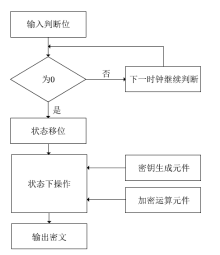
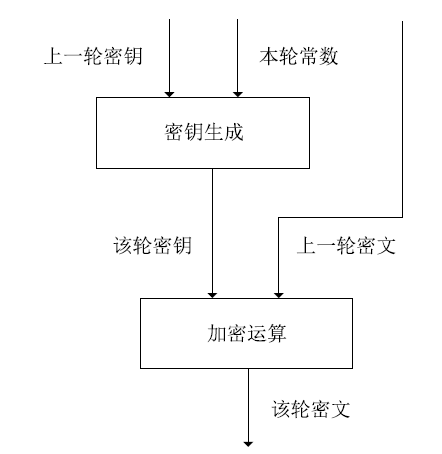
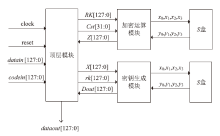
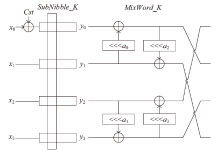
Netinfo Security ›› 2021, Vol. 21 ›› Issue (1): 57-64.doi: 10.3969/j.issn.1671-1122.2021.01.007
Previous Articles Next Articles
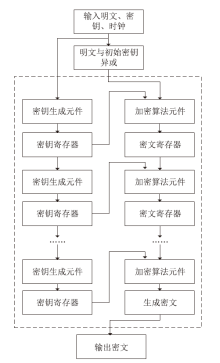
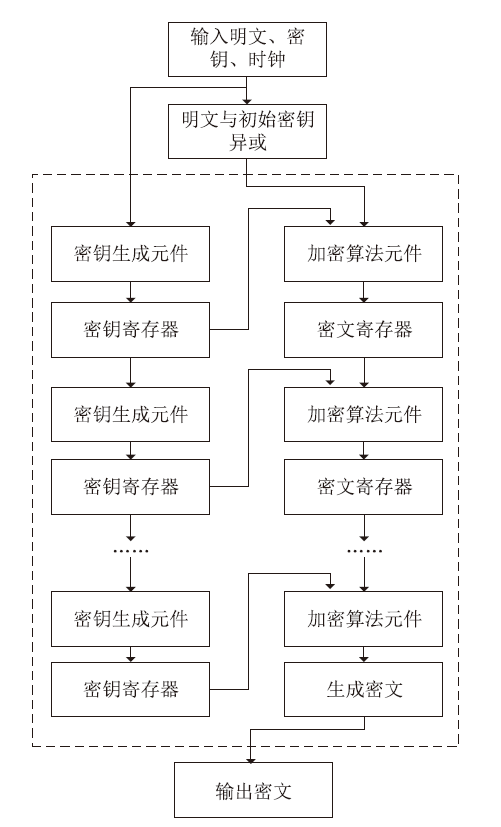
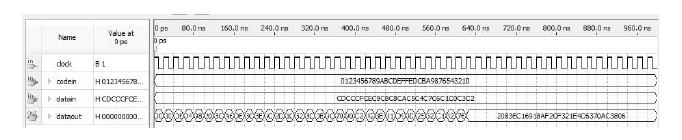
High-speed Implementation of FESH Block Cipher Algorithm Based on FPGA
WANG Jianxin1, ZHOU Shiqiang1, XIAO Chaoen1( ), ZHANG Lei1,2
), ZHANG Lei1,2
- 1. Department of Electronic and Communication Engineering, Beijing Electronics Science and Technology Institute, Beijing 100070, China
2. National Engineering Laboratory for Agri-product Quality Traceability, Beijing Technology and Business University, Beijing 100048, China
-
Received:2020-11-24Online:2021-01-10Published:2021-02-23 -
Contact:XIAO Chaoen E-mail:xce@besti.edu.cn
CLC Number:
Cite this article
WANG Jianxin, ZHOU Shiqiang, XIAO Chaoen, ZHANG Lei. High-speed Implementation of FESH Block Cipher Algorithm Based on FPGA[J]. Netinfo Security, 2021, 21(1): 57-64.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.01.007
| [1] | WANG Jianfeng, ZHANG Yinghui, MA Hua. Discussion the Relationship Between Cryptography and Information Security[J]. Journal of Xi'an University(Natural Science Edition), 2020,23(1):34-36. |
| 王剑锋, 张应辉, 马华. 浅谈密码学与信息安全[J]. 西安文理学院学报(自然科学版), 2020,23(1):34-36. | |
| [2] | GE Xiaohu. Application and Development of Cryptography in Network Information Security[J]. Electronic Technology and Software Engineering, 2020,176(6):242-243. |
| 葛小虎. 密码学技术在网络信息安全中的应用与发展[J]. 电子技术与软件工程, 2020,176(6):242-243. | |
| [3] | LIU Lihua. Attribute-based Lattice Cryptography and its Application in Security Access Control of Information[D]. Xi'an: Xi'an University of Technology, 2019. |
| 刘丽华. 基于属性的格密码及其在信息安全访问控制中的应用[D]. 西安:西安理工大学, 2019. | |
| [4] | MISHRA D, DAS A K, CHATURVEDI A, et al. A Secure Password-based Authentication and Key Agreement Scheme Using Smart Cards[J]. Journal of Information Security & Applications, 2015,23(8):28-43. |
| [5] | PRENEEL B. Cryptography and Information Security in the Post-Snowden Era[C] //IEEE. 2015 IEEE/ACM 1st International Workshop on Technical and Legal Aspects of Data Privacy and Security, May 18, 2015, Florence, Italy. New Jersey: IEEE, 2015: 1. |
| [6] | ZHENG Fangyu, LIN Jingqiang, WEI Rong, et al. Research Progresses on Security Applications of Cryptography and Discussions on Validation of Software Cryptographic Modules[J]. Journal of Cryptologic Research, 2020,7(3):290-310. |
| 郑昉昱, 林璟锵, 魏荣, 等. 密码应用安全技术研究及软件密码模块检测的讨论[J]. 密码学报, 2020,7(3):290-310. | |
| [7] | WANG Xiaoxia. Analysis on the Application of Cryptography to Network Information Security[J]. Network Security Technology & Application, 2019(2):17-18. |
| 王晓霞. 关于密码学技术应用于网络信息安全的分析[J]. 网络安全技术与应用, 2019(2):17-18. | |
