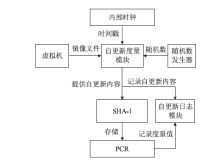
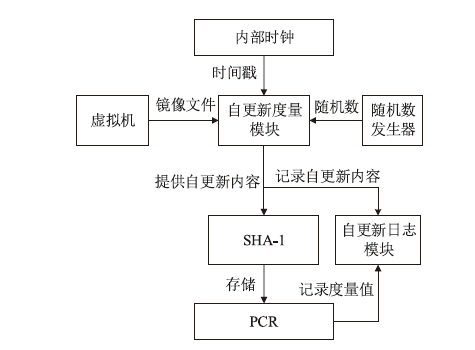
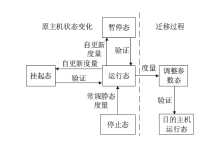
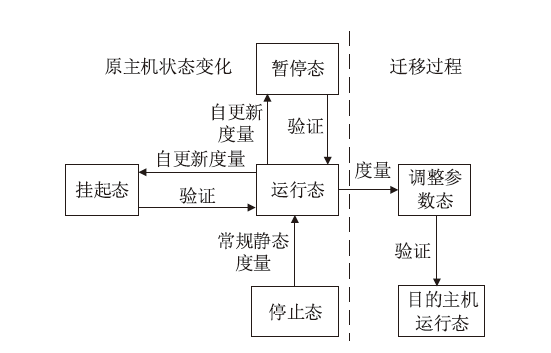
| [1] |
REN Chunhui, WANG Zhihao, ZHAO Baohua. Standard Industrial Application of Trusted Computing Architecture[J]. Information Security and Communications Privacy, 2019(1): 43-49.
|
|
任春卉, 王志皓, 赵保华. 《可信计算体系结构》标准产业化应用[J]. 信息安全与通信保密, 2019(1):43-49.
|
| [2] |
HOU Jie, XUE Liang, WANG Yang. Trusted Migration for Virtual Machine Based on Trusted Chain[J]. Command Control & Simulation, 2019, 41(6): 120-124.
|
|
侯婕, 薛亮, 王阳. 基于可信链的虚拟机可信迁移方法[J]. 指挥控制与仿真, 2019, 41(6):120-124.
doi: 10.3969/j.issn.1673-3819.2019.06.022
|
| [3] |
ZHANG Jianbiao, YANG Shisong, TU Shanshan, et al. Research on vTPCM Trust Management Technique for Cloud Computing Environment[J]. Netinfo Security, 2018, 18(4): 9-14.
|
|
张建标, 杨石松, 涂山山, 等. 面向云计算环境的vTPCM可信管理方案[J]. 信息网络安全, 2018, 18(4):9-14.
|
| [4] |
TAN Liang, XIAO Huan, WANG Juan. Research and Development of TPM Virtualization[C]// Springer. Chineses Conference on Trusted Computing and Information Security. Heidelberg: Springer, 2020: 206-250.
|
| [5] |
SUN Haonan, HE Rongyu, GUO Li. A Verification Scheme for Trusted Virtual Platform Environment[J]. Computer Applications and Software, 2018, 35(8): 307-313.
|
|
孙浩男, 鹤荣育, 郭丽. 一种可信虚拟平台底层环境验证方案[J]. 计算机应用与软件, 2018, 35(8):307-313.
|
| [6] |
DU Jiabing. Design of Virtualized Trusted Model Based on QEMU-KVM[J]. Electronic Design Engineering, 2019, 27(10): 146-149, 154.
|
|
杜家兵. 基于QEMU-KVM的虚拟化可信模型设计[J]. 电子设计工程, 2019, 27(10):146-149,154.
|
| [7] |
TAN Liang, WANG Shan, SONG Min, et al. Software vTPM Key Information Protection Scheme Based on Shadow Page Table Plus[J]. Journal of Cryptologic Research, 2019, 6(3): 304-323.
doi: 10.13868/j.cnki.jcr.000304
|
| [8] |
ZHANG Feifei. Research on Measurement Approach for the Trusted Virtual Domains[D]. Beijing: Beijing Jiaotong University, 2018.
|
|
张飞飞. 可信虚拟域度量技术研究[D]. 北京: 北京交通大学, 2018.
|
| [9] |
WANG Juan, XIAO Feng, HUANG Jianwei, et al. A Security-Enhanced vTPM 2.0 for Cloud Computing[C]// Springer. International Conference on Information and Communications Security. Heidelberg: Springer, 2017: 557-569.
|
| [10] |
WANG Yong, ZHANG Yuhan, HONG Zhi, et al. Kernel Integrity Measurement Architecture Based on TPM 2.0[J]. Computer Engineering, 2018, 44(3): 166-170.
|
|
王勇, 张雨菡, 洪智, 等. 基于TPM 2.0的内核完整性度量框架[J]. 计算机工程, 2018, 44(3):166-170.
|
| [11] |
CHEN Xingshu, JIANG Chao, WANG Wei, et al. Research on the Extension of Chinese Commercial Cryptographic Algorithms for Virtual Trusted Platform Module[J]. Advanced Engineering Sciences, 2020, 52(3): 141-149.
|
|
陈兴蜀, 蒋超, 王伟, 等. 针对虚拟可信平台模块的国密算法扩展技术研究[J]. 工程科学与技术, 2020, 52(3):141-149.
|
| [12] |
JIN Xin, WANG Qixu, LI Xiang, et al. Cloud Virtual Machine Lifecycle Security Framework Based on Trusted Computing[J]. Tsinghua Science and Technology, 2019, 24(5): 520-534.
doi: 10.26599/TST.2018.9010129
|
| [13] |
QI Neng, TAN Liang. Trust Chain Model with Waterfall Characteristic Based on Trusted Virtualization Platform[J]. Journal of Computer Applications, 2018, 38(2): 327-336.
doi: 10.11772/j.issn.1001-9081.2017082159
|
|
齐能, 谭良. 具有瀑布特征的可信虚拟平台信任链模型[J]. 计算机应用, 2018, 38(2):327-336.
doi: 10.11772/j.issn.1001-9081.2017082159
|
| [14] |
LIU Haidong, GUO Songhui, SUN Lei, et al. Trusted Virtual Machine Model Based on High-Performance Cipher Coprocessor[C]// Springer. International Conference of Pioneering Computer Scientists, Engineers and Educators. Heidelberg: Springer, 2020: 705-715.
|
| [15] |
WANG Xiao, ZHANG Jianbiao, ZENG Zhiqiang. Construction Method of Trusted Virtual Execution Environment Based on Trusted Platform Control Module[J]. Journal of Beijing University of Technology, 2019, 45(6): 554-565.
|
|
王晓, 张建标, 曾志强. 基于可信平台控制模块的可信虚拟执行环境构建方法[J]. 北京工业大学学报, 2019, 45(6):554-565.
|
 ), GE Zhenwei, PAN Jingwei, CHEN Liquan
), GE Zhenwei, PAN Jingwei, CHEN Liquan