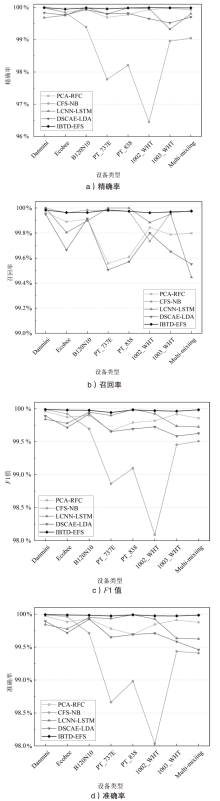
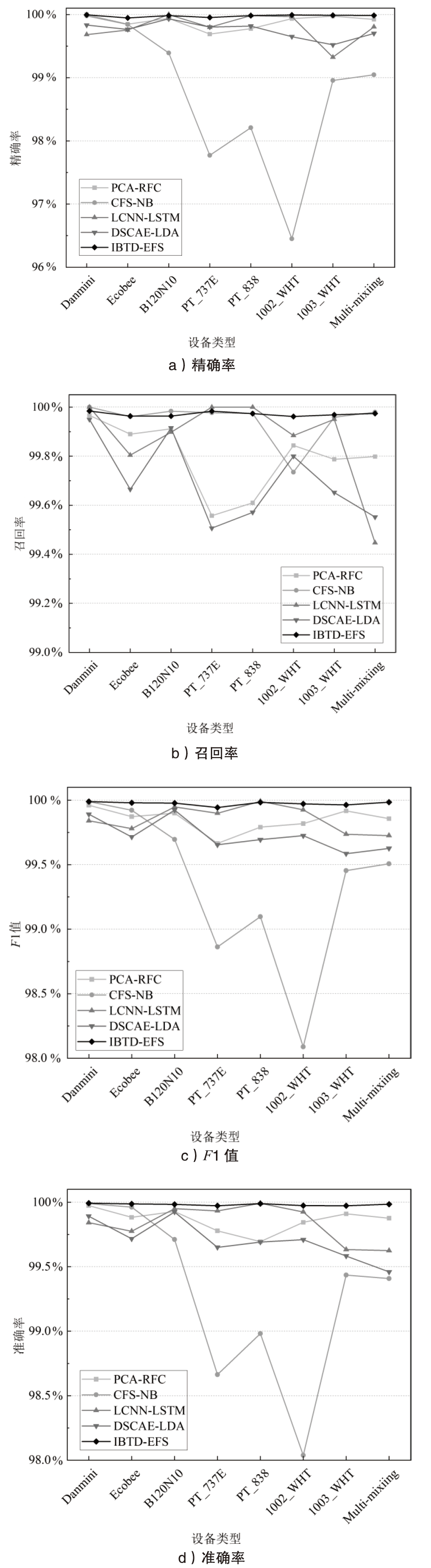
Netinfo Security ›› 2024, Vol. 24 ›› Issue (5): 667-681.doi: 10.3969/j.issn.1671-1122.2024.05.002
Previous Articles Next Articles
Lightweight Detection Method for IoT Mirai Botnet
LI Zhihua1( ), CHEN Liang1, LU Xulin1, FANG Zhaohui2, QIAN Junhao3
), CHEN Liang1, LU Xulin1, FANG Zhaohui2, QIAN Junhao3
- 1. School of Artificial Intelligence and Computer, Jiangnan University, Wuxi 214122, China
2. Hunan Bojiang Information Technology Co., Ltd., Changsha 410073, China
3. School of Internet of Things Engineering, Jiangnan University, Wuxi 214122, China
-
Received:2024-03-05Online:2024-05-10Published:2024-06-24 -
Contact:LI Zhihua E-mail:jswxzhli@aliyun.com
CLC Number:
Cite this article
LI Zhihua, CHEN Liang, LU Xulin, FANG Zhaohui, QIAN Junhao. Lightweight Detection Method for IoT Mirai Botnet[J]. Netinfo Security, 2024, 24(5): 667-681.
share this article
| [1] | STATISTA R D. Internet of Things-Number of Connected Devices Worldwide 2012-2025[EB/OL]. (2016-11-27)[2024-02-02]. https://www.statista.com/statistics/471264/iot-number-of-connected-devices-worldwide/. |
| [2] |
ZHANG Ye, LI Zhihua, WANG Changjie. Kernel Density Estimation-Based Lightweight IoT Anomaly Traffic Detection Method[J]. Computer Science, 2021, 48(9): 337-344.