| [8] | LIN Xiao. Cryptography is Applied to the Research of Network Information Security[J]. Network Security Technology & Application, 2018(9): 33, 38. |
| 林晓. 密码学技术应用于网络信息安全研究[J]. 网络安全技术与应用, 2018(9): 33, 38. | |
| [9] | MUGHAL M A, LUO Xiong, ULLAH A, et al. A Lightweight Digital Signature Based Security Scheme for Human-centered Internet of Things[EB/OL]. https://ieeexplore.ieee.org/document/8374035, 2010-06-06. |
| [10] | HAN Guoyong. Several Cryptanalysis Methods on Block Ciphers[D]. Jinan: Shandong Normal University, 2019. |
| 韩国勇. 分组密码算法的若干安全性分析方法研究[D]. 济南:山东师范大学, 2019. | |
| [11] | LI Fan. Research and Analysis of Diffusion Layer and Confusion Layer of Block Cipher[D]. Jinan: Shandong Normal University, 2020. |
| 李凡. 分组密码扩散层与混淆层的研究与分析[D]. 济南:山东师范大学, 2020. | |
| [12] | RASHIDI B. High-throughput and Flexible ASIC Implementations of SIMON and SPECK Lightweight Block Ciphers[J]. International Journal of Circuit Theory and Applications, 2019,47(8):1254-1268. |
| [13] | BANIK S, BOGDANOV A, ISOBE T, et al. Midori: A Block Cipher for Low Energy[C] //Springer. International Conference on the Theory and Application of Cryptology and Information Security, November 29-December 3, Auckland, New Zealand. Heidelberg: Springer, 2015: 411-436. |
| [14] | BANIK S, PANDEY S K, PEYRIN T, et al. GIFT: A Small Present-towards Reaching the Limit of Lightweight Encryption[EB/OL]. https://www.iacr.org/archive/ches2017/10529227/10529227.pdf, 2020-08-11. |
| [15] | FENG Chen. Research on Support of 256-bit Algorithms in 5G Mobile Communication System[J]. Journal of Information Security Research, 2020,6(8):716-721. |
| [16] | ZHANG Jingzhi. Design and Analysis of Lightweight Block Cipher Algorithms for Internet of Things Applications[D]. Chengdu: University of Electronic Science and Technology of China, 2020. |
| 张景芝. 面向物联网应用的轻量级分组密码算法的设计与分析[D]. 成都:电子科技大学, 2020. | |
| [17] | GUI Zhuang. Research of Cryptography Application Technology in Security Communication of Internet of Vehicles[D]. Chengdu: University of Electronic Science and Technology of China, 2020. |
| 桂壮. 面向车联网安全通信的密码应用技术研究[D]. 成都:电子科技大学, 2020. | |
| [18] | FENG Kai, LI Wei, GONG Jiezhong. Analysis on the Application Status of Cryptographic Algorithms in Internet of Vehicles[J]. China Information Security, 2019(9):97-99. |
| 冯凯, 李巍, 龚洁中. 车联网中密码算法应用现状分析[J]. 中国信息安全, 2019(9):97-99. | |
| [19] | JIA Keting, DONG Xiaoyang, WEI Chongming, et al. On the Design of Block Cipher FESH[J]. Journal of Cryptologic Research, 2019,6(6):713-726. |
| 贾珂婷, 董晓阳, 魏淙洺, 等. 分组密码算法FESH[J]. 密码学报, 2019,6(6):713-726. | |
| [20] | SHANG Liwei. Design and Implementation of Multiplier Based on Finite State Machine[D]. Taiyuan: Taiyuan University of Science and Technology, 2012. |
| 商丽卫. 基于有限状态机的乘法器设计与实现[D]. 太原:太原科技大学, 2012. | |
