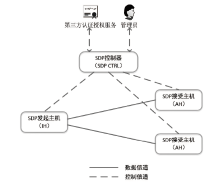
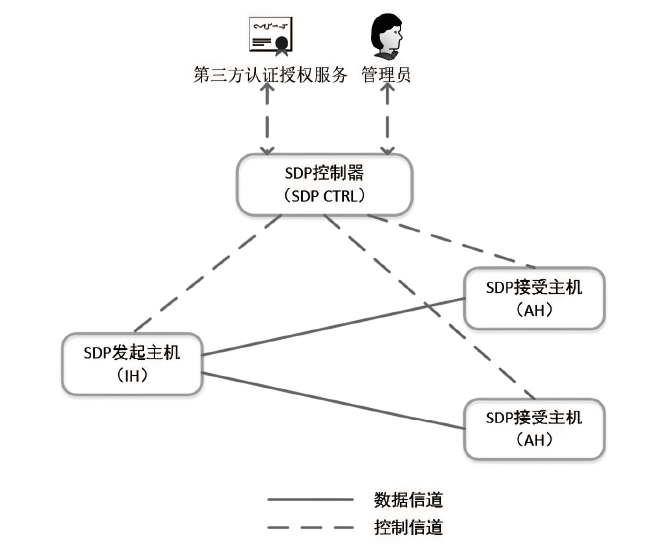
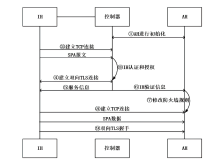
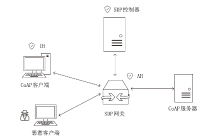
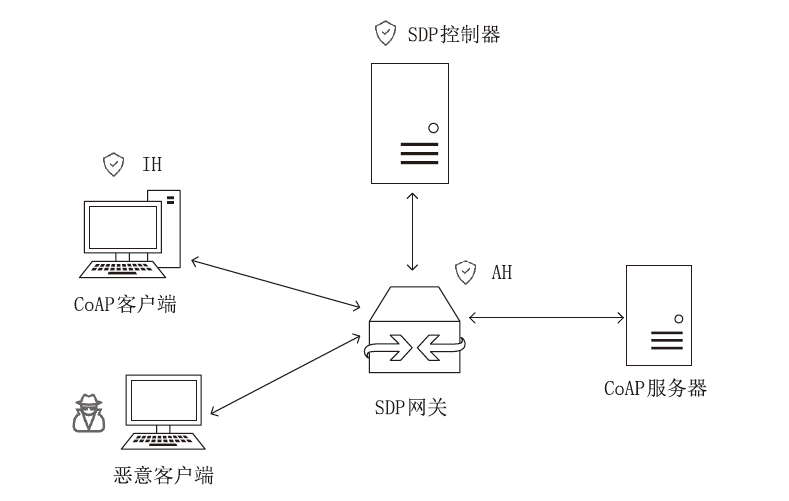
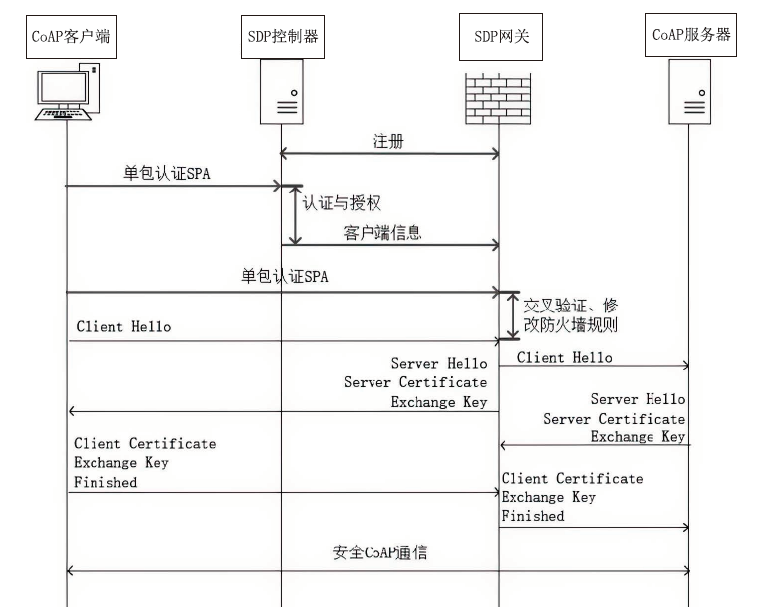
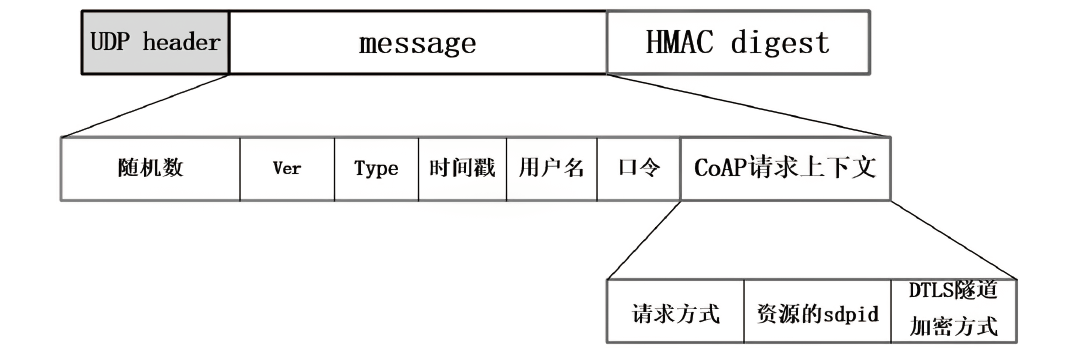
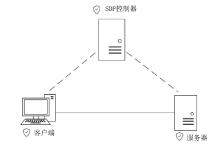
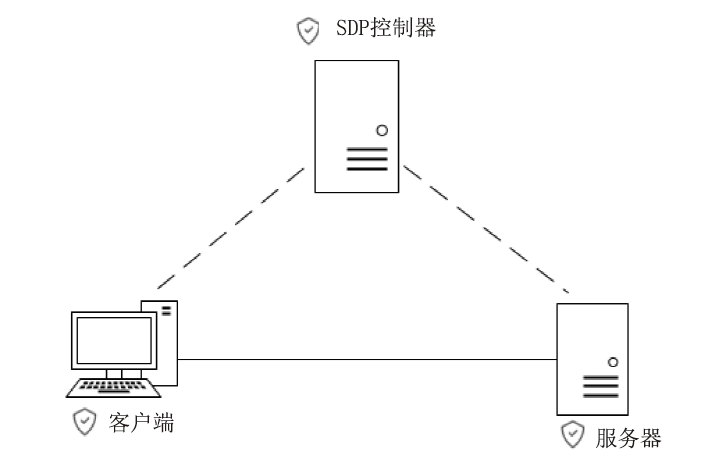
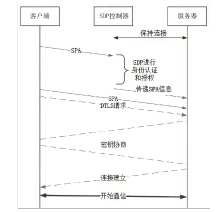
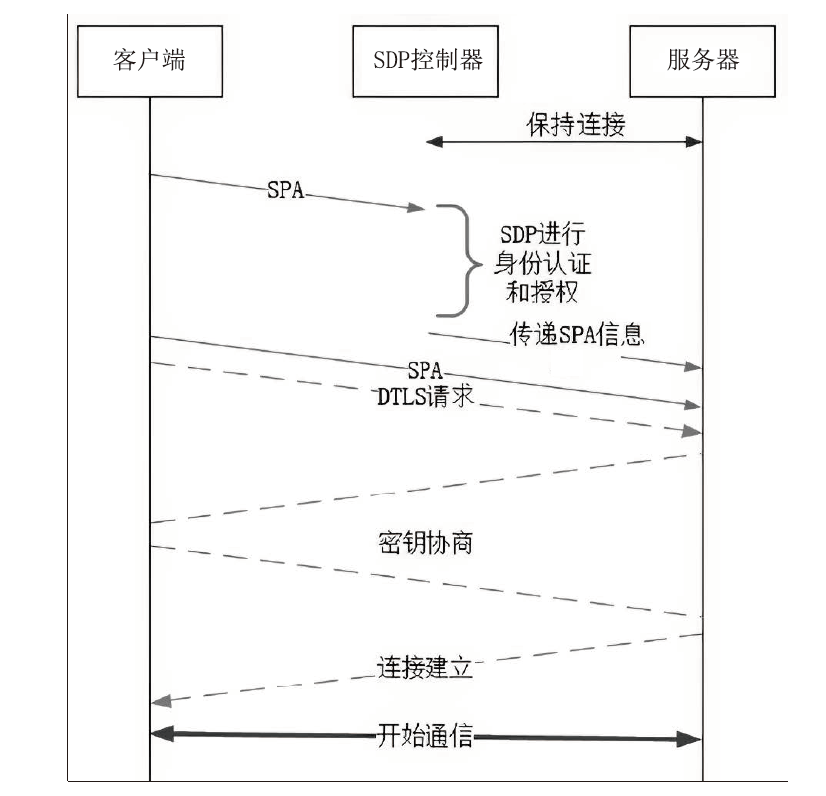
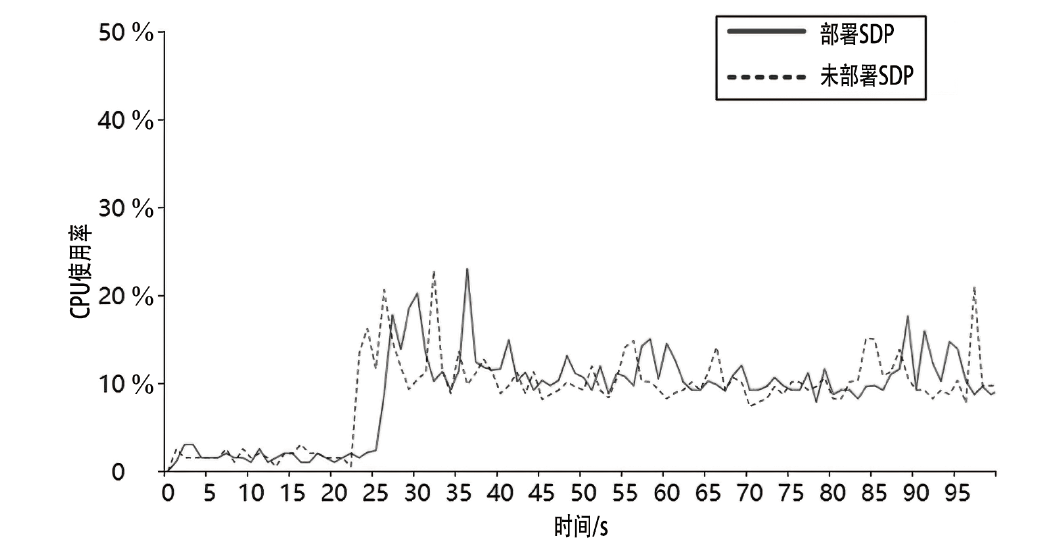