doi: 10.11896/jsjkx.200600108 |
|
张叶, 李志华, 王长杰. 基于核密度估计的轻量级物联网异常流量检测方法[J]. 计算机科学, 2021, 48(9): 337-344.
doi: 10.11896/jsjkx.200600108 |
|
| [3] | ANTONAKAKIS M, APRIL T, BAILEY M, et al. UnderStanding the Mirai Botnet[C]// USENIX. 26th USENIX Security Symposium (USENIX Security 17). Berkeley: USENIX, 2017: 1093-1110. |
| [4] | SHOBANA M, RATHI S. IoT Malware: An Analysis of IoT Device Hijacking[J]. International Journal of Scientific Research in Computer Science, Engineering and Information Technology, 2018, 5: 2456-3307. |
| [5] | KHAN A, SHARMA I. Tackling Okiru Attacks in IoT with AI-Driven Detection and Mitigation Strategies[C]// IEEE. 2023 International Conference on Power Energy, Environment & Intelligent Control (PEEIC). New York: IEEE, 2023: 336-341. |
| [6] | ABBAS S G, HASHMAT F, SHAH G A, et al. Generic Signature Development for IoT Botnet Families[EB/OL]. (2021-09-01)[2024-02-25]. https://www.sciencedirect.com/science/article/abs/pii/S2666281721001323. |
| [7] | BLAISE A, BOUET M, CONAN V, et al. Detection of Zero-Day Attacks: An Unsupervised Port-Based Approach[EB/OL]. (2020-10-01)[2024-02-25]. https://www.sciencedirect.com/science/article/abs/pii/S1389128620300761. |
| [8] | PANDA M, ABD ALLAH A M, HASSANIEN A E. Developing an Efficient Feature Engineering and Machine Learning Model for Detecting IoT-Botnet Cyber Attacks[J]. IEEE Access, 2021, 9: 91038-91052. |
| [9] | SAFITRI W A, AHMAD T, HOSTIADI D P. Analyzing Machine Learning-Based Feature Selection for Botnet Detection[C]// IEEE. 2022 1st International Conference on Information System & Information Technology (ICISIT). New York: IEEE, 2022: 386-391. |
| [10] | LEFOANE M, GHAFIR I, KABIR S, et al. Machine Learning for Botnet Detection: An Optimized Feature Selection Approach[C]// ACM. The 5th International Conference on Future Networks & Distributed Systems. New York: ACM, 2022: 195-200. |
| [11] | NIMBALKAR P, KSHIRSAGAR D. Feature Selection for Intrusion Detection System in Internet-of-Things (IoT)[J]. ICT Express, 2021, 7(2): 177-181. |
| [12] | BAHSI H, NOMM S, TORRE F B L. Dimensionality Reduction for Machine Learning Based IoT Botnet Detection[C]// IEEE. 2018 15th International Conference on Control, Automation, Robotics and Vision (ICARCV). New York: IEEE, 2018: 1857-1862. |
| [13] | GUERRA M A, BAHSI H, NOMM S. Hybrid Feature Selection Models for Machine Learning Based Botnet Detection in IoT Networks[C]// IEEE. 2019 International Conference on Cyberworlds (CW). New York: IEEE, 2019: 324-327. |
| [14] | SHAFIQ M, TIAN Zhihong, BASHIR A K, et al. CorrAUC: A Malicious Bot-IoT Traffic Detection Method in IoT Network Using Machine-Learning Techniques[J]. IEEE Internet of Things Journal, 2020, 8(5): 3242-3254. |
| [15] | LEE J, PARK D, LEE C. Feature Selection Algorithm for Intrusions Detection System Using Sequential forward Search and Random Forest Classifier[J]. KSII Transactions on Internet and Information Systems (TIIS), 2017, 11(10): 5132-5148. |
| [16] | ALAM T, QAMARS, DIXIT A, et al. Genetic Algorithm: Reviews, Implementations, and Applications[EB/OL]. (2020-06-05)[2024-02-25]. https://arxiv.org/abs/2007.12673. |
| [17] | LIU Xiangyu, DU Yanhui. Towards Effective Feature Selection for IoT Botnet Attack Detection Using a Genetic Algorithm[EB/OL]. (2023-02-07)[2024-02-25]. https://www.mdpi.com/2079-9292/12/5/1260. |
