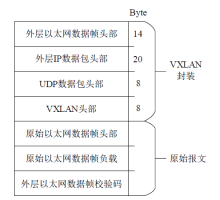
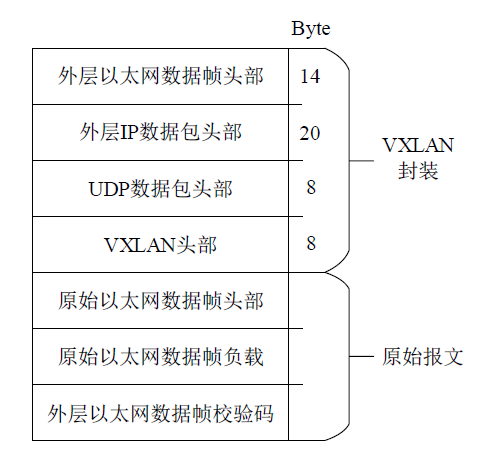
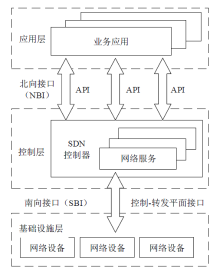
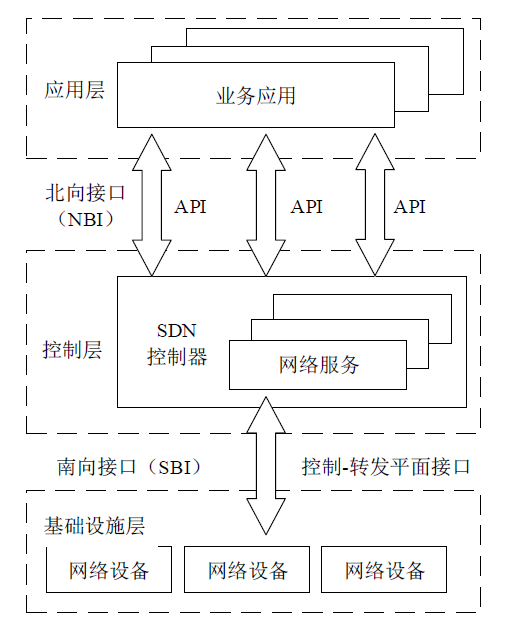
Netinfo Security ›› 2022, Vol. 22 ›› Issue (4): 49-57.doi: 10.3969/j.issn.1671-1122.2022.04.006
Previous Articles Next Articles
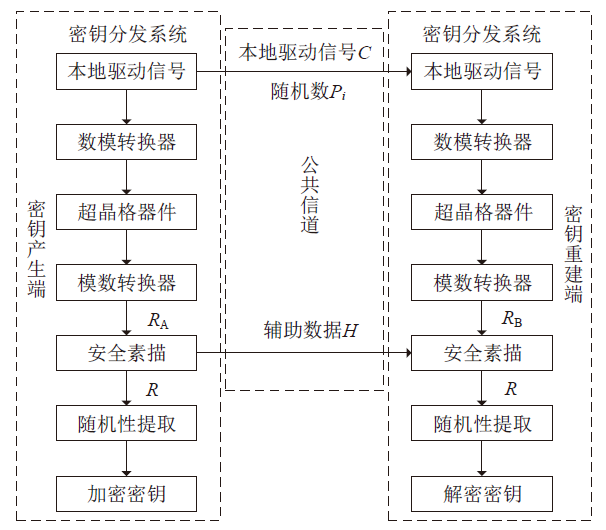
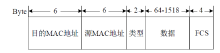
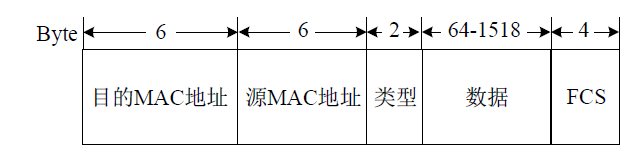
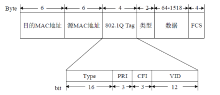
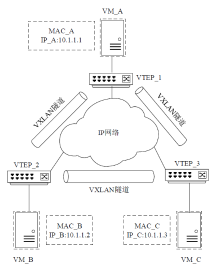
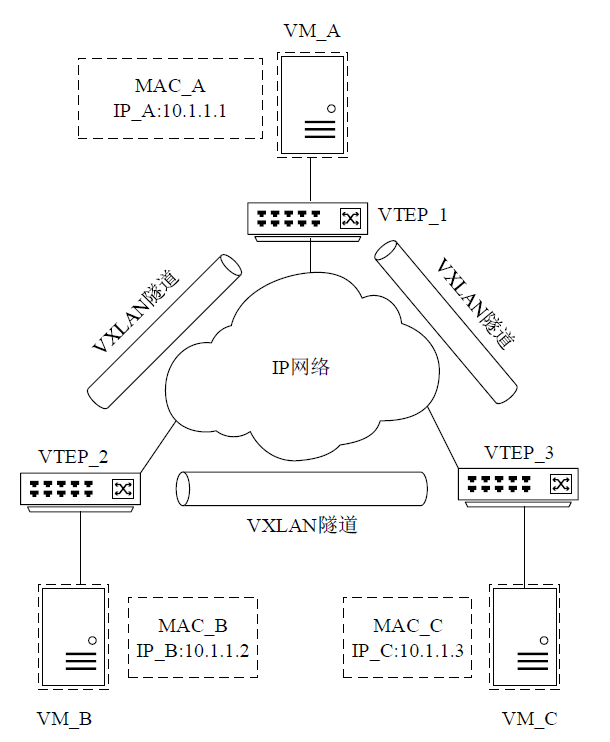
Cross-Network Implementation of Superlattice Key Distribution Based on VLAN
WANG Ziheng1, WU Han2, XIE Jianguo1, CHEN Xiaoming1( )
)
- 1. Beijing Electronic Science & Technology Institute, Beijing 100070, China
2. Suzhou Institute of Nano-Tech and Nano-Bionics, Chinese Academy of Sciences, Suzhou 215000, China
-
Received:2021-03-17Online:2022-04-10Published:2022-05-12 -
Contact:CHEN Xiaoming E-mail:chenxmphd@yeah.net
CLC Number:
Cite this article
WANG Ziheng, WU Han, XIE Jianguo, CHEN Xiaoming. Cross-Network Implementation of Superlattice Key Distribution Based on VLAN[J]. Netinfo Security, 2022, 22(4): 49-57.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.04.006
| [1] | TONG Xinhai, CHEN Xiaoming, XU Shu. Advances in Superlattice Cryptography Research[J]. Chinese Science Bulletin, 2020, 65(108): 108-116. |
| [2] |
ZHANG Yaohui, KASTRUP J, KLANN R, et al. Synchronization and Chaos Induced by Rosonant Tunneling in GaAs/AlAs Superlattices[J]. Physical Review Letters, 1996, 77(14): 3001-3004.
doi: 10.1103/PhysRevLett.77.3001 URL |
| [3] | LIU Wei, YIN Zhizhen, CHEN Xiaoming, et al. A Secret Key Distribution Technique Based on Semiconductor Superlattice Chaos Devices[J]. Chinese Science Bulletin, 2018, 63(16): 1034-1036. |