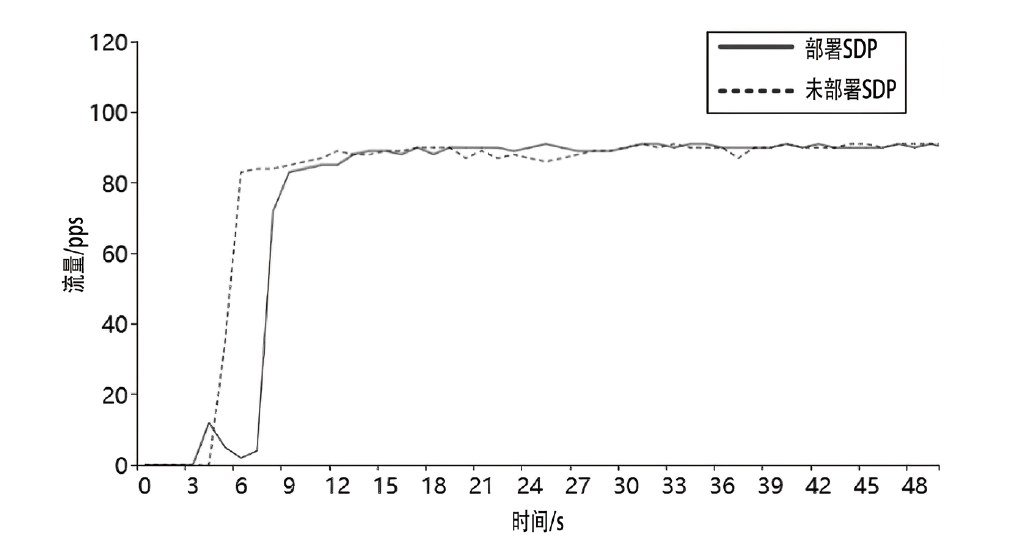
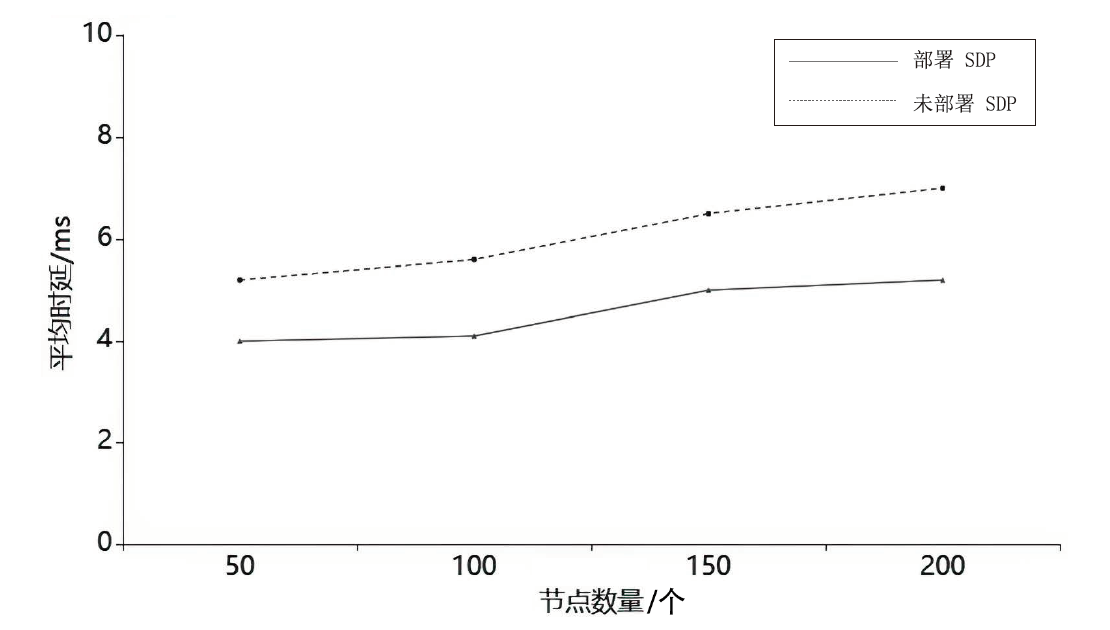
Netinfo Security ›› 2023, Vol. 23 ›› Issue (8): 17-31.doi: 10.3969/j.issn.1671-1122.2023.08.002
Previous Articles Next Articles
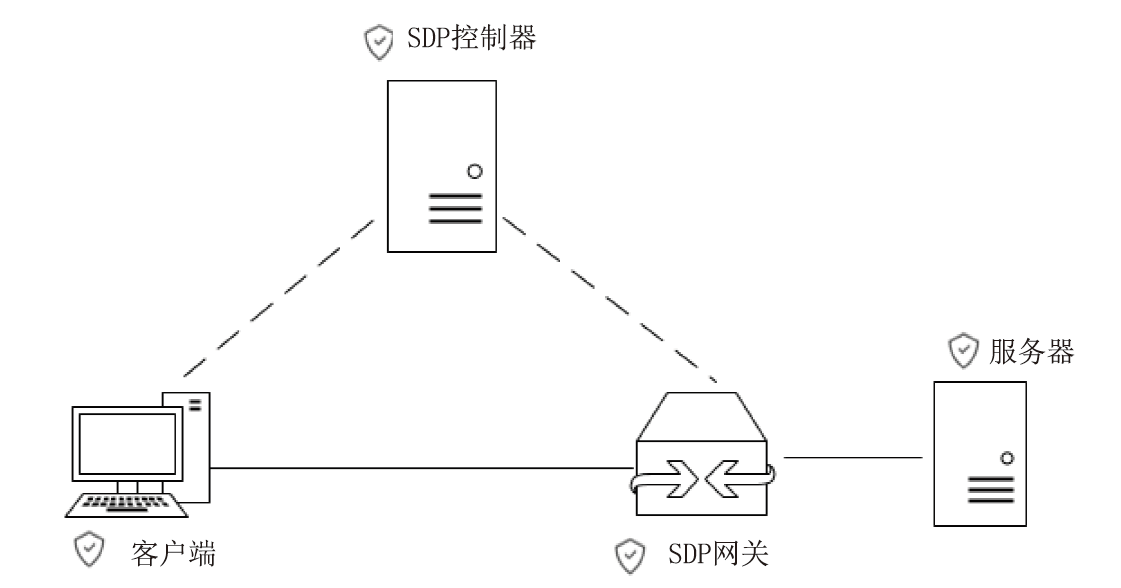
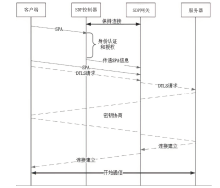
SDP-CoAP: Design of Security Enhanced CoAP Communication Framework Based on Software Defined Perimeter
ZHANG Wei1( ), LI Zixuan1, XU Xiaoyu2, HUANG Haiping1
