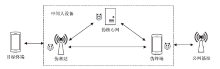
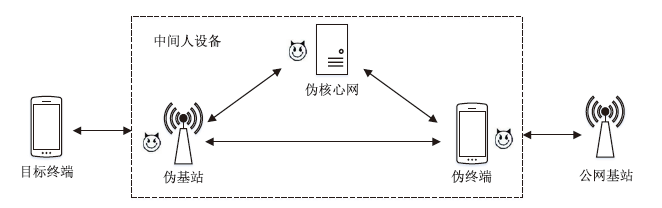
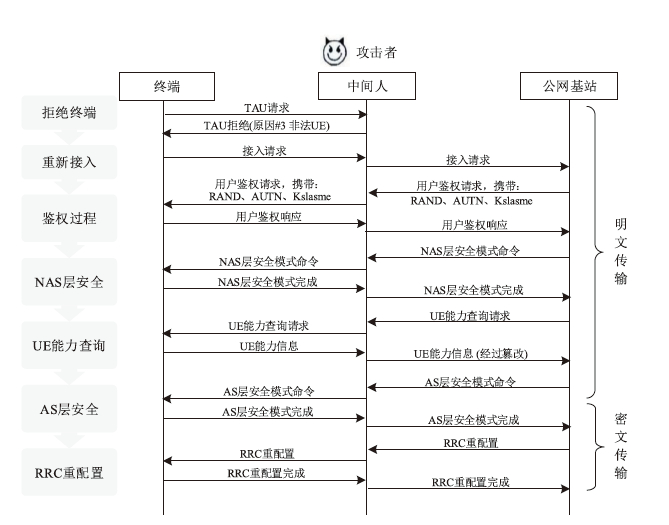
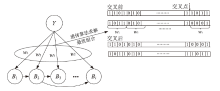
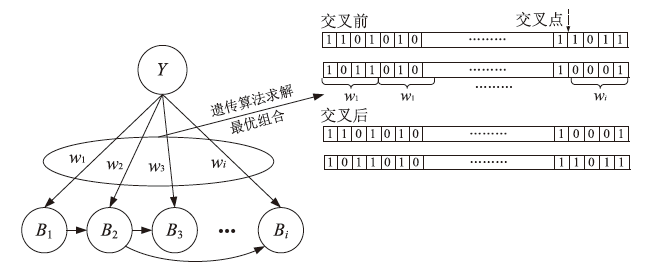
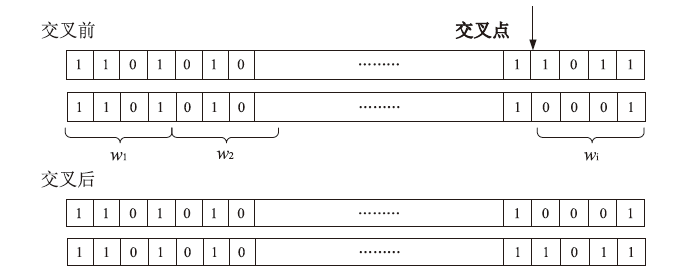
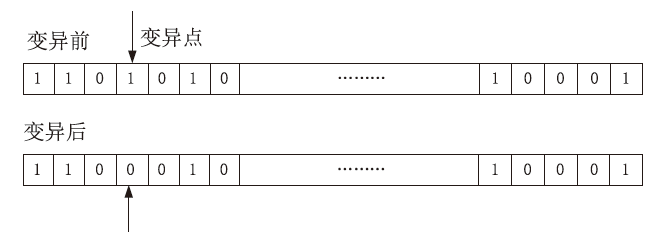
| [1] |
3GPP. 3GPP TS 33.401 Technical Specification Group Services and System Aspects; 3GPP System Architecture Evolution (SAE): Security architecture (Release17)[EB/OL]. (2022-06-17)[2022-11-14]. https://www.3gpp.org/ftp/Specs/archive/33_series/33.401.
|
| [2] |
LIAO Junkai, FENG Zhonghua. Security Threat Analysis of LTE Wireless Air Interface[J]. Communication Technology, 2017, 50(6): 1257-1263.
|
|
廖竣锴, 冯中华. LTE无线空口安全威胁分析[J]. 通信技术, 2017, 50(6): 1257-1263.
|
| [3] |
3GPP. 3GPP TS 36.300 Technical Specification Group Radio Access Network; Evolved Universal Terrestrial Radio Access (E-UTRA) and Evolved Universal Terrestrial Radio Access Network (E-UTRAN)(Release16)[EB/OL]. (2021-12-23)[2022-11-14]. https://www.3gpp.org/ftp/Specs/archive/36_series/36.300.
|
| [4] |
ZHANG Lizhuo, JIA Weijia, SHENG Wen, et al. Man-in-the-Middle Attack on 3G-WLAN Interworking[C]// IEEE. 2010 International Conference on Communications and Mobile Computing. New York: IEEE, 2010: 121-125.
|
| [5] |
YU Bo. An Detection and Protection Method for Man-in the-Middle Attack in the Wireless Networks[D]. Beijing: Beijing University of Posts and Telecommunications, 2015.
|
|
于波. 针对无线网络中间人攻击的检测与防御[D]. 北京: 北京邮电大学, 2015.