| [4] | WU Han. An Experimental Demonstration of Long-Haul Public-Channel Key Distribution Using Matched Superlattice Physical Unclonable Function Pairs[J]. Chinese Science Bulletin, 2020, 65(11): 879-882. |
| [5] | SUN Weixi, XI Shaolong. Research on NAT Traversal Problem in Peer-to-Peer[J]. Computer Technology and Development, 2014, 22(2): 242-245. |
| 孙卫喜, 席少龙. P2P中NAT穿越问题的研究[J]. 计算机技术与发展, 2014, 22(2): 242-245. | |
| [6] | YAN Ping, YI Runzhong, TONG Liang. Server Internet/Intranet Dynamic Mapping Based on DDNS and NAT[J]. Computer Engineering, 2008, 34(20): 136-137. |
| 鄢萍, 易润忠, 童亮. 基于DDNS和NAT的服务器内外网动态映射[J]. 计算机工程, 2008, 34(20):136-137. | |
| [7] | AI-KHAFFAF D A J. Improving LAN Performance Based on IEEE802.1Q VLAN Switching Techniques[J]. Journal of University of Babylon, Engineering Sciences, 2018, 26(1): 286-297. |
| [8] | HU Shuai. Research on VLAN Technology in Network Engineering[J]. Wireless Internet Technology, 2017, 10(4): 34-36. |
| 胡帅. 网络工程中的VLAN技术研究[J]. 无线互联科技, 2017, 10(4):34-36. | |
| [9] | RAO Jian. Discussion on the Experimental Design of VLAN Based on Cisco Packet Tracer[J]. Network Security Technology & Application, 2016, 16(2): 79-80. |
| 饶俭. 基于Cisco Packet Tracer的VLAN实验设计探讨[J]. 网络安全技术与应用, 2016, 16(2):79-80. | |
| [10] | QU Xinglong, AN Weipeng, WANG Lei. Inproved Scheduling Algorithm Based on CSMA/CD[J]. Measurement & Control Technology, 2016, 35(12): 98-101. |
| 屈星龙, 安葳鹏, 王磊. 基于CSMA/CD的改进调度算法研究[J]. 测控技术, 2016, 35(12):98-101. | |
| [11] | ZHANG Heying, DOU Wenhua. Implementation of VLAN in Gigabit Ethernet Switch[J]. Application Research of Computers, 2001, 18(7): 25-26. |