), LI Zixuan1, XU Xiaoyu2, HUANG Haiping1
- 1. School of Computer Science, Nanjing University of Posts and Telecommunications, Nanjing 210023, China
2. Jiangsu Lianchuang Software Research Institute, Nanjing 210003, China
-
Received:2023-06-25Online:2023-08-10Published:2023-08-08 -
Contact:ZHANG Wei E-mail:zhangw@njupt.edu.cn
CLC Number:
Cite this article
ZHANG Wei, LI Zixuan, XU Xiaoyu, HUANG Haiping. SDP-CoAP: Design of Security Enhanced CoAP Communication Framework Based on Software Defined Perimeter[J]. Netinfo Security, 2023, 23(8): 17-31.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.08.002
| 设备 | 安装的软件 | 配置 |
|---|---|---|
| VM1 (SDP Controller) | - Linux CentOS7 - SDPcontroller module | - 1 Processor - 2 GB RAM - 2 NICs |
| VM2 (SDP Gateway) | - Linux Ubuntu 20.04 - Californium CoAP Server - SDPgateway module | - 2 Processor - 4 GB RAM - 2 NICs |
| VM3 (Normal Client) | - Linux Ubuntu 20.04 - Californium CoAP Client - IH module | - 2 Processor - 2 GB RAM - 2 NICs |
| VM4 (Malicious Client) | - Linux Ubuntu 20.04 - Californium CoAP Client | - 2 Processor - 4 GB RAM - 2 NICs |
| VM5 (CoAP Server) | - Linux Ubuntu 20.04 - Californium CoAP Server | - 2 Processor - 2 GB RAM - 2 NICs |
| [1] |
SHAFIQUE K, KHAWAJA B A, SABIR F, et al. Internet of Things (IoT) for Next-Generation Smart Systems: A Review of Current Challenges, Future Trends and Prospects for Emerging 5G-IoT Scenarios[J]. IEEE Access, 2020, 8: 23022-23040.
