTTA S. Brief Review on Journey of Secured Hash Algorithms[C]// IEEE. 2017 4th International Conference on Opto-Electronics and Applied Optics (Optronix). New York: IEEE, 2017: 1-5. |
| [10] | PINTO A, COSTA R. Hash-Chain-Based Authentication for IoT[J]. ADCAIJ: Advances in Distributed Computing and Artificial Intelligence Journal, 2016, 5(4): 43-57. |
| [11] | MASUD M, GABA G S, CHOUDHARY K, et al. Lightweight and Anonymity-Preserving User Authentication Scheme for IoT-Based Healthcare[J]. IEEE Internet of Things Journal, 2021, 9(4): 2649-2656. |
| [12] | YIN Xinming, HE Junhui, GUO Yi, et al. An Efficient Two-Factor Authentication Scheme Based on the Merkle Tree[J]. Sensors, 2020, 20(20): 5735-5753. |
| [13] | WANG Chengyu, DING Wang, DUAN Yihe, et al. Secure and Lightweight User Authentication Scheme for Cloud-Assisted Internet of Things[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 2961-2976. |
| [14] | LI Hongwei, LU Rongxing, ZHOU Liang, et al. An Efficient Merkle-Tree-Based Authentication Scheme for Smart Grid[J]. IEEE Systems Journal, 2013, 8(2): 655-663. |
| [15] | Merkle R C. Protocols for Public Key Cryptosystems[C]// IEEE. 1980 IEEE Symposium on Security and Privacy. New York: IEEE, 1980: 122-132. |
| [16] | JING Shimin, ZHENG Xin, CHEN Zhengwen. Review and Investigation of Merkle Tree’s Technical Principles and Related Application Fields[C]// IEEE. 2021 International Conference on Artificial Intelligence, Big Data and Algorithms (CAIBDA). New York: IEEE, 2021: 86-90. |
| [17] | LAMPORT L. Password Authentication with Insecure Communication[J]. Communications of the ACM, 1981, 24(11): 770-772. |
| [18] | MARTINO R, CILARDO A. SHA-2 Acceleration Meeting the Needs of Emerging Applications: A Comparative Survey[J]. IEEE Access, 2020, 8: 28415-28436. |
| [1] | SHI Runhua, YANG Jingyi, WANG Pengbo, LIU Huawei. Online/Off line Cross-Domain Identity Authentication Scheme Based on Blockchain in Vehicle to Grid [J]. Netinfo Security, 2024, 24(4): 587-601. |
| [2] | ZHAI Peng, HE Jingsha, ZHANG Yu. An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment [J]. Netinfo Security, 2024, 24(2): 179-187. |
| [3] | ZHANG Min, FENG Yongqiang, XU Chunxiang, ZHANG Jianhua. Research on Multi-Factor Authenticated Key Agreement Protocol for Smart Home Networks [J]. Netinfo Security, 2024, 24(1): 133-142. |
| [4] | DAI Yu, ZHOU Fei, XUE Dan. Handover Authentication Protocol Based on Chinese Remainder Theorem Secret Sharing [J]. Netinfo Security, 2023, 23(9): 118-128. |
| [5] | ZHANG Wei, LI Zixuan, XU Xiaoyu, HUANG Haiping. SDP-CoAP: Design of Security Enhanced CoAP Communication Framework Based on Software Defined Perimeter [J]. Netinfo Security, 2023, 23(8): 17-31. |
| [6] | TAN Weijie, YANG Yuting, NIU Kun, PENG Changgen. MI-PUF-Based Secure Authentication Protocol for V2X Communication [J]. Netinfo Security, 2023, 23(12): 38-48. |
| [7] | ZHANG Min, XU Chunxiang, ZHANG Jianhua. Research on Authentication Key Agreement Protocol Based on Multi-Factor in Internet of Drones [J]. Netinfo Security, 2022, 22(9): 21-30. |
| [8] | ZHANG Xuewang, LIU Yufan. Identity Traceable Anonymous Authentication Scheme for Nodes in the Perception Layer of IoT [J]. Netinfo Security, 2022, 22(9): 55-62. |
| [9] | LIU Xin, LI Yunyi, WANG Miao. A Lightweight Authentication Protocol Based on Confidential Computing for Federated Learning Nodes [J]. Netinfo Security, 2022, 22(7): 37-45. |
| [10] | WANG Shushuang, MA Zhaofeng, LIU Jiawei, LUO Shoushan. Research and Implementation of Cross-Chain Security Access and Identity Authentication Scheme of Blockchain [J]. Netinfo Security, 2022, 22(6): 61-72. |
| [11] | SHI Runhua, WANG Shuhao, LI Kunchang. A Lightweight Cross-domain Mutual Authentication Scheme in V2G Networks [J]. Netinfo Security, 2022, 22(3): 20-28. |
| [12] | WU Kehe, CHENG Rui, JIANG Xiaochen, ZHANG Jiyu. Security Protection Scheme of Power IoT Based on SDP [J]. Netinfo Security, 2022, 22(2): 32-38. |
| [13] | ZHANG Yu, SUN Guangmin, ZHAI Peng, LI Yu. A Provably Secure Traceability Authentication Protocol Based on Chebyshev Chaotic Map [J]. Netinfo Security, 2022, 22(12): 25-33. |
| [14] | LIU Xin, WANG Jiayin, YANG Haorui, ZHANG Ruisheng. An Internet of Vehicles Authentication Protocol Based on Blockchain and secGear Framework [J]. Netinfo Security, 2022, 22(1): 27-36. |
| [15] | LI Tong, REN Shuai, WANG Gang, MENG Qingyu. Cloud-edge-device Collaborative Integrity Verification Scheme Based on Chameleon Authentication Tree for Streaming Data [J]. Netinfo Security, 2022, 22(1): 37-45. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||