| 张鹤颖, 窦文华. VLAN在千兆位以太网交换机中的实现[J]. 计算机应用研究, 2001, 18(7):25-26. | |
| [12] | WEI Jinqiang. Research on the Construction of Computer Network Based on VLAN Technology[J]. Journal of Liaoning Economic Management Cadre College, 2020, 22(3): 48-50. |
| 魏晋强. 基于VLAN技术的计算机网络组建研究[J]. 辽宁经济管理干部学院学报, 2020, 22(3):48-50. | |
| [13] | QIU Jianfeng.Research on Enterprise Network Based on VLAN and Layer 3 Switching[D]. Changsha: Central South University, 2006. |
| 仇剑锋. 基于VLAN和三层交换的企业网络安全策略研究[D]. 长沙: 中南大学, 2006. | |
| [14] | ZHANG Guoping. Data Center Network for Cloud Computing Based on SDN and Overlay Technology[J]. China New Telecommunications, 2015, 17(3): 109-111. |
| 张国平. 基于SDN和Overlay的云计算数据中心网络[J]. 中国新技术, 2015, 17(3):109-111. | |
| [15] | LU Zhigang, JIANG Zhengwei, LIU Baoxu. A Virtual Network Access Control Method Based on VXLAN[J]. Computer Engineering, 2014, 40(8): 86-95. |
| 卢志刚, 姜政伟, 刘宝旭. 一种基于VXLAN的虚拟网络访问控制方法[J]. 计算机工程, 2014, 40(8):86-95. | |
| [16] | WANG Yongjian, ZHANG Jian, ZHANG Fugen, et al. VXLAN-Based Network in Cloud Data Center[J]. Communications Technology, 2017, 50(1): 78-83. |
| 王永建, 张健, 张富根, 等. 基于VXLAN的云数据中心网络研究[J]. 通信技术, 2017, 50(1):78-83. | |
| [17] | ZHANG Chaokun, CUI Yong, TANG Hehe, et al. State-of-the-Art Survey on Software Defined Networking(SDN)[J]. Journal of Software, 2015, 26(1): 62-81. |
| 张朝昆, 崔勇, 唐翯翯, 等. 软件定义网络(SDN)研究进展[J]. 软件学报, 2015, 26(1):62-81. | |
| [18] | KARAKUS M, DURRESI A. Economic Viability of Software Defined Networking(SDN)[J]. Computer Networks, 2018, 2(15): 81-95. |
| [19] |
MOHAMMED B A S, ESTABRAK B Y. Survey of Software Components to Emulate OpenFlow Protocol as an SDN Implementation[J]. American Journal of Software Engineering and Applications, 2014, 3(6): 74-82.