doi: 10.1109/Access.6287639 URL |
| [2] | Ministry of Industry and Information Technology. Economic Operation of the Communications Industry from January to May 2023[EB/OL]. (2023-06-21)[2023-06-25]. https://wap.miit.gov.cn/gxsj/tjfx/txy/art/2023/art_a62ac3d2646541fba9e6a5e3a20534c1.html. |
| 中华人民共和国工业与信息化部. 2023年1-5月份通信业经济运行情况[EB/OL]. (2023-06-21)[2023-06-25]. https://wap.miit.gov.cn/gxsj/tjfx/txy/art/2023/art_a62ac3d2646541fba9e6a5e3a20534c1.html. | |
| [3] |
BORMANN C, CASTELLANI A P, SHELBY Z. Coap: An Application Protocol for Billions of Tiny Internet Nodes[J]. IEEE Internet Computing, 2012, 16(2): 62-67.
doi: 10.1109/MIC.2012.29 URL |
| [4] | KARAGIANNIS V, CHATZIMISIOS P, VAZQUEZ-GALLEGO F, et al. A Survey on Application Layer Protocols for the Internet of Things[J]. Transaction on IoT and Cloud Computing, 2015, 3(1): 11-17 |
| [5] | HAN J, HA M, KIM D. Practical Security Analysis for the Constrained Node Networks:Focusing on the DTLS Protocol[C]//IEEE. 2015 5th International Conference on the Internet of Things (IoT). New York: IEEE, 2015: 22-29. |
| [6] | CAMPBELL M. Beyond Zero Trust: Trust is a Vulnerability[J]. Computer, 2020, 53(10): 110-113. |
| [7] | PALMO Y, TANIMOTO S, SATO H, et al. A Consideration of Scalability for Software Defined Perimeter Based on the Zero-Trust Model[C]//IEEE. 2021 10th International Congress on Advanced Applied Informatics (IIAI-AAI). New York: IEEE, 2021: 717-724. |
| [8] | Internet Engineering Task Force. Datagram Transport Layer Security[EB/OL]. [2023-05-20]. https://www.rfc-editor.org/rfc/rfc6347. |
| [9] | ARVIND S, NARAYANAN V A. An Overview of Security in CoAP:Attack and Analysis[C]//IEEE. 2019 5th International Conference on Advanced Computing & Communication Systems (ICACCS). New York: IEEE, 2019: 655-660. |
| [10] | LERCHE C, HARTKE K, KOVATSCH M. Industry Adoption of the Internet of Things:A Constrained Application Protocol Survey[C]//IEEE. Proceedings of 2012 IEEE 17th International Conference on Emerging Technologies & Factory Automation (ETFA 2012). New York: IEEE, 2012: 1-6. |
| [11] | CAPOSSELE A, CERVO V, DECICCO G, et al. Security as a CoAP Resource:An Optimized DTLS Implementation for the IoT[C]//IEEE. 2015 IEEE International Conference on Communications (ICC). New York: IEEE, 2015: 549-554. |
| [12] | NAVAS R E, BOUDER H L, CUPPENS N, et al. Do not Trust Your Neighbors! A Small IoT Platform Illustrating a Man-in-the-Middle Attack[C]//Springer. International Conference on Ad-Hoc Networks and Wireless. Berlin: Springer, 2018: 120-125. |
| [13] |
MOUBAYED A, REFAEY A, SHAMI A. Software-Defined Perimeter (SDP): State of the Art Secure Solution for Modern Networks[J]. IEEE Network, 2019, 33(5): 226-233.