| [18] | DESAI M G, SHI Yong, SUO Kun. IoT Bonet and Network Intrusion Detection Using Dimensionality Reduction and Supervised Machine Learning[C]// IEEE. 2020 11th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON). New York: IEEE, 2020: 316-322. |
| [19] | SOE Y N, FENG Yaokai, SANTOSA P I, et al. Machine Learning-Based IoT-Botnet Attack Detection with Sequential Architecture[EB/OL]. (2020-08-05)[2024-02-25]. https://www.mdpi.com/1424-8220/20/16/4372. |
| [20] | ALSHEHRI M S, AHMAD J, ALMAKDI S, et al. SkipGateNet: A Lightweight CNN-LSTM Hybrid Model with Learnable Skip Connections for Efficient Botnet Attack Detection in IoT[J]. IEEE Access, 2024, 12(12): 35521-35538. |
| [21] | LUU C D, NGUYEN V Q, PHAM T S, et al. A Zero-Shot Deep Learning Approach for Unknown IoT Botnet Attack Detection[C]// IEEE. 2023 RIVF International Conference on Computing and Communication Technologies (RIVF). New York: IEEE, 2023: 278-283. |
| [22] | XU Zhaozhao, SHEN Derong, NIE Tiezheng, et al. Hybrid Feature Selection Algorithm Combining Information Gain Ratio and Genetic Algorithm[J]. Journal or Software, 2022, 33(3): 1128-1140. |
| 许召召, 申德荣, 聂铁铮, 等. 融合信息增益比和遗传算法的混合式特征选择算法[J]. 软件学报, 2022, 33(3): 1128-1140. | |
| [23] |
PAUL A, MUKHERJEE D P, DAS P, et al. Improved Random Forest for Classification[J]. IEEE Transactions on Image Processing, 2018, 27(8): 4012-4024.
doi: 10.1109/TIP.2018.2834830 pmid: 29993742 |
| [24] | KE Guolin, MENG Qi, FINLEY T, et al. LightGBM: A Highly Efficient Gradient Boosting Decision Tree[EB/OL]. (2017-12-04)[2024-02-25]. https://proceedings.neurips.cc/paper/2017/hash/6449f44a102fde848669bdd9eb6b76fa-Abstract.html. |
| [25] | GOPIKA N, ME A M K. Correlation Based Feature Selection Algorithm for Machine Learning[C]// IEEE. 2018 3rd International Conference on Communication and Electronics Systems (ICCES). New York: IEEE, 2018: 692-695. |
| [26] | VERGARA J R, ESTEVEZ P A. A Review of Feature Selection Methods Based on Mutual Information[J]. Neural Computing and Applications, 2014, 24: 175-186. |
| [27] | LYU Yang, FENG Yaokai, SAKURAI K. A Survey on Feature Selection Techniques Based on Filtering Methods for Cyber Attack Detection[EB/OL]. (2023-03-15)[2024-02-25]. https://www.mdpi.com/2078-2489/14/3/191. |
| [28] | HUANG C L, WANG C J. A GA-Based Feature Selection and Parameters Optimization for Support Vector Machines[J]. Expert Systems with Applications, 2006, 31(2): 231-240. |
| [29] | ALEJANDRE F V, CORTES N C, ANAYA E A. Feature Selection to Detect Botnets Using Machine Learning Algorithms[C]// IEEE. 2017 International Conference on Electronics, Communications and Computers (CONIELECOMP). New York: IEEE, 2017: 1-7. |
| [30] | WIYONO R T, CAHYANI N D W. Performance Analysis of Decision Tree C4.5 as a Classification Technique to Conduct Network Forensics for Botnet Activities in Internet of Things[C]// IEEE. 2020 International Conference on Data Science and Its Applications (ICoDSA). New York: IEEE, 2020: 1-5. |
| [31] | IFTIKHAR S, AL-MADANI D, ABDULLAH S, et al. A Supervised Feature Selection Method for Malicious Intrusions Detection in IoT Based on Genetic Algorithm[J]. International Journal of Computer Science & Network Security, 2023, 23(3): 49-56. |
| [32] | AN Ting. Application of Genetic Algorithm Based on F-Ratio Rule in Signal Feature Selection[C]// IEEE. 2017 10th International Symposium on Computational Intelligence and Design (ISCID). New York: IEEE, 2017: 492-495. |
| [33] | LI Juan. A Feature Subset Selection Algorithm Based on Feature Activity and Improved GA[C]// IEEE. 2015 11th International Conference on Computational Intelligence and Security (CIS). New York: IEEE, 2015: 206-210. |
