Netinfo Security ›› 2022, Vol. 22 ›› Issue (4): 30-39.doi: 10.3969/j.issn.1671-1122.2022.04.004
Previous Articles Next Articles
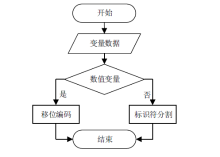
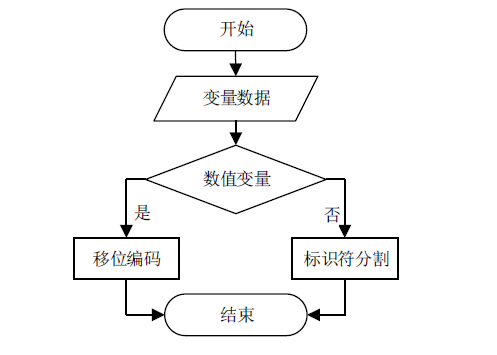
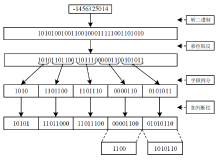
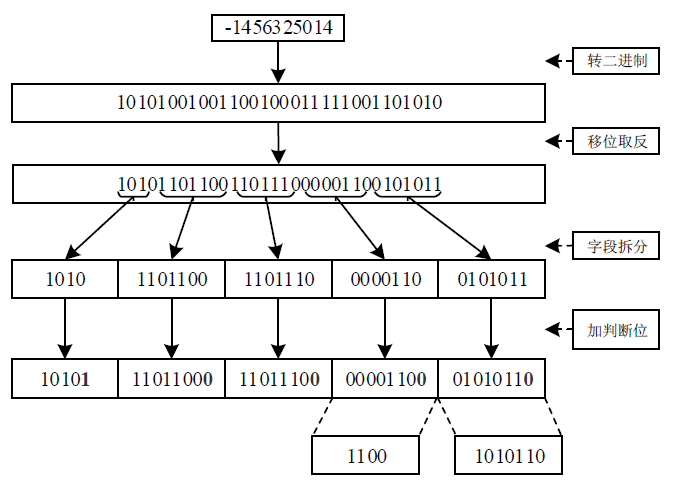
Log Compression Optimization Method Based on Parser Tree
LIU Jiqiang1( ), HE Jiahao1, ZHANG Jiancheng2,3, HUANG Xuezhen4
), HE Jiahao1, ZHANG Jiancheng2,3, HUANG Xuezhen4
- 1. Department of Computer and Information Technology, Beijing Jiaotong University, Beijing 100044, China
2. Shandong Computer Science Center, Jinan 250014, China
3. Shandong Zhengzhong Information Technology Co.,Ltd, Jinan 250014, China
4. The First Research Institute of the Ministry of Public Security, Beijing 100048, China
-
Received:2022-01-12Online:2022-04-10Published:2022-05-12 -
Contact:LIU Jiqiang E-mail:jqliu@bjtu.edu.cn
CLC Number:
Cite this article
LIU Jiqiang, HE Jiahao, ZHANG Jiancheng, HUANG Xuezhen. Log Compression Optimization Method Based on Parser Tree[J]. Netinfo Security, 2022, 22(4): 30-39.
share this article
| [1] | SAYOOD K. Introduction to Data Compression[M]. San Francisco: Morgan Kaufmann, 2017. |
| [2] |
CLEARY J, WITTEN I. Data Compression Using Adaptive Coding and Partial String Matching[J]. IEEE Transactions on Communications, 1984, 32(4): 396-402.
