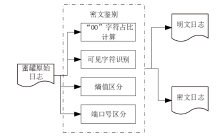
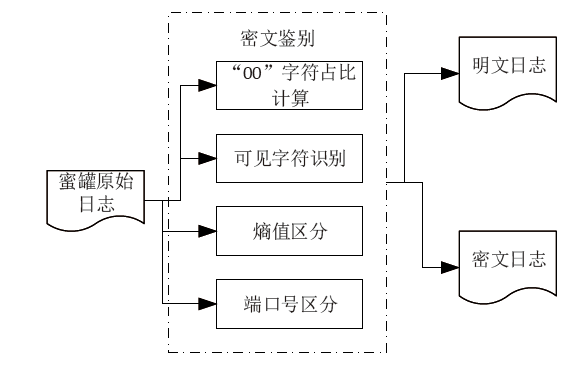
Netinfo Security ›› 2022, Vol. 22 ›› Issue (10): 82-90.doi: 10.3969/j.issn.1671-1122.2022.10.012
Previous Articles Next Articles
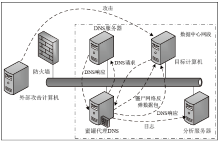
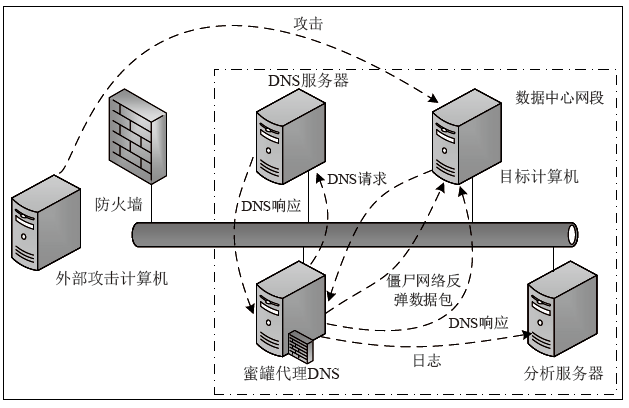
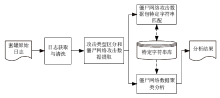
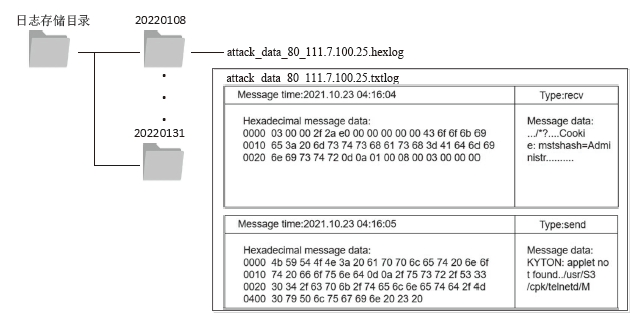
Analysis of Botnet Attack Data Based on Log
ZHU Tao1( ), XIA Lingling1, LI Penghui1, XU Zhongyi2
), XIA Lingling1, LI Penghui1, XU Zhongyi2
- 1. Department of Computer Information and Cyber Security, Jiangsu Police Institute, Nanjing 210031, China
2. Beijing Qihoo Technology Co., Ltd., Beijing 100020, China
-
Received:2022-07-03Online:2022-10-10Published:2022-11-15 -
Contact:ZHU Tao E-mail:zhutaonj@163.com
CLC Number:
Cite this article
ZHU Tao, XIA Lingling, LI Penghui, XU Zhongyi. Analysis of Botnet Attack Data Based on Log[J]. Netinfo Security, 2022, 22(10): 82-90.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.10.012
| 序号 | 特定字符串 | 类型 |
|---|---|---|
| 1 | Mozi.a | 特定词T4 |
| 2 | http://z.shavsl.com | 下载地址T2 |
| 3 | http://crypto.htxreceive.top/ | 下载地址T2 |
| 4 | http://oracle.zzhreceive.top/ | 下载地址T2 |
| 5 | http://185.142.239.128/ | 下载地址T2 |
| 6 | http://188.213.49.155/ | 下载地址T2 |
| 7 | http://194.147.142.88/ | 下载地址T2 |
| 8 | /MyPlugin | 交互报文T1 |
| 9 | http://103.209.103.16/ | 下载地址T2 |
| 10 | http://199.19.226.117/ | 下载地址T2 |
| 11 | http://205.185.121.185/ | 下载地址T2 |
| 12 | http://86.105.195.120/ | 下载地址T2 |
| 13 | http://104.192.82.138/ | 下载地址T2 |
| 14 | Mozi.m | 特定词T4 |
| 15 | http://185.224.129.251/ | 下载地址T2 |
| 16 | http://149.28.85.17/ | 下载地址T2 |
| 17 | http://128.199.240.129/ | 下载地址T2 |
| 18 | STOR/Photo.scr | 执行操作T3 |
| 19 | http://194.87.139.103/ | 下载地址T2 |
| 20 | http://45.133.203.192/ | 下载地址T2 |
| 21 | http://85.239.33.9/ | 下载地址T2 |
| 22 | http://34.66.229.152/ | 下载地址T2 |
| 序号 | 报文数据属性 | 含义 |
|---|---|---|
| 1 | attackPort | 受到攻击的端口号 |
| 2 | packetNumber | 攻击过程中的包数量 |
| 3 | recvPacketNumber | 攻击过程中接收的包数量 |
| 4 | sendPacketNumber | 攻击过程中发送的包数量 |
| 5 | recvPktSizeAvg | 攻击过程中接收的包的平均大小 |
| 6 | sendPktSizeAvg | 攻击过程中发送的包的平均大小 |
| 7 | recvPktSizeMin | 攻击过程中接收的最小包的大小 |
| 8 | sendPktSizeMin | 攻击过程中发送的最小包的大小 |
| 9 | recvPktSizeMax | 攻击过程中接收的最大包的大小 |
| 10 | sendPktSizeMax | 攻击过程中发送的最大包的大小 |
| 11 | recvPktSizeStd | 攻击过程中接收的包的大小的标准差 |
| 12 | sendPktSizeStd | 攻击过程中发送的包的大小的标准差 |
| 13 | timeDuration | 持续时间 |
| 14 | timeDelayAve | 平均延迟时间 |
| 15 | timeDelayMax | 最大延迟时间 |
| 16 | timeDelayMin | 最小延迟时间 |