| [34] | ABDI H, WILLIAMS L J. Normalizing Data[J]. Encyclopedia of Research Design, 2010, 1: 935-938. |
| [35] | CHEN Tianqi, GUESTRIN C. XGBoost: A Scalable Tree Boosting System[C]// ACM. Proceedings of the 22nd ACM Sigkdd International Conference on Knowledge Discovery and Data Mining. New York: ACM,2016: 785-794. |
| [36] | HAN Lu, LI Wenjun, SU Zhi. An Assertive Reasoning Method for Emergency Response Management Based on Knowledge Elements C4.5 Decision Tree[J]. Expert Systems with Applications, 2019, 122: 65-74. |
| [37] | MEIDAN Y, BOHADANA M, MATHOV Y, et al. N-Baiot—Network-Based Detection of IoT Botnet Attacks Using Deep Autoencoders[J]. IEEE Pervasive Computing, 2018, 17(3): 12-22. |
| [1] | GU Guomin, CHEN Wenhao, HUANG Weida. A Covert Tunnel and Encrypted Malicious Traffic Detection Method Based on Multi-Model Fusion [J]. Netinfo Security, 2024, 24(5): 694-708. |
| [2] | TU Xiaohan, ZHANG Chuanhao, LIU Mengran. Design and Implementation of Malicious Traffic Detection Model [J]. Netinfo Security, 2024, 24(4): 520-533. |
| [3] | XU Zirong, GUO Yanping, YAN Qiao. Malicious Software Adversarial Defense Model Based on Feature Severity Ranking [J]. Netinfo Security, 2024, 24(4): 640-649. |
| [4] | ZHONG Jing, FANG Bing, ZHU Jiang. Recent Research of Feature Selection Algorithms Based on Sparse Matrix Structure [J]. Netinfo Security, 2024, 24(3): 352-362. |
| [5] | ZHANG Qiang, HE Junjiang, LI Wenshan, LI Tao. Anomaly Traffic Detection Based on Deep Metric Learning [J]. Netinfo Security, 2024, 24(3): 462-472. |
| [6] | YIN Chunyong, JIANG Yiyang. Differential Privacy Trajectory Protection Model Based on Personalized Spatiotemporal Clustering [J]. Netinfo Security, 2024, 24(1): 80-92. |
| [7] | LIU Yuxiao, CHEN Wei, ZHANG Tianyue, WU Lifa. Explainable Anomaly Traffic Detection Based on Sparse Autoencoders [J]. Netinfo Security, 2023, 23(7): 74-85. |
| [8] | GUO Rui, WEI Xin, CHEN Li. An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System [J]. Netinfo Security, 2023, 23(3): 1-12. |
| [9] | PENG Cheng, FAN Wei, ZHU Dali, YANG Fen. Research on Man-in-the-Middle Attack Detection in LTE Access Network Based on Weighted Bayesian Classifier [J]. Netinfo Security, 2023, 23(2): 1-10. |
| [10] | LIU Xiangyu, LU Tianliang, DU Yanhui, WANG Jingxiang. Lightweight IoT Intrusion Detection Method Based on Feature Selection [J]. Netinfo Security, 2023, 23(1): 66-72. |
| [11] | LANG Bo, XIE Chong, CHEN Shaojie, LIU Hongyu. Fast-Flux Malicious Domain Name Detection Method Based on Multimodal Feature Fusion [J]. Netinfo Security, 2022, 22(4): 20-29. |
| [12] | WU Kehe, CHENG Rui, JIANG Xiaochen, ZHANG Jiyu. Security Protection Scheme of Power IoT Based on SDP [J]. Netinfo Security, 2022, 22(2): 32-38. |
| [13] | SONG Jing, DIAO Run, ZHOU Jie, QI Jianhuai. The Optimization Method of Industrial Control System Functional Safety and Information Security Policy [J]. Netinfo Security, 2022, 22(11): 68-76. |
| [14] | ZHU Tao, XIA Lingling, LI Penghui, XU Zhongyi. Analysis of Botnet Attack Data Based on Log [J]. Netinfo Security, 2022, 22(10): 82-90. |
| [15] | LI Yanlin, CAI Manchun, LU Tianliang, XI Rongkang. A Website Fingerprinting Attack Method via Convolutional Neural Network Optimized by Genetic Algorithm [J]. Netinfo Security, 2021, 21(9): 59-66. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||