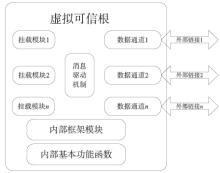
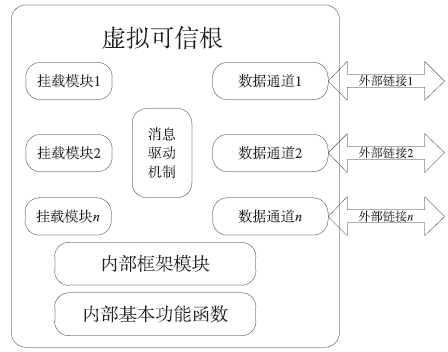
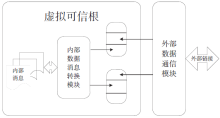
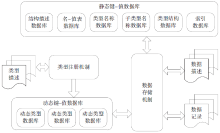
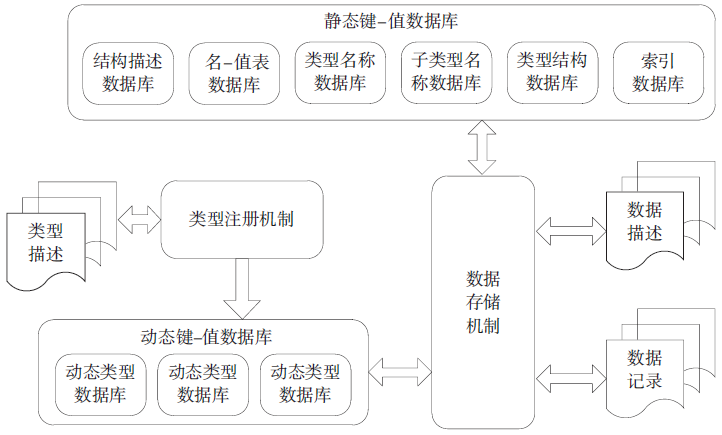
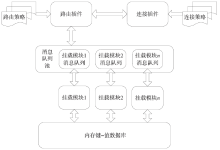
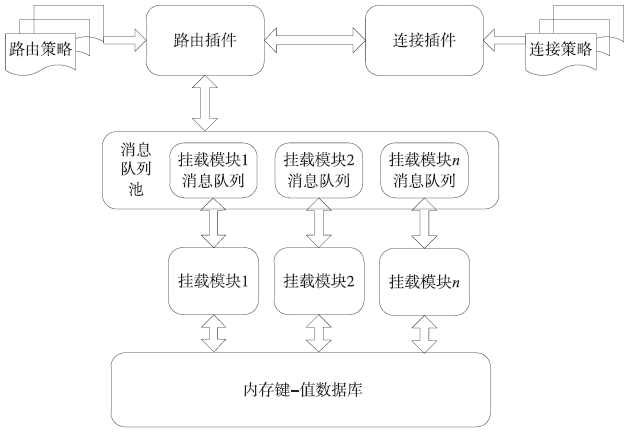
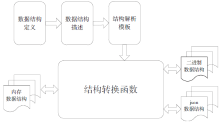
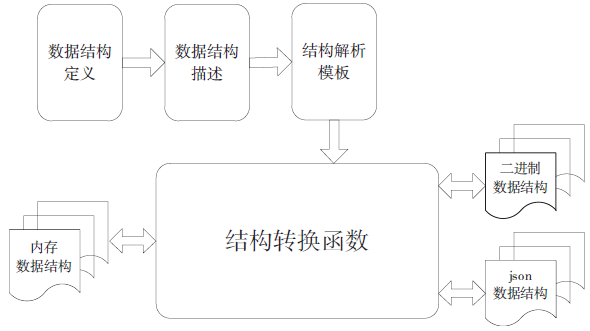
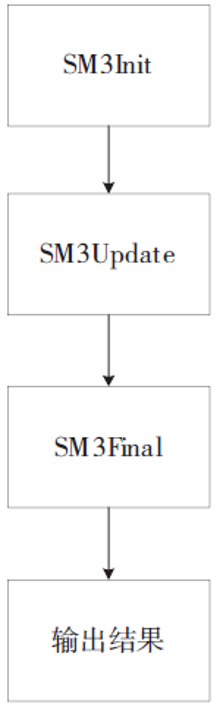
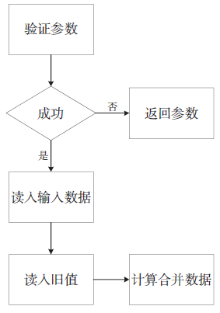
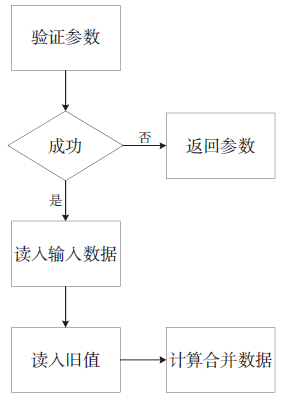
| [1] |
MELL P, GRANCE T.The NIST definition of cloud computing[J]. Communications of the Acm, 2011,53(6):50.
