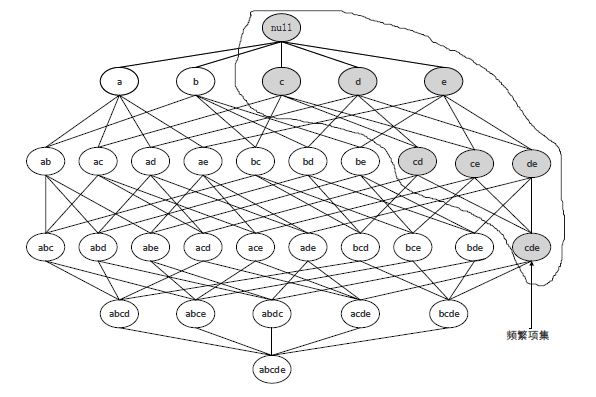
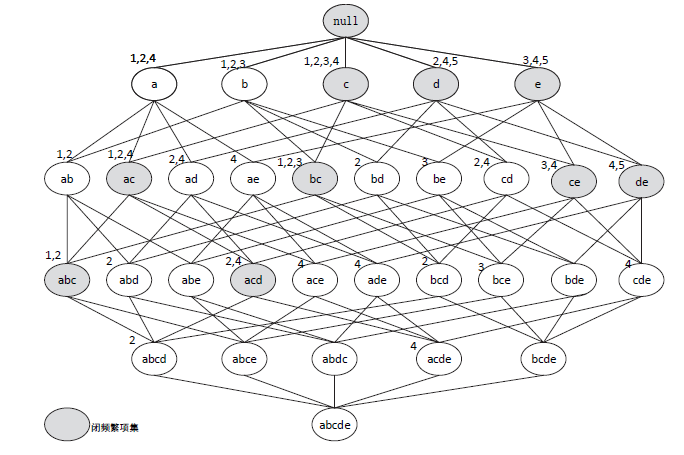
Netinfo Security ›› 2022, Vol. 22 ›› Issue (4): 58-66.doi: 10.3969/j.issn.1671-1122.2022.04.007
Previous Articles Next Articles
Research on Association Algorithm of Heterogeneous Network Security Monitoring
- China Software Evaluation Center, Beijing, 100048
-
Received:2021-12-26Online:2022-04-10Published:2022-05-12 -
Contact:LIU Longgeng E-mail:liulg@126.com
CLC Number:
Cite this article
LIU Longgeng. Research on Association Algorithm of Heterogeneous Network Security Monitoring[J]. Netinfo Security, 2022, 22(4): 58-66.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.04.007
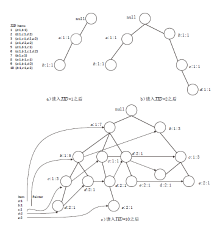
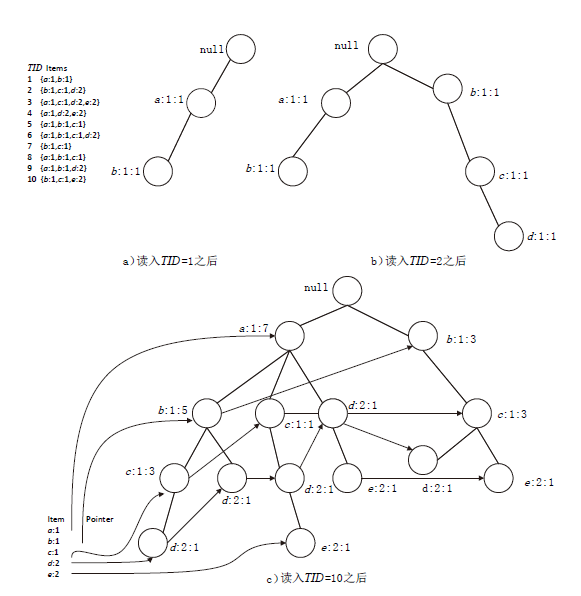
| 项 事务 | a1 | a2 | a3 | a4 | a5 | b1 | b2 | b3 | b4 | b5 | c1 | c2 | c3 | c4 | c5 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 1 | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 2 | 1 | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 3 | 1 | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 4 | 0 | 0 | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 |
| 5 | 0 | 0 | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 |
| 6 | 0 | 0 | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 |
| 7 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 1 |
| 8 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 1 |
| 9 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 1 |
| 10 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 1 |
| [1] |
RAGHAVENDRA K C, ASWANI K C. Scalable Algorithm for Generation of Attribute Implication Base Using FP-Growth and Spark[J]. Soft Computing, 2021, 25(14): 9219-9240.