doi: 10.1109/MNET.65 URL |
| [14] | HAROON A, AKRAM S, SHAH M A, et al. E-Lithe:A Lightweight Secure DTLS for IoT[C]//IEEE. 2017 IEEE 86th Vehicular Technology Conference (VTC-Fall). New York: IEEE, 2017: 1-5. |
| [15] | KAJWADKAR S, JAIN V K. A Novel Algorithm for DoS and DDoS Attack Detection in Internet of Things[C]//IEEE. 2018 Conference on Information and Communication Technology (CICT). New York: IEEE, 2018: 1-4. |
| [16] | DEY S, HOSSAIN A. Session-Key Establishment and Authentication in a Smart Home Network Using Public Key Cryptography[J]. IEEE Sensors Letters, 2019, 3(4): 1-4. |
| [17] |
MAJUMDER S, RAY S, SADHUKHAN D, et al. ECC-CoAP: Elliptic Curve Cryptography Based Constraint Application Protocol for Internet of Things[J]. Wireless Personal Communications, 2021, 116(3): 1867-1896.
doi: 10.1007/s11277-020-07769-2 |
| [18] | SARAIVA D A F, LEITHARDT V R Q, DEPAULA D, et al. Prisec: Comparison of Symmetric Key Algorithms for IoT Devices[EB/OL]. [2023-06-21]. https://www.mdpi.com/1424-8220/19/19/4312. |
| [19] | HALABI D, HAMDAN S, ALMAJALI S. Enhance the Security in Smart Home Applications Based on IoT-CoAP Protocol[C]//IEEE. 2018 Sixth International Conference on Digital Information, Networking, and Wireless Communications (DINWC). New York: IEEE, 2018: 81-85. |
| [20] | PANDYA H B, CHAMPANERIA T A. Enhancement of Security in IoTSyS Framework[C]//Springer. Proceedings of International Conference on Communication and Networks. Berlin: Springer, 2017: 31-43. |
| [21] |
DE HOZ DIEGO J D, SALDANA J, FERNÁNDEZ-NAVAJAS J, et al. Decoupling Security from Applications in CoAP-Based IoT Devices[J]. IEEE Internet of Things Journal, 2019, 7(1): 467-476.
doi: 10.1109/JIoT.6488907 URL |
| [22] |
KUMAR P M, GANDHI U D. Enhanced DTLS with CoAP-Based Authentication Scheme for the Internet of Things in Healthcare Application[J]. The Journal of Supercomputing, 2020, 76(6): 3963-3983.
doi: 10.1007/s11227-017-2169-5 |
| [23] |
SINGH J, REFAEY A, KOILPILLAI J. Adoption of the Software-Defined Perimeter (SDP) Architecture for Infrastructure as a Service[J]. Canadian Journal of Electrical and Computer Engineering, 2020, 43(4): 357-363.
doi: 10.1109/CJECE.2020.3005316 URL |
| [24] |
SALLAM A, REFAEY A, SHAMI A. On the Security of SDN: A Completed Secure and Scalable Framework Using the Software-Defined Perimeter[J]. IEEE Access, 2019, 7: 146577-146587.
doi: 10.1109/Access.6287639 URL |
| [25] | SINGH J, REFAEY A, SHAMI A. Multilevel Security Framework for NFV Based on Software Defined Perimeter[J]. IEEE Network, 2020, 34(5): 114-119. |
| [26] |
SINGH J, BELLO Y, HUSSEIN A R, et al. Hierarchical Security Paradigm for IoT Multiaccess Edge Computing[J]. IEEE Internet of Things Journal, 2020, 8(7): 5794-5805.
