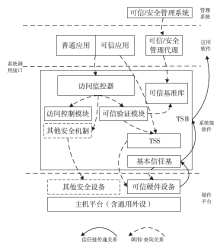
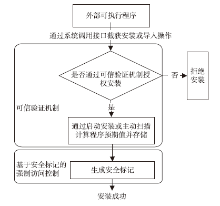
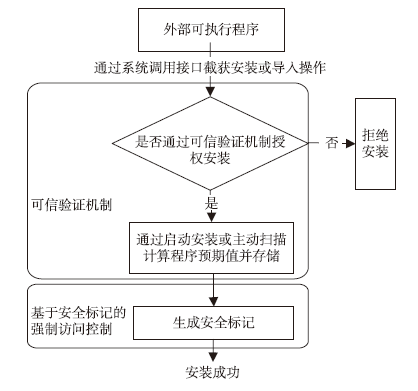
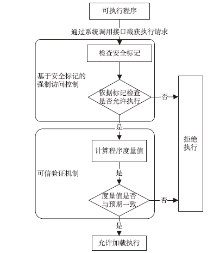
| [1] |
沈昌祥. 对当前信息安全系统的反思[C]//计算机学会计算机安全专委会.第18次全国计算机安全学术交流会,2003-08-16,哈尔滨,中国. 北京:计算机学会计算机安全专委会,2003:16-19.
|
| [2] |
Trusted Computing Group. TCG Specification Architecture Overview[EB/OL].,2006-01-15.
|
| [3] |
VIVEK H,DEEPAK C,MICHAEL F.Semantic Remote Attestation - A Virtual Machine Directed Approach to Trusted Computing[EB/OL]..
|
| [4] |
SADEHI. Bridging the Gap between TCPA/Palladium and Personal Security[EB/OL]. .
|
| [5] |
Trusted Computing Group. Cloud Computing and Security-A Natural Match[EB/OL]. .
|
| [6] |
Trusted Computing Group. TCG Guidance for Securing IoT[EB/OL]. .
|
| [7] |
沈昌祥. 可信计算的研究与发展[J].中国科学:信息科学, 2010,(4):139-166.
|
| [8] |
王冠. TPCM及可信平台主板标准[EB/OL]..
|
| [9] |
章睿. 基于可信计算技术的隐私保护研究[D]. 北京:北京交通大学, 2011.
|
| [10] |
周新,陶露菁. 可信计算及其在信息系统中的应用[J]. 指挥信息系统与技术,2011(2):28-31.
|
| [11] |
张焕国,李晶,潘丹铃,等.嵌入式系统可信平台模块研究[J]. 计算机研究与发展,2011(7):1269-1278.
|
| [12] |
尚京,徐开勇,杨启超. 一种面向集中管控系统的计算机可信启动架构[J]. 计算机工程与应用,2015,51(17):64-69.
|
| [13] |
刘传波,王催. 舰载指控系统可信计算构建技术研究[J]. 计算机与数字工程, 2014(12):2439-2442.
|
| [14] |
刘巍然,刘建伟. Android操作系统可信计算平台架构[J]. 武汉大学学报(理学版), 2013(4):159-164.
|
| [15] |
王东霞,赵刚. 安全体系结构与安全标准体系[J]. 计算机工程与应用,2005(8):149-152.
|
| [16] |
李柏松. 由Windows的安全实践看可信计算的价值和局限[J]. 信息安全与通信保密, 2014(9):100-107.
|
| [17] |
黄强,沈昌祥.可信计算技术对操作系统的安全服务支持[J]. 武汉大学学报(理学版), 2004, 50(S1):15-18.
|
| [18] |
ZHANG H G.Surrey on Cyberspace Security[J]. Science China Information Sciences, 2015, 58(11):143.
|
| [19] |
白云等. 信息系统安全体系结构发展研究[J]. 空军工程大学学报(自然科学版),2010,11(5):75-80.
|
| [20] |
李超,王红胜,陈军广,等. 加强计算机终端信息安全的两种解决方案[J].计算机技术与发展,2009,19(1):165-167.
|
| [21] |
聂晓伟, 冯登国. 基于可信平台的一种访问控制策略框架——TXACML[J].计算机研究与发展, 2008,45(10):1676-1686.
|
| [22] |
谭良, 周明天. 基于可信计算平台的静态客体可信验证系统的设计与实现[J]. 计算机科学, 2008,35(2):253-255.
|
| [23] |
李勇. 基于可信计算的应用环境安全研究[D]. 郑州:解放军信息工程大学, 2011.
|
| [24] |
Dod-Std. Department of Defense Standard. DoD Trusted Computer System Evaluation Criteria[EB/OL]. ,1999-05-15.
|