doi: 10.1007/s00500-021-05844-9 URL |
| [2] | ZHANG Mingwei, CHEN Rong. Research on Optimization of Heterogeneous Air Cargo Network Based on Hybrid Particle Swarm Algorithm[EB/OL]. [2021-11-05]. https://www.researchgate.net/publication/349983223_Research_on_Optimization_of_Heterogeneous_Air_Cargo_Network_Based_on_Hybrid_Particle_Swarm_Algorithm . |
| [3] | HE Wang, LIN Guoyuan. Analysis of Cloud Server Fault Data Based on Improved FP-Growth Algorithm[J]. Computer Engineering & Science, 2020, 42(5): 770-775. |
| 何望, 林果园. 基于FP-Growth改进算法的云服务器故障数据分析[J]. 计算机工程与科学, 2020, 42(5):770-775. | |
| [4] | ZHU Anqing, LI Shuai, TANG Xiaodong. Parallel FP_Growth Association Rules Mining Method on Spark Platform[J]. Computer Science, 2020, 47(12): 147-151. |
| 朱岸青, 李帅, 唐晓东. Spark平台中的并行化FP_Growth关联规则挖掘方法[J]. 计算机科学, 2020, 47(12): 147-151. | |
| [5] | ZHANG Ya. On Mining of Frequent Item Sets of Big Data Based on K-Means Clustering[J]. Computer Simulation, 2020, 37(8): 463-467. |
| 张娅. 基于K均值聚类的大数据频繁项集挖掘研究[J]. 计算机仿真, 2020, 37(8):463-467. | |
| [6] | DAI Weimin. Research and Implementation of Parallelization of FP Growth Algorithm Based on Hadoop Platform[J]. Journal of Ningxia University(Natural Science Edition), 2020, 41(1): 74-79. |
| 戴伟敏. 基于Hadoop平台FP-Growth算法并行化研究与实现[J]. 宁夏大学学报(自然科学版), 2020, 41 (1):74-79. | |
| [7] |
WU Yilan, ZHANG Jing. Building the Electronic Evidence Analysis Model Based on Association Rule Mining and FP-Growth Algorithm[J]. Soft Computing, 2019, 24: 1-12.
doi: 10.1007/s00500-019-04566-3 URL |
| [8] | SHABTAY L, FOURNIER V P, YAARI R, et al. A Guided FP-Growth Algorithm for Mining Multitude-Targeted Item-Sets and Class Association Rules in Imbalanced Data[J]. Information Sciences, 2021, 55(3): 353-375. |
| [9] |
HU Wei, LI Jing, CHENG Jie, et al. Security Monitoring of Heterogeneous Networks for Big Data Based on Distributed Association Algorithm[J]. Computer Communications, 2020, 152(2): 206-214.
doi: 10.1016/j.comcom.2020.01.045 URL |
| [10] | HE Yunrui, YAN Yiying, DANG Yijie, et al. Research on Alarm Association Mechanism of Information System Based on FP-Growth Algorithm[J]. Journal of Physics: Conference Series, 2020, 93(1): 12082-12087. |
| [11] | WANG Xiaoying, LIU Qingjie, PAN Zhian, et al. APT Attack Detection Algorithm Based on Spatio-Temporal Association Analysis in Industrial Network[J]. Journal of Ambient Intelligence and Humanized Computing, 2020(12): 1-10. |
| [12] | FU Zeqiang, WANG Xiaofeng, KONG Jun. High-Performance Association Analysis Method for Network Security Alarm Information[J]. Computer Science, 2019, 46(5): 123-128. |
| 付泽强, 王晓锋, 孔军. 高性能网络安全告警信息的关联分析方法[J]. 计算机科学, 2019, 46(5): 123-128. | |
| [13] | LU Xianguang, DU Xuehui, WANG Wenjuan. Alert Correlation Algorithm Based on Improved FP Growth[J]. Computer Science, 2019, 46(8): 64-70. |
| 鲁显光, 杜学绘, 王文娟. 基于改进FP growth的告警关联算法[J]. 计算机科学, 2019, 46(8):64-70. | |
| [14] | GAO Quan, WAN Xiaodong. Parallel FP-Growth Algorithm Based on Load Balance[J]. Computer Engineering, 2019, 45(3): 38-41, 46. |
| 高权, 万晓冬. 基于负载均衡的并行FP-growth算法[J]. 计算机工程, 2019, 45 (3):38-41,46. | |
| [15] | WU Zihong, CHENG Lianglun, WANG Zhuowei. Hierarchical Itemset Mining Algorithm Based on Spark[J]. Computer Engineering and Design, 2019, 40(4): 96-100. |
| 吴梓宏, 程良伦, 王卓薇. 基于Spark的层次化项集挖掘算法[J]. 计算机工程与设计, 2019, 40(4):96-100. | |
| [16] |
YANG Xiaodong, LIN Xiaoxia, LIN Xiaole. Application of Apriori and FP-Growth Algorithms in Soft Examination Data Analysis[J]. Journal of Intelligent and Fuzzy Systems, 2019, 37(1): 425-432.