doi: 10.1109/JIOT.2020.3033265 URL |
| [27] |
REFAEY A, SALLAM A, SHAMI A. On IoT Applications: A Proposed SDP Framework for MQTT[J]. Electronics Letters, 2019, 55(22): 1201-1203.
doi: 10.1049/el.2019.2334 |
| [28] | SALLAM A, REFAEY A, SHAMI A. Securing Smart Home Networks with Software-Defined Perimeter[C]//IEEE. 2019 15th International Wireless Communications & Mobile Computing Conference (IWCMC). New York: IEEE, 2019: 1989-1993. |
| [1] | HUANG Jie, HE Chengjun. Service Protection Scheme Based on Software Defined Perimeter [J]. Netinfo Security, 2023, 23(6): 1-10. |
| [2] | LI Zhihua, WANG Zhihao. IoT Device Identification Method Based on LCNN and LSTM Hybrid Structure [J]. Netinfo Security, 2023, 23(6): 43-54. |
| [3] | LIU Xiangyu, LU Tianliang, DU Yanhui, WANG Jingxiang. Lightweight IoT Intrusion Detection Method Based on Feature Selection [J]. Netinfo Security, 2023, 23(1): 66-72. |
| [4] | ZHANG Xuewang, LIU Yufan. Identity Traceable Anonymous Authentication Scheme for Nodes in the Perception Layer of IoT [J]. Netinfo Security, 2022, 22(9): 55-62. |
| [5] | ZHAO Hong, LI Shan, ZUO Peiliang, WEI Zhanzhen. Security Resource Allocation Method for Internet of Things Based on Reinforcement Learning [J]. Netinfo Security, 2022, 22(6): 44-52. |
| [6] | GUO Baoxia, WANG Jiahui, MA Limin, ZHANG Wei. Research on Dynamic Access Control Model of Sensitive Data Based on Zero Trust [J]. Netinfo Security, 2022, 22(6): 86-93. |
| [7] | HAN Li, SONG Jixiang, SUN Shimin. Moving Target Defense Mechanism Research Based on Device Address in SD-IoT [J]. Netinfo Security, 2022, 22(11): 36-46. |
| [8] | LI Tong, REN Shuai, WANG Gang, MENG Qingyu. Cloud-edge-device Collaborative Integrity Verification Scheme Based on Chameleon Authentication Tree for Streaming Data [J]. Netinfo Security, 2022, 22(1): 37-45. |
| [9] | CHEN Qinggang, DU Yanhui, HAN Yi, LIU Xiangyu. IoT Device Recognition Model Based on Depthwise Separable Convolution [J]. Netinfo Security, 2021, 21(9): 67-73. |
| [10] | WU Kehe, CHENG Rui, ZHENG Bihuang, CUI Wenchao. Research on Security Communication Protocol of Power Internet of Things [J]. Netinfo Security, 2021, 21(9): 8-15. |
| [11] | LI Qun, DONG Jiahan, GUAN Zhitao, WANG Chao. A Clustering and Classification-based Malicious Attack Detection Method for Internet of Things [J]. Netinfo Security, 2021, 21(8): 82-90. |
| [12] | LIU Xin, GUO Zhenbin, SONG Yuchen. An Authentication Scheme Based on SGX for Industrial Internet of Things [J]. Netinfo Security, 2021, 21(6): 1-10. |
| [13] | LI Tong, ZHOU Xiaoming, REN Shuai, XU Jian. Light-weight Mutual Authentication Protocol for Mobile Edge Computing [J]. Netinfo Security, 2021, 21(11): 58-64. |
| [14] | WU Yunkun, JIANG Bo, PAN Ruixuan, LIU Yuling. A SDN Access Control Mechanism Based on Zero Trust [J]. Netinfo Security, 2020, 20(8): 37-46. |
| [15] | LIU Jianwei, HAN Yiran, LIU Bin, YU Beiyuan. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||