|
| [6] |
LEI Yang. Based on Wireless Intrusion Prevention System’s Man in the Middle Attack Detection’s Design and Realization[D]. Wuhan: Huazhong University of Science and Technology, 2014.
|
|
雷阳. 基于无线入侵防御系统的中间人攻击检测功能的设计与实现[D]. 武汉: 华中科技大学, 2014.
|
| [7] |
MOHAPATRA S K, SWAIN B R, DAS P. Comprehensive Survey of Possible Security Issues on 4G Networks[J]. International Journal of Network Security & Its Applications, 2015, 7(2): 61-69.
|
| [8] |
WANG Qianran, HUANG Chengbin, WANG Jinhua. Research on Application Strategy of Confidentiality and Integrity Protection Algorithm on 5G Air Interface[C]// IEEE. 2022 International Conference on Networks, Communications and Information Technology (CNCIT). New York:IEEE, 2022: 161-165.
|
| [9] |
YU Jiaxin. Research on Network Intrusion Detection Algorithm Based on Active Learning[D]. Dalian: Liaoning Normal University, 2019.
|
|
于佳鑫. 基于主动学习的网络入侵检测算法研究[D]. 大连: 辽宁师范大学, 2019.
|
| [10] |
DU Jiang, LI Xinghui, HUANG Hua. A Study of Man-in-the-Middle Attack Based on SSL Certificate Interaction[C]// IEEE. International Conference on Instrumentation. New York: IEEE Computer Society, 2011: 445-228.
|
| [11] |
RAJVANSHI N, CHOWDHARY KR. Comparison of SVM and Naive Bayes Text Classification Algorithms Using WEKA[J]. International Journal of Engineering Research and Technology, 2017, 6(9): 141-143.
|
| [12] |
XUE Jiming. Bayes Classifier Based Network Intrusion Detection[C]// Chinese Society for Electrical Engineering. 2013 Annual Meeting of the Chinese Society of Electrical Engineering. Beijing: Chinese Society for Electrical Engineering, 2013: 833-838.
|
|
薛集明. 基于贝叶斯分类的网络入侵检测[C]// 中国电机工程学会. 2013年中国电机工程学会年会论文集. 北京: 中国电机工程学会, 2013: 833-838.
|
| [13] |
SUN Pengyu. Application Research on the Multi-Step Attack in Bayesian Network[D]. Changchun: Jilin University, 2011.
|
|
孙鹏宇. 贝叶斯网络在多步攻击中应用研究[D]. 长春: 吉林大学, 2011.
|
| [14] |
JOACHIMS T. Text Classification on with Support Vector Machine: Learning with Many Relevant Features[C]// Springer. 10th European Conference on Machine Learning (ECML). Berlin:Springer. 1998: 137-142.
|
| [15] |
LI Ming, LIU Kefeng. Causality-Based Attribute Weighting via Information Flow and Genetic Algorithm for Naive Bayes Classifier[J]. IEEE Access, 2019, 7: 150630-150641.
doi: 10.1109/ACCESS.2019.2947568
|
| [16] |
MARYAM G, WITOLD K. Designing a Neural Network and a Genetic-Algorithm-Based Adaptive Wavelet for Internet Traffic Containing DDoS Attacks[C]// IEEE. 20th International Conference on Cognitive Informatics and Cognitive Computing. New York: IEEE, 2021: 173-180.
|
| [17] |
WANG Chunfeng, ZHANG Yonghong. Bayesian Network Structure Learning Based on Unconstrained Optimization and Genetic Algorithm[J]. Control and Decision, 2013, 28(4): 618-622.
|
|
汪春峰, 张永红. 基于无约束优化和遗传算法的贝叶斯网络结构学习方法[J]. 控制与决策, 2013, 28(4): 618-622.
|
| [18] |
SHAIK A, BORGAONKAR R, PARK S, et al. New Vulnerabilities in 4G and 5G Cellular Access Network Protocols: Exposing Device Capabilities[C]// ACM. 12th Conference Security and Privacy in Wireless and Mobile Networks. New York: ACM, 2019: 221-231.
|
| [19] |
3GPP. 3GPP TS 36.306 Technical Specification Group Radio Access Network; Evolved Universal Terrestrial Radio Access (E-UTRA); User Equipment (UE) radio access capabilities (Release 17)[EB/OL]. (2022-04-13)[2022-11-14]. https://www.3gpp.org/ftp/Specs/archive/36_series/36.306.
|
| [20] |
LEE J, CHUNG W, KIM E, et al. A New Genetic Approach for Structure Learning of Bayesian Networks: Matrix Genetic Algorithm[J]. International Journal of Control, Automation and Systems, 2010, 8(2): 398-407.
doi: 10.1007/s12555-010-0227-3
URL
|
| [21] |
LIAO Xingfa, CHEN Dezhao, HE Yijun. The Application of Genetic Algorithm to the Construction of Chemical Pattern Classifier[J]. Computers and Applied Chemistry, 2007, 27(5): 593-596.
|
|
廖兴发, 陈德钊, 贺益君. 应用遗传算法构建化学模式分类器[J]. 计算机与应用化学, 2007, 27(5): 593-596.
|
 ), ZHU Dali1,2, YANG Fen3
), ZHU Dali1,2, YANG Fen3