doi: 10.3233/JIFS-179097 |
| [17] | DONG Jie. Research on Intelligent Classification Method of Multi-Component Big Data in Heterogeneous Networks[J]. Modern Electronics Technique, 2019, 42(18): 164-167. |
| [18] | ZHAI Jianli, WANG Yingli. Research on Network Anomaly Detection Algorithm Based on Fuzzy Clustering[J]. Electronic Measurement Technology, 2019, 42(16): 172-176. |
| [19] | YUAN Ziye, GE Wancheng. Research on Resource Management Optimization of Heterogeneous Network in Vehicle Networking[J]. Information & Communications, 2019(5): 93-95. |
| [20] | LU Xianguang, DU Xuehui, WANG Wenjuan. Alert Correlation Algorithm Based on Improved FP Growth[J]. Computer Science, 2019, 46(8): 64-70. |
| [21] | LIANG Zhiqing, LI Peiyu, WANG Hui, et al. Research on TCP Protocol of QoS in Heterogeneous Network[J]. Computer Measurement & Control, 2018, 26(8): 186-190. |
| [22] | WANG Tianyue, HOU Jinxiu, YU Zhihong. Analysis of Hierarchical and Time-Phased Model of Large-Scale Power Grid Based on FP-Growth Algorithm[J]. IOP Conference Series: Earth and Environmental Science, 2018, 192(1): 31-38. |
| [23] | LIU Longgeng, LUO Guangchun. Routing Optimization in Networks Based on Traffic Gravitational Field Model[J]. International Journal of Modern Physics B, 2017, 31(11): 74-82. |
| [24] | LIU Longgeng, LUO Guangchun, QIN Ke, et al. An Algorithm Based on Logistic Regression with Data Fusion in Wireless Sensor Networks[J]. Eurasip Journal on Wireless Communications & Networking, 2017, 2017(1): 1-9. |
| [25] | LIU Longgeng, LUO Guangchun, QIN Ke, et al. An On-Demand Global Time Synchronization Based on Data Analysis for Wireless Sensor Networks[J]. Procedia Computer Science, 2018, 12(9): 503-510. |
| [1] | LIU Hong, ZHANG Yuejin, ZHAO Wenxia, YANG Mu. A Security Management Framework for Data Sensitivity and Multidimensional Classification [J]. Netinfo Security, 2021, 21(10): 48-53. |
| [2] | LANG Weimin, MA Weiguo, ZHANG Yin, YAO Jinfang. A Data Deduplication Scheme Supporting Dynamic Management of Data Ownership [J]. Netinfo Security, 2020, 20(6): 1-9. |
| [3] | ZHANG Jiacheng, PENG Jia, WANG Lei. A Graph Information Collection Method Based on Local Differential Privacy in Big Data Environment [J]. Netinfo Security, 2020, 20(6): 44-56. |
| [4] | JI Zhaoxuan, YANG Zhi, SUN Yu, SHAN Yiwei. GPU High Speed Implementation of SHA1 in Big Data Environment [J]. Netinfo Security, 2020, 20(2): 75-82. |
| [5] | Yongheng XIE, Yubo FENG, Qingfeng DONG, Mei WANG. Research on Data Ingestion Method Based on Deep Learning [J]. Netinfo Security, 2019, 19(9): 36-40. |
| [6] | Yi WEN, Xingshu CHEN, Xuemei ZENG, Yonggang LUO. DNS Protocol Restore System for Security Analysis Based on Large-scale Network [J]. Netinfo Security, 2019, 19(5): 77-83. |
| [7] | Tianxiong WU, Xingshu CHEN, Yonggang LUO. Research and Implementation of Application Program Protection Mechanism under Big Data Platform [J]. Netinfo Security, 2019, 19(1): 68-75. |
| [8] | Ronglei HU, Yanqiong HE, Ping ZENG, Xiaohong FAN. Design and Implementation of Medical Privacy Protection Scheme in Big Data Environment [J]. Netinfo Security, 2018, 18(9): 48-54. |
| [9] | Xinyang FENG, Jianjing SHEN. A Yarn and NMF Based Big Data Clustering Algorithm [J]. Netinfo Security, 2018, 18(8): 43-49. |
| [10] | Yuan TAO, Tao HUANG, Mohan ZHANG, Shuilin LI. Research and Development Trend Analysis of Key Technologies for Cyberspace Security Situation Awareness [J]. Netinfo Security, 2018, 18(8): 79-85. |
| [11] | Lin YOU, Jiahao LIANG. Research on Secure Identity Authentication Based on Homomorphic Encryption and Biometric [J]. Netinfo Security, 2018, 18(4): 1-8. |
| [12] | Xiuqing LU, Hequn XIAN. A Big Data Integrity Auditing Scheme Based on User Authorization in Cloud Storage [J]. Netinfo Security, 2018, 18(4): 32-37. |
| [13] | Min GUO, Yingming ZENG, Jinli YAO, Xiaowen DA. The Analysis of Software Behavior Security Based on Big Data Samples [J]. Netinfo Security, 2017, 17(9): 153-156. |
| [14] | Yang CHEN, Yong WANG, Wei SUN. A YARN-based Smart Grid Big Data Abnormal Detection [J]. Netinfo Security, 2017, 17(7): 11-17. |
| [15] | Wenjie WANG, Baiqing HU, Chi LIU. A Survey of Open Source Software for Big Data Governance and Security [J]. Netinfo Security, 2017, 17(5): 28-36. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||