| [21] | MIAO Sanli, ZUO Jinyin, SONG Yufei. Design and Achieve of FPGA-based RC4 Encryption Algorithm[J]. Computer Measurement & Control, 2018,26(2):252-254, 263. |
| 苗三立, 左金印, 宋宇飞. 基于FPGA的RC4加密算法设计及实现[J]. 计算机测量与控制, 2018,26(2):252-254,263. | |
| [22] | LUO Xiang, LI Jiaolong, TIAN Zhengkai. Optimization Design of FSM Based on Verilog HDL[J]. Electronics Quality, 2012(3):26-38, 42. |
| 罗翔, 李娇龙, 田正凯. 基于Verilog HDL的有限状态机的优化设计[J]. 电子质量, 2012(3):36-38,42. | |
| [23] | SALAUYOU V, ZABROCKI U. Coding Techniques in Verilog for Finite State Machine Designs in FPGA[EB/OL]. https://www.researchgate.net/publication/335766383_Coding_Techniques_in_Verilog_for_Finite_State_Machine_Designs_in_FPGA, 2020-05-11. |
| [24] | UMA R, DHAVACHELVAN P. Synjournal Optimization for Finite State Machine Design in FPGAs[J]. International Journal of VLSI Design & Communication Systems, 2013,3(6):79-89. |
| [25] | LIU Yufeng, XU Xiangyang, SU Hao, et al. Optimization and Design of Block Cipher AES[J]. Computer Applications and Software, 2020,37(1):267-270, 297. |
| 刘宇峰, 许向阳, 苏浩, 等. 分组密码AES的优化与设计[J]. 计算机应用与软件, 2020,37(1):267-270,297. | |
| [26] | FANG Yi, CONG Linhu, DENG Jianqiu, et al. Fast Implementation of SM3 Algorithm Based on FPGA[J]. Computer Applications and Software, 2020,37(6):259-262. |
| 方轶, 丛林虎, 邓建球, 等. 基于FPGA的SM3算法快速实现方案[J]. 计算机应用与软件, 2020,37(6):259-262. | |
| [27] | GU Huitao, WU Zongtao. Fast Hardware Design of SM3 Algorithms Based on Double-pipeline and Synchronous Iteration[J]. Computer & Network, 2020,46(2):54-56. |
| 谷会涛, 武宗涛. 基于双重流水同步迭代的SM3算法高速硬件设计[J]. 计算机与网络, 2020,46(2):54-56. | |
| [28] | ZHOU Yonghao, DONG Wanying, LI Bin, et al. Reconfigurable SHA-3 Pipeline Structure Optimization and Implementation[J]. Modern Computer, 2020(12):15-20. |
| 周雍浩, 董婉莹, 李斌, 等. 可重构的SHA-3算法流水线结构优化及实现[J]. 现代计算机, 2020(12):15-20. | |
| [29] | DESHPANDE P U, BHOSALE S A. AES Encryption Engines of Many Core Processor Arrays on FPGA by Using Parallel, Pipeline and Sequential Technique[C] //IEEE. 2015 International Conference on Energy Systems & Applications, October 30-November 1, 2015, Pune, India. New Jersey: IEEE, 2016: 75-80. |
| [30] | BHIMANNAVAR R, JAYASHREE H V, BHIMANNAVAR R, et al. FPGA Implementation of Pipelined Architecture for RC5[EB/OL]. https://research.ijcaonline.org/gtetc/number1/gtetc1306.pdf, 2020-05-11. |
| [1] | DONG Xiaoli, SHANG Shuai, CHEN Jie. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [2] | Yong WANG. Study on New Mathematical Difficult Problem and Application in Block Cipher [J]. Netinfo Security, 2014, 15(11): 79-82. |
| [3] | Ping ZHANG, Chang-song CHEN, Hong-gang HU. Authenticated Encryption Modes Based on Block Ciphers [J]. Netinfo Security, 2014, 15(11): 8-10. |
| [4] | . Authenticated Encryption Modes Based on Block Ciphers [J]. , 2014, 14(11): 8-. |
| [5] | . Study on New Mathematical Difficult Problem and Application in Block Cipher [J]. , 2014, 14(11): 79-. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||