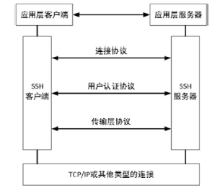
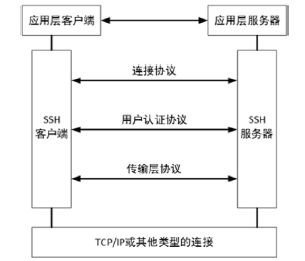
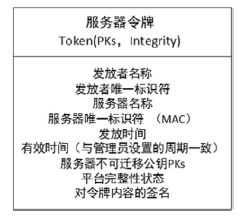
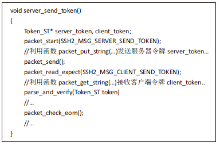
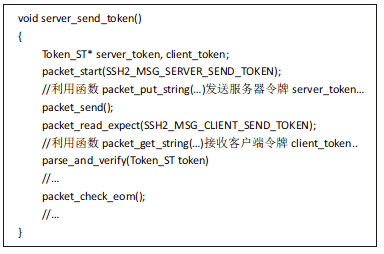
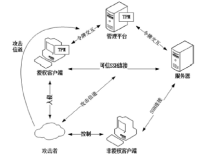
| [1] |
BARRETT D J, SILVERMANN R E.SSH, The Secure Shell[M]. Sebastopol, CA: O'Reilly, 2001.
|
| [2] |
DIERKS T, RESCORLA E. Transport Layer Security (TLS) Protocol Version 1.1, RFC 4346[EB/OL]. .
|
| [3] |
KENT S, SEO K. Security Architecture for the Internet Protocol, RFC 4301[EB/OL]..
|
| [4] |
段然,徐乃阳,胡爱群. 基于形式化分析工具的认证协议安全性研究[J]. 信息网络安全,2015(7):71-76.
|
| [5] |
LONVICKC , YLONEN T. The Secure Shell (SSH) Protocol ArchitectureRFC 4251[EB/OL]. .
|
| [6] |
常晓林,秦英,邢彬,等. SSH可信信道安全属性的形式化验证[J]. 北京交通大学学报,2012,36(2):11-18.
|
| [7] |
Trusted Computing Group. TCG Specification Architecture Overview Specification (revision 1.4)[EB/OL]. , 2016-8-1.
|
| [8] |
Trusted Computing Group. TPM Main Specification Level 2 (Version 1.2)[EB/OL]. , 2016-8-1.
|
| [9] |
YLONEN T, LONVICK C. The Secure Shell (SSH) Transport Layer ProtocolRFC 4253[EB/OL]. .
|
| [10] |
YLONEN T, LONVICK C. The Secure Shell (SSH) Authentication ProtocolRFC 4252[EB/OL]. .
|
| [11] |
YLONEN T, LONVICK C. The Secure Shell (SSH) Connection ProtocolRFC 4254[EB/OL]. .
|
| [12] |
文伟平,郭荣华,孟正,等. 信息安全风险评估关键技术研究与实现[J]. 信息网络安全,2015(2):7-14.
|
| [13] |
沈昌祥, 张焕国, 冯登国,等. 信息安全综述[J]. 中国科学:技术科学, 2007, 37(2):129-150.
|
| [14] |
SAILER R, ZHANG X, JAEGER T, et al.Design and implementation of a TCG-based Integrity Measurement Architecture[C]// IEEE. Usenix Security Symposium, August 9-13, 2004, San Diego, Ca, USA. San Diego:Conference on Usenix Security Symposium, 2004: 16.
|
| [15] |
PORITZ J,SCHUNTERM , HERREWEGHEN E V, et al. Property Attestation – Scalable and Privacy-friendly Security Assessment of Peer Computers[J]. Biotechniques, 2004, 27(3):1-6.
|
| [16] |
SADEGHI A R, STUBLEC. Property-based Attestation for Computing Platforms: Caring about Properties, not Mechanisms[C]// IEEE. New Security Paradigms Workshop 2004, September 20-23, 2004, Nova Scotia, Canada. Nova Scotia: New Security Paradigms Workshop, 2004:67-77.
|
| [17] |
STUMPF F, TAFRESCHI O, RODERP, et al. A Robust Integrity Reporting Protocol for Remote Attestation[C]// Japanese Ministry of Economy, Trade and Industry (METI). Proceedings of the Second Workshop on Advances in Trusted Computing(WATC’06 Fall),November 30-December 1, 2006, Ivy Hall AogakuKaikan, Tokyo, Japan. Tokyo, Japan: Japanese Ministry of Economy, Trade and Industry (METI), 2006:25-36.
|
| [18] |
ARMKNECHT F, GASMI Y, SADEGHI A R, et al.An efficient implementation of trusted channels based on openssl[C]//ACM. ACM Workshop on Scalable Trusted Computing (STC'06), November 3, 2008, Alexandria, VA, USA. New York, USA:ACM, 2008: 41-50.
|
 ), Yongzhong HE1, Aimin YU2
), Yongzhong HE1, Aimin YU2