| 17 | timeDelayMedian | 延迟时间中间值 |
| 18 | timeDelayStd | 延迟时间标准差 |
| 序号 | 报文数据属性 | 重要性 | 簇1 | 簇2 | 簇3 |
|---|---|---|---|---|---|
| 1 | attackPort | 1 | 80 | 6379 | 5555 |
| 2 | packetNumber | 1 | 1.46 | 55.19 | 18.99 |
| 3 | recvPacketNumber | 1 | 1.42 | 26.37 | 14.24 |
| 4 | sendPacketNumber | 1 | 0.04 | 28.83 | 4.75 |
| 5 | recvPktSizeAvg | 1 | 232.85 | 375.15 | 112.86 |
| 6 | sendPktSizeAvg | 0 | 0.00 | 0.00 | 0.00 |
| 7 | recvPktSizeMin | 1 | 212.63 | 5.02 | 49.51 |
| 8 | sendPktSizeMin | 0 | 0.00 | 0.00 | 0.00 |
| 9 | recvPktSizeMax | 1 | 257.81 | 12862.02 | 470.78 |
| 10 | sendPktSizeMax | 0 | 0.00 | 0.00 | 0.00 |
| 11 | recvPktSizeStd | 1 | 4601.21 | 377825.12 | 74255.04 |
| 12 | sendPktSizeStd | 0 | 0.00 | 0.00 | 0.00 |
| 13 | timeDuration | 1 | 534.27 | 234.82 | 60668.96 |
| 14 | timeDelayAve | 1 | 123.06 | 3.12 | 7373.01 |
| 15 | timeDelayMax | 1 | 381.42 | 231.93 | 27280.19 |
| 16 | timeDelayMin | 0.02 | 0.11 | 0.00 | 264.96 |
| 17 | timeDelayMedian | 0.25 | 0.14 | 0.00 | 1108.72 |
| 18 | timeDelayStd | 1 | 827693.26 | 64625.06 | 123535682.12 |
| [1] | LI Ke, FANG Binxing, CUI Xiang, et al. Study of Botnets Trends[J]. Journal of Computer Research and Development, 2016, 53(10): 2189-2206. |
| 李可, 方滨兴, 崔翔, 等. 僵尸网络发展研究[J]. 计算机研究与发展, 2016, 53(10): 2189-2206. | |
| [2] | CUI Lijuan, MA Weiguo, ZHAO Wei, et al. A Survey of Botnet[J]. Journal of Information Security Research, 2017, 3(7): 589-600. |
| 崔丽娟, 马卫国, 赵巍, 等. 僵尸网络综述[J]. 信息安全研究, 2017, 3(7): 589-600. | |
| [3] | ZHOU Anmin, ZHONG Yi, ZUO Zheng, et al. D-BitBot: A P2P Duplex Botnet Model in Bitcoin Network[J]. Journal of Harbin Institute of Technology, 2020, 52(5): 66-74. |
| 周安民, 钟毅, 左政, 等. D-BitBot:比特币网络双向通信的P2P僵尸网络模型[J]. 哈尔滨工业大学学报, 2020, 52(5): 66-74. | |
| [4] | WU Di, CUI Xiang, LIU Qixu, et al. Research on Ubiquitous Botnet[J]. Netinfo Security, 2018, 18(7): 16-28. |
| 吴迪, 崔翔, 刘奇旭, 等. 泛在僵尸网络发展研究[J]. 信息网络安全, 2018, 18(7): 16-28. | |
| [5] | GE Xin, ZOU Futai, GUO Wanda, et al. Review on the Development of Social Botnets[J]. Computer Engineering, 2022, 48(8): 12-24. |
| 葛昕, 邹福泰, 郭万达, 等. 社交僵尸网络发展综述[J]. 计算机工程, 2022, 48(8): 12-24. | |
| [6] | FAN Yiyan, WU Guorui. Research of Dynamic Botnet Model[J]. Journal of Computer Applications, 2010, 30(3): 692-694. |
| 范轶彦, 邬国锐. 动态僵尸网络模型研究[J]. 计算机应用, 2010, 30(3): 692-694. | |
| [7] | HUANG Biao, CHENG Shuping, OUYANG Chenxing, et al. Botnet Propagation Model with Two-Factor on Scale-Free Network[J]. Computer Science, 2012, 39(10): 78-81, 114. |
| 黄彪, 成淑萍, 欧阳晨星, 等. 无尺度网络下具有双因素的僵尸网络传播模型[J]. 计算机科学, 2012, 39(10): 78-81, 114. | |