|
| [2] |
黄强,王高剑,米文智,等. 集中统一的可信计算平台管理模型研究及其应用[J]. 信息网络安全,2017(4):9-14.
|
| [3] |
杨波, 冯登国, 秦宇, 等. 基于TrustZone 的可信移动终端云服务安全接入方案[J]. 软件学报, 2016,27(6): 1366-1383.
|
| [4] |
张家伟,张冬梅,黄偲琪. 一种抗APT攻击的可信软件基设计与实现[J]. 信息网络安全,2017(6):49-55.
|
| [5] |
KO R K L, JAGADPRAMANA P, MOWBRAY M, et al. TrustCloud: A framework for accountability and trust in cloud computing[C]//IEEE.2011 IEEE World Congress onServices, July 4-9, 2011, Washington, DC.New York: IEEE, 2011: 584-588.
|
| [6] |
MANFERDELLI J, ROEDER T, SCHNEIDER F. The CloudproxyTao for Trusted Computing[EB/OL]., 2013-1-1.
|
| [7] |
王勇, 许荣强, 任兴田, 等. 可信计算中信任链建立的形式化验证[J]. 北京工业大学学报, 2016, 42(3): 387-392.
|
| [8] |
沈昌祥. 可信计算构筑主动防御的安全体系[J]. 信息安全与通信保密, 2016 (6): 34.
|
| [9] |
王冠,袁华浩. 基于可信根服务器的虚拟TCM密钥管理功能研究[J]. 信息网络安全,2016(4):17-22.
|
| [10] |
KANSTRÉN T, LEHTONEN S, KUKKOHOVI H. Opportunities In Using a Secure Element to Increase Confidence in Cloud Security Monitoring[C]//IEEE. InternatinalConference on Cloud Computing, June 27 - July 2,New York.New York: IEEE, 2015: 1093-1098.
|
| [11] |
OTHMAN A T, KHAN S, NAUMAN M, et al.Towards a high-level trusted computing API for Android software stack[C]//ICUIMC. International Conference on Ubiquitous Information Management and Communication, January 17-19, 2013, Kota Kinabalu.New York: ACM, 2013:1-9.
|
| [12] |
张松鸽. 云计算下可信支撑机制关键技术研究与实现[D]. 北京:北京工业大学, 2015.
|
| [13] |
ISO/IEC 11889-1:2009. Trusted Platform Module Part 1:OverviewSO/IEC 11889-1:2009. Trusted Platform Module Part 1:Overview[S].Switzerland: International Organization for Standardization,2009.
|
| [14] |
ISO/IEC 11889-1:2015. Trusted Platform Module Library Part 1:ArchitectureSO/IEC 11889-1:2015. Trusted Platform Module Library Part 1:Architecture[S].Switzerland: International Organization for Standardization, 2015.
|
| [15] |
IBM. IBM’s Softeware Trusted Platform Module(TPM)[EB/OL]. .
|
| [16] |
沈昌祥, 张大伟, 刘吉强, 等. 可信3.0 战略: 可信计算的革命性演变[J]. 中国工程科学, 2016, 18(6): 53-57.
|
| [17] |
YU W, ZHANG Y, XU H, et al.High Performance PCIe Interface for the TPCM Based on Linux Platform[C]//IEEE. International Symposium on Computational Intelligence and Design(ISCID), December 12-13, 2015, Zhejiang University,Hangzhou.NewYork: IEEE, 2015: 422-425.
|
| [18] |
GM/T 0011-2012, 可信计算密码支撑平台功能与接口规范[S].北京:国家密码管理局,2007
|
 ), Jun HU1,2,3, Xiao WANG1,2,3
), Jun HU1,2,3, Xiao WANG1,2,3