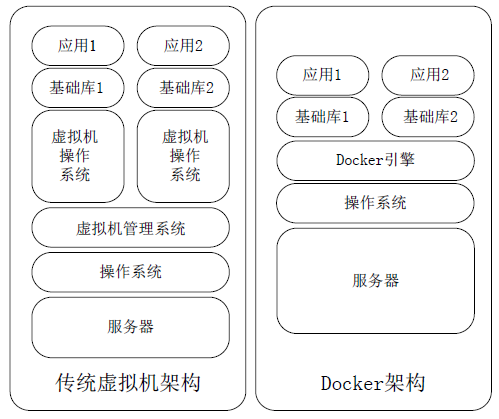
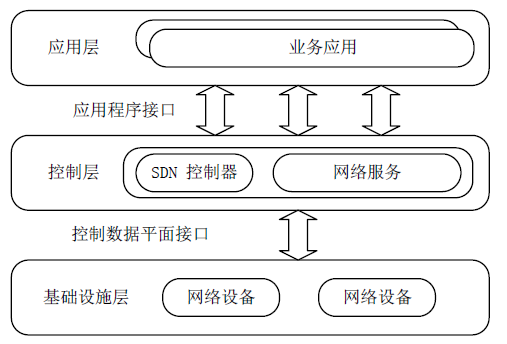
Netinfo Security ›› 2022, Vol. 22 ›› Issue (4): 40-48.doi: 10.3969/j.issn.1671-1122.2022.04.005
Previous Articles Next Articles
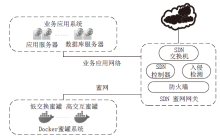
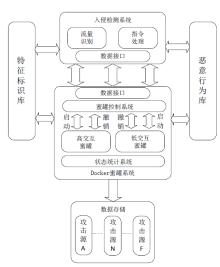
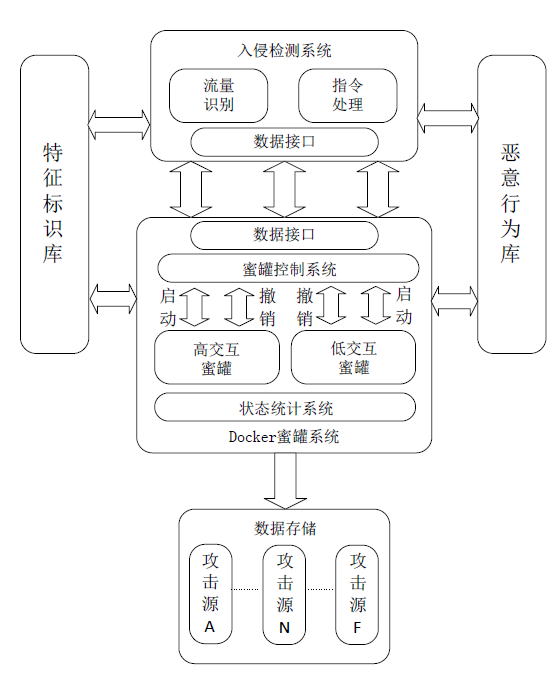
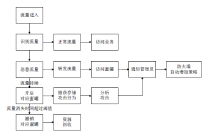
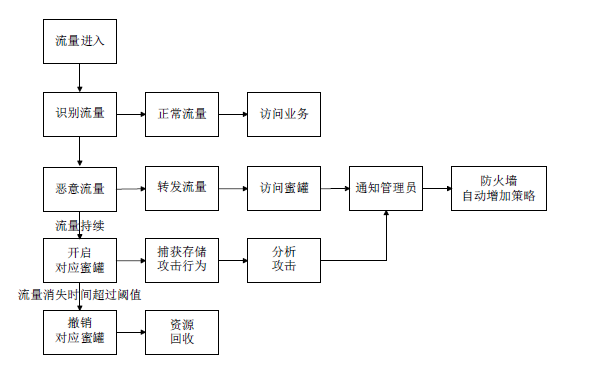
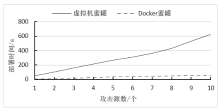
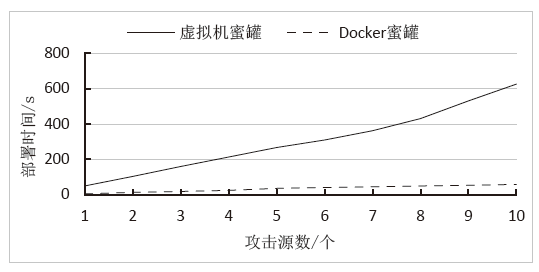
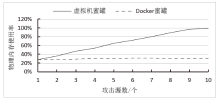
Design and Implementation of a SDN Honeynet Based on Dynamic Docker
ZHANG Wei1( ), XU Zhigang2, CHEN Yunfang1, HUANG Haiping1
), XU Zhigang2, CHEN Yunfang1, HUANG Haiping1
- 1. School of Computer Science, Nanjing University of Posts and Telecommunications, Nanjing 210023, China
2. China Information Consulting & Designing Institute co., LTD, Nanjing 210019, China
-
Received:2021-10-26Online:2022-04-10Published:2022-05-12 -
Contact:ZHANG Wei E-mail:zhangw@njupt.edu.cn
CLC Number:
Cite this article
ZHANG Wei, XU Zhigang, CHEN Yunfang, HUANG Haiping. Design and Implementation of a SDN Honeynet Based on Dynamic Docker[J]. Netinfo Security, 2022, 22(4): 40-48.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.04.005
| [1] | LIU Jian, SU Purui, YANG Min, et al. Software and Cyber Security-a Survey[J]. Journal of Software, 2018, 29(1): 42-68. |
| 刘剑, 苏璞睿, 杨珉, 等. 软件与网络安全研究综述[J]. 软件学报, 2018, 29(1): 42-68. | |
| [2] | China National Information Center. CNCERT Internet Security Threat Report[EB/OL]. [2021-10-07]. https://www.cert.org.cn/publish/main/45/2020/20200430101311844493731/20200430101311844493731_.html . |
| 中国国家信息中心. CNCERT 互联网安全威胁报告[EB/OL]. [2021-10-07]. https://www.cert.org.cn/publish/main/45/2020/20200430101311844493731/20200430101311844493731_.html . | |
| [3] |
ZHUGE Jianwei, TANG Yong, HAN Xinhui, et al. Honeypot Technology Research and Application[J]. Journal of Software, 2013, 24(4): 825-842.
doi: 10.3724/SP.J.1001.2013.04369 URL |
| 诸葛建伟, 唐勇, 韩心慧, 等. 蜜罐技术研究与应用进展[J]. 软件学报, 2013, 24(4):825-842. | |
| [4] | SPITZNER L. The Honeynet Project: Trapping the Hackers[J]. IEEE Security & Privacy, 2003(2): 15-23. |