doi: 10.1109/TCOM.1984.1096090 URL |
| [3] | SKIBIŃSKI P, SWACHA J. Fast and Efficient Log File Compression[C]// Springer. CEUR Workshop Proceedings of the 11th East-European Conference on Advances in Databases and Information Systems(ADBIS). Heidelberg: Springer, 2007: 330-342. |
| [4] | GRABOWSKI S, DEOROWICZ S. Web Log Compression[EB/OL]. [2021-11-22]. https://journals.bg.agh.edu.pl/AUTOMATYKA/2007-03/Auto36.pdf . |
| [5] | DEOROWICZ S, GRABOWSKI S. Efficient Preprocessing for Web Log Compression[EB/OL]. [2021-11-22]. https://www.researchgate.net/publication/309732616_Efficient_Preprocessing_for_Web_log_compression . |
| [6] | DEOROWICZ S, GRABOWSKI S. Sub-Atomic Field Processing for Improved Web Log Compression[C]// IEEE. 2008 International Conference on Modern Problems of Radio Engineering, Telecommunications and Computer Science(TCSET). New Jersey: IEEE, 2008: 551-556. |
| [7] | HÄTÖNEN K, BOULICAUT J F, KLEMETTINEN M, et al. Comprehensive Log Compression with Frequent Patterns[C]// Springer. International Conference on Data Warehousing and Knowledge Discovery. Heidelberg: Springer, 2003: 360-370. |
| [8] | WANG Yanfeng, WANG Zheng, YAN Baoping. High-Efficient DNS Log Compression Algorithm[J]. Computer Engineering, 2010, 36(15): 32-35. |
| 王艳峰, 王正, 阎保平. 一种高效的DNS日志压缩算法[J]. 计算机工程, 2010, 36(15):32-35. | |
| [9] | CHRISTENSEN R. Improving Compression of Massive Log Data[EB/OL]. [2021-11-22]. https://my.eng.utah.edu/-robertc/papers/uthesis-rc.pdf . |
| [10] | JANG J H, LEE S M, KIM S D, et al. Accelerating Forex Trading System through Transaction Log Compression[C]// IEEE. 2014 International SoC Design Conference(ISOCC). New Jersey: IEEE, 2014: 74-75. |
| [11] | HE Pinjia, ZHU Jieming, ZHENG Zibin, et al. Drain: An Online Log Parsing Approach with Fixed Depth Tree[C]// IEEE. 2017 IEEE International Conference on Web Services(ICWS). New Jersey: IEEE, 2017: 33-40. |
| [12] | LIU Jinyang, ZHU Jieming, HE Shilin, et al. Logzip: Extracting Hidden Structures via Iterative Clustering for Log Compression[C]// IEEE. 34th IEEE/ACM International Conference on Automated Software Engineering(ASE). New Jersey: IEEE, 2019: 863-873. |
| [13] |
MAKANJU A, ZINCIR-HEYWOOD A N, MILIOS E E. A Lightweight Algorithm for Message Type Extraction in System Application Logs[J]. IEEE Transactions on Knowledge and Data Engineering, 2011, 24(11): 1921-1936.
doi: 10.1109/TKDE.2011.138 URL |
| [14] | MESSAOUDI S, PANICHELLA A, BIANCULLI D, et al. A Search-Based Approach for Accurate Identification of Log Message Formats[C]// IEEE. 26th International Conference on Program Comprehension(ICPC). New Jersey: IEEE, 2018: 167-177. |
| [15] | VAARANDI R. A Data Clustering Algorithm for Mining Patterns from Event Logs[C]// IEEE. 3rd IEEE Workshop on IP Operations & Management(IPOM 2003). New Jersey: IEEE, 2003: 119-126. |
| [16] | ZHU Jieming, HE Shilin, LIU Jinyang, et al. Tools and Benchmarks for Automated Log Parsing[C]// IEEE. 41st International Conference on Software Engineering: Software Engineering in Practice(ICSE-SEIP). New Jersey: IEEE, 2019: 121-130. |
| [17] | FU Qiang, LOU Jianguang, WANG Yi, et al. Execution Anomaly Detection in Distributed Systems through Unstructured Log Analysis[C]// IEEE. 9th IEEE International Conference on Data Mining. New Jersey: IEEE, 2009: 149-158. |
| [18] | TANG Liang, LI Tao, PERNG C S. LogSig: Generating System Events from Raw Textual Logs[C]// ACM. 20th ACM International Conference on Information and Knowledge Management. New York: ACM, 2011: 785-794. |
| [19] | MIZUTANI M. Incremental Mining of System Log Format[C]// IEEE. 2013 IEEE International Conference on Services Computing. New Jersey: IEEE, 2013: 595-602. |
| [20] | SHIMA K. Length Matters: Clustering System Log Messages Using Length of Words[EB/OL]. [2021-11-22]. https://arxiv.org/pdf/1611.03213.pdf . |
| [21] | HAMOONI H, DEBNATH B, XU Jianwu, et al. Logmine: Fast Pattern Recognition for Log Analytics[C]// ACM. 25th ACM International on Conference on Information and Knowledge Management. New York: ACM, 2016: 1573-1582. |
| [22] | VAARANDI R. A Data Clustering Algorithm for Mining Patterns from Event Logs[C]// IEEE. 3rd IEEE Workshop on IP Operations & Management(IPOM 2003). New Jersey: IEEE, 2003: 119-126. |
| [23] | NAGAPPAN M, VOUK M A. Abstracting Log Lines to Log Event Types for Mining Software System Logs[C]// IEEE. 7th IEEE Working Conference on Mining Software Repositories(MSR 2010). New Jersey: IEEE, 2010: 114-117. |
| [24] | MAKANJU A A O, ZINCIR-HEYWOOD A N, MILIOS E E. Clustering Event Logs Using Iterative Partitioning[C]// ACM. 15th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining. New York: ACM, 2009: 1255-1264. |
| [25] | JIANG Zhenming, HASSAN A E, FLORA P, et al. Abstracting Execution Logs to Execution Events for Enterprise Applications(Short Paper)[C]// IEEE. 8th International Conference on Quality Software. New Jersey: IEEE, 2008: 181-186. |
| [26] |
WITTEN I H, NEAL R M, CLEARY J G. Arithmetic Coding for Data Compression[J]. Communications of the ACM, 1987, 30(6): 520-540.