| [8] | NIU Weina, ZHANG Xiaosong, YANG Guowu, et al. Modeling and Analysis of Botnet with Heterogeneous Infection Rate[J]. Computer Science, 2018, 45(7): 135-138, 153. |
| 牛伟纳, 张小松, 杨国武, 等. 具有异构感染率的僵尸网络建模与分析[J]. 计算机科学, 2018, 45(7): 135-138, 153. | |
| [9] | OUYANG Chenxing, TAN Liang. New Propagation Model of Botnet on Scale-Free Network[J]. Computer Engineering and Applications, 2013, 49(9): 110-114. |
| 欧阳晨星, 谭良. 无尺度网络下的僵尸网络传播模型研究[J]. 计算机工程与应用, 2013, 49(9): 110-114. | |
| [10] | FENG Liping, SONG Lipeng, WANG Hongbin, et al. Propagation Modeling and Analysis of Peer-to-Peer Botnet[J]. Journal of Computer Applications, 2015, 35(1): 68-71. |
| 冯丽萍, 宋礼鹏, 王鸿斌, 等. P2P僵尸网络的传播建模与分析[J]. 计算机应用, 2015, 35(1): 68-71. | |
| [11] | ZHOU Anmin, ZHONG Yi, ZUO Zheng, et al. D-BitBot: A P2P Duplex Botnet Model in Bitcoin Network[J]. Journal of Harbin Institute of Technology, 2020, 52(5): 66-74. |
| 周安民, 钟毅, 左政, 等. D-BitBot:比特币网络双向通信的P2P僵尸网络模型[J]. 哈尔滨工业大学学报, 2020, 52(5): 66-74. | |
| [12] | ZHANG Xiran, LIU Wanping, LONG Hua. Dynamic Model and Analysis of Spreading of Botnet Viruses over Internet of Things[J]. Computer Science, 2022, 49(S1): 738-743. |
| 张翕然, 刘万平, 龙华. 物联网僵尸网络病毒的传播动力学模型与分析[J]. 计算机科学, 2022, 49(S1): 738-743. | |
| [13] | XIA Qin, WANG Zhiwen, LIU Lu. Tracking Botnet Activity Based on Co-Occurrence Relation of Domain Name System Queries[J]. Journal of Xi’an Jiaotong University, 2012, 46(4): 7-12. |
| 夏秦, 王志文, 刘璐. 基于域名共现行为的僵尸网络行为追踪[J]. 西安交通大学学报, 2012, 46(4): 7-12. | |
| [14] | WANG Hailong, TANG Yong, GONG Zhenghu. Signature Generation Model for Botnet Command and Control Channel[J]. Computer Engineering & Science, 2013, 35(2): 62-67. |
| 王海龙, 唐勇, 龚正虎. 僵尸网络命令与控制信道的特征提取模型研究[J]. 计算机工程与科学, 2013, 35(2): 62-67. | |
| [15] | NIU Weina, JIANG Tianyu, ZHANG Xiaosong, et al. Fast-Flux Botnet Detection Method Based on Spatiotemporal Feature of Network Traffic[J]. Journal of Electronics & Information Technology, 2020, 42(8): 1872-1880. |
| 牛伟纳, 蒋天宇, 张小松, 等. 基于流量时空特征的fast-flux僵尸网络检测方法[J]. 电子与信息学报, 2020, 42(8): 1872-1880. | |
| [16] | HE Yukun, LI Qiang, JI Yuede, et al. Analysis of Botnet Detection Technique Based on Traffic Graph[J]. Journal of Jilin University (Science Edition), 2013, 51(4): 681-688. |
| 何毓锟, 李强, 嵇跃德, 等. 基于流量图的僵尸网络检测技术分析[J]. 吉林大学学报(理学版), 2013, 51(4): 681-688. | |
| [17] | BAI Jun, XIA Jingbo, ZHANG Wenjing, et al. Rapid Botnet Detecting Method Based on Multi-Dimensional Information Divergence[J]. Journal of Huazhong University of Science and Technology(Natural Science Edition), 2014, 42(9): 28-32. |
| 柏骏, 夏靖波, 张文静, 等. 基于多维信息散度的僵尸网络快速检测方法[J]. 华中科技大学学报(自然科学版), 2014, 42(9): 28-32. | |
| [18] | CHEN Ruidong, ZHAO Lingyuan, ZHANG Xiaosong. Botnet Identification Technology Based on Fuzzy Clustering[J]. Computer Engineering, 2018, 44(10): 46-50. |
| 陈瑞东, 赵凌园, 张小松. 基于模糊聚类的僵尸网络识别技术[J]. 计算机工程, 2018, 44(10): 46-50. | |
| [19] | XIAO Qi, SU Kaiyu. Botnet Traffic Detection Based on Random Forest Algorithm[J]. Microelectronics & Computer, 2019, 36(3): 43-47. |
| 肖琦, 苏开宇. 基于随机森林的僵尸网络流量检测[J]. 微电子学与计算机, 2019, 36(3): 43-47. | |
| [20] | ZOU Futai, TAN Yue, WANG Lin, et al. Botnet Detection Based on Generative Adversarial Network[J]. Journal on Communications, 2021, 42(7): 95-106. |
| 邹福泰, 谭越, 王林, 等. 基于生成对抗网络的僵尸网络检测[J]. 通信学报, 2021, 42(7): 95-106. | |
| [21] | LIN Honggang, ZHANG Yunli, GUO Nanxin, et al. P2P Botnet Detection Method Based on Graph Neural Network[J]. Advanced Engineering Sciences, 2022, 54(2): 65-72. |
| 林宏刚, 张运理, 郭楠馨, 等. 基于图神经网络的P2P僵尸网络检测方法[J]. 工程科学与技术, 2022, 54(2): 65-72. | |
| [22] | FENG Liping, HAN Qi, WANG Hongbin, et al. Effective Immune Measures on P2P Botnets[J]. Journal of Computer Applications, 2012, 32(9): 2617-2619, 2623. |
| 冯丽萍, 韩琦, 王鸿斌, 等. P2P僵尸网络的有效免疫措施[J]. 计算机应用, 2012, 32(9): 2617-2619, 2623. | |
| [23] | YING Lingyun, FENG Dengguo, SU Purui. P2P-Based Super Botnet: Threats and Defenses[J]. Acta Electronica Sinica, 2009, 37(1): 31-37. |
| 应凌云, 冯登国, 苏璞睿. 基于P2P的僵尸网络及其防御[J]. 电子学报, 2009, 37(1): 31-37. | |
| [24] | CHEN Duanbing, WAN Ying, TIAN Junwei, et al. P2P Botnet Control Strategy Based on Social Network Analysis[J]. Computer Science, 2009, 36(6): 101-104, 111. |
| 陈端兵, 万英, 田军伟, 等. 一种基于社会网络分析的P2P僵尸网络反制策略[J]. 计算机科学, 2009, 36(6): 101-104, 111. | |
| [25] | ZHANG Sijie, SU Yang. Defense System of P2P Botnet Based on Domain[J]. Computer Engineering and Design, 2013, 34(7): 2291-2295. |
| 张斯捷, 苏旸. 基于域的P2P僵尸网络防御体系[J]. 计算机工程与设计, 2013, 34(7): 2291-2295. | |
| [26] | YANG M S, SINAGA K P. A Feature-Reduction Multi-View K-Means Clustering Algorithm[J]. IEEE Access, 2019(7): 114472-114486. |
| [27] | TUAN T A, LONG H V, SON L H, et al. Performance Evaluation of Botnet DDoS Attack Detection Using Machine Learning[J]. Evolutionary Intelligence, 2020, 13(2): 283-294. |
| [28] | CHIU T, FANG Dongping, CHEN J, et al. A Robust and Scalable Clustering Algorithm for Mixed Type Attributes in Large Database Environment[C]// ACM. ACM SIGKDD International Conference on Knowledge Discovery and Data Mining. New York: ACM, 2001: 263-268. |