doi: 10.11648/j.ajsea.20140306.12 URL |
| [20] | MCKEOWN N, ANDERSON T, BALAKRISHNAN H, et al. OpenFlow: Enabling Innovation in Campus Networks[J]. ACM SIGCOMM Computer Communication Review, 2008, 38(2): 69-74. |
| [21] | CHEN Bikang. Research and Implementation of SDN Routing Algorithm Based on OpenFlow Protocol[D]. Nanjing: Nanjing University of Posts and Telecommunications, 2020. |
| 陈必康. 基于OpenFlow协议的SDN路由算法的研究与实现[D]. 南京: 南京邮电大学, 2020. | |
| [22] | GAO Yang. Research and Implementation of VXLAN Technology Based under SDN Architecture[D]. Nanjing: Southeast University, 2015. |
| 高扬. SDN架构下VXLAN技术的研究与实现[D]. 南京: 东南大学, 2015. | |
| [23] | DING Xueling, HUA Yiqiang, ZHANG Pei. Why Do Cloud Computing Networks Need VXLAN[J]. Communications World, 2015, 23(28): 39. |
| 丁雪玲, 华一强, 张沛. 云计算网络为什么需要VXLAN[J]. 通信世界, 2015, 23(28):39. |
| [1] | ZHANG Wei, XU Zhigang, CHEN Yunfang, HUANG Haiping. Design and Implementation of a SDN Honeynet Based on Dynamic Docker [J]. Netinfo Security, 2022, 22(4): 40-48. |
| [2] | LIU Jiqiang, HE Jiahao, ZHANG Jiancheng, HUANG Xuezhen. Log Compression Optimization Method Based on Parser Tree [J]. Netinfo Security, 2022, 22(4): 30-39. |
| [3] | LANG Bo, XIE Chong, CHEN Shaojie, LIU Hongyu. Fast-Flux Malicious Domain Name Detection Method Based on Multimodal Feature Fusion [J]. Netinfo Security, 2022, 22(4): 20-29. |
| [4] | JIN Bo, TANG Qianjin, TANG Qianlin. Interpretation of the Top 10 Development Trends of Network Security in 2022 by CCF Computer Security Professional Committee [J]. Netinfo Security, 2022, 22(4): 1-6. |
| [5] | LIU Longgeng. Research on Association Algorithm of Heterogeneous Network Security Monitoring [J]. Netinfo Security, 2022, 22(4): 58-66. |
| [6] | LYU Guohua, HU Xuexian, YANG Ming, XU Min. Ship AIS Trajectory Classification Algorithm Based on Federated Random Forest [J]. Netinfo Security, 2022, 22(4): 67-76. |
| [7] | TANG Ming, LI Cong, LI Yongbo, YUE Tianyu. Study on Static Detection of Timing Side Channel for RISC-V Architecture [J]. Netinfo Security, 2022, 22(4): 7-19. |
| [8] | LYU Kaixin, LI Zhihui, HEI Jiliao, SONG Yun. Optimal Information Rate Calculation Based on a Class of Graph Access Structure [J]. Netinfo Security, 2022, 22(4): 77-85. |
| [9] | HUANG Baohua, QU Xi, ZHENG Huiying, XIONG Tinggang. A Credit-Based Byzantine Fault Tolerance Consensus Algorithm [J]. Netinfo Security, 2022, 22(4): 86-92. |
| [10] | FENG Jingyu, SHI Yifei, WANG Teng. Crowd Spectrum Sensing Reinforcement Scheme Against Primary-secondary Collusive Attack in Smart Grid [J]. Netinfo Security, 2022, 23(3): 1-9. |
| [11] | LI Guoqi, HONG Sheng, LAN Xueting, ZHANG Hong. The Security Reference Model of the Multi-rotor UAV System [J]. Netinfo Security, 2022, 23(3): 10-19. |
| [12] | SHI Runhua, WANG Shuhao, LI Kunchang. A Lightweight Cross-domain Mutual Authentication Scheme in V2G Networks [J]. Netinfo Security, 2022, 23(3): 20-28. |
| [13] | GU Zhaojun, YANG Rui, SUI He. System Attack Surface Modeling Method in Network [J]. Netinfo Security, 2022, 23(3): 29-38. |
| [14] | FENG Guangsheng, ZHANG Yizhe, SUN Jiayu, LYU Hongwu. Key Technologies and Advances in the Research on Automated Exploitation of Computer System Vulnerabilities [J]. Netinfo Security, 2022, 23(3): 39-52. |
| [15] | LI Li, LI Zequn, LI Xuemei, SHI Guozhen. FPGA Realization of Physical Unclonable Function Based on Cross-coupling Circuit [J]. Netinfo Security, 2022, 23(3): 53-61. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||