| [5] | ABBASI F, HARRIS R. Experiences with a Generation III Virtual Honeynet[C]// IEEE. Telecommunication Networks and Applications Conference (ATNAC). New York: IEEE, 2009: 1-6. |
| [6] | SHI Leyi, LI Yang, MA Mengfei. Latest Research Progress of Honeypot Technology[J]. Journal of Electronics & Information Technology. 2019, 41(2): 498-508. |
| 石乐义, 李阳, 马猛飞. 蜜罐技术研究新进展[J]. 电子与信息学报, 2019, 41(2):498-508. | |
| [7] | WU Zhixue. Advances on Virtualization Technology of Cloud Computing[J]. Journal of Computer Applications, 2017, 37(4): 915-923. |
| 武志学. 云计算虚拟化技术的发展与趋势[J]. 计算机应用, 2017, 37(4):915-923. | |
| [8] | ZHANG Jian, XIE Tianjun. Research of Platform as a Service Architecture Based on the Docker[J]. Information Technology and Informatization, 2014(10): 131-134. |
| 张建, 谢天钧. 基于Docker的平台即服务架构研究[J]. 信息技术与信息化, 2014(10):131-134. | |
| [9] | LIU Xi, HU Zhiyong. Design and Implementation of Web Cluster Based on Docker Container[J]. Electronic Design Engineering, 2016, 4(8): 117-119. |
| [10] | Stanford University. Clean Slate Program[EB/OL]. [2021-09-07]. http://cleanslate.stanford.edu/ . |
| [11] | Open Networking Foundation. Software-Defined Networking: The New Norm for Networks[EB/OL]. [2021-09-07]. https://xueshu.baidu.com/usercenter/paper/show?paperid=71c6a62c9579d9db720a61259787cbff . |
| [12] |
GUDE N, KOPONEN T, PETTIT J, et al. NOX: Towards an Operating System for Networks[J]. Acm Sigcomm Computer Communication Review, 2008, 38(3): 105-110.
doi: 10.1145/1384609.1384625 URL |
| [13] | SUZUKI K, SONODA K. A Survey on OpenFlow Technologies[J]. IEICE Transactions on Communications, 2014, 97(2): 375-386. |
| [14] | HAH Wonkyu, ZHAO Ziming, ADAM D, et al. HoneyMix: Toward SDN-based Intelligent Honeynet[C]// ACM. The 2016 ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization. New York: ACM, 2016: 1-6. |
| [15] | KYUNG S, HAN Wonkyu, TIWARI N, et al. HoneyProxy: Design and Implementation of Next-Generation Honeynet via SDN[C]// IEEE. 2017 IEEE Conference on Communications and Network Security(CNS). New York: IEEE, 2017: 1-9. |
| [16] |
FAN Wenjun, FERNANDEZ D, DU Zhihui. Versatile Virtual Honeynet Management Framework[J]. IET Information Security, 2017, 11(1): 38-45.
doi: 10.1049/iet-ifs.2015.0256 URL |
| [17] | HU Yixun, ZHENG Kangfeng, WU Bin, et al. Dynamic Virtual Honeynet System Using Openflow[J]. Journal of Beijing University of Posts and Telecommunications, 2015, 38(6): 104-108, 119. |
| 胡毅勋, 郑康锋, 武斌, 等. Openflow下的动态虚拟蜜网系统[J]. 北京邮电大学学报, 2015, 38(6):104-108,119. | |
| [18] | KYRIAKOU A, SKLAVOS N. Container-Based Honeypot Deployment for the Analysis of Malicious Activity[C]// IEEE. Global Information Infrastructure and Networking Symposium (GIIS’18). New York: IEEE, 2018: 1-4. |
| [1] | LIU Jiqiang, HE Jiahao, ZHANG Jiancheng, HUANG Xuezhen. Log Compression Optimization Method Based on Parser Tree [J]. Netinfo Security, 2022, 22(4): 30-39. |
| [2] | LANG Bo, XIE Chong, CHEN Shaojie, LIU Hongyu. Fast-Flux Malicious Domain Name Detection Method Based on Multimodal Feature Fusion [J]. Netinfo Security, 2022, 22(4): 20-29. |
| [3] | JIN Bo, TANG Qianjin, TANG Qianlin. Interpretation of the Top 10 Development Trends of Network Security in 2022 by CCF Computer Security Professional Committee [J]. Netinfo Security, 2022, 22(4): 1-6. |
| [4] | WANG Ziheng, WU Han, XIE Jianguo, CHEN Xiaoming. Cross-Network Implementation of Superlattice Key Distribution Based on VLAN [J]. Netinfo Security, 2022, 22(4): 49-57. |
| [5] | LIU Longgeng. Research on Association Algorithm of Heterogeneous Network Security Monitoring [J]. Netinfo Security, 2022, 22(4): 58-66. |
| [6] | LYU Guohua, HU Xuexian, YANG Ming, XU Min. Ship AIS Trajectory Classification Algorithm Based on Federated Random Forest [J]. Netinfo Security, 2022, 22(4): 67-76. |
| [7] | TANG Ming, LI Cong, LI Yongbo, YUE Tianyu. Study on Static Detection of Timing Side Channel for RISC-V Architecture [J]. Netinfo Security, 2022, 22(4): 7-19. |
| [8] | LYU Kaixin, LI Zhihui, HEI Jiliao, SONG Yun. Optimal Information Rate Calculation Based on a Class of Graph Access Structure [J]. Netinfo Security, 2022, 22(4): 77-85. |
| [9] | HUANG Baohua, QU Xi, ZHENG Huiying, XIONG Tinggang. A Credit-Based Byzantine Fault Tolerance Consensus Algorithm [J]. Netinfo Security, 2022, 22(4): 86-92. |
| [10] | FENG Jingyu, SHI Yifei, WANG Teng. Crowd Spectrum Sensing Reinforcement Scheme Against Primary-secondary Collusive Attack in Smart Grid [J]. Netinfo Security, 2022, 23(3): 1-9. |
| [11] | LI Guoqi, HONG Sheng, LAN Xueting, ZHANG Hong. The Security Reference Model of the Multi-rotor UAV System [J]. Netinfo Security, 2022, 23(3): 10-19. |
| [12] | SHI Runhua, WANG Shuhao, LI Kunchang. A Lightweight Cross-domain Mutual Authentication Scheme in V2G Networks [J]. Netinfo Security, 2022, 23(3): 20-28. |
| [13] | GU Zhaojun, YANG Rui, SUI He. System Attack Surface Modeling Method in Network [J]. Netinfo Security, 2022, 23(3): 29-38. |
| [14] | FENG Guangsheng, ZHANG Yizhe, SUN Jiayu, LYU Hongwu. Key Technologies and Advances in the Research on Automated Exploitation of Computer System Vulnerabilities [J]. Netinfo Security, 2022, 23(3): 39-52. |
| [15] | LI Li, LI Zequn, LI Xuemei, SHI Guozhen. FPGA Realization of Physical Unclonable Function Based on Cross-coupling Circuit [J]. Netinfo Security, 2022, 23(3): 53-61. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||