| [1] | LANG Bo, XIE Chong, CHEN Shaojie, LIU Hongyu. Fast-Flux Malicious Domain Name Detection Method Based on Multimodal Feature Fusion [J]. Netinfo Security, 2022, 22(4): 20-29. |
| [2] | LIU Jiqiang, HE Jiahao, ZHANG Jiancheng, HUANG Xuezhen. Log Compression Optimization Method Based on Parser Tree [J]. Netinfo Security, 2022, 22(4): 30-39. |
| [3] | HU Wei, ZHAO Wenlong, CHEN Lu, FU Wei. An Improved JSMA Algorithm against Sample Attack Based on Logits Vector [J]. Netinfo Security, 2022, 23(3): 62-69. |
| [4] | JIN Shuting, HE Jingsha, ZHU Nafei, PAN Shijia. Research on Privacy Protection Access Control Mechanism Based on Ontology Reasoning [J]. Netinfo Security, 2021, 21(8): 52-61. |
| [5] | SONG Yulong, WANG Lei, WU Xinrong, ZENG Weijun. Research on WSN Topological Invulnerability Based on Adaptive Simulated Annealing Particle Swarm Optimization Algorithm [J]. Netinfo Security, 2021, 21(6): 89-96. |
| [6] | ZHENG Jun, NIE Rong, WANG Shouxin, TAN Yu’an. Attribute Weight Snapshot Selection Strategy Based on Docker Container Fault Recovery [J]. Netinfo Security, 2021, 21(5): 12-18. |
| [7] | LI Kunchang, SHI Runhua, LI En. Survey on Data Aggregation and Privacy Protection of User Query in Smart Grid [J]. Netinfo Security, 2021, 21(11): 65-74. |
| [8] | LIU Hong, ZHANG Yuejin, ZHAO Wenxia, YANG Mu. A Security Management Framework for Data Sensitivity and Multidimensional Classification [J]. Netinfo Security, 2021, 21(10): 48-53. |
| [9] | MA Xiao, CAI Manchun, LU Tianliang. Malicious Domain Name Training Data Generation Technology Based on Improved CNN Model [J]. Netinfo Security, 2021, 21(10): 69-75. |
| [10] | WANG Jianxin, ZHOU Shiqiang, XIAO Chaoen, ZHANG Lei. High-speed Implementation of FESH Block Cipher Algorithm Based on FPGA [J]. Netinfo Security, 2021, 21(1): 57-64. |
| [11] | LU Jiali. Log Anomaly Detection Method Based on Improved Time Series Model [J]. Netinfo Security, 2020, 20(9): 1-5. |
| [12] | SHEN Jinwei, ZHAO Yi, LIANG Chunlin, ZHANG Ping. RFID Group Tag Ownership Transfer Protocol Based on Cyclic Grouping Function [J]. Netinfo Security, 2020, 20(9): 102-106. |
| [13] | LI Qiao, LONG Chun, WEI Jinxia, ZHAO Jing. A Hybrid Model of Intrusion Detection Based on LMDR and CNN [J]. Netinfo Security, 2020, 20(9): 117-121. |
| [14] | LIU Hong, XIE Yongheng, WANG Guowei, JIANG Shuai. Ontology-based Cross-domain Security Analysis [J]. Netinfo Security, 2020, 20(9): 82-86. |
| [15] | SONG Yubo, FAN Ming, YANG Junjie, HU Aiqun. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||