doi: 10.1145/214762.214771 URL |
| [27] | DU Min, LI Feifei. Spell: Streaming Parsing of System Event Logs[C]// IEEE. 16th International Conference on Data Mining(ICDM). New Jersey: IEEE, 2016: 859-864. |
| [28] | LIN Hao, ZHOU Jingyu, YAO Bin, et al. Cowic: A Column-Wise Independent Compression for Log Stream Analysis[C]// IEEE. 15th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing. New Jersey: IEEE, 2015: 21-30. |
| [1] | LANG Bo, XIE Chong, CHEN Shaojie, LIU Hongyu. Fast-Flux Malicious Domain Name Detection Method Based on Multimodal Feature Fusion [J]. Netinfo Security, 2022, 22(4): 20-29. |
| [2] | JIN Bo, TANG Qianjin, TANG Qianlin. Interpretation of the Top 10 Development Trends of Network Security in 2022 by CCF Computer Security Professional Committee [J]. Netinfo Security, 2022, 22(4): 1-6. |
| [3] | ZHANG Wei, XU Zhigang, CHEN Yunfang, HUANG Haiping. Design and Implementation of a SDN Honeynet Based on Dynamic Docker [J]. Netinfo Security, 2022, 22(4): 40-48. |
| [4] | WANG Ziheng, WU Han, XIE Jianguo, CHEN Xiaoming. Cross-Network Implementation of Superlattice Key Distribution Based on VLAN [J]. Netinfo Security, 2022, 22(4): 49-57. |
| [5] | LIU Longgeng. Research on Association Algorithm of Heterogeneous Network Security Monitoring [J]. Netinfo Security, 2022, 22(4): 58-66. |
| [6] | LYU Guohua, HU Xuexian, YANG Ming, XU Min. Ship AIS Trajectory Classification Algorithm Based on Federated Random Forest [J]. Netinfo Security, 2022, 22(4): 67-76. |
| [7] | TANG Ming, LI Cong, LI Yongbo, YUE Tianyu. Study on Static Detection of Timing Side Channel for RISC-V Architecture [J]. Netinfo Security, 2022, 22(4): 7-19. |
| [8] | LYU Kaixin, LI Zhihui, HEI Jiliao, SONG Yun. Optimal Information Rate Calculation Based on a Class of Graph Access Structure [J]. Netinfo Security, 2022, 22(4): 77-85. |
| [9] | HUANG Baohua, QU Xi, ZHENG Huiying, XIONG Tinggang. A Credit-Based Byzantine Fault Tolerance Consensus Algorithm [J]. Netinfo Security, 2022, 22(4): 86-92. |
| [10] | FENG Jingyu, SHI Yifei, WANG Teng. Crowd Spectrum Sensing Reinforcement Scheme Against Primary-secondary Collusive Attack in Smart Grid [J]. Netinfo Security, 2022, 23(3): 1-9. |
| [11] | LI Guoqi, HONG Sheng, LAN Xueting, ZHANG Hong. The Security Reference Model of the Multi-rotor UAV System [J]. Netinfo Security, 2022, 23(3): 10-19. |
| [12] | SHI Runhua, WANG Shuhao, LI Kunchang. A Lightweight Cross-domain Mutual Authentication Scheme in V2G Networks [J]. Netinfo Security, 2022, 23(3): 20-28. |
| [13] | GU Zhaojun, YANG Rui, SUI He. System Attack Surface Modeling Method in Network [J]. Netinfo Security, 2022, 23(3): 29-38. |
| [14] | FENG Guangsheng, ZHANG Yizhe, SUN Jiayu, LYU Hongwu. Key Technologies and Advances in the Research on Automated Exploitation of Computer System Vulnerabilities [J]. Netinfo Security, 2022, 23(3): 39-52. |
| [15] | LI Li, LI Zequn, LI Xuemei, SHI Guozhen. FPGA Realization of Physical Unclonable Function Based on Cross-coupling Circuit [J]. Netinfo Security, 2022, 23(